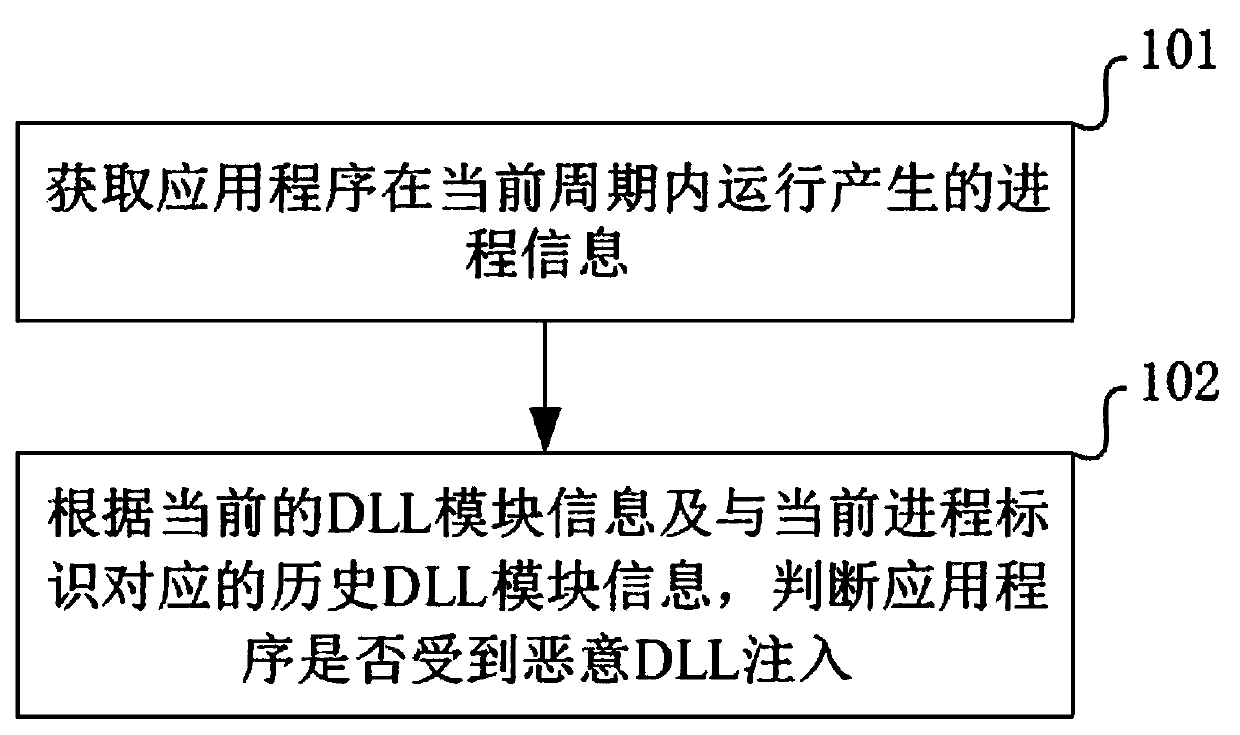
Malicious DLL injection detection method and device
A detection method and malicious technology, applied in the field of network security, can solve problems such as application program running failure, failure to detect malicious DLL injection in time, and application program destruction.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0081] Example 1, if the current DLL module information only includes the file name of the DLL module, then it can be determined whether the file name of the current DLL module exists in the file name of the historical DLL module, if not, it can be determined that the application program is injected by a malicious DLL.
[0082] On the contrary, if the file name of the current DLL module exists in the file name of the historical DLL module, it can be determined that the application program is not injected by a malicious DLL.
example 2
[0083] Example 2, if the current DLL module information includes the file name of the current DLL module and the file size of the current DLL module, then you can refer to figure 2 , which exemplarily shows one of the schematic flowcharts corresponding to a method for judging whether an application is injected with a malicious DLL provided by the embodiment of the present application. Such as figure 2 As shown, specifically include the following
[0084] Step 201, judge whether the file name of the current DLL module exists in the file name of the historical DLL module, if yes, execute step 202; otherwise, execute step 204.
[0085] Step 202, judging whether the file size of the current DLL module is consistent with the file size of the historical DLL module, if they are consistent, execute step 203; otherwise, execute step 204.
[0086] In step 203, it is determined that the application program is not injected by a malicious DLL.
[0087] In step 204, it is determined th...
example 3
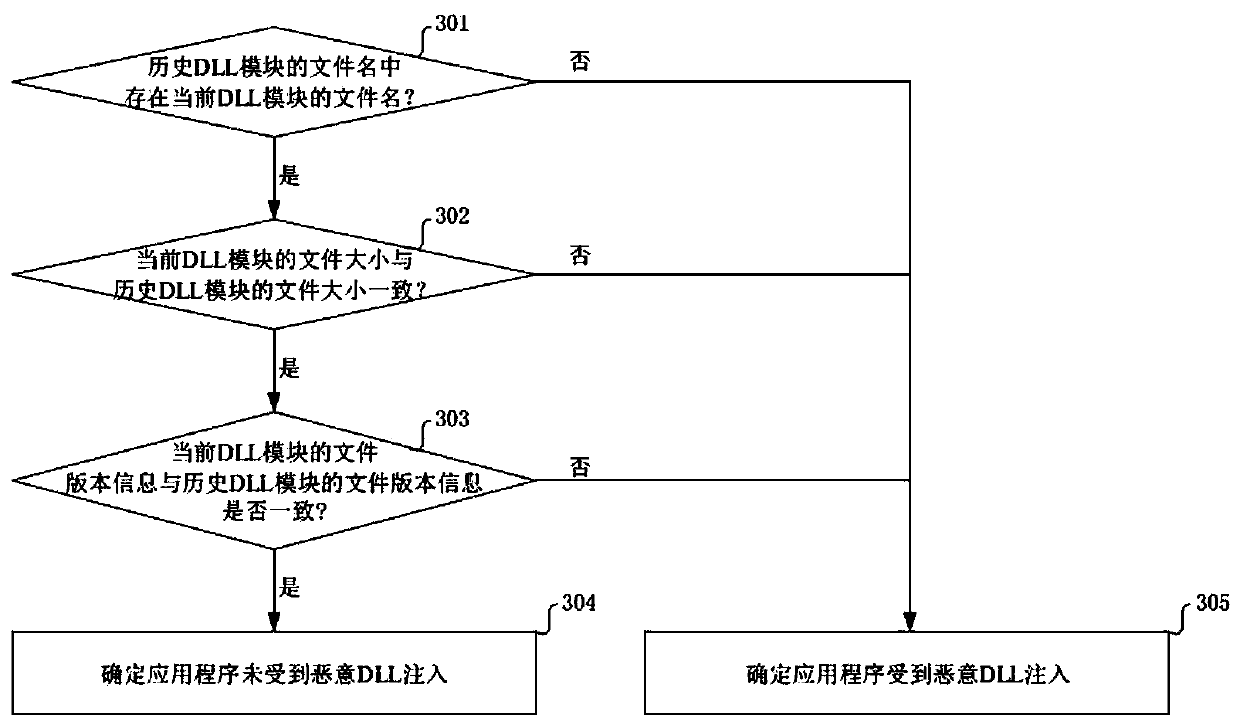
[0088] Example 3, if the current DLL module information includes the file name of the current DLL module, the file size of the current DLL module and the file version information of the current DLL module, then you can refer to image 3 , which exemplarily shows the second schematic flowchart corresponding to a method for judging whether an application program is injected with a malicious DLL provided by the embodiment of the present application. Such as image 3 As shown, specifically include the following
[0089] Step 301, judge whether the file name of the current DLL module exists in the file name of the historical DLL module, if yes, execute step 302; otherwise, execute step 305.
[0090] Step 302, judging whether the file size of the current DLL module is consistent with the file size of the historical DLL module, and if they are consistent, execute step 303; otherwise, execute step 305.
[0091] Step 303, judging whether the file version information of the current DL...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com