Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
30 results about "DLL injection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
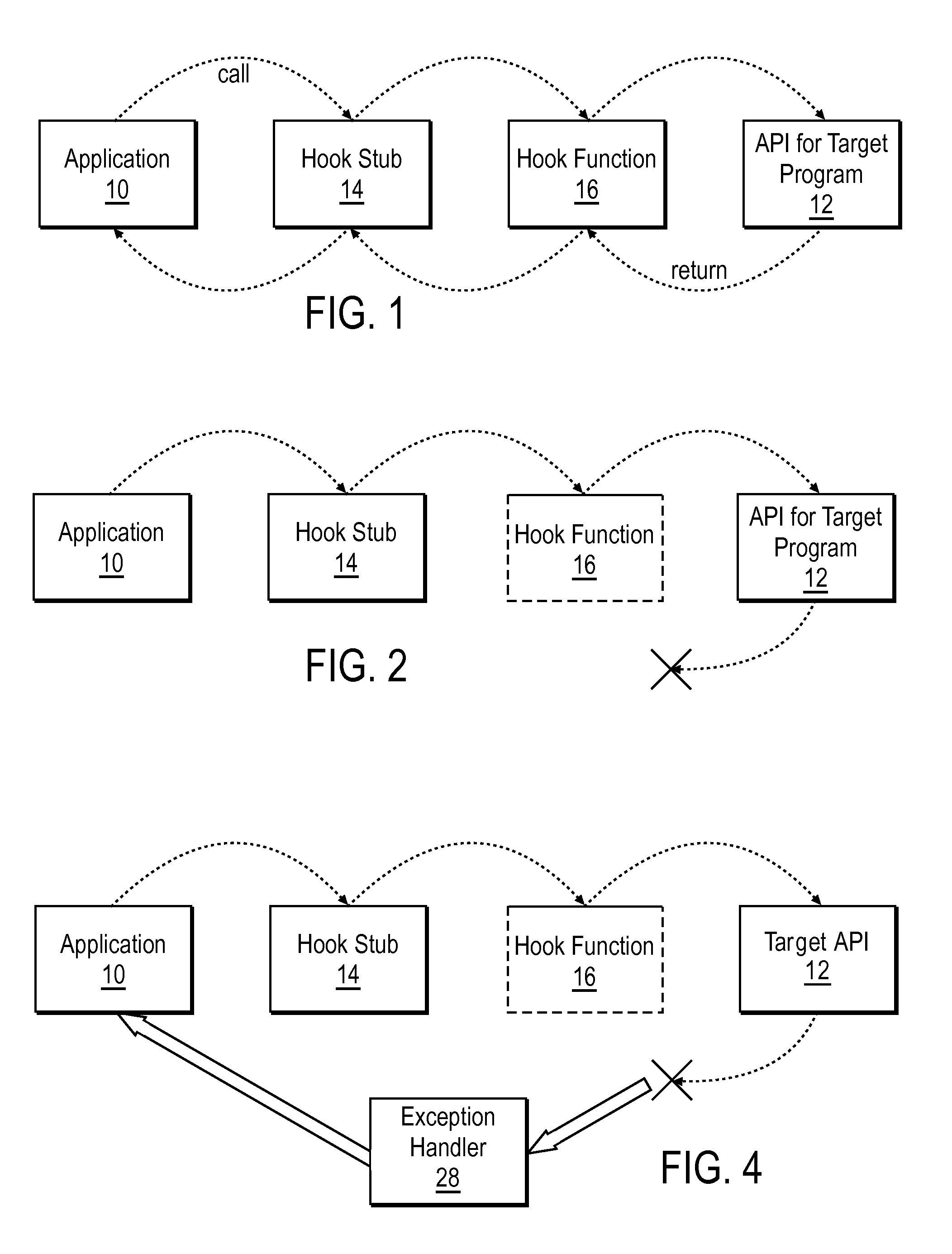
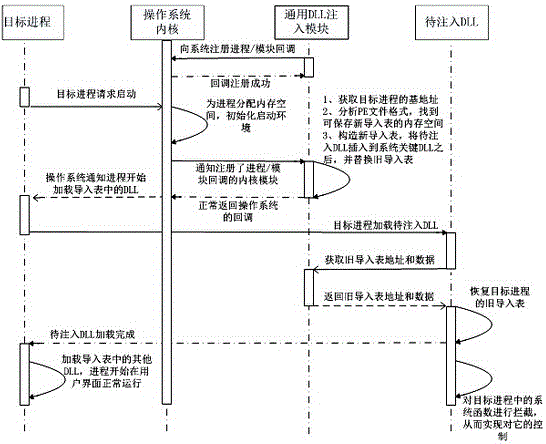
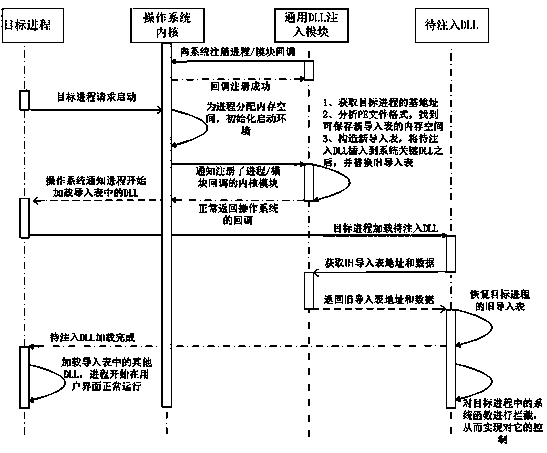
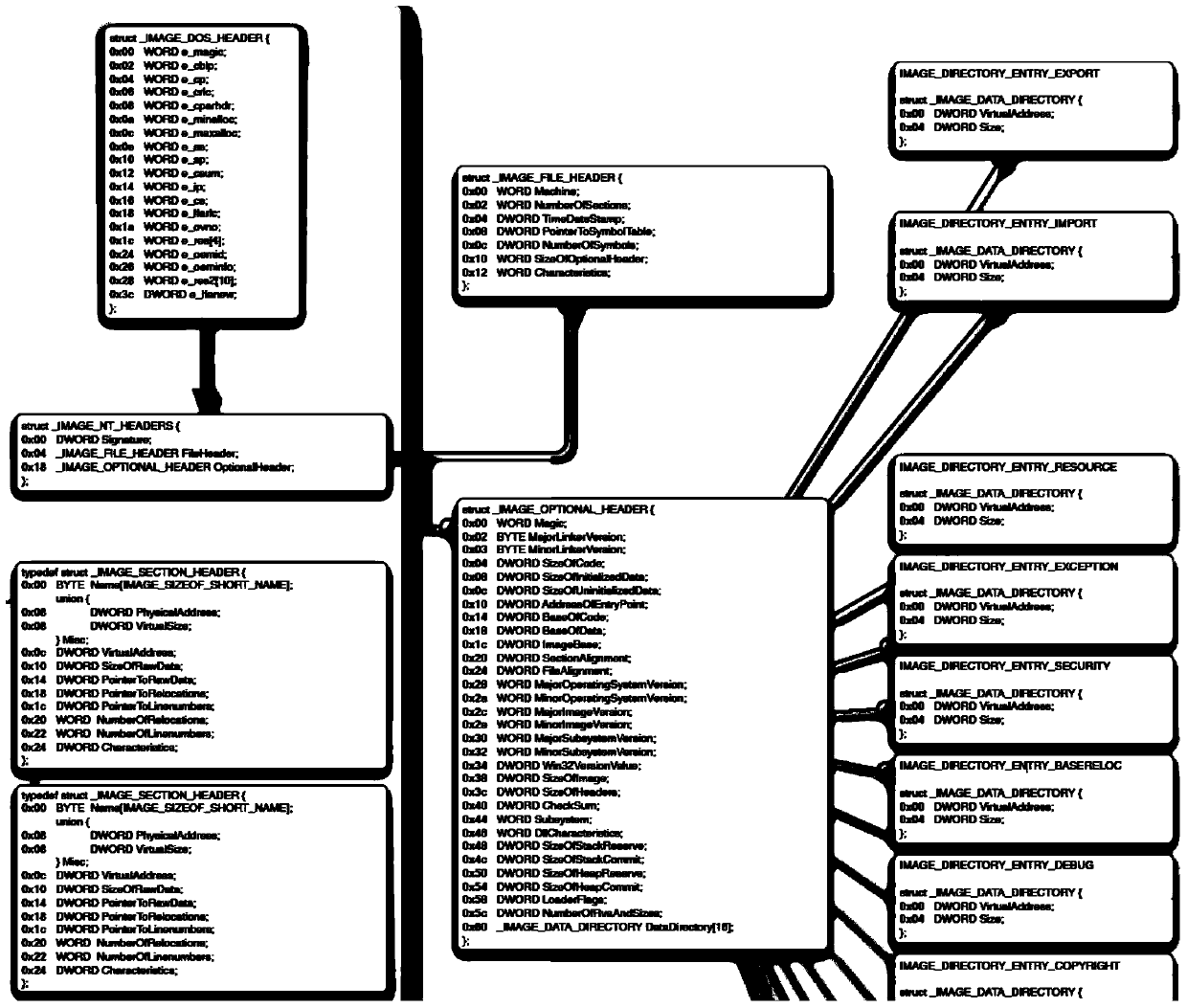
In computer programming, DLL injection is a technique used for running code within the address space of another process by forcing it to load a dynamic-link library. DLL injection is often used by external programs to influence the behavior of another program in a way its authors did not anticipate or intend. For example, the injected code could hook system function calls, or read the contents of password textboxes, which cannot be done the usual way. A program used to inject arbitrary code into arbitrary processes is called a DLL injector.
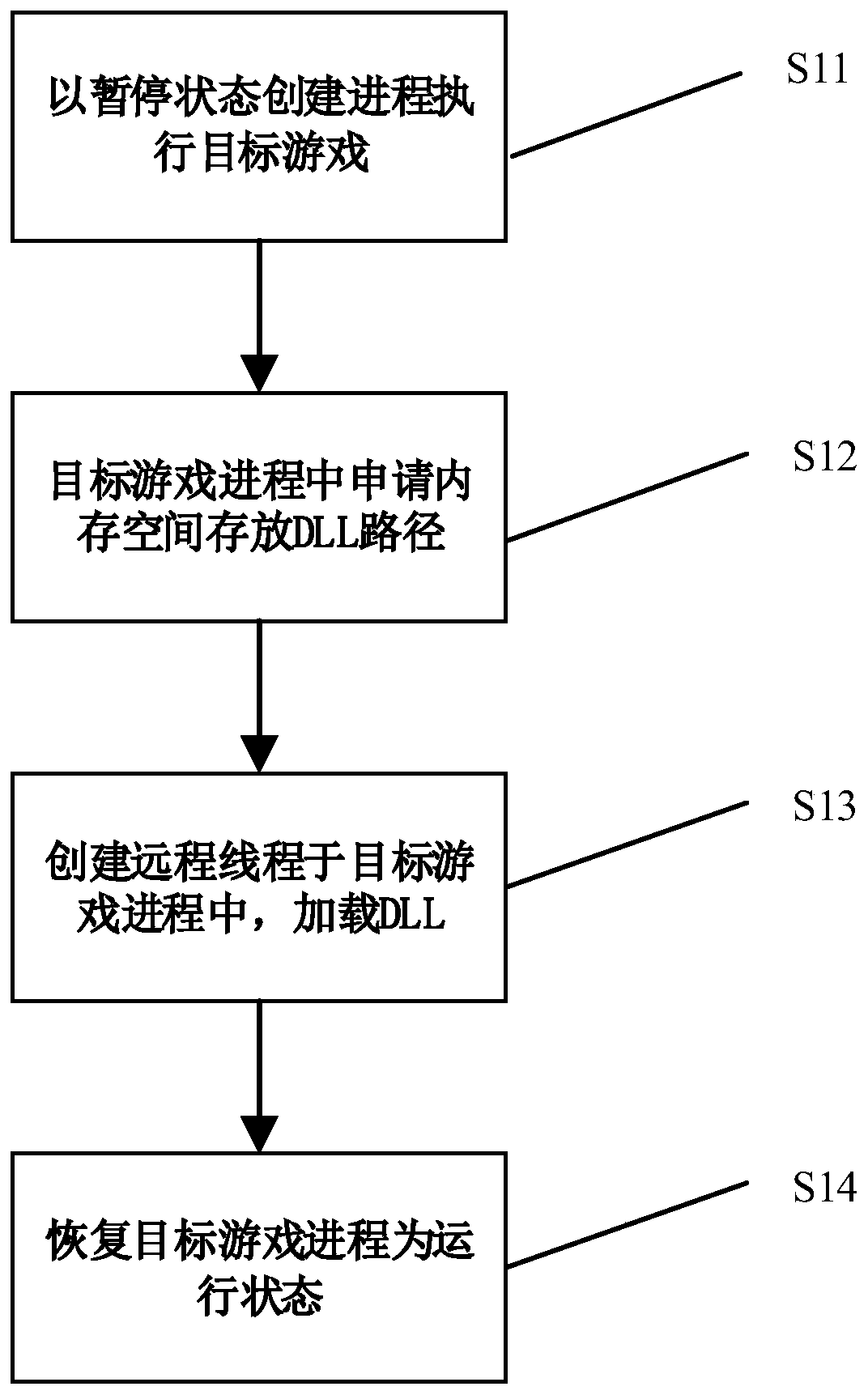
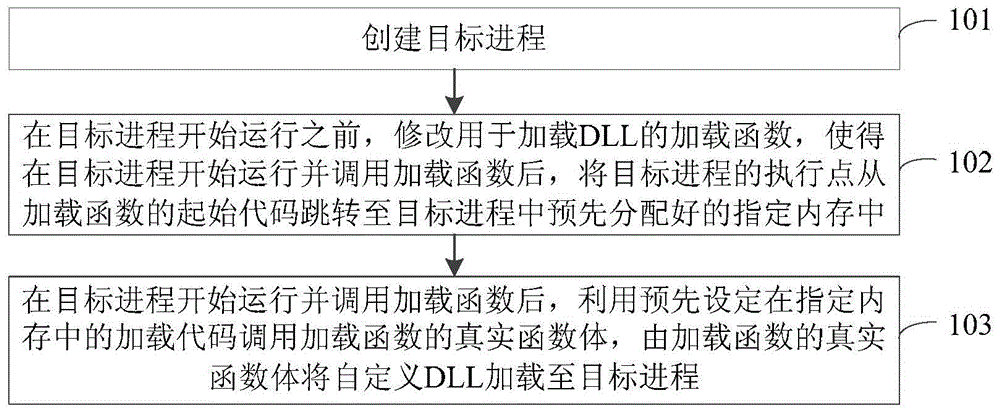
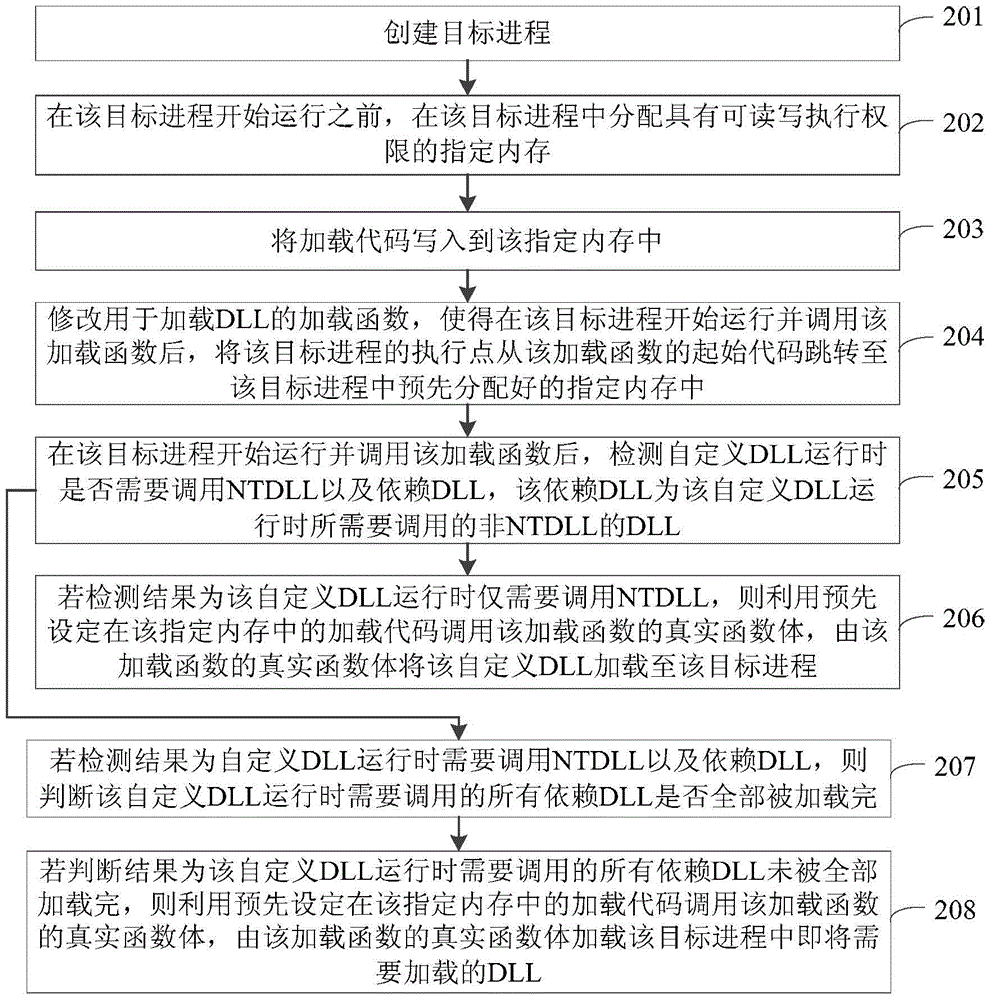
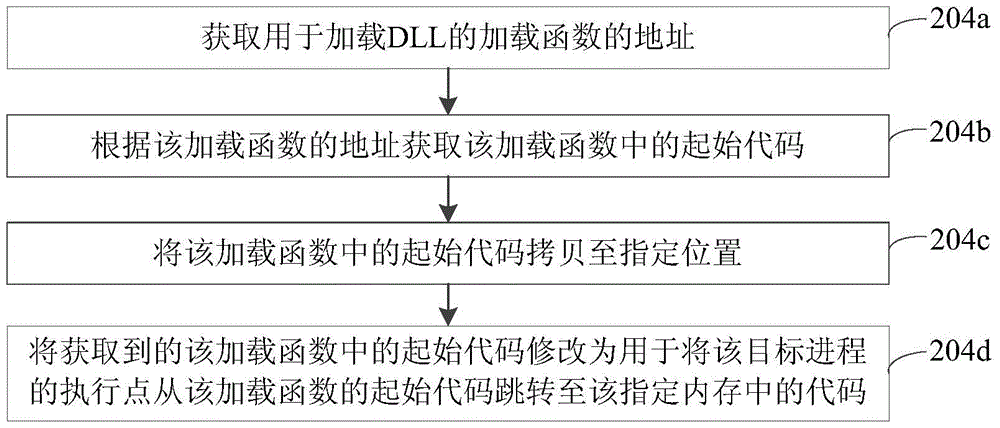
Method and device for loading user-defined DLL into target progress
Owner:GUANGZHOU HUADUO NETWORK TECH
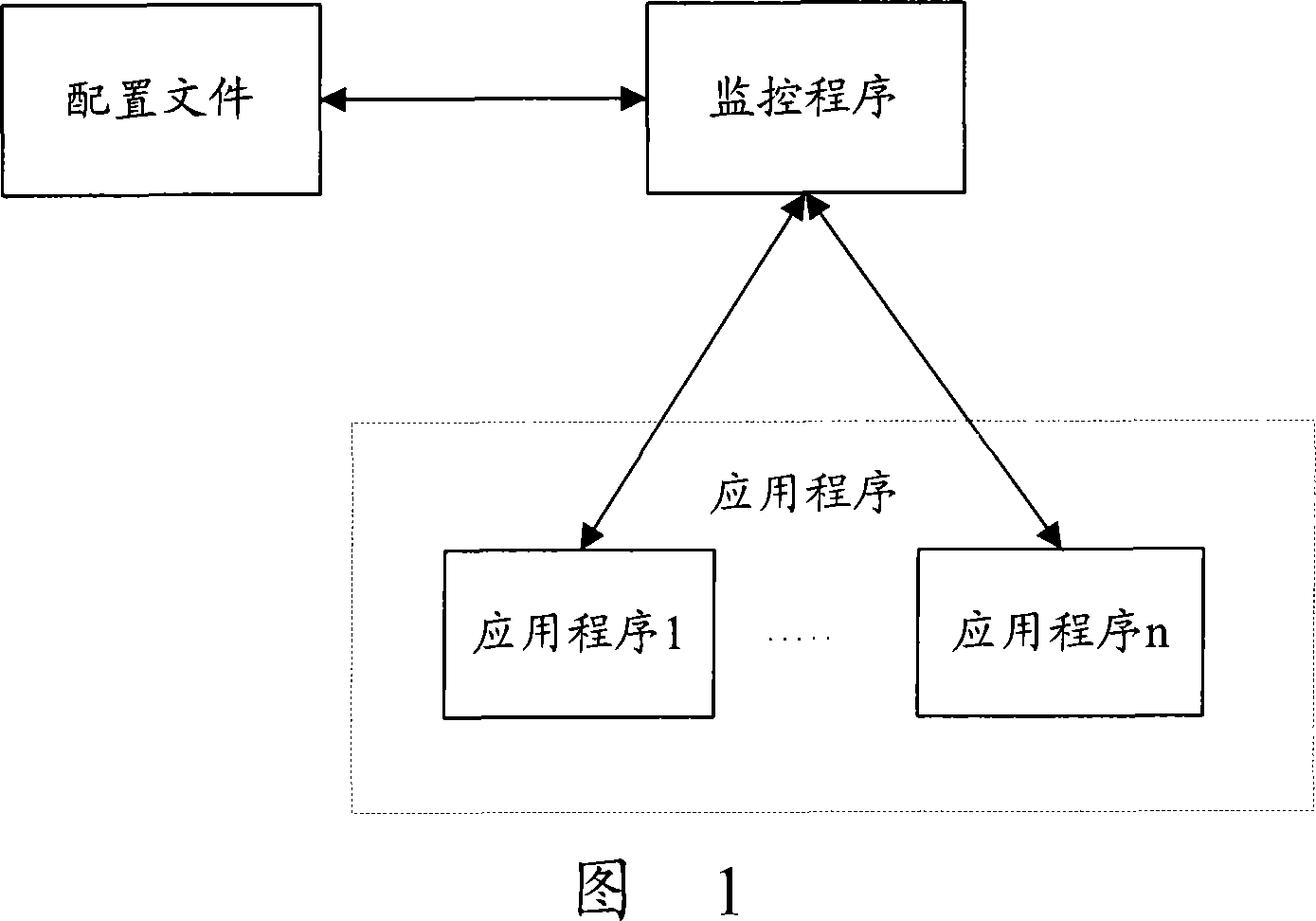
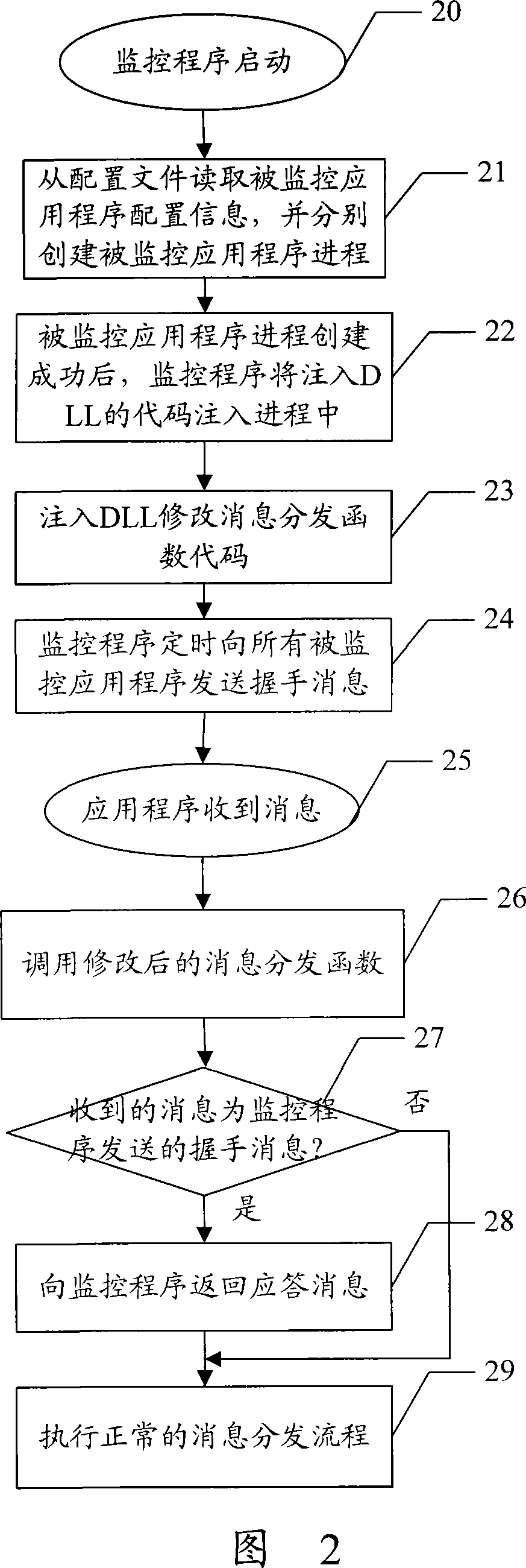
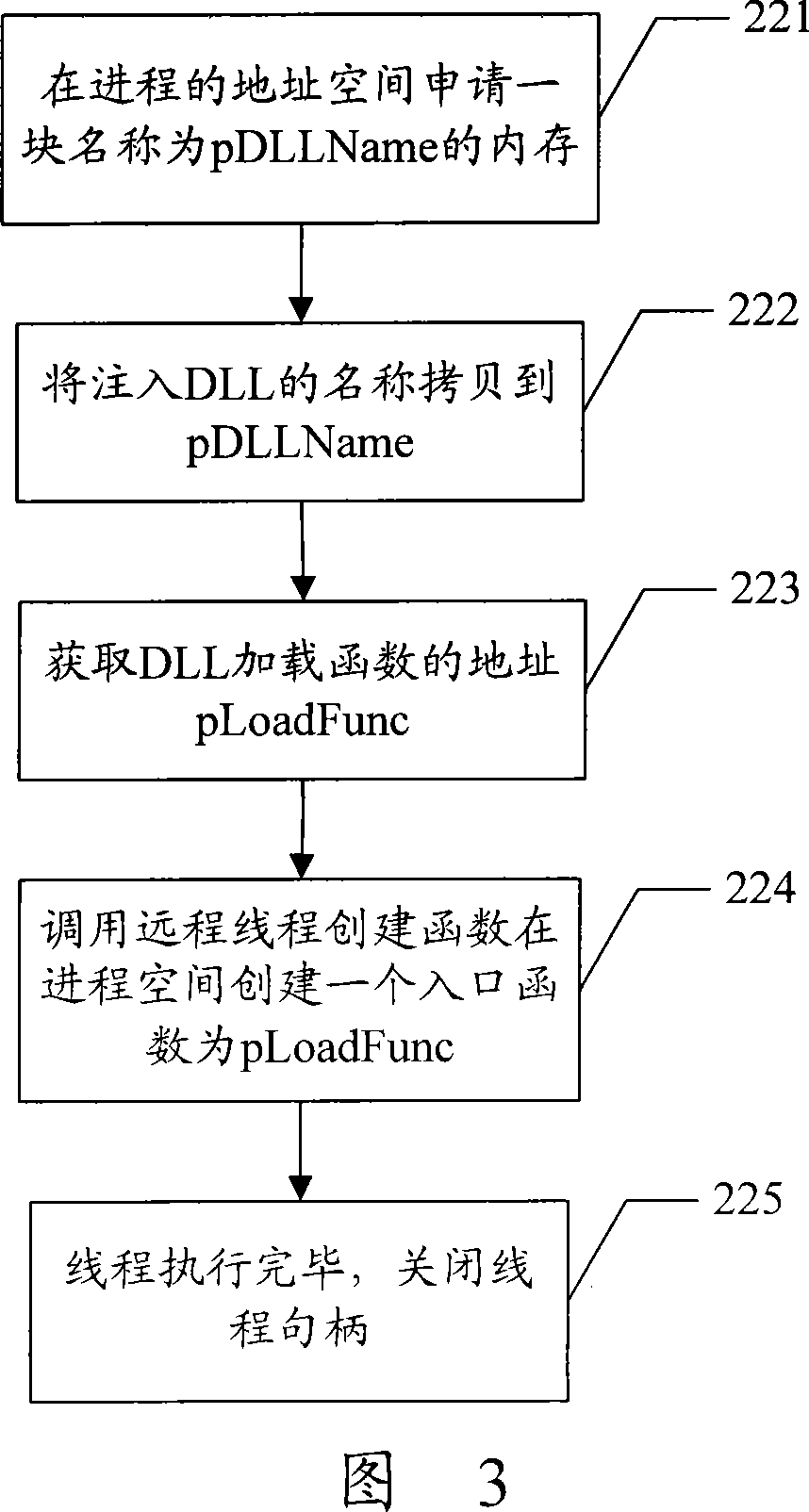
Method for monitoring application program based on window platform
InactiveCN101227630AImprove scalabilityAccurate real-time monitoringSupervisory/monitoring/testing arrangementsData switching networksCode injectionApplication software
The invention discloses an application program monitoring process based on a window platform, which comprises the following steps respectively establishing a process of the application program which is monitored after the starting of the monitor program, wherein the monitor program inputs the code which belongs to a dynamic link library (DLL), inputting a message distribution function code in a modification process of DLL, sending handshaking messages to all the monitored programs by the monitor program on a scheduled time, transferring modified message distribution function by the monitored programs the after receiving the message, sanding a return answer message to the monitor program after the message distribution function ascertains the massage is the handshaking message which is sent by the monitor program. The monitoring method of the invention adopts the DLL inputting mode to modify the code of the system information distribution function, which enables the system information distribution function to capture and answer the handshaking message from the monitor program without adding code combined monitoring in application programs, and has the advantages of good scalability and can realize a accurate real-time monitor.
Owner:ZTE CORP
Video recording device and method
InactiveCN103823683AReduce resource consumptionImprove service experienceSpecific program execution arrangementsComputer hardwareResource consumption
The invention provides a video recording device and method. The video recording device and method are applied to a host of a user. The video recording device comprises a DLL injection unit, an interface establishment unit, a function replacement unit and a function call unit. The DLL injection unit is used for injecting a DLL into a target process, wherein the DLL comprises a video capture DLL. The interface establishment unit is used for establishing a Direct device interface. The function replacement unit is used for replacing a drawing function in the target process with an address of an image capture function in the video capture DLL. The function call unit is used for calling the image capture function to acquire pixel data of an image to be drawn in a background buffering process before the drawing function is called by the target process every time. Compared with the prior art, the video recording device and method have the advantages that API HOOK can be conducted on drawing functions of various Direct versions, as a result, image data on a display card can be acquired, the purpose of reducing resource consumption of a CPU, an internal storage and the like is achieved when full-screen game video is recorded, and better service experience is provided.
Owner:北京花房科技有限公司
Method for implementing ejection-safe API interception
ActiveUS20090204980A1Specific program execution arrangementsMemory systemsParallel computingApplication software
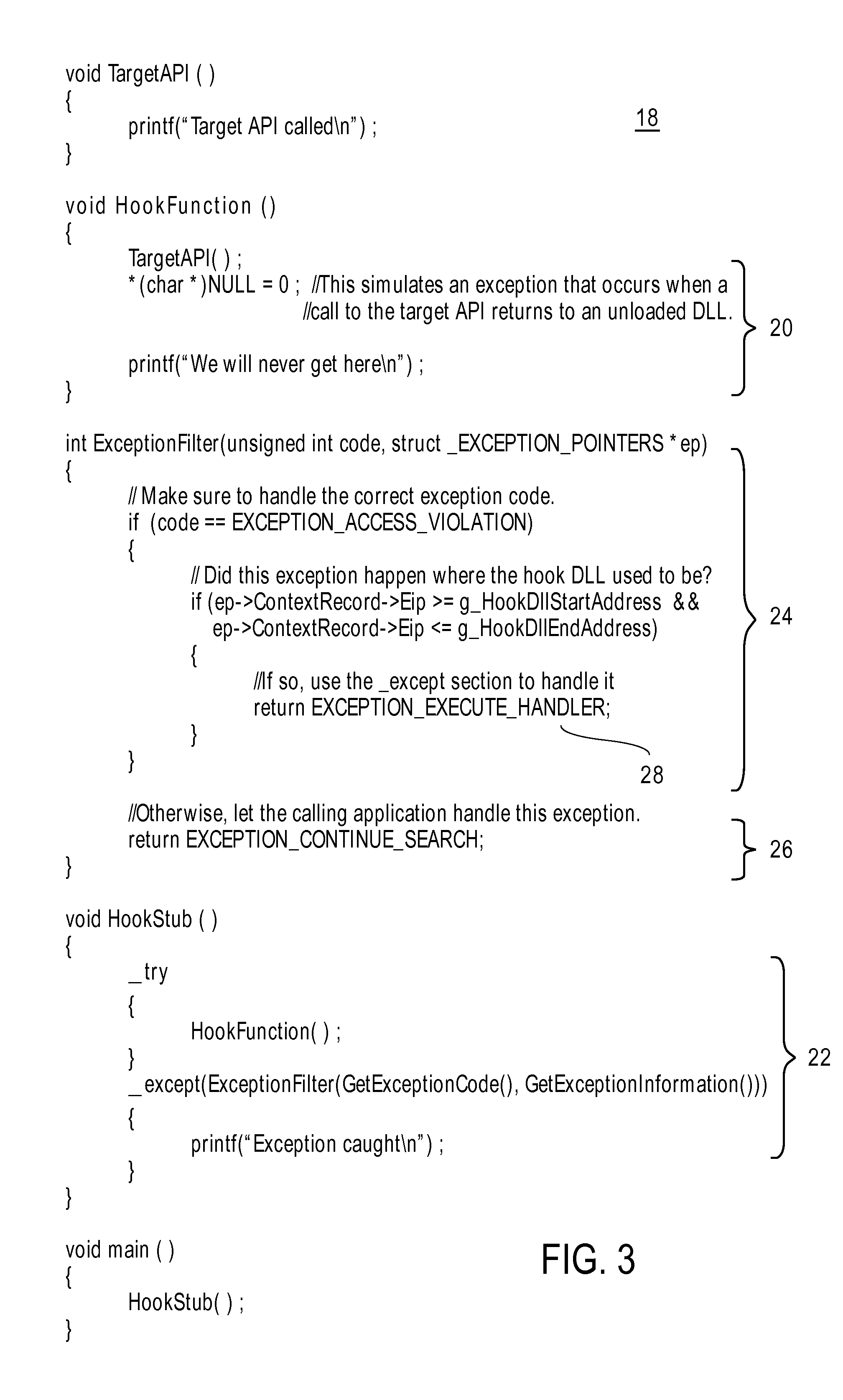
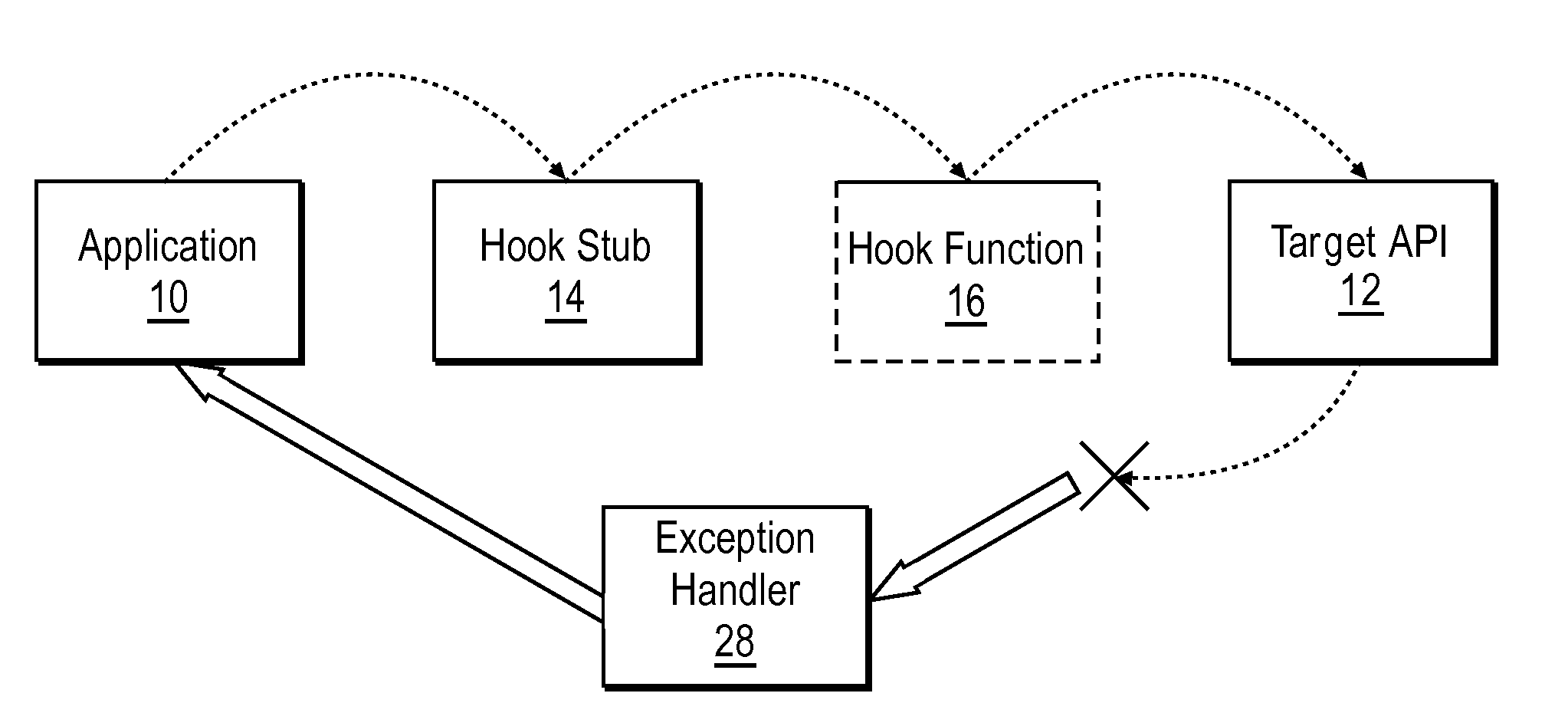
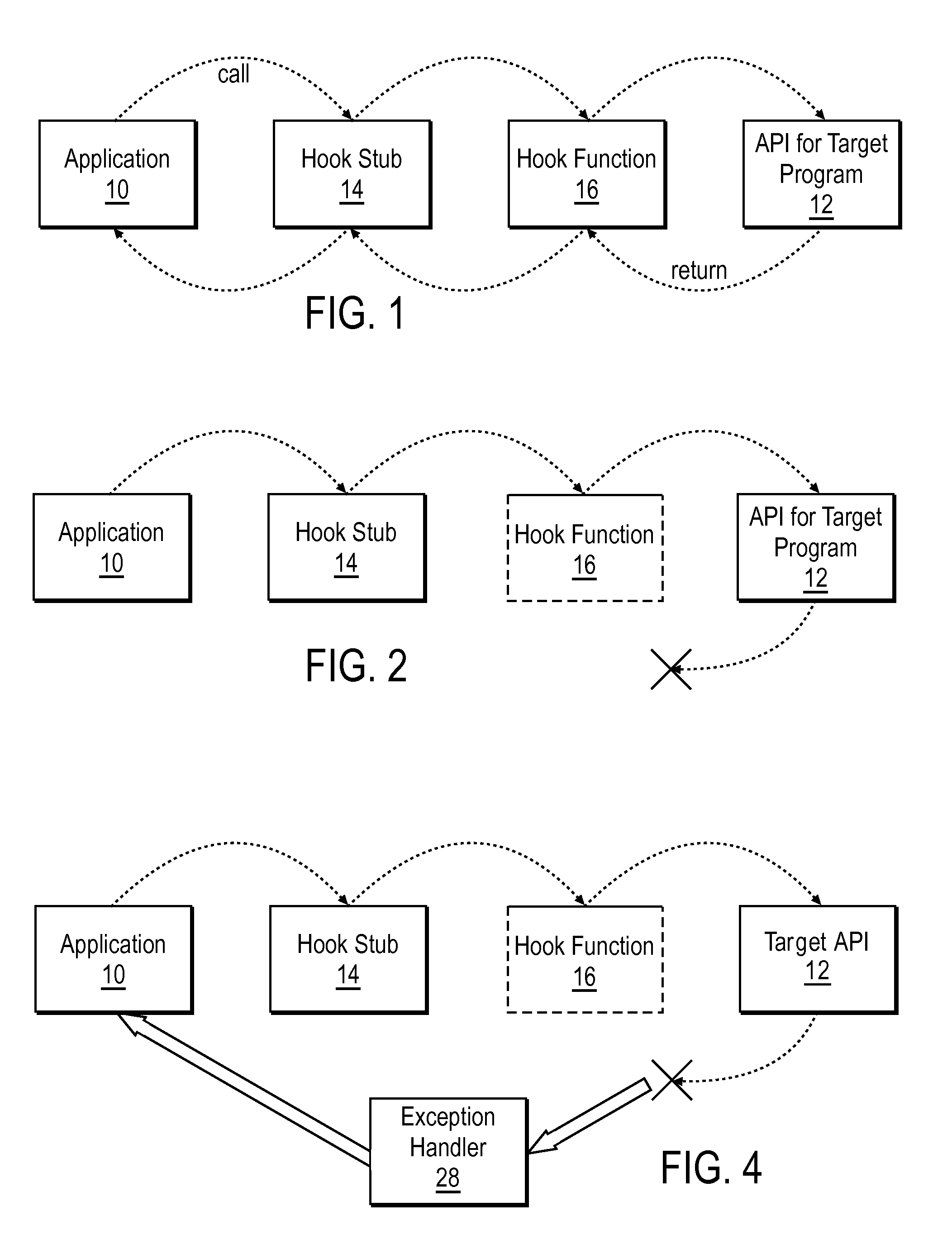
A DLL that includes an API hook is injected into the address space of a target computer process called by an application program. Upon termination of the application program, computer-readable instructions describing a process for filtering exceptions returned from the target computer process are stored in memory locations accessible to the target computer process and the DLL is ejected from the address space.
Owner:CA TECH INC
Method and device for monitoring program
ActiveCN106709325AImprove monitoring efficiencyImprove efficiencyPlatform integrity maintainanceApplication programming interfaceSoftware engineering
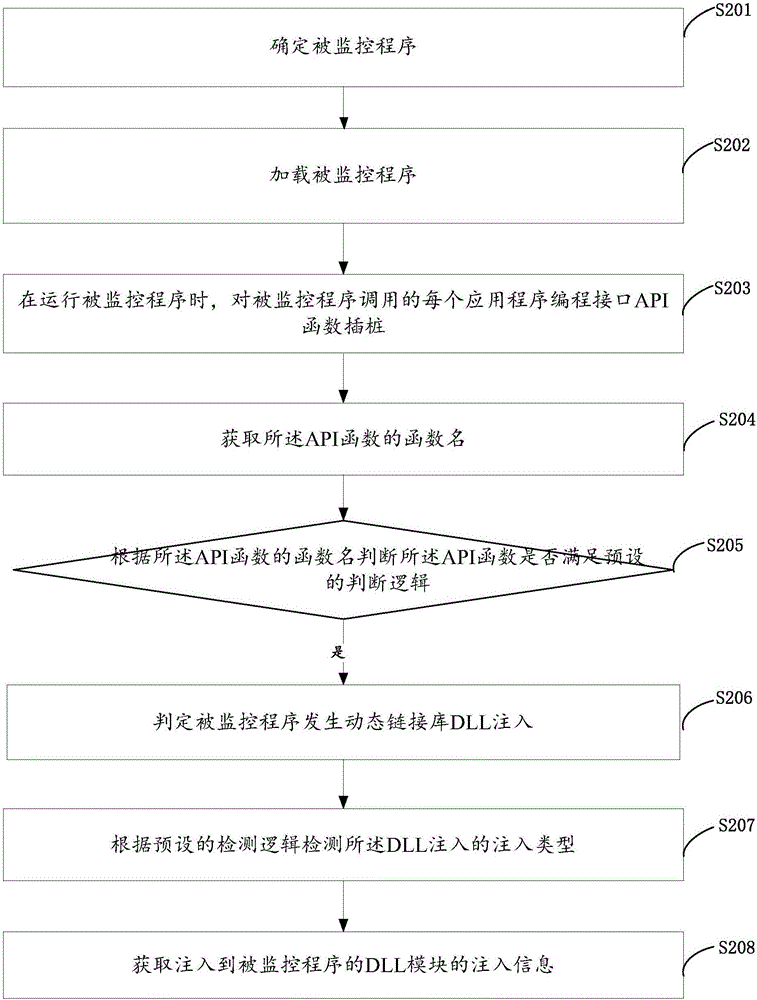
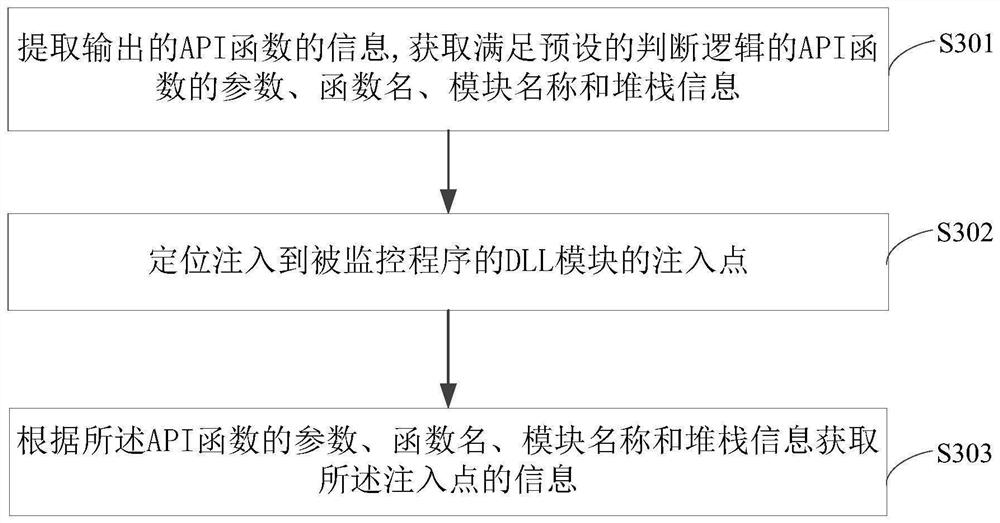
The invention discloses a method and device for monitoring a program and belongs to the technical field of computers. The method includes: loading a to-be-monitored program; during the operation of the to-be-monitored program, performing instrumentation on each application programming interface API function called by the to-be-monitored program; acquiring the function name of each API function; judging whether each API function satisfies preset judging logic or not according to the corresponding function name; if so, judging that the to-be-monitored program has dynamic-link library DLL injection; detecting the injection type of the DLL injection according to preset detecting logic; acquiring injection information. The method has the advantages that whether the to-be-monitored is injected with a DLL module or not and an injection manner can be judged effectively, only the information of the API functions conforming to the logic needs to be output and judged, other API functions are not processed and output, and accordingly monitoring efficiency is increased evidently.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Method and system for injecting DLL into target process
ActiveCN105045605AFull controlImprove concealmentSpecific program execution arrangementsOperational systemEngineering
The invention provides a method and a system for injecting a DLL (Dynamic Link Library) into a target process. A DLL injection module used for monitoring the program start in an operating system is set; the DLL injection module is registered into the operating system; when the target process sends a start request to the operating system, the operating system informs the DLL injection module of the request; and a user inserts a target DLL to be injected into the DLL of the target process according to requirements. The method and the system have the advantages of control comprehensiveness, good concealing performance, high flexibility and the like; the method and the system can be applied to data leaking prevention and can enhance the data protection grade; all non-system key processes can be injected; an injection system explorer technology can be applied to a secure desktop technology; and the method and the system can adapt to various common operating systems such as Windows XP, Windows Server 2003 and Windows 7.
Owner:中电科网络安全科技股份有限公司
Windows process protection method
InactiveCN104123492AImprove stabilityImprove compatibilityPlatform integrity maintainanceCore functionOperational system
The invention discloses a Windows process protection method. According to the Windows process protection method, a dll containing a core function code is injected into a system process to be run through a driver, so that the protected process is monitored. Through the injected dll used as a redirector, a system dynamic link library scesrv.dll can be reloaded to the memory space of the system process services.exe, and then the injected dll can be loaded to the memory space of the system process services.exe along with the system dynamic link library scesrv.dll. According to the Windows process protection method, the stability and the compatibility are high, the implementation difficulty is low, and the invisibility is high; due to the fact that no Patch system code exists, the Windows process protection method is also suitable for the 64-bit Windows operating system.
Owner:蓝盾信息安全技术有限公司
Method for implementing ejection-safe API interception
ActiveUS8255931B2Multiprogramming arrangementsSpecific program execution arrangementsParallel computingApplication software
A DLL that includes an API hook is injected into the address space of a target computer process called by an application program. Upon termination of the application program, computer-readable instructions describing a process for filtering exceptions returned from the target computer process are stored in memory locations accessible to the target computer process and the DLL is ejected from the address space.
Owner:CA TECH INC
Method for protecting mirror image codes based on executable mirror image hiding and dll injection
ActiveCN105512548APrevent dynamic debuggingIncreased protectionComputer security arrangementsProcess functionComputer module
Provided is a method for protecting mirror image codes based on executable mirror image hiding and dll injection. The method comprises the following steps that 1, a target mirror image is decrypted in a memorizer; 2, a PE mirror image is loaded, wherein a dll file needed for a program is loaded, mirror image repositioning is executed, and finally OEP is executed; 3, whether an IAT of an exe module is hijacked or not is checked; 4, a Load Library and a Load Library Ex are actively hijacked, operation in the step 3 is executed on a dll mirror image of a load result, and if judgment is not abnormal, the step 5 is executed; 5, a Create Process function is hijacked, and a protection dll is injected while a subprocess is set up; 6, remote thread injection is carried out, a protected target process is injected in a Ring3 environment, and thread injection of a vicious loader is avoided; 7, a thread (THREAD_PRIORITY_BELOW_NORMAL) with low priority is built, endless loop check is carried out, whether the thread is loaded by a Debugger or not is checked, and checking is carried out once every second.
Owner:XIANGTAN UNIV
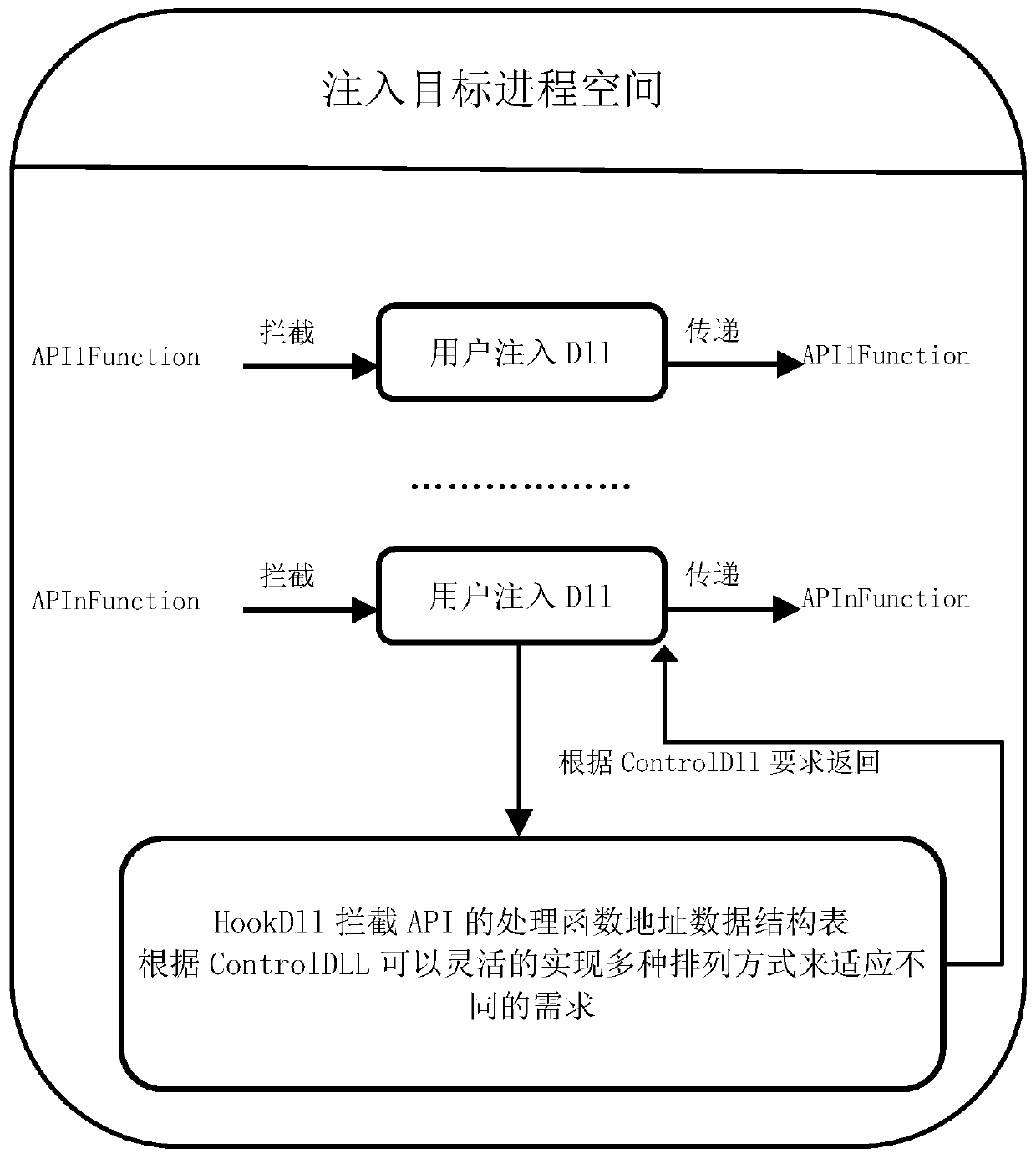
Optimal management method for injecting multi-DLL (dynamic link library) into target procedure
ActiveCN106406852AImprove stabilityImprove efficiencySpecific program execution arrangementsMulti injectionComputer module
The invention discloses an optimal management method for injecting multi-DLL (dynamic link library) into a target procedure. The method comprises the following steps: inserting an APC function in a kernel space by use of an APC mechanism, and additionally adding the optimal management on the injection DLL while injecting the injection execution DLL into the target procedure, and injecting the DLL management module in unification through an unified injection interception mechanism under the condition of needing to inject multi-DLL in the target procedure, thereby improving the target procedure stability and the entire execution efficiency of the interception function. The technical scheme disclosed by the invention has the advantages of being comprehensive in control and high in flexibility, any number of DLL can be injected, and the stability and the efficiency of the target procedure can be obviously improved in particular under the condition of the existence of multi-injection HookDLL; and the execution order of the multi-HookDLL is effectively managed by use of an injection control DLL module (ControlDLL module), the method is flexible and varied, and can be suitable for various places.
Owner:BEIJING VRV SOFTWARE CO LTD
Configurable and integratable Hook system in Windows environment and method thereof
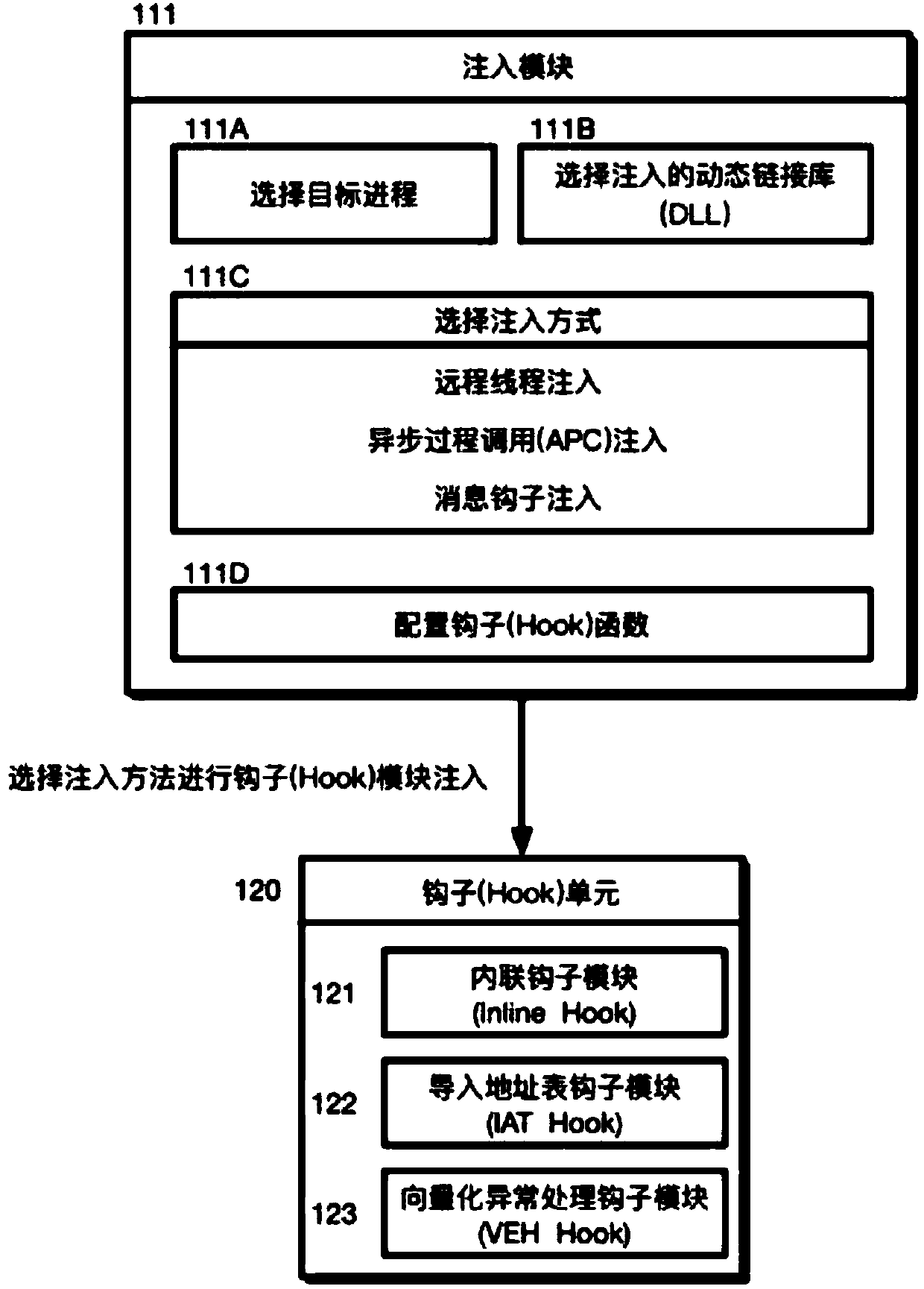
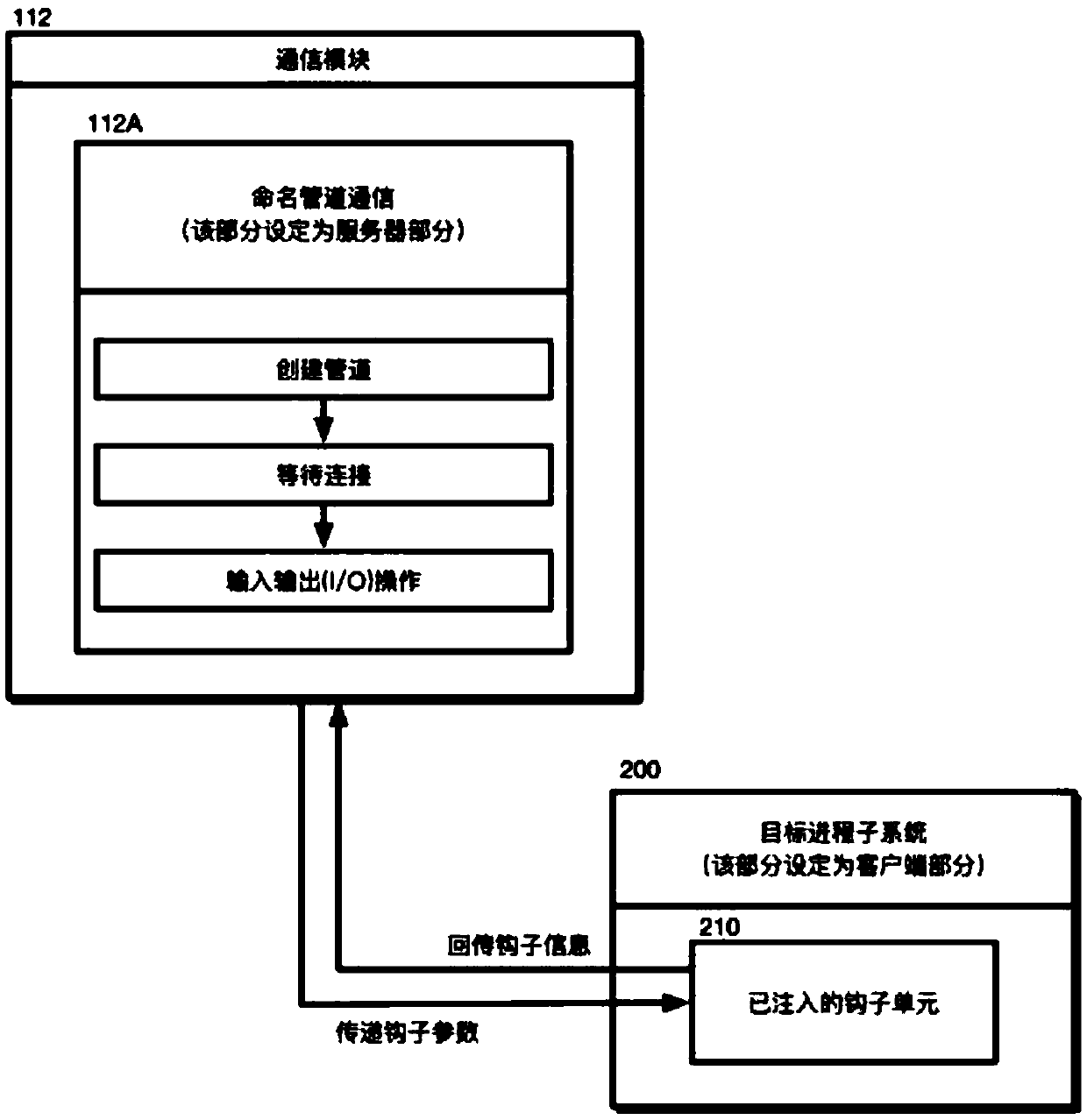
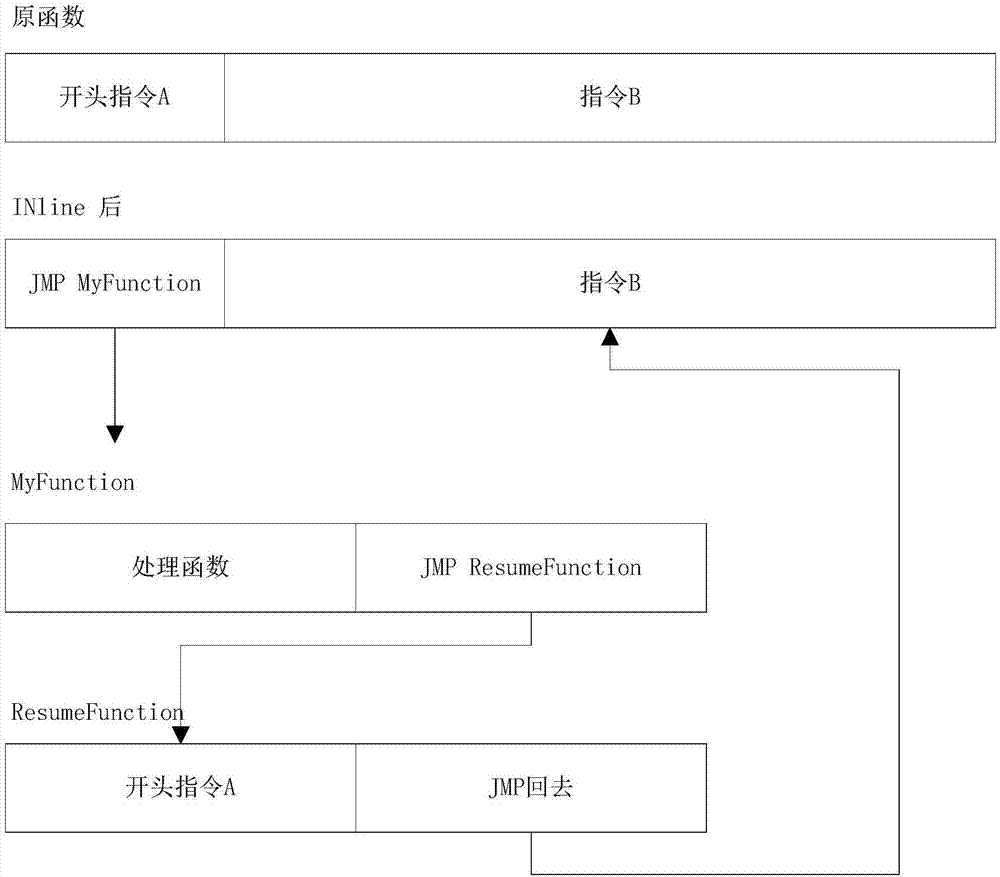
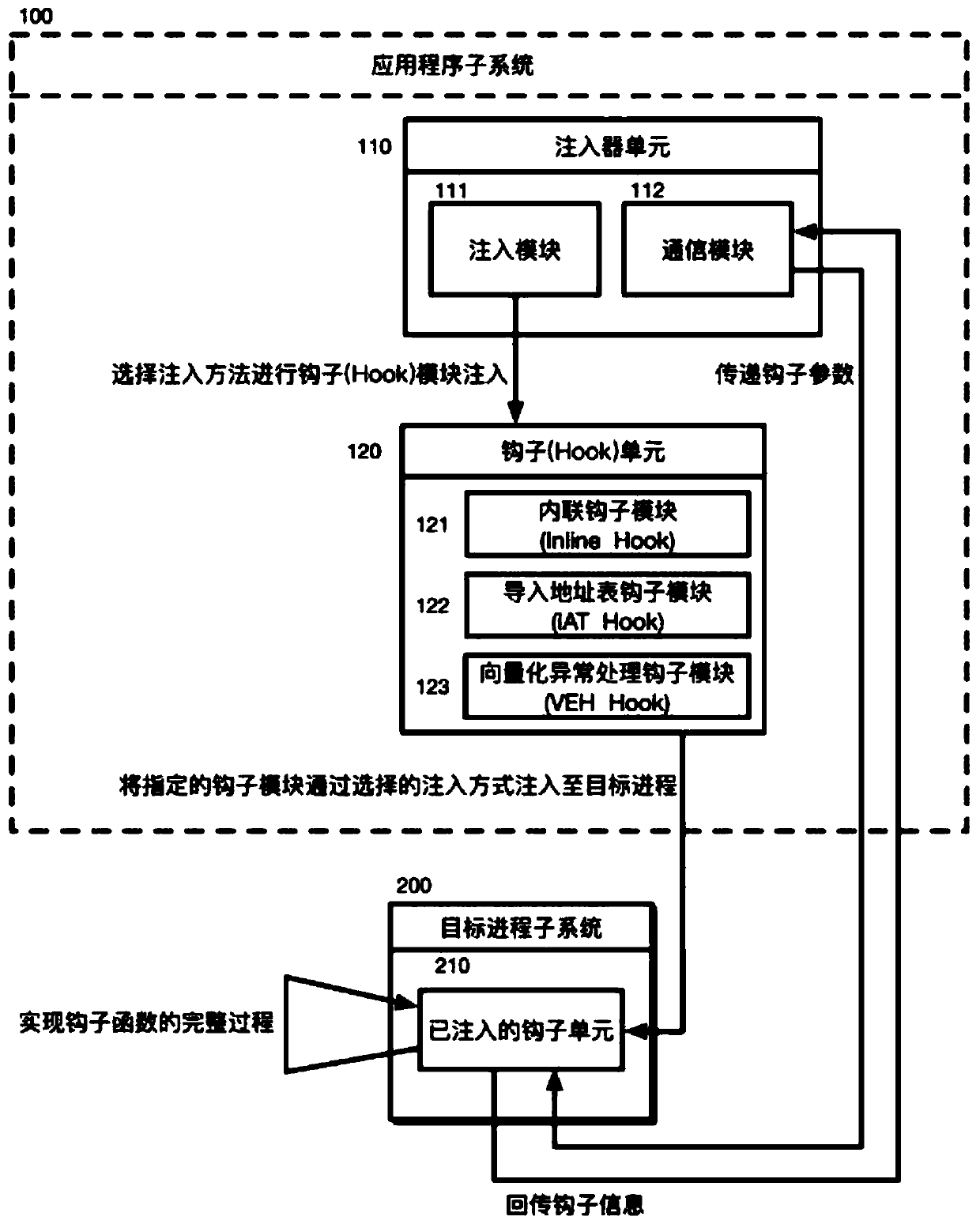
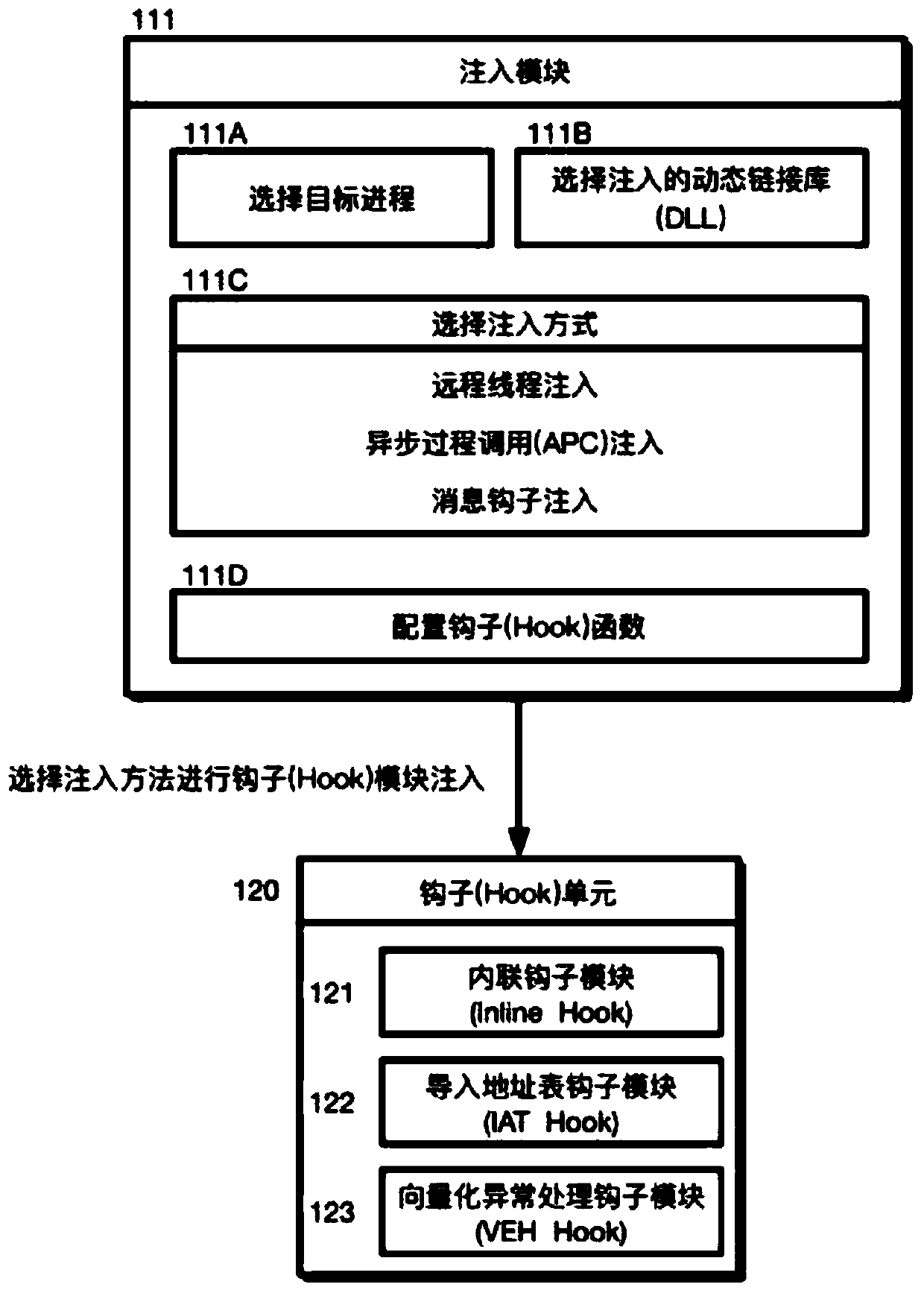
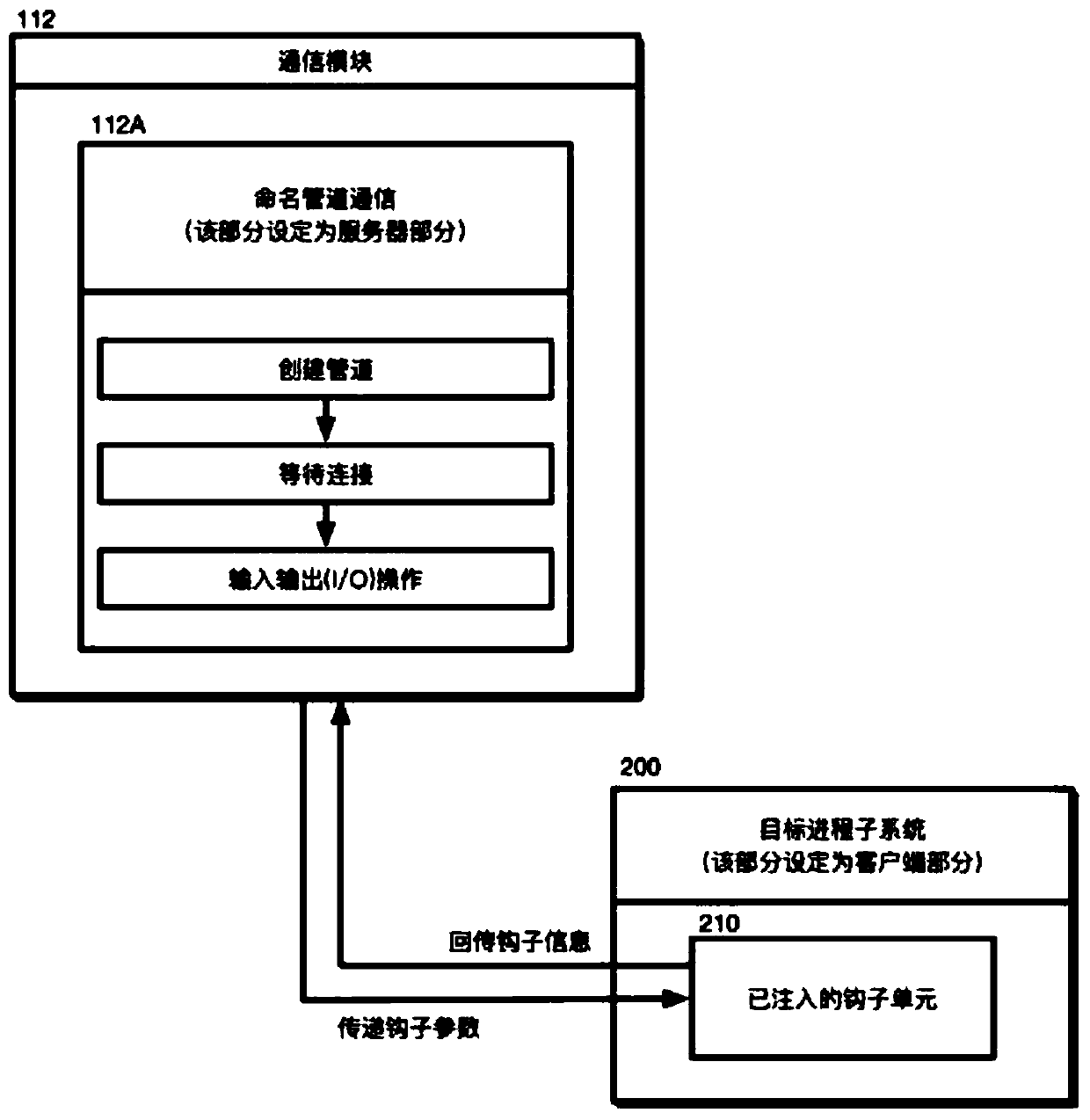
ActiveCN107688747AReduce the difficulty of operationImprove efficiencyPlatform integrity maintainanceComputer moduleInter-process communication
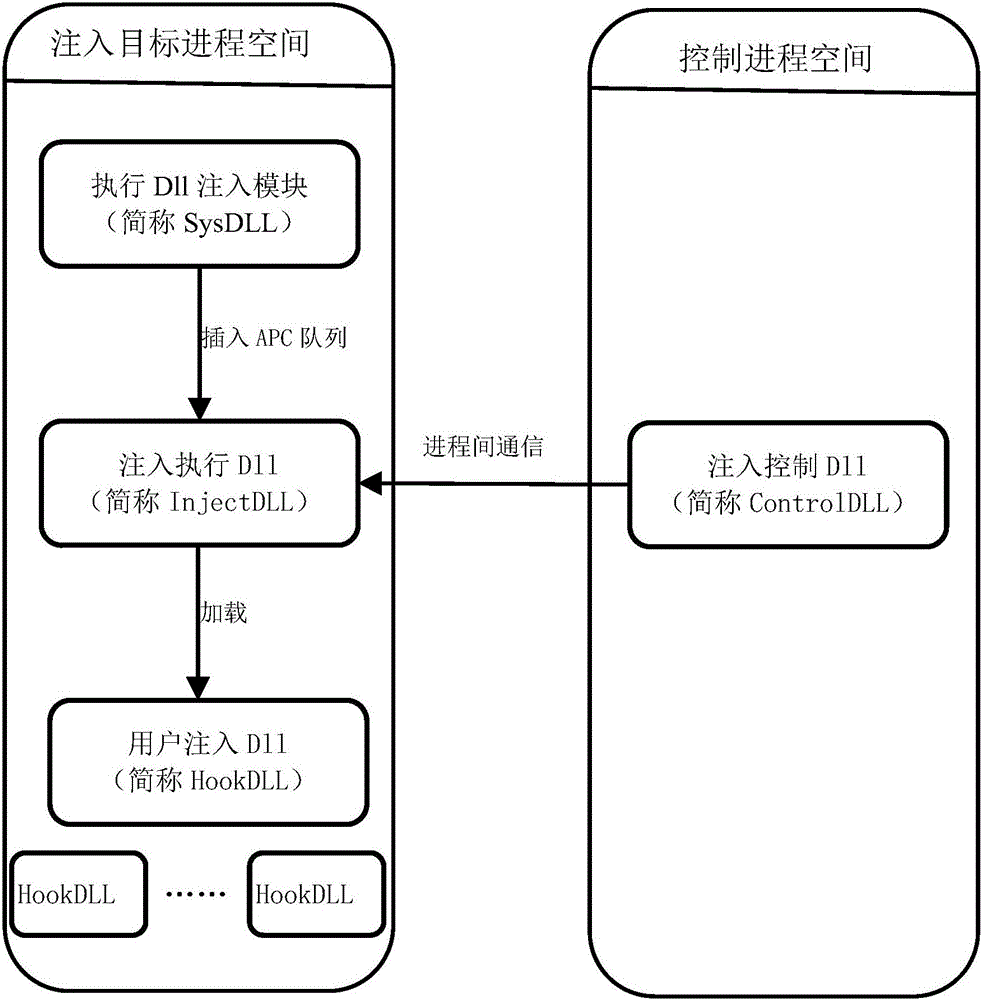
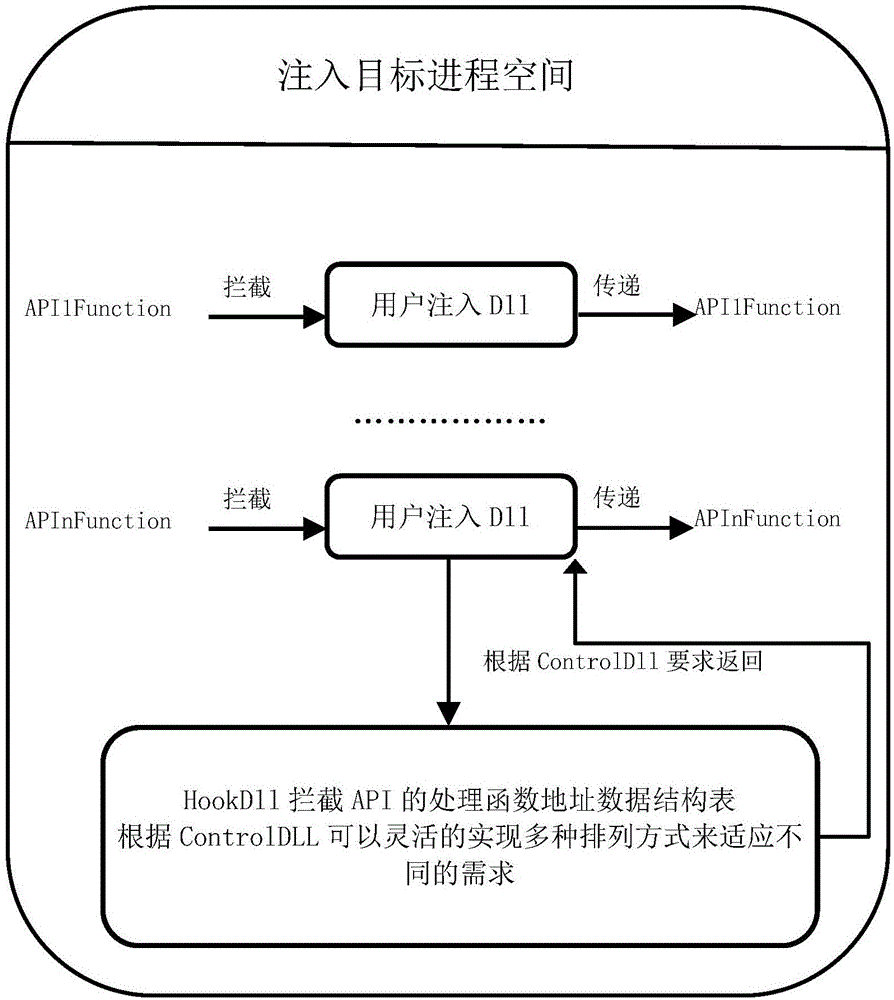
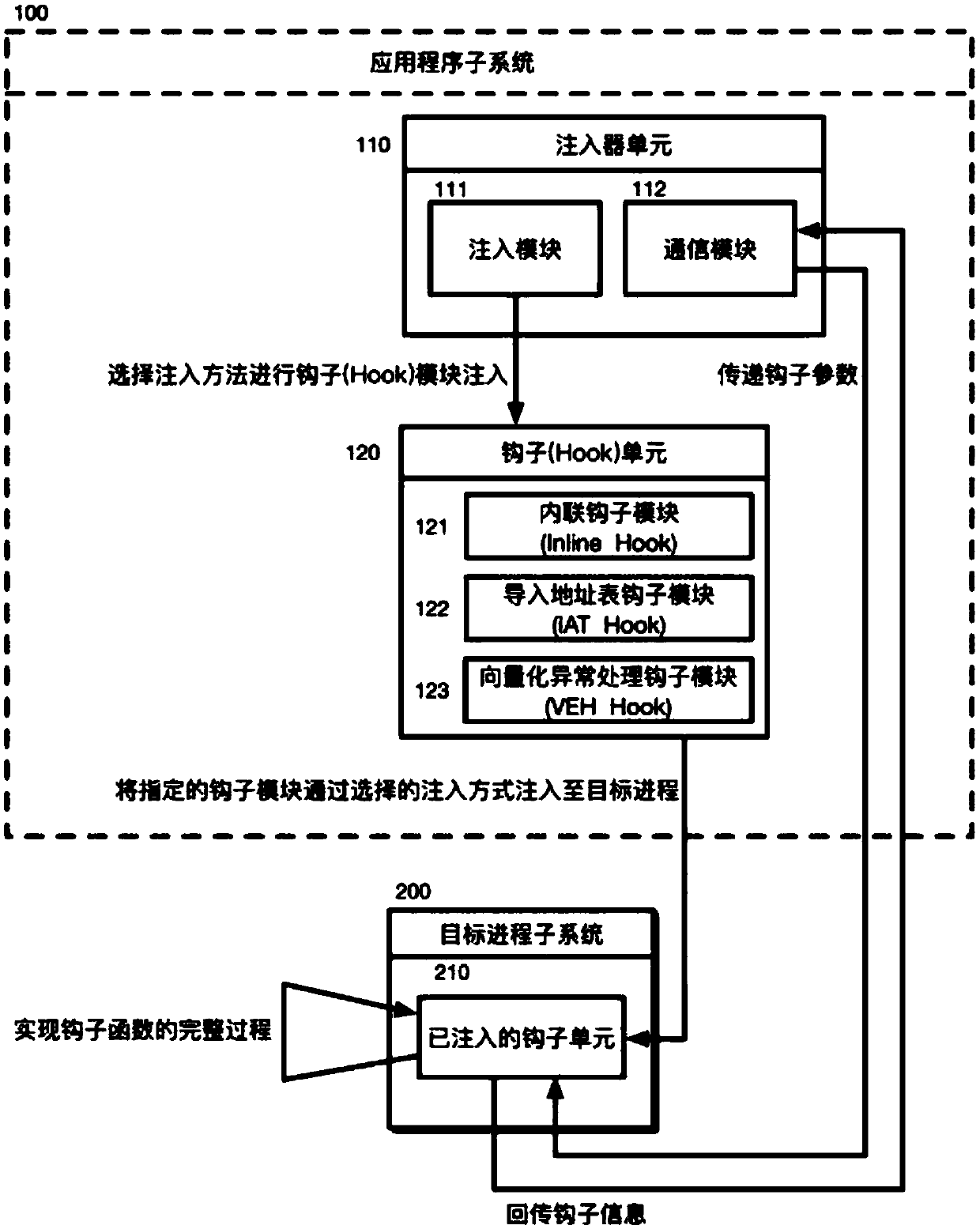
The invention discloses a configurable and integratable Hook system in Windows environment and a method thereof and relates to the technical field of DLL injection technology, Hook technology and interprocess communication. The system is characterized in that an application program subsystem comprises an injector unit and a hook unit, the injector unit comprises an injection module and a communication module, the hook unit comprises an inline hook module, an import address table hook module and a vectored exception handling module, and the injection module, the hook unit, an injected hook unitand the communication module sequentially interact. The method includes: 1, creating a naming pipeline; 2, selecting a target process; 3, selecting a dynamic link library for injection; 4, selectingan injection mode; 5, feeding back injection information; 6, configuring Hook parameters; 7, transmitting the Hook parameters to the injected hook unit; 8, completing Hook functional procedure; 9, feeding back Hook information. The system is configurable, and related process parameters of Hook can be configured by a user; the system has the characteristic of being easy to operate and can help to intercept and acquire enough useful information.
Owner:武汉倚天剑科技有限公司
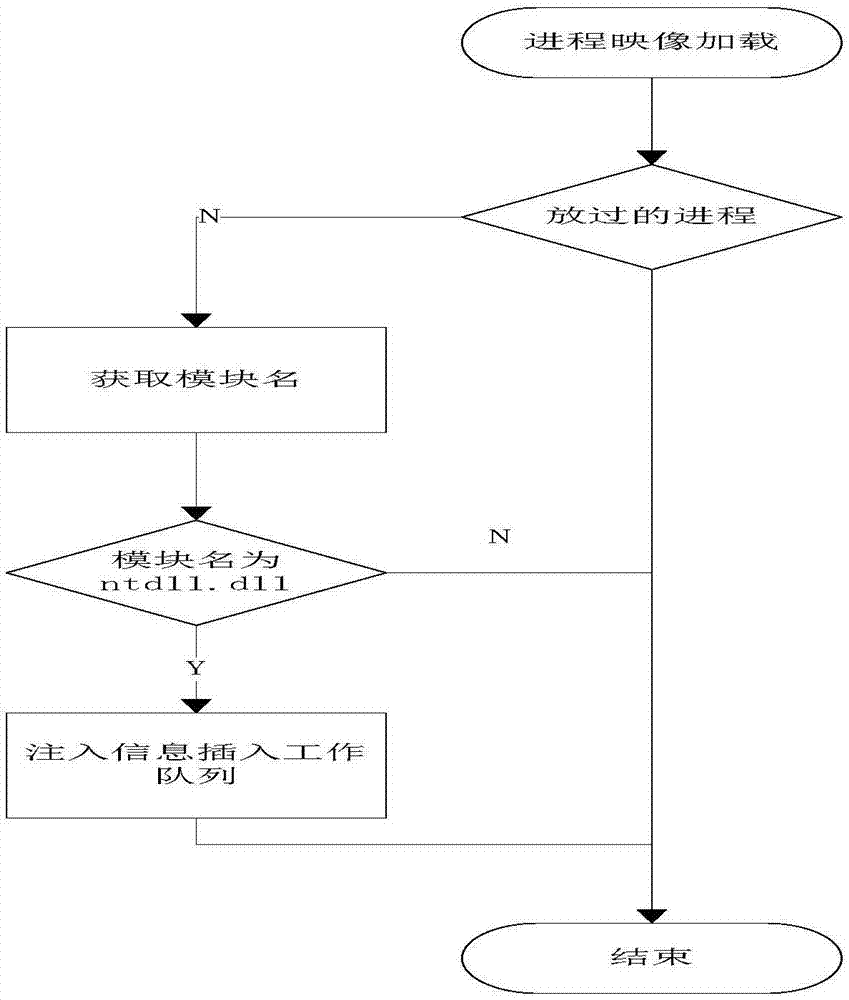
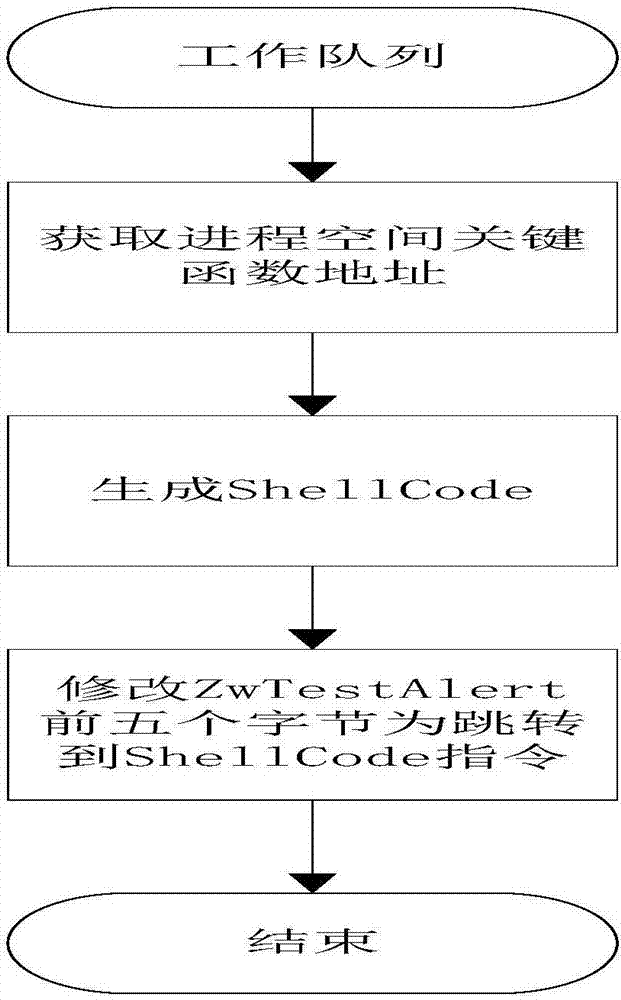
DLL injection method and system based on Windows platform
ActiveCN107479874AInject morePlatform integrity maintainanceExecution paradigmsComputer scienceSoftware
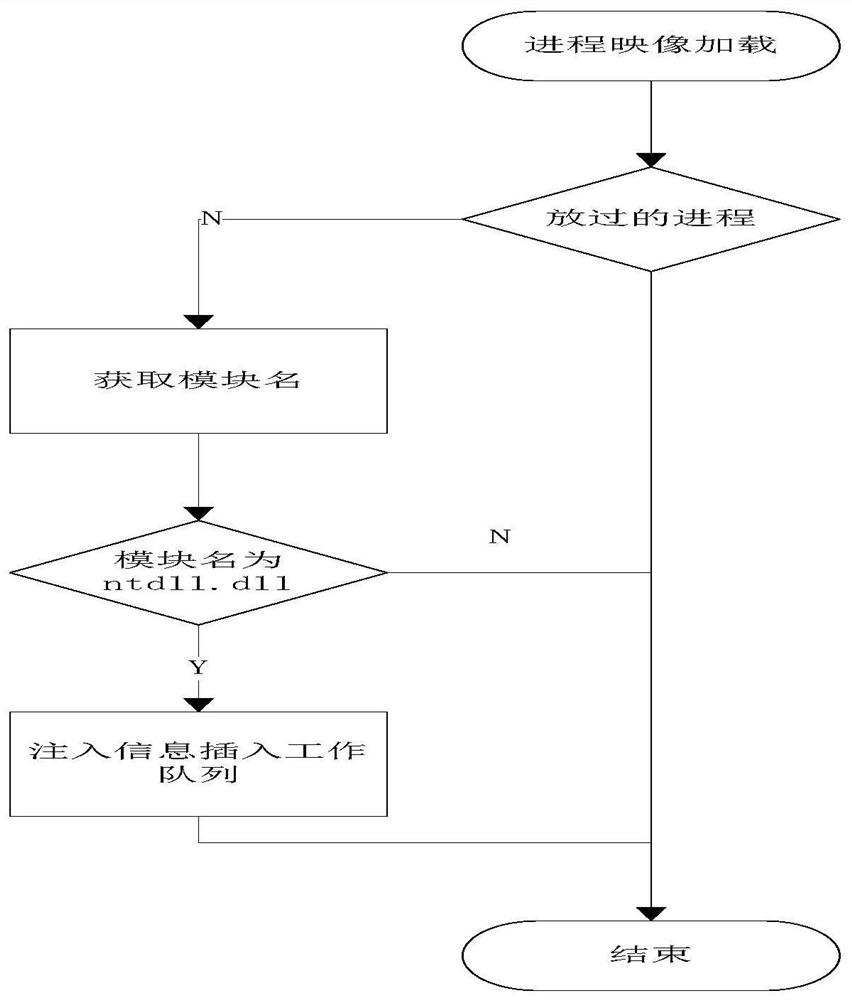
The invention discloses a DLL injection method and system based on a Windows platform. The method comprises the following steps that a process is stared, whether safety detection DLL needs to be injected to the process or not is judged, and if yes, a module name requiring the safety detection DLL injection is obtained; whether the module name is 'ntdll.dll' or not is judged, and if yes, the injection information of a current process is inserted into a work queue; the safety detection DLL conducts safety detection on the current process; if unsafe according to the detection, the current process is ended, and if safe, the current process is allowed to be started. According to the DLL injection method and system based on the Windows platform, more processes can be injected, antivirus software does not kill the processes by mistake, and the DLL injection method and system is more stable and more efficient.
Owner:北京明朝万达科技股份有限公司
Method To Protect Application Running In A Hostile Environment
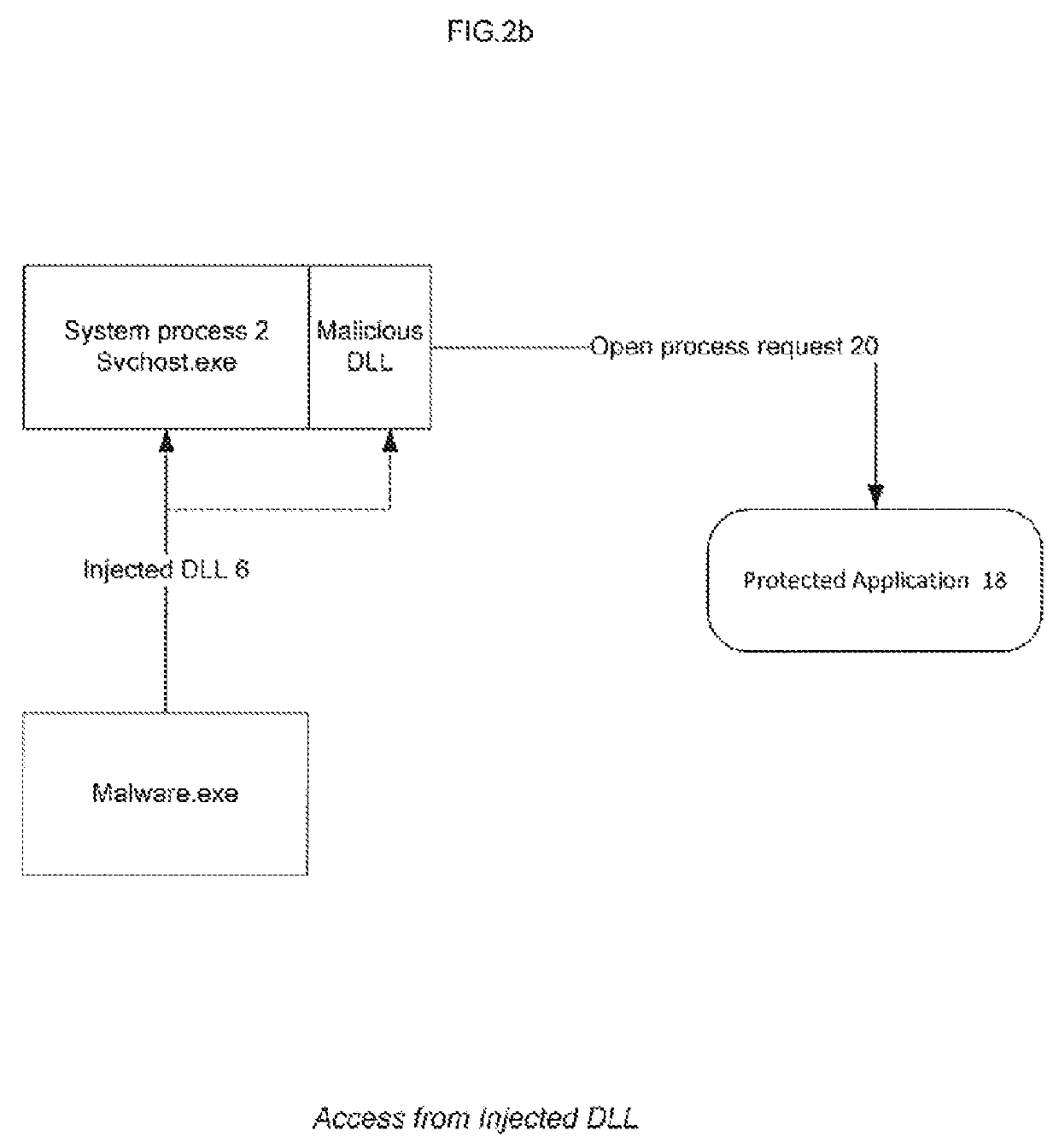
There is provided a method to protect applications running in a hostile environment, including against trampoline based attacks which use dll injection and code modification. The method includes protecting an application when access is performed from injected dll, and protecting the application when access is performed from modified codes.
Owner:COMODO SECURITY SOLUTIONS
A cloud game data acquisition method and system
InactiveCN109840058AAchieve captureImprove experienceProgram loading/initiatingVideo gamesVideo memoryData acquisition
The invention discloses a cloud game data collection method and system, and relates to the field of cloud games, and the method comprises the following steps: injecting a customized DLL into a targetgame process, and inserting a customized MyEndScence function for collecting data into a Direct3D rendering pipeline; Enabling the target game process to skip to a MyEndScence function, and copying abackend cache Buffer of the target game from a video memory of a video card to a memory to obtain original RGB pixel data and encode the original RGB pixel data. According to the cloud game data collection method, data collection does not depend on SDK provided by a display card manufacturer, time delay can be shortened, and user experience can be improved.
Owner:FENGHUO COMM SCI & TECH CO LTD
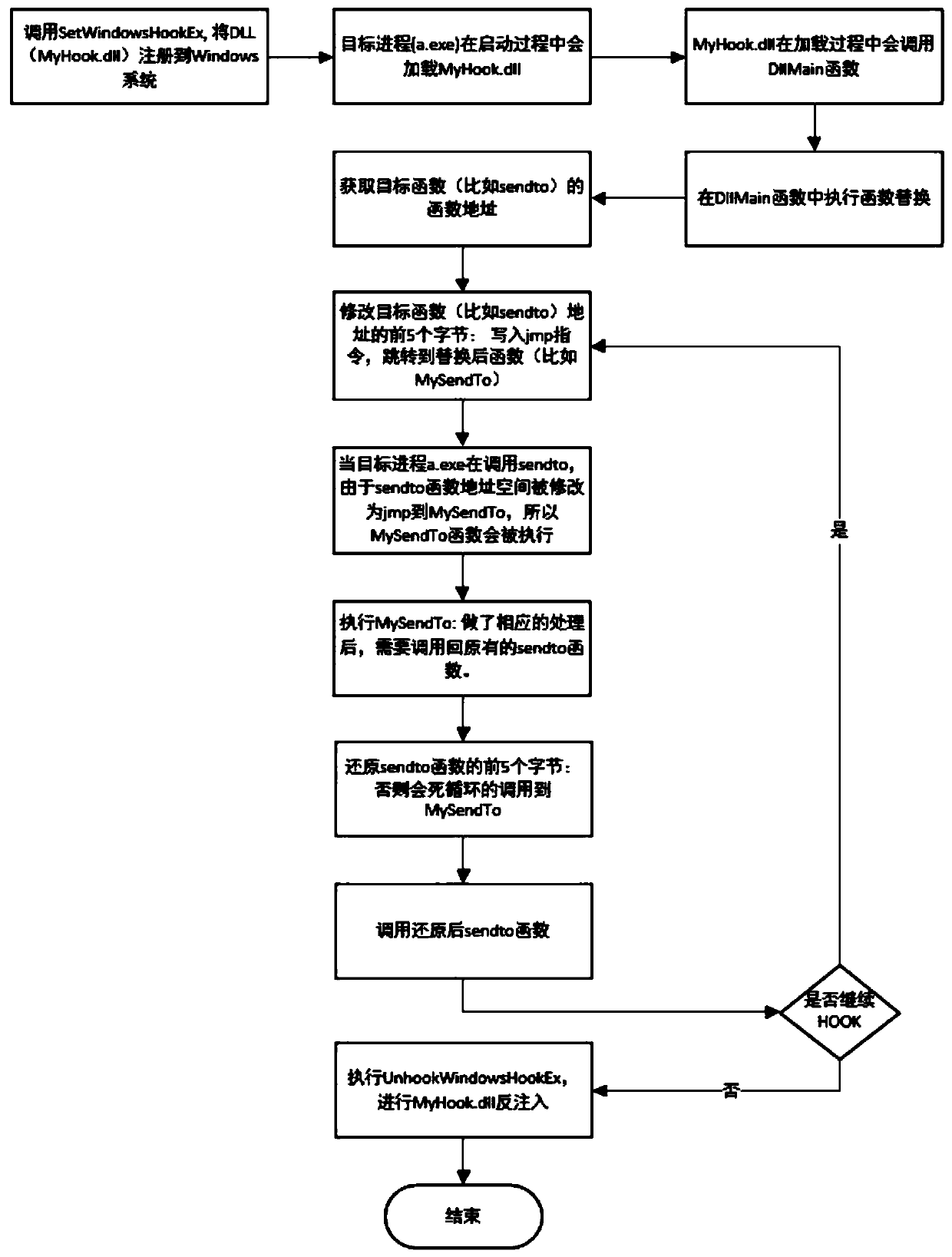
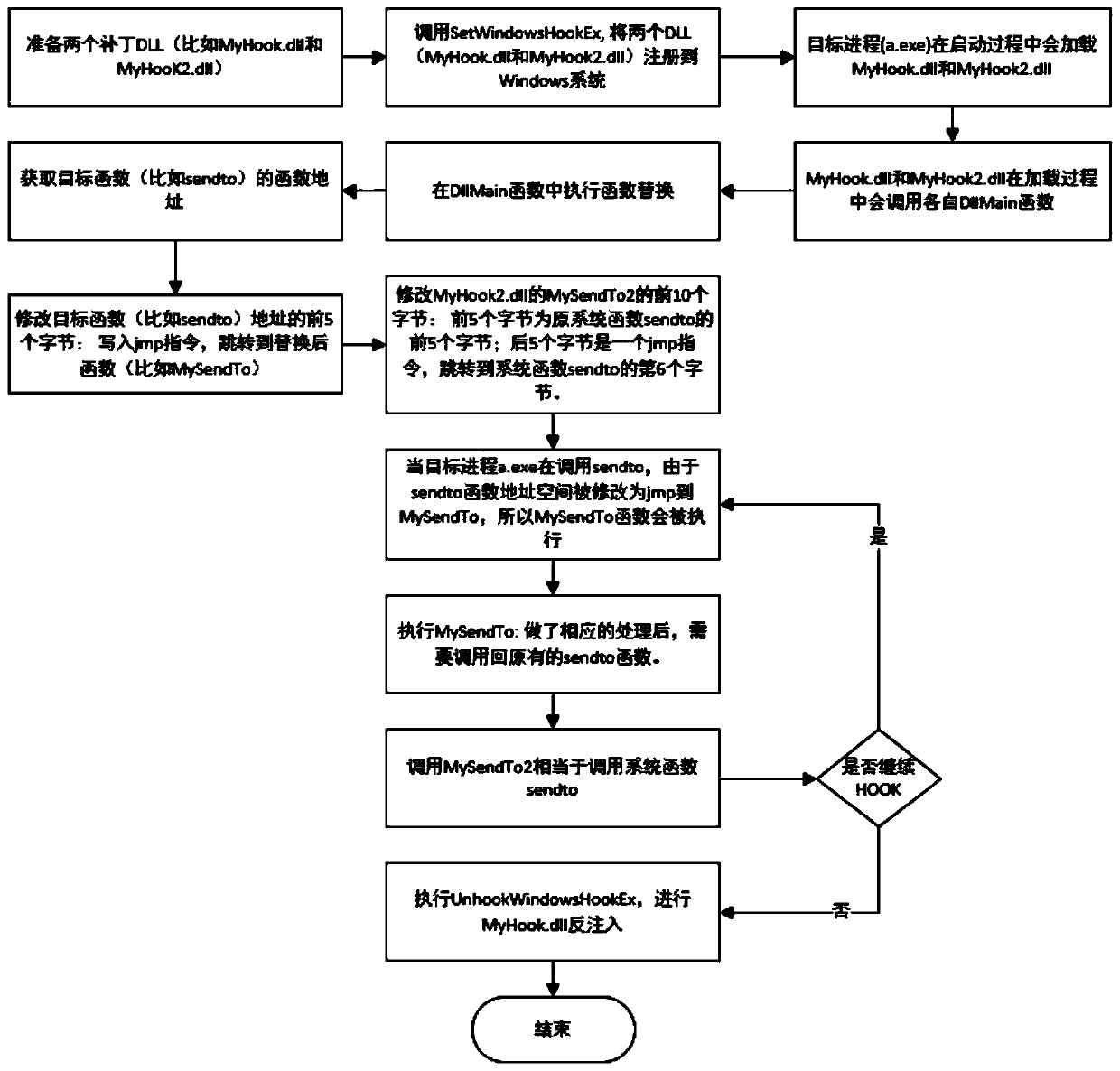
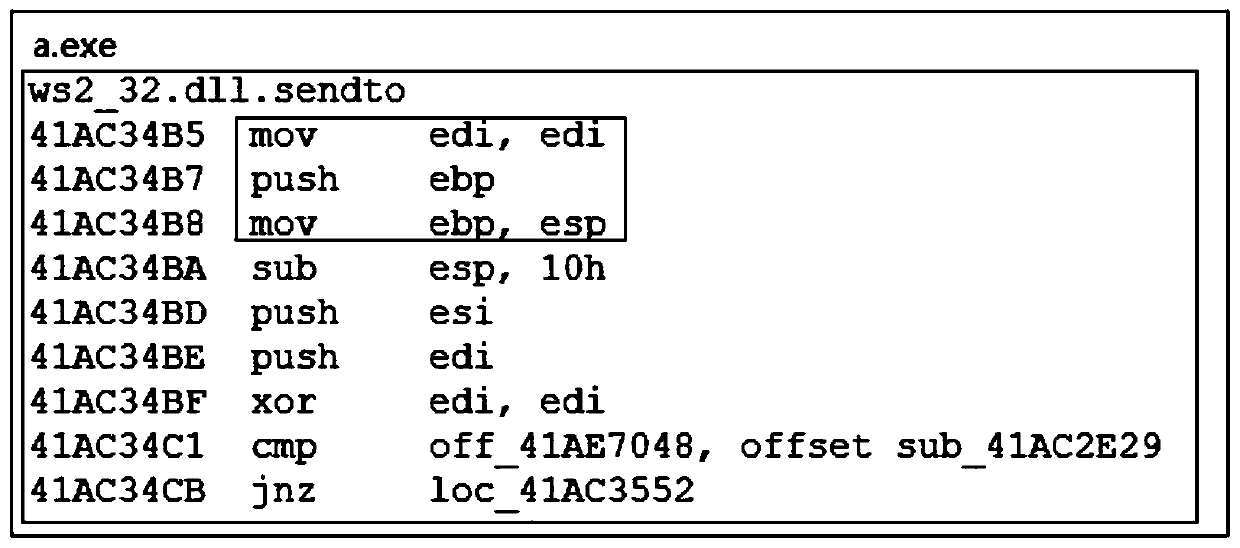
method for realizing a function hot patch through a HOOK technology under Windows
InactiveCN109766145ASolve repeated replacementSolve the problem of restoring function sceneProgram loading/initiatingJumping functionComputer science
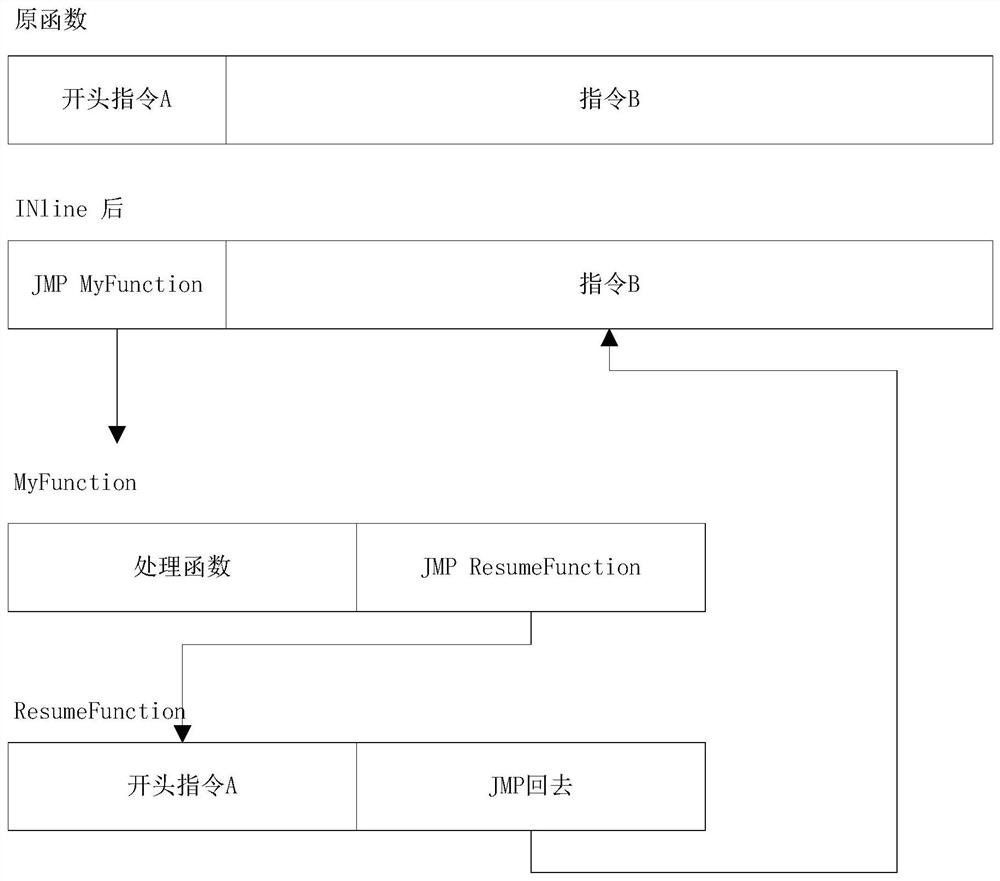
The invention discloses a method for realizing a function hot patch under Windows through HOOK technology, which relates to the technical field of communication and comprises the following steps of: preparing two patches DLL, one patch DLL is a true patch DLL containing a replacement function, and the other patch DLL is a false patch DLL containing a jump function; Injecting the two patches DLL into the target process; Modifying a system function to enable the system function to skip to a replacement function; And executing the jump function, jumping back to the system function, and continuingexecution of the system function API. According to the invention, unnecessary performance loss is reduced, and the HOOK accuracy is improved.
Owner:杭州云缔盟科技有限公司
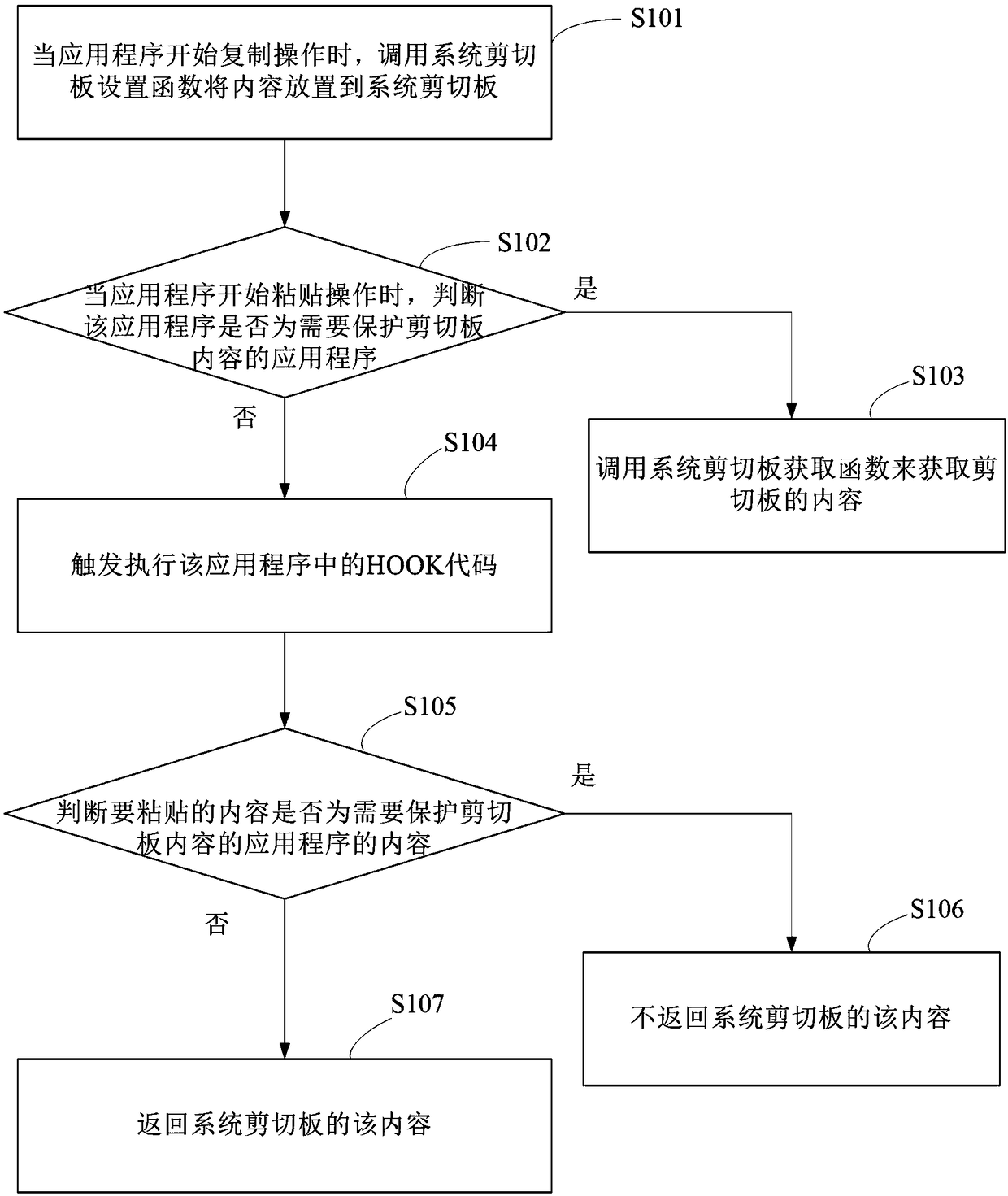
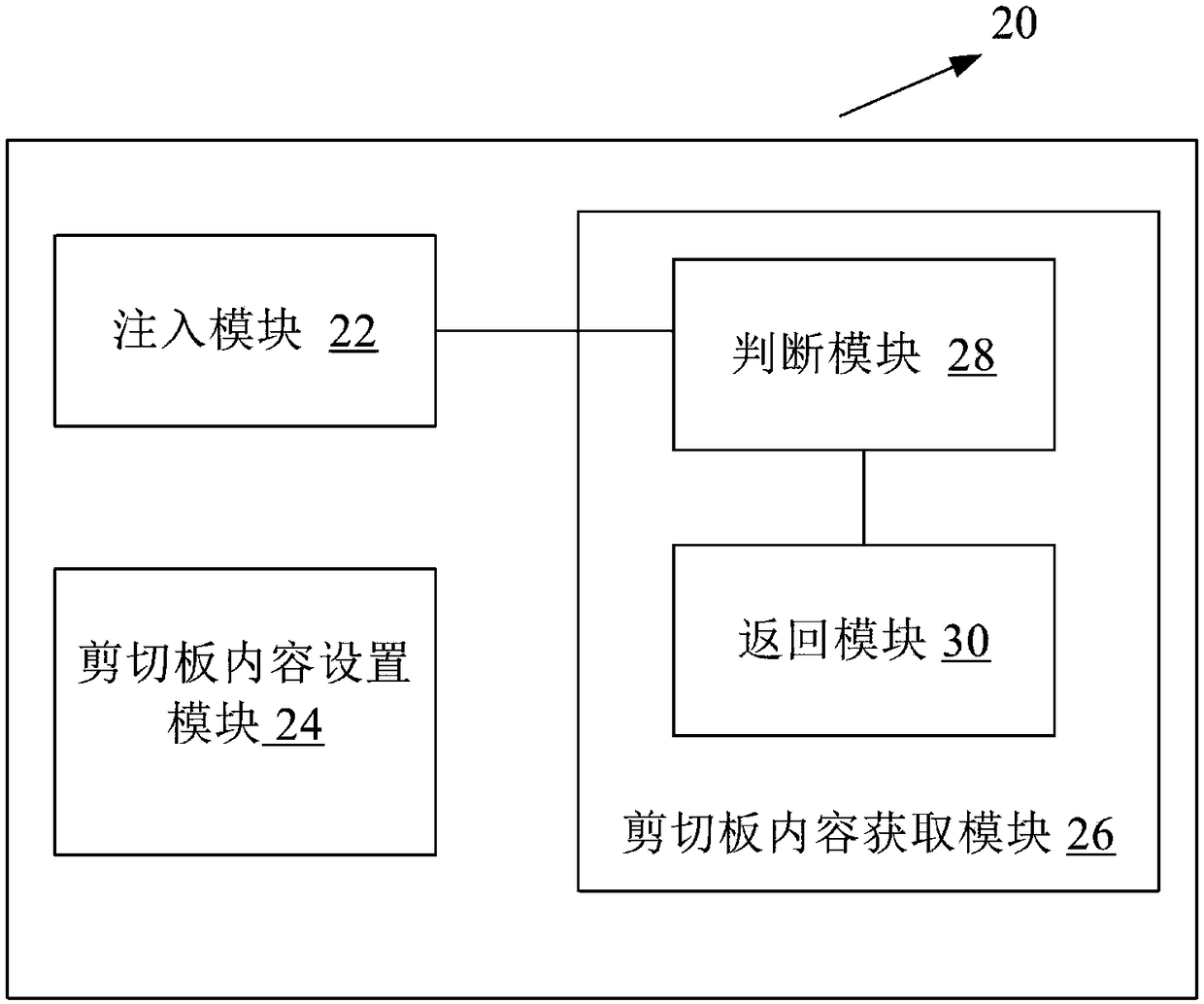
A method and apparatus for preventing data leakage from a clipboard
ActiveCN109409098APrevent leakageImprove securityInterprogram communicationDigital data protectionApplication softwareDatabase
The invention discloses a method for preventing data leakage of a clipboard. The method comprises injecting and executing a HOOK code by using a dynamic link library DLL in an application program. When the application program starts copying operation, triggering the execution of the clipboard setting function inside the HOOK to set the format and content of the internal clipboard, and placing theclipboard into the queue inside the HOOK correspondingly; when the application program starts pasting operation, triggering the execution of a clipboard obtaining function inside HOOK, querying the corresponding clipboard content from the HOOK internal queue according to the clipboard format, and returning the corresponding content of the clipboard format when the corresponding clipboard content is queried. Accordingly, the invention also discloses a device for preventing data leakage of a shear board. Embodiments of the present invention can prevent data disclosure due to the contents of thesystem clipboard being listened to and invoked by other applications.
Owner:浙江华途信息安全技术股份有限公司
A method and system for injecting dll into target process
ActiveCN105045605BFull controlImprove concealmentPlatform integrity maintainanceEngineeringDLL injection
Owner:中电科网络安全科技股份有限公司
Method of protecting image code based on hiding executable image and injecting dll
ActiveCN105512548BPrevent dynamic debuggingIncreased protectionComputer security arrangementsProcess functionComputer module
Provided is a method for protecting mirror image codes based on executable mirror image hiding and dll injection. The method comprises the following steps that 1, a target mirror image is decrypted in a memorizer; 2, a PE mirror image is loaded, wherein a dll file needed for a program is loaded, mirror image repositioning is executed, and finally OEP is executed; 3, whether an IAT of an exe module is hijacked or not is checked; 4, a Load Library and a Load Library Ex are actively hijacked, operation in the step 3 is executed on a dll mirror image of a load result, and if judgment is not abnormal, the step 5 is executed; 5, a Create Process function is hijacked, and a protection dll is injected while a subprocess is set up; 6, remote thread injection is carried out, a protected target process is injected in a Ring3 environment, and thread injection of a vicious loader is avoided; 7, a thread (THREAD_PRIORITY_BELOW_NORMAL) with low priority is built, endless loop check is carried out, whether the thread is loaded by a Debugger or not is checked, and checking is carried out once every second.
Owner:XIANGTAN UNIV
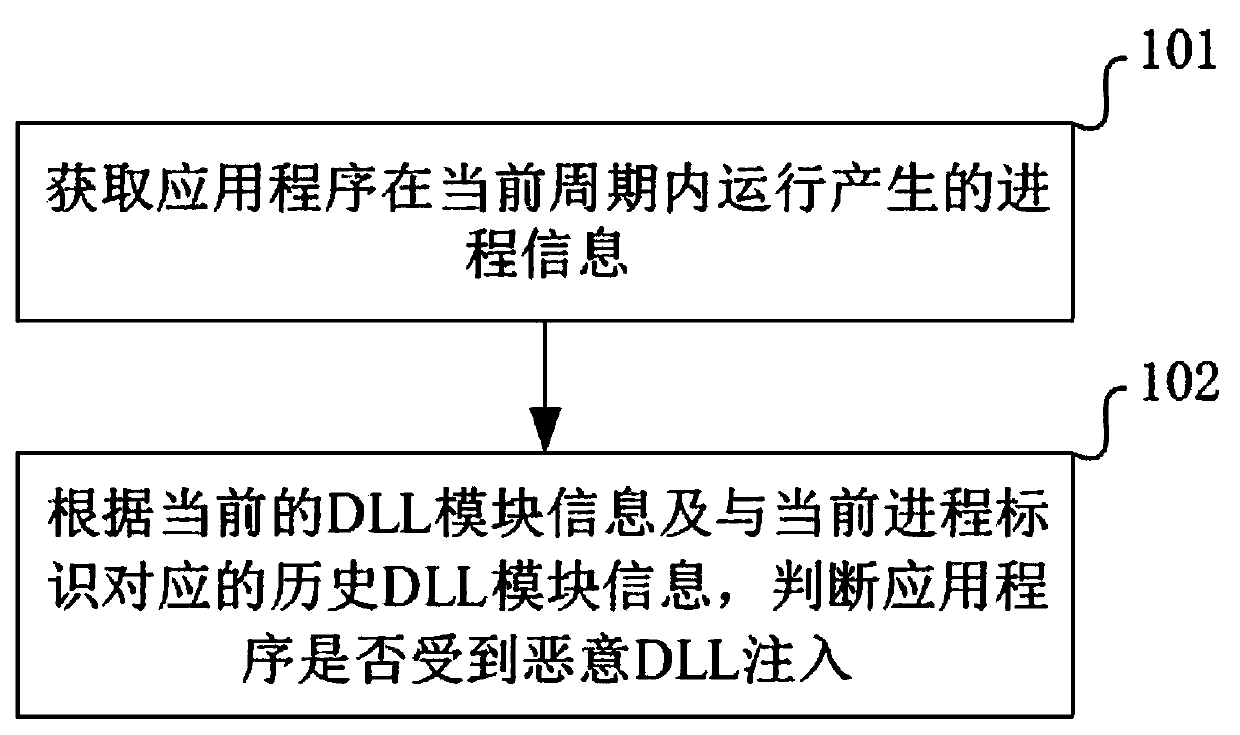
Malicious DLL injection detection method and device
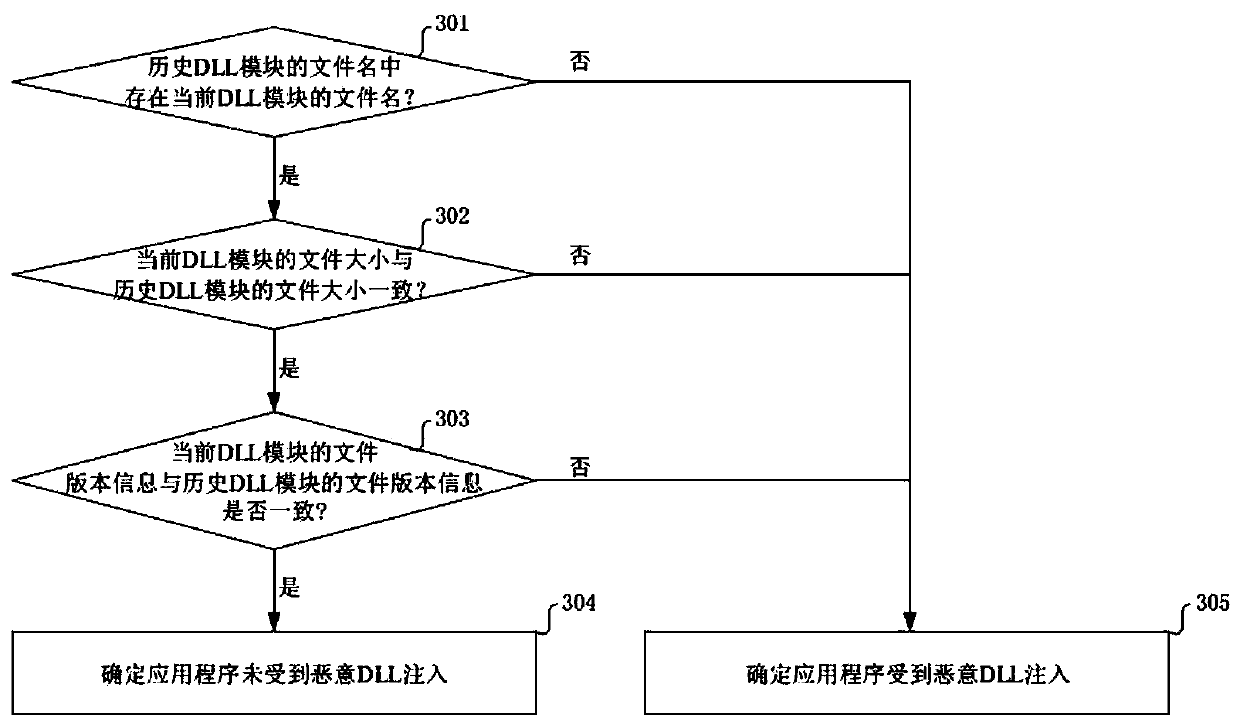
InactiveCN111159707AGuaranteed uptimeImprove operational safetyPlatform integrity maintainanceApplication procedureFailure causes
The invention provides a malicious DLL injection detection method and device. The method comprises the steps that process information generated when an application program runs in a current period isobtained, and the process information comprises a current process identifier and current DLL module information corresponding to the current process identifier; and then, according to the current DLLmodule information and historical DLL module information corresponding to the current process identifier, whether the application is subjected to malicious DLL injection or not is judged, the historical DLL module information is generated when the application runs in a historical period, and the historical period is a period before the current period in time dimension. Therefore, malicious DLL injection can be discovered in time, so that the problem of application running failure caused by damage of the normally running application can be avoided, and the running safety of the application is improved.
Owner:BEIJING ANBOTONG TECH CO LTD
Cross-process data capturing method of desktop application program
InactiveCN107741862AImprove reusabilityLow costInterprogram communicationSpecific program execution arrangementsData displayData scraping
The invention provides a cross-process data capturing method of a desktop application program. The method of the invention includes: adopting a message hooking function provided by Windows to carry out DLL injection, running code of a local side in the program of another side, and carrying out API hooking through modifying entry addresses of Windows APIs to acquire all data displayed by the program of the another side on an interface. According to the cross-process data capturing method of the desktop application program provided by the invention, systems to which the method can adapt are many, reusability is high, and costs are low.
Owner:CHANGSHA BIOVISION SOFTWARE TECH CO LTD
Method to protect application running in a hostile environment
There is provided a method to protect applications running in a hostile environment, including against trampoline based attacks which use dll injection and code modification. The method includes protecting an application when access is performed from injected dll, and protecting the application when access is performed from modified codes.
Owner:COMODO SECURITY SOLUTIONS
A Configurable and Integrated Hook System and Its Method in Windows Environment
The invention discloses a configurable and integratable Hook system in Windows environment and a method thereof and relates to the technical field of DLL injection technology, Hook technology and interprocess communication. The system is characterized in that an application program subsystem comprises an injector unit and a hook unit, the injector unit comprises an injection module and a communication module, the hook unit comprises an inline hook module, an import address table hook module and a vectored exception handling module, and the injection module, the hook unit, an injected hook unitand the communication module sequentially interact. The method includes: 1, creating a naming pipeline; 2, selecting a target process; 3, selecting a dynamic link library for injection; 4, selectingan injection mode; 5, feeding back injection information; 6, configuring Hook parameters; 7, transmitting the Hook parameters to the injected hook unit; 8, completing Hook functional procedure; 9, feeding back Hook information. The system is configurable, and related process parameters of Hook can be configured by a user; the system has the characteristic of being easy to operate and can help to intercept and acquire enough useful information.
Owner:武汉倚天剑科技有限公司
A dll injection method and system under windows platform
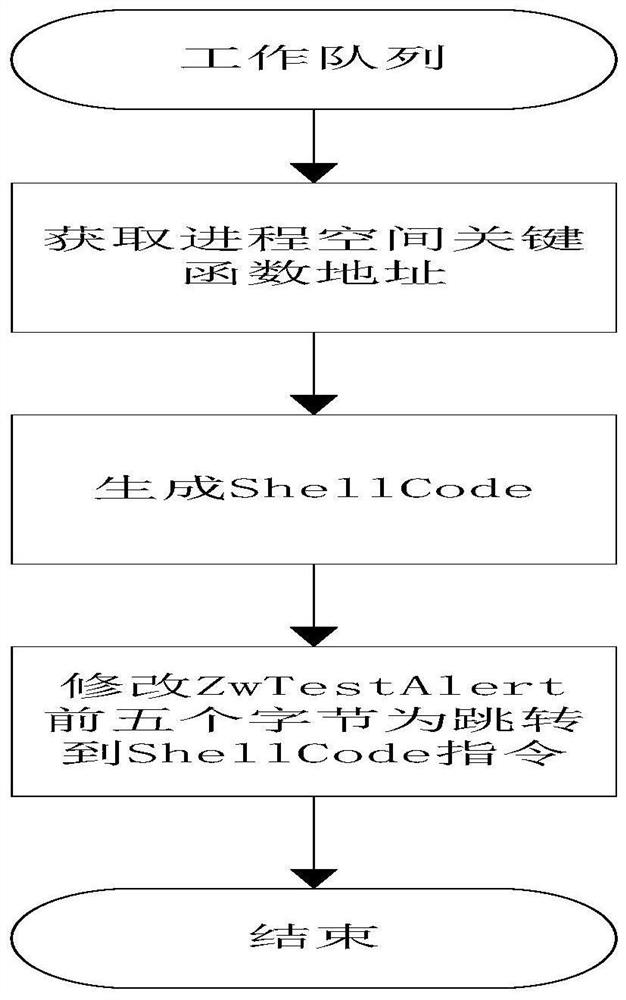
ActiveCN111475229BLess restrictiveIncrease success ratePlatform integrity maintainanceProgram loading/initiatingSoftware engineeringShellcode
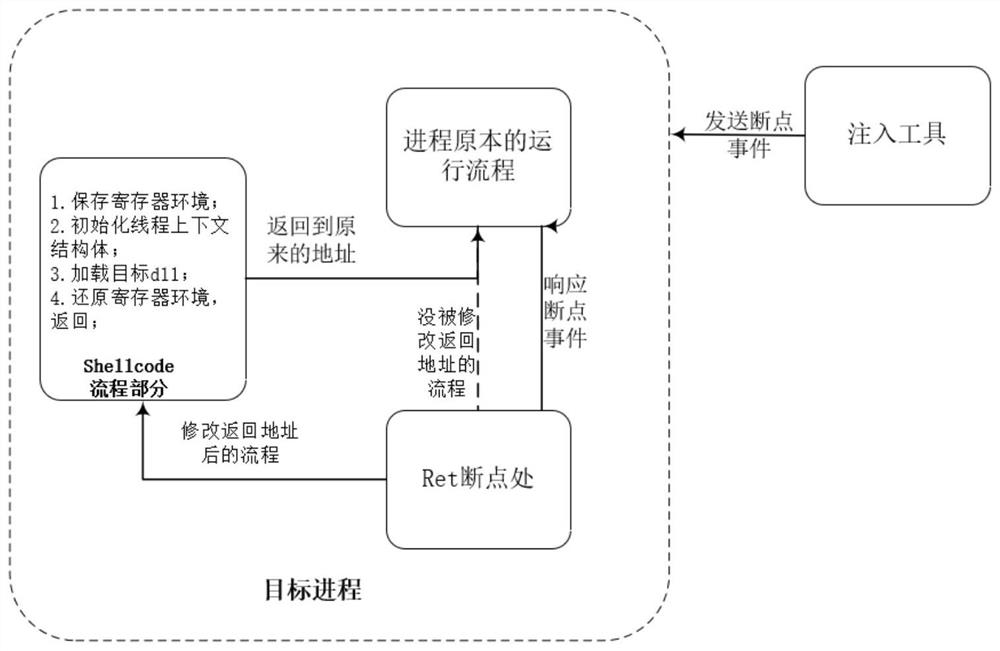
The invention relates to a dll injection method and system under a Windows platform. The dll injection method comprises the following steps: S01, preparing an injection program; S02, improving the authority of the operator; S03, sending a breakpoint event to a target process; S04, enabling the target process to respond to the breakpoint event; S05, running the target process to the breakpoint, suspending the program, storing the return address of the stack, and modifying the return address into the address of the injection program; S06, correcting the code of the injection program, and returning the code to the original return address after the code is executed; S07, enabling the target program continues to run and returning to the injection program part, and completing dll injection afterthe injection program runs; S08, enabling the target program to skip to the stored return address to continue to run, by sending the breakpoint event to the target program, modifying the breakpoint return address and skipping to the shellcode to complete dll injection. Therefore, the problem that in the prior art, dll injection cannot be conducted on the running process is solved, the success rate is high, and limited conditions are few.
Owner:广州锦行网络科技有限公司
Method and device for monitoring program
ActiveCN106709325BImprove monitoring efficiencyImprove efficiencyPlatform integrity maintainanceApplication programming interfaceSoftware engineering
The invention discloses a method and device for monitoring a program and belongs to the technical field of computers. The method includes: loading a to-be-monitored program; during the operation of the to-be-monitored program, performing instrumentation on each application programming interface API function called by the to-be-monitored program; acquiring the function name of each API function; judging whether each API function satisfies preset judging logic or not according to the corresponding function name; if so, judging that the to-be-monitored program has dynamic-link library DLL injection; detecting the injection type of the DLL injection according to preset detecting logic; acquiring injection information. The method has the advantages that whether the to-be-monitored is injected with a DLL module or not and an injection manner can be judged effectively, only the information of the API functions conforming to the logic needs to be output and judged, other API functions are not processed and output, and accordingly monitoring efficiency is increased evidently.
Owner:TENCENT TECH (SHENZHEN) CO LTD
A dll injection method and system based on windows platform
ActiveCN107479874BInject morePlatform integrity maintainanceExecution paradigmsEngineeringEmbedded system
The invention discloses a DLL injection method and system based on a Windows platform. The method includes the following steps: starting a process, judging whether the current process needs to inject a safety detection DLL, and if so, obtaining the module name that needs to be injected into the safety detection DLL; judging the module Whether the name is "ntdll.dll", if yes, insert the injection information of the current process into the work queue; the safety detection DLL performs safety detection on the current process; if it is detected to be unsafe, it ends, and if it is safe, the current process is allowed to start. Through the solution of the present invention, more processes can be injected, and anti-virus software will not be accidentally killed, which is more stable and efficient.
Owner:北京明朝万达科技股份有限公司
Method and device for injecting custom dll into target process
Owner:GUANGZHOU HUADUO NETWORK TECH
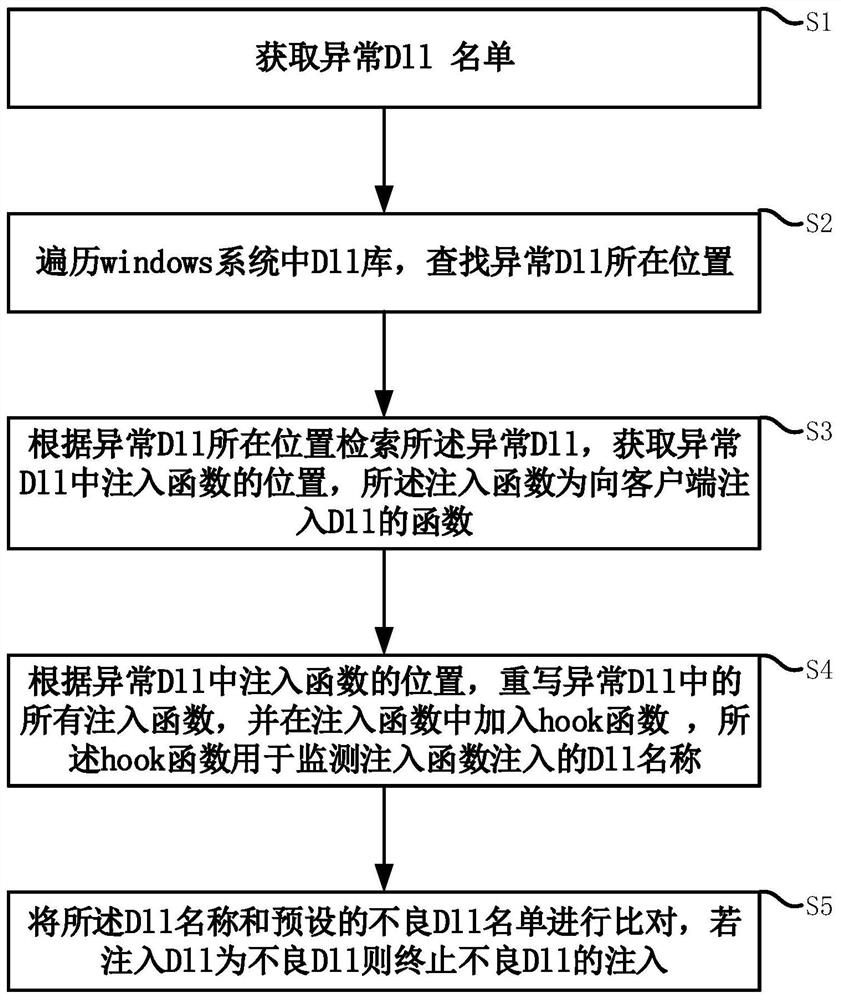
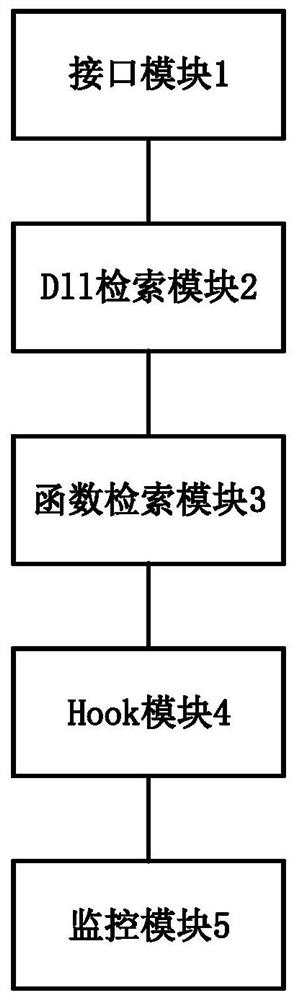
Method, storage medium, electronic device and system for preventing bad dll injection
ActiveCN110968867BInhibit injectionPrevent crashPlatform integrity maintainanceThe InternetEmbedded system
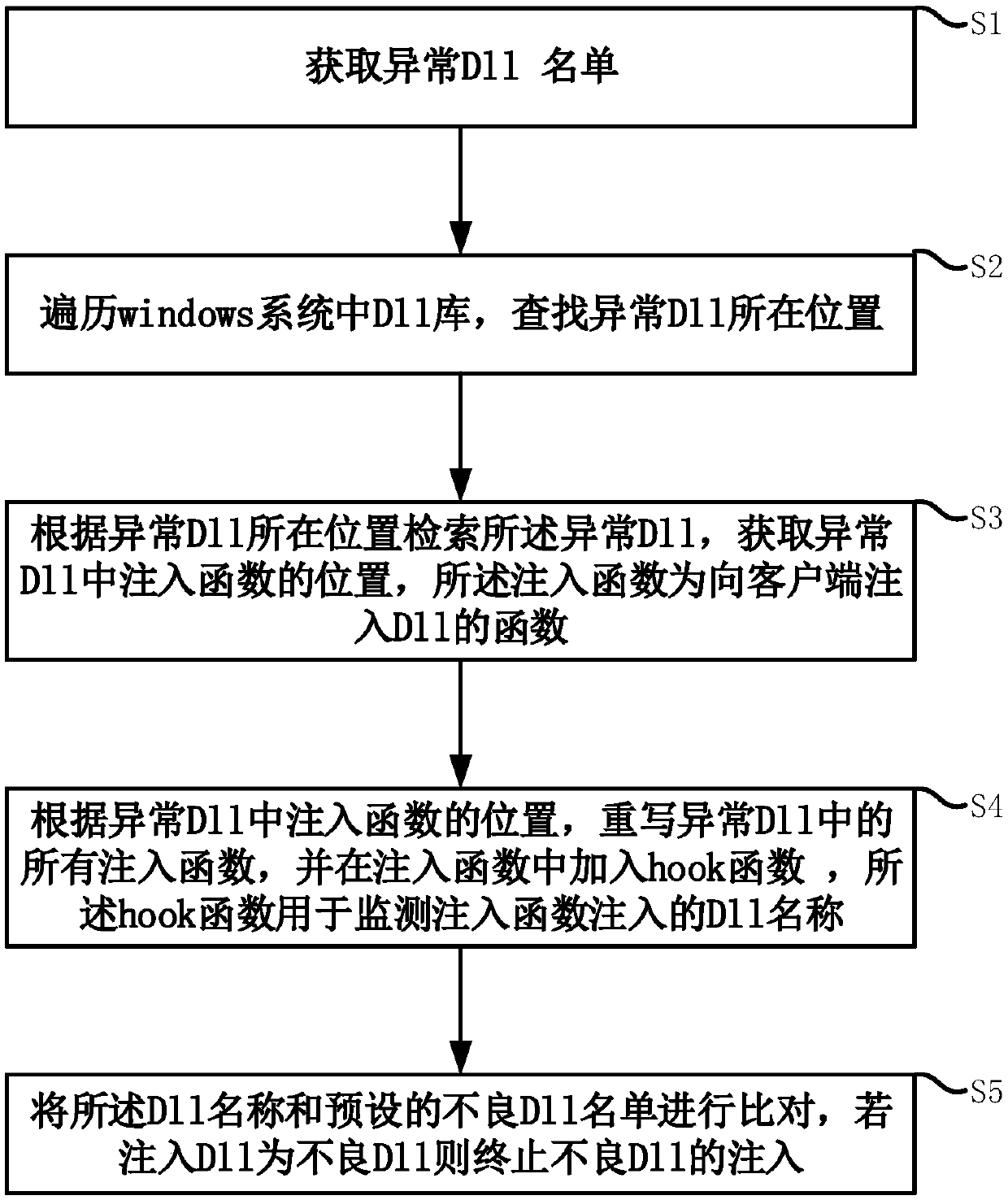
The invention discloses a method, a storage medium, an electronic device and a system for preventing bad DLL injection, and relates to the field of Internet PC client application development. The method includes obtaining a list of abnormal DLLs. Traverse the DLL library in the Windows system to find the location of the abnormal DLL. The abnormal DLL is retrieved according to the location of the abnormal DLL, and the position of the injected function in the abnormal DLL is acquired, and the injected function is a function injected into the DLL to the client. According to the location of the injected function in the abnormal DLL, rewrite all the injected functions in the abnormal DLL, and add a hook function in the injected function, and the hook function is used to monitor the name of the DLL injected by the injected function. The DLL name is compared with the preset list of bad DLLs, and if the injected DLL is a bad DLL, the injection of the bad DLL is terminated. The invention can prevent the client running in Windows from being injected with a bad DLL, thereby preventing the client from crashing and being hacked.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
An optimized management method for injecting multiple dlls into the target process
ActiveCN106406852BImprove stabilityImprove efficiencyProgram loading/initiatingExecution paradigmsMulti injectionComputer science
The invention discloses an optimal management method for injecting multi-DLL (dynamic link library) into a target procedure. The method comprises the following steps: inserting an APC function in a kernel space by use of an APC mechanism, and additionally adding the optimal management on the injection DLL while injecting the injection execution DLL into the target procedure, and injecting the DLL management module in unification through an unified injection interception mechanism under the condition of needing to inject multi-DLL in the target procedure, thereby improving the target procedure stability and the entire execution efficiency of the interception function. The technical scheme disclosed by the invention has the advantages of being comprehensive in control and high in flexibility, any number of DLL can be injected, and the stability and the efficiency of the target procedure can be obviously improved in particular under the condition of the existence of multi-injection HookDLL; and the execution order of the multi-HookDLL is effectively managed by use of an injection control DLL module (ControlDLL module), the method is flexible and varied, and can be suitable for various places.
Owner:BEIJING VRV SOFTWARE CO LTD
Selection frame recognition method based on graphic comparison
PendingCN108595152ASmall footprintAvoid the difficulty of finding specific recordsSoftware designGraphicsAlgorithm
The invention provides a selection frame recognition method based on graphic comparison. The method comprises followings steps: performing DLL injection using the message hooking function provided byWindows; running own code in an opposite side program, and performing API hooking by modifying the Windows API entry address; comparing the state images of all the enumerated selection boxes of the with the image captured by the current window, and replacing it with the text associated with the reference image of the selection box state. The method of the invention avoids the difficulty of findinga specified record in the form of a picture, and the space occupied by the data becomes smaller, the transmission and storage speed are improved, the reusability is high, and the cost is low.
Owner:CHANGSHA BIOVISION SOFTWARE TECH CO LTD
Method for preventing bad DLL injection, storage medium, electronic equipment and system
The invention discloses a method for preventing bad DLL injection, a storage medium, electronic equipment and a system, and relates to the field of internet PC client application and development. Themethod comprises the steps: obtaining an abnormal DLL list; and traversing the DLL library in the Windows system, and searching the position of the abnormal DLL. And retrieving the abnormal DLL according to the position of the abnormal DLL, and obtaining the position of an injection function in the abnormal DLL, the injection function being a function of injecting the DLL into the client. According to the positions of the injection functions in the abnormal DLL, all the injection functions in the abnormal DLL are rewritten, a hook function is added into the injection functions, and the hook function is used for monitoring the name of the DLL injected by the injection functions. And comparing the DLL name with a preset bad DLL list, If the injected DLL is a bad DLL, terminating the injection of the bad DLL. According to the method, the client running in Windows can be prevented from being injected with bad DLL, so that the client is prevented from collapsing and being invaded by hackers.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com