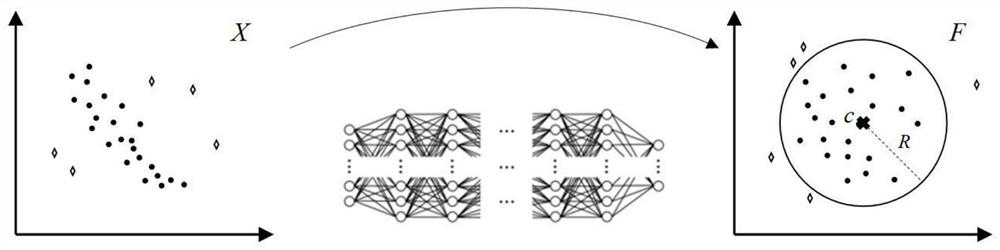
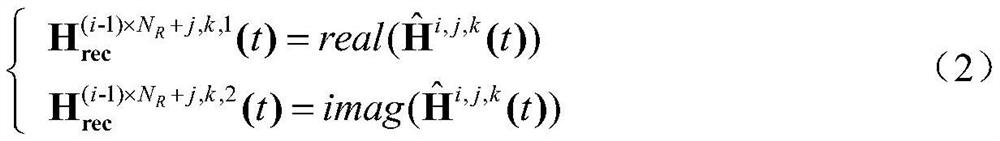Physical layer identity authentication method based on deep support vector description method
An identity authentication and support vector technology, applied in neural learning methods, climate sustainability, sustainable communication technology, etc., can solve problems such as key leakage, increase communication resources and computing resource consumption, and decipher ciphertext.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] The physical layer identity authentication based on the deep support vector description method in the present invention is described by taking a communication scenario including one legal information sender, one legal information receiver and three attackers as an example. In this example, the number of transmit antennas of the MIMO-OFDM communication system is N T = 2, the number of receiving antennas N R =2, the number of subcarriers N S = 256. The time delay of each path and the fading at all levels of the multipath fading channel are shown in Table 1, and the signal-to-noise ratio is 1 dB.
[0056] It includes the following steps:
[0057] Step 1: Collect CSI data between legal users at T (in this example, T=2000) times as a training data set, where each record is the CSI data at time t (t=1, 2,...T) , called a training sample. The T value determines the number of training samples. Too few training samples will reduce the generalization ability of the authentic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com