Information Security Risk Evaluation System
A risk assessment and information security technology, applied in the field of information security, can solve problems such as inability to accurately analyze and calculate business network security risks, and achieve the effects of improving security protection performance, reducing evaluation difficulty, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
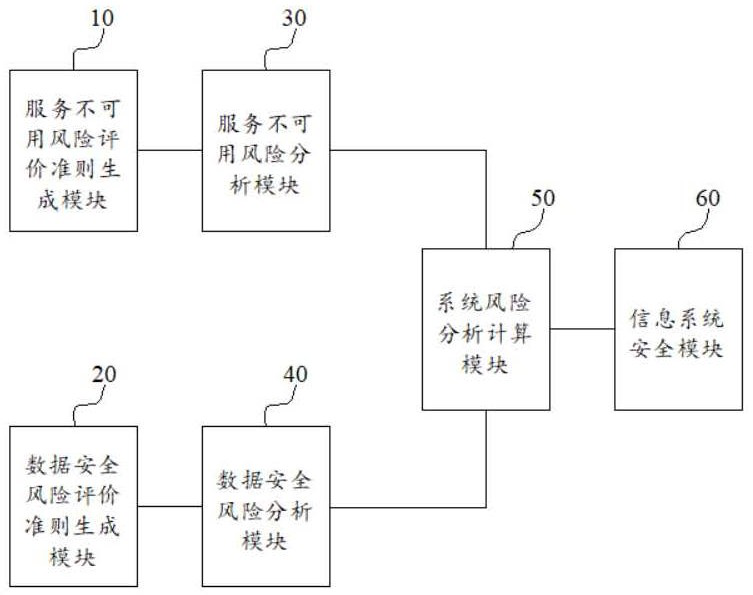
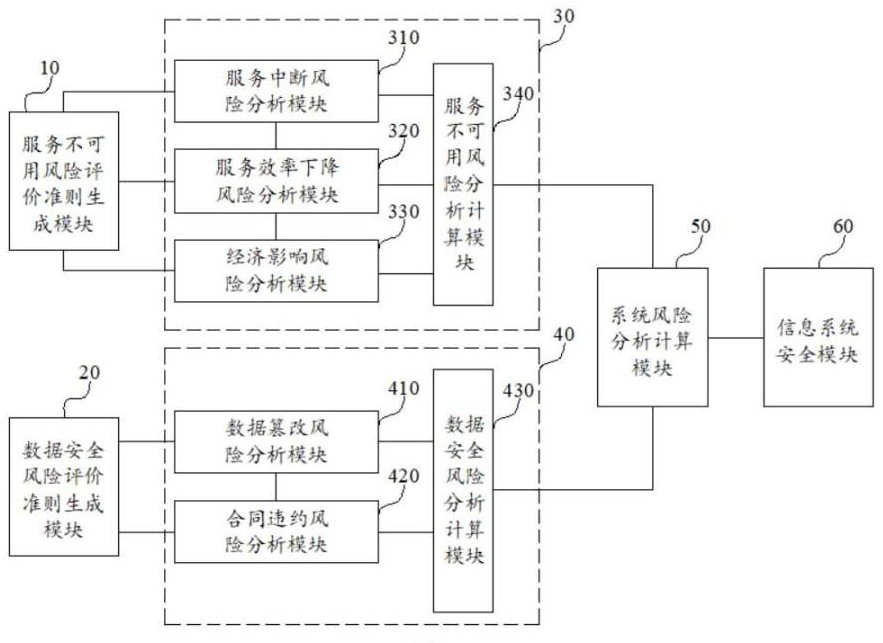
[0038] figure 1 It is a schematic structural diagram of a circuit module of Embodiment 1 of the information security risk assessment system provided by the present invention. like figure 1 As shown, the system includes: a service unavailable risk evaluation criterion generation module 10, a data security risk evaluation criterion generation module 20, a service unavailable risk analysis calculation module 30, a data security risk analysis module 40, a system risk analysis calculation module 50 and information System security module 60; wherein, the service unavailable risk evaluation criterion generation module 10 is used to generate service unavailable risk evaluation criterion data; the data security risk assessment criterion generation module 20 is used to generate data security risk assessment criterion data; the service is unavailable The risk analysis calculation module 30 is connected with the service unavailable risk evaluation criterion generation module 10, and is u...
Embodiment 2
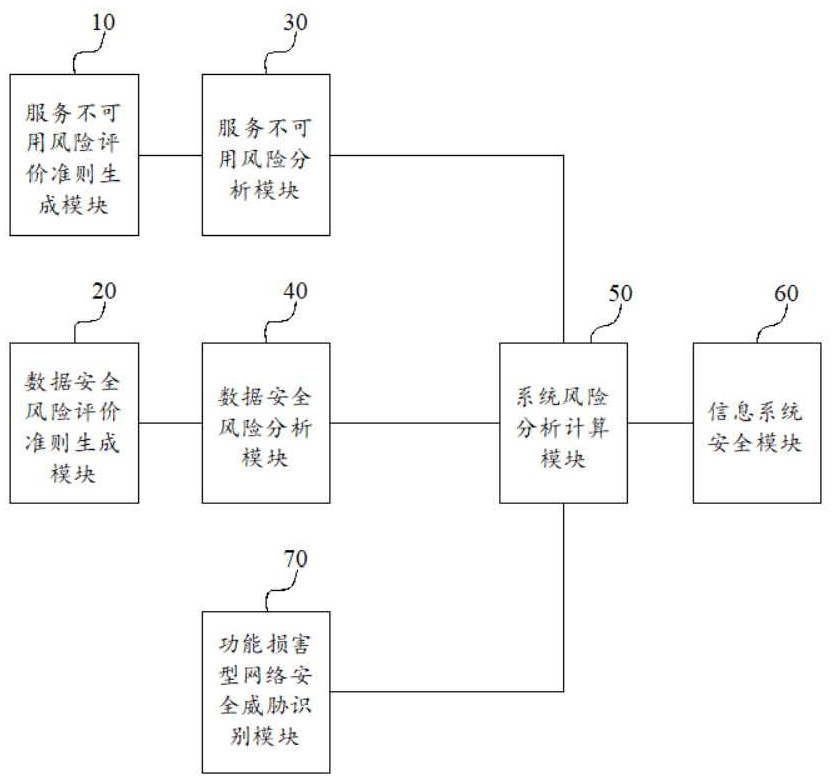
[0067] image 3 It is a schematic structural diagram of a circuit module of Embodiment 2 of the information security risk assessment system provided by the present invention. Figure 4 It is a schematic structural diagram of a circuit module of a function-impaired network security threat identification module in Embodiment 2 of the information security risk assessment system provided by the present invention. like image 3 and Figure 4 As shown, the difference between the information security risk assessment system in Embodiment 2 and the information security risk assessment system in Embodiment 1 is that: the information security risk assessment system in Embodiment 2 also includes: a function-impaired network security threat identification module 70; wherein, The functional impairment network security threat identification module 70 includes: a threat behavior judgment definition module 701 , a threat originator identification module 702 , a threat capability identificati...
example 1
[0084] Example 1: If the data stored in the threat capability data subunit (that is, the threat capability) is the capability of the operator, it can be divided into five levels: the first level is for daily application users; the second level is for terminal The person with operation and configuration authority; the third level is the technician with software and application system configuration operation authority; the fourth level is the technician with equipment or software asset administrator authority; the fifth level is the access to the computer room for physical equipment and environmental control Technicians with direct access to equipment.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com