Single sign-on mechanism oriented to MEC environment and based on OAuth2.0
A single sign-on, environmental technology, applied in security devices, digital data authentication, electrical components, etc., can solve problems such as small application scope, complex protocols, and inapplicability to mass user key management.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] The present invention will be described in detail below in conjunction with the accompanying drawings.
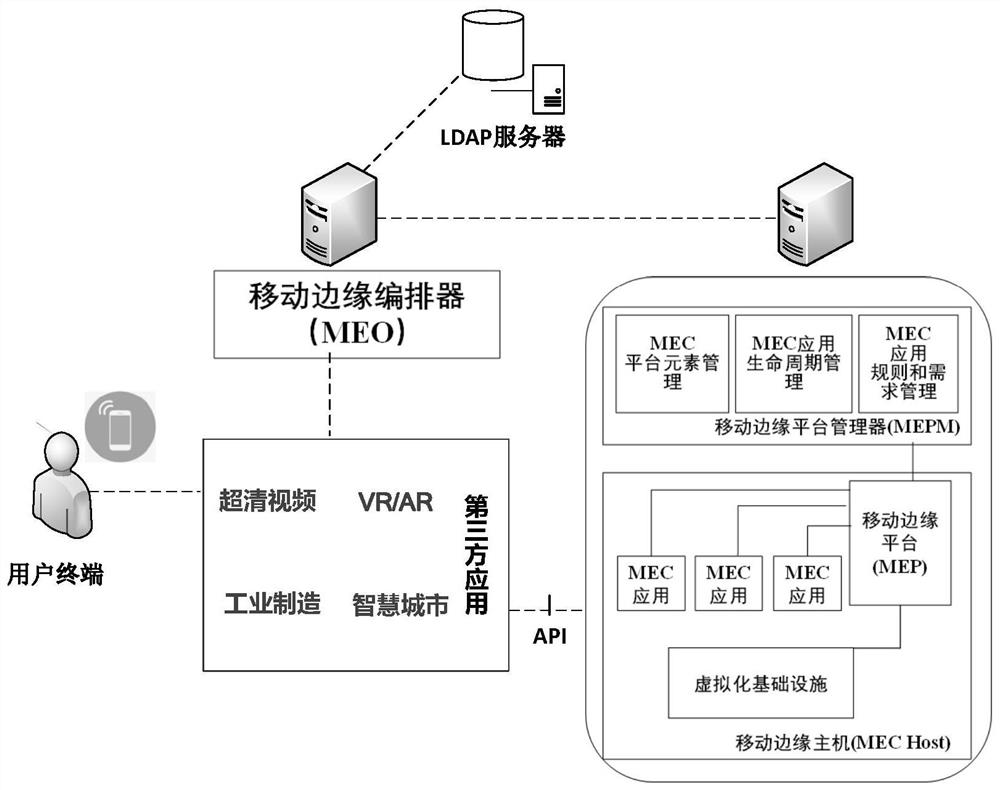
[0054] Such as figure 1 As shown, the single sign-on system of the embodiment of the present invention includes the following entities:
[0055] User terminals, users access third-party applications through terminal devices to meet corresponding business needs;
[0056] Third-party applications, service providers deploy them on the MEC platform through open interfaces, provide users with business services, receive user account names, passwords and other identity information, and help them complete login and authorization operations;
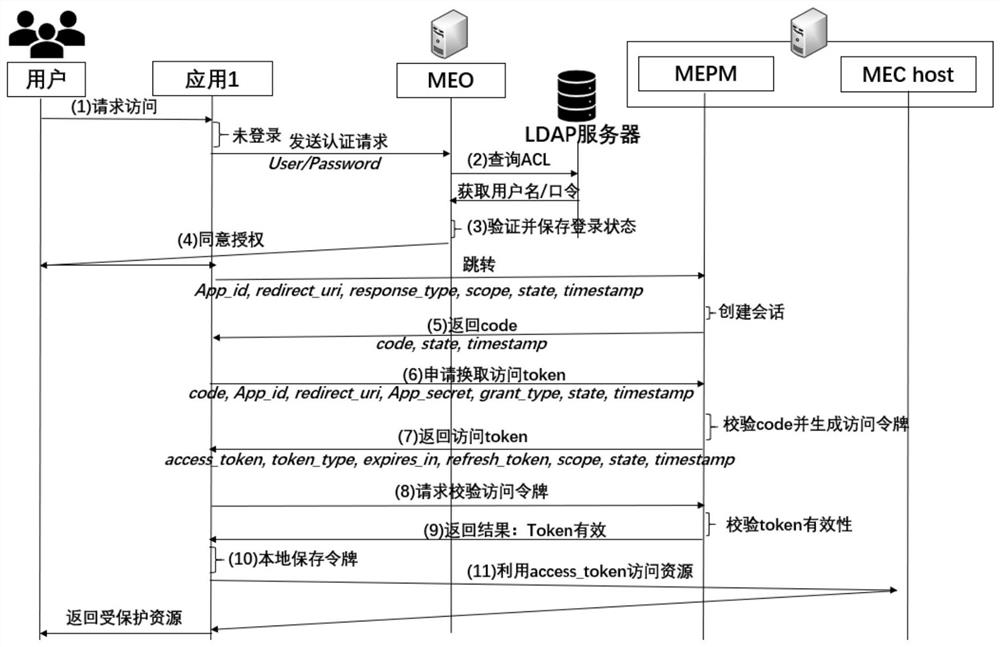
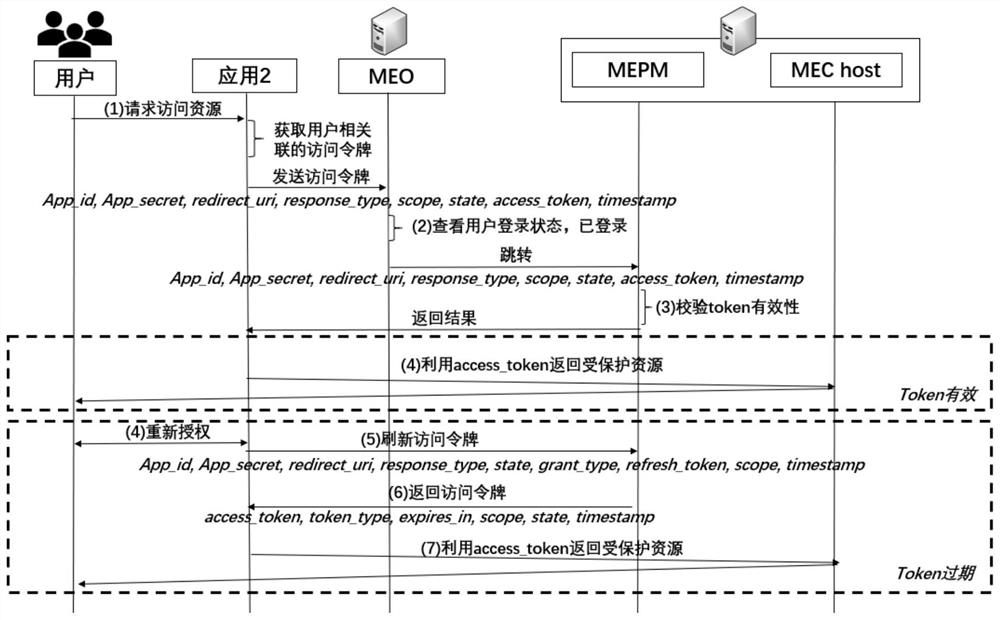
[0057] MEO, the mobile edge orchestrator, processes authentication and authorization requests from users, and sends a token application request to MEPM after passing the verification;
[0058] LDAP server, used for quick query of user information, obtaining access control authority, and helping to complete user identity authentication...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com