Big data implementation control system based on internet network security
A network security and implementation control technology, applied in the field of big data and network security, can solve the problems of increasing packet loss rate, key delay exposure, vulnerability to attack, etc., to prevent route replay attacks, reduce packet loss rate, and ensure The effect of freshness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
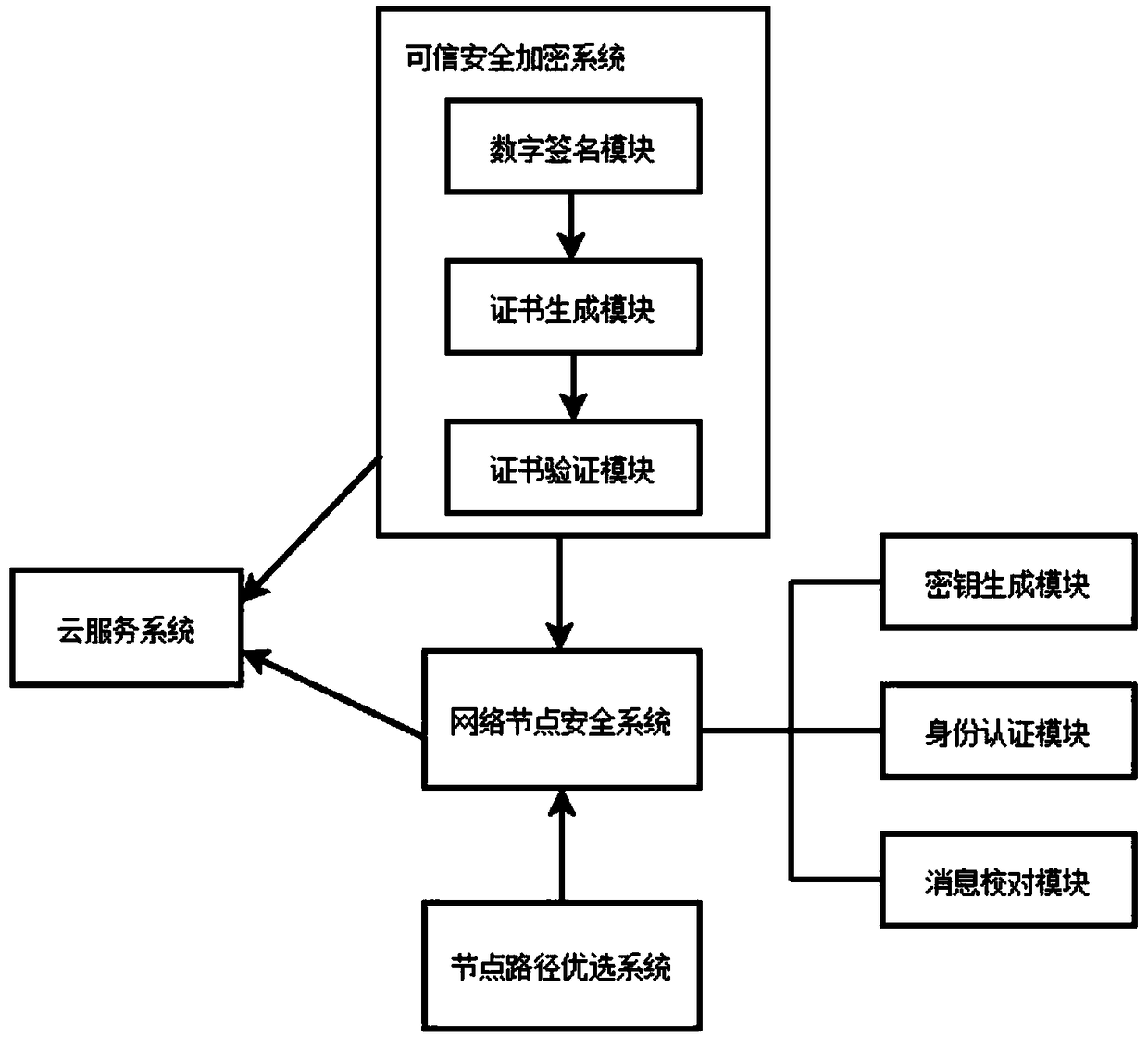
[0038] Big data implementation control system based on Internet network security, such as figure 1 As shown, including network node security system, trusted security encryption system, node path optimization system, cloud service system;
[0039] The network node security system establishes a secure route to determine the safe transmission path of data in the network;
[0040] The establishment of the safe route includes the following steps:
[0041] (1) Each node of the wireless sensor is pre-assigned a unique number before sowing;
[0042] (2) There is a shared key between each node and the cloud service system;
[0043] (3) Each node generates a key pair with its adjacent nodes, and stores the key pair in the key ring of each node;
[0044] (4) The cloud service system includes the numbers of all nodes and the key pool of the entire network;
[0045] The network node security system includes an identity authentication module, a key generation module and a message proofr...
Embodiment 2
[0072] This embodiment is further optimized on the basis of Embodiment 1. The node path optimization system is used for safe routing and uses the node occupancy to judge the actual transmission situation of the node. The node occupancy is set as follows:
[0073] The source node is assigned a value of 1;
[0074] The intermediate node is assigned a value of 2;
[0075] The target node is assigned a value of 3;
[0076] Unused nodes are assigned a value of 0;
[0077] When the node occupancy is not 0, it means that the node is already occupied, then skip this node and select other neighbor nodes; when the node occupancy is 0, it means that the node is in an idle state, then this node is selected as a candidate node;
[0078] Based on the AODV algorithm, node occupancy is used in the routing request pathfinding process.
[0079] Specifically, the link E→F→G is transmitting data, that is, the node occupancy degrees of nodes E, F, and G are all assigned non-zero values. Where ...
Embodiment 3
[0081] This embodiment is further optimized on the basis of Embodiment 1, the node path optimization system is used for the MAC layer and the network layer of the wireless sensor node in the security routing to participate in the path selection of the node;
[0082] The MAC layer sets two parameters, which include the ratio of the data packet sending rate to the data packet receiving rate, and the queue length. The two parameters are used to comprehensively evaluate whether the node is in a busy state, and select the optimal node path therefrom;
[0083] The ratio of the data packet sending rate to the data packet receiving rate is used to judge whether the node is in a congested state;
[0084] The queue length is used to compare the set queue length threshold to determine the data packet capacity that the node buffer can store.
[0085] Specifically, when the ratio of the data packet sending rate to the data packet receiving rate is less than 1, it indicates that the rate at...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com