Song ci poetry text message hiding technology based on hybrid encryption
A technology of mixed encryption and text information, applied in encryption devices with shift registers/memory, secure communication devices, public keys for secure communications, etc., can solve problems such as poor security, stiff carrier text, and easy reverse restoration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
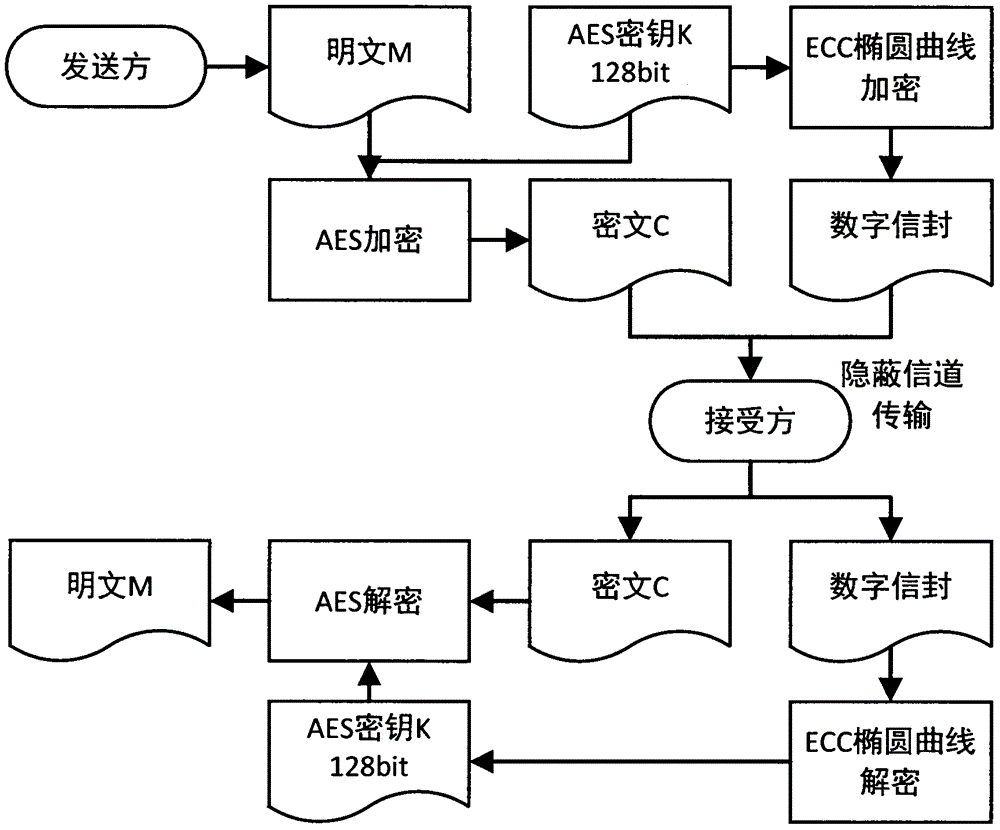
[0048] The first embodiment of the present invention introduces the process of performing AES encryption on the input information to be transmitted by a hybrid encryption tool, and using the ECC algorithm to encrypt the AES key. The encrypted information will be further processed that is information hiding. The specific steps are as follows figure 2 Shown, including:
[0049] (1) The sender enters the information of any length to be transmitted, namely the plaintext M, uses the AES algorithm of 128bit key length to encrypt, and generates the key C.
[0050] (2) For the 128-bit AES key, use the ECC encryption algorithm for encryption to generate a digital envelope with secret information.
[0051] (3) The secret information encrypted by AES and the digital envelope are used together with the text information hiding system of the Song Ci carrier to hide the information.
[0052] (4) After receiving the hidden information, the receiver uses the extraction algorithm to restore the secre...
Embodiment 2
[0056] The second embodiment of the present invention introduces two schemes for template generation, namely, a designated single template and a random mixed template, and the user selects the template generation scheme according to needs. The specific steps are as follows image 3 with Figure 4 Shown, including:
[0057] (1) Read the template library file, and store the template name and corresponding embeddable information into the poems[] structure array
[0058] (2) Obtain the total length of the information bit stream that needs to be steganographically written, record it as len, and initialize the currently selected template that can embed information sum = 0.
[0059] (3) A random number n is randomly generated, and n=n mod k (k is the total number of templates).
[0060] (4) Select the nth template and record it in the temps array.
[0061] (5) Calculate the current embeddable information amount sum=sum plus the embeddable information amount of the nth template.
[0062] (6) If...
Embodiment 3
[0065] The third embodiment of the present invention Figure 5 As shown, it introduces the process of steganography of the secret information for the template generation scheme selected in the second embodiment, and the process of generating multiple Song Ci with steganographic information. The dictionary after hash reset and a higher template utilization rate are used to improve the efficiency in code extraction. The specific implementation process includes:
[0066] (1) Initialize the secret information that needs to be steganographically written as m, the Song Ci style template T, read the related information of the prosody library, and read the selected template file into the s string array.
[0067] (2) Convert all the input secret messages m into binary codes m'. If the length of m'is not enough, zero is added to the last digit.
[0068] (3) Obtain the next division block of the s string array (the first division block for the first time), search and match in the prosody libra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com