M2M transmission control method, device and system
A technology of transmission control and corresponding relationship, applied in security devices, electrical components, wireless communication, etc., can solve the problems of weak M2M terminal, unfavorable service promotion, large data transmission volume, etc., to achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
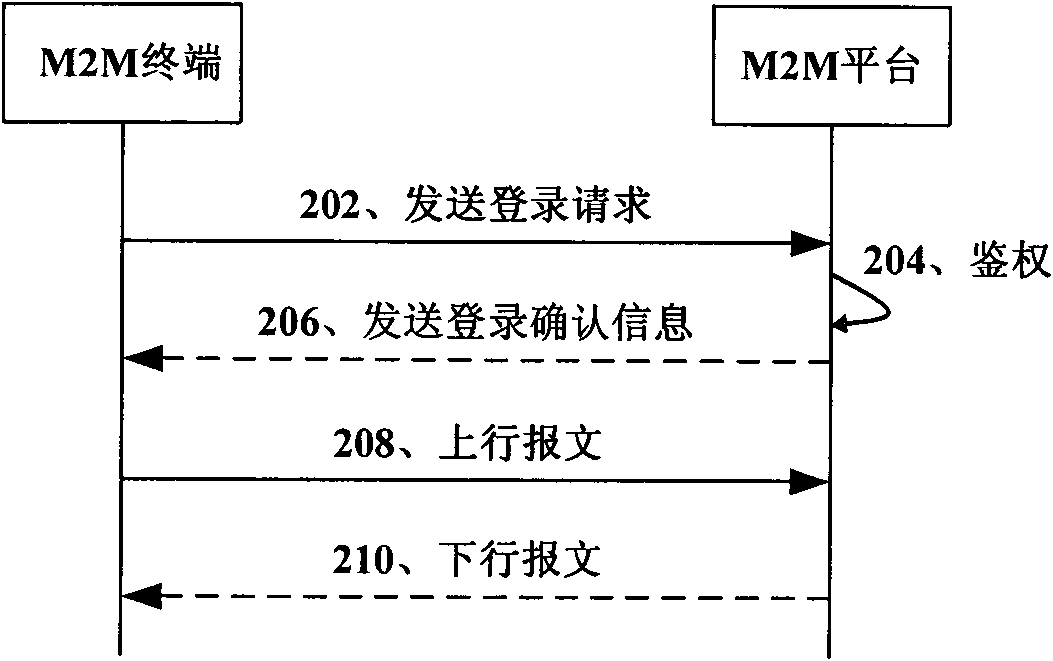
[0037] figure 2 It is a flow chart of Embodiment 1 of the M2M transmission control method of the present invention, as shown in figure 2 As shown, this embodiment includes:
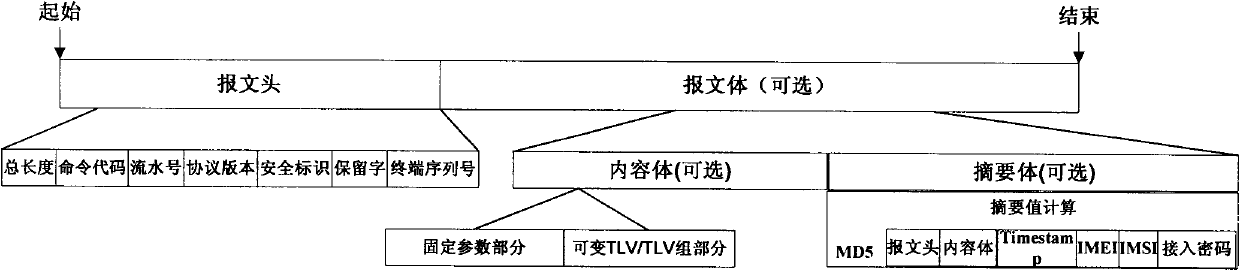
[0038]Step 202, the M2M terminal sends a login request including the access password, IMEI code, IMSI code and terminal serial number to the M2M platform, wherein the access password is preset in the M2M terminal or sent to the M2M terminal by the M2M platform, Login request message format:
[0039] Packet header + content body + MD5 (packet header + content body + Timestamp + IMEI + IMSI + uplink access password);
[0040] Step 204, the M2M platform receives the login request, and authenticates the M2M terminal according to the stored correspondence between the IMEI code, IMSI code, and terminal serial number,
[0041] The M2M platform also uses a security authentication algorithm based on the header and content body of the received login request message, the time stamp generated by the M2M platform...
Embodiment 2
[0051] image 3 It is a flow chart of Embodiment 2 of the M2M transmission control method of the present invention. For an M2M terminal that supports data communication encryption and enables an encryption function, it can apply for a session key from the M2M platform during its login process for data encryption after login. like image 3 As shown, this embodiment includes:
[0052] Step 302, the M2M terminal sends a login request including access password, IMEI code, IMSI code and terminal serial number to the M2M platform, and the login request also includes information related to the basic key in the M2M terminal, and information about requesting a session key,
[0053] Login request message format:
[0054] Message header + content body (including the digest value of the basic key-related information) + MD5 (message header + content body (including the digest value of the basic key-related information) + Timestamp+IMEI+IMSI+uplink access password);
[0055] Step 304, ...
Embodiment 5
[0086] Image 6 It is a flow chart of Embodiment 5 of the M2M transmission control method of the present invention. During the interaction between the M2M terminal and the M2M platform, both parties can initiate the change of the access password or basic key, such as Image 6 As shown, this embodiment includes:
[0087]Step 602, the M2M terminal sends a change request including the IMEI code, IMSI code, terminal serial number and access password to apply for the access key and / or the basic key to the M2M platform;
[0088] Step 604: After receiving the change request, the M2M platform authenticates the M2M terminal according to the change request;
[0089] Step 606, the M2M platform judges whether to send the new access key and / or basic key to the M2M terminal in plaintext or ciphertext,
[0090] Step 608, if it is sent in plain text, the M2M platform returns a request change acceptance response to the M2M terminal, requiring it to enter the SMS communication mode and wait ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com