An Embedded Module of Safety Mechanism
A security mechanism and embedded technology, applied in computer security devices, instruments, electrical digital data processing, etc., to achieve the effect of improving operating efficiency, good protection effect, and less resource occupation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
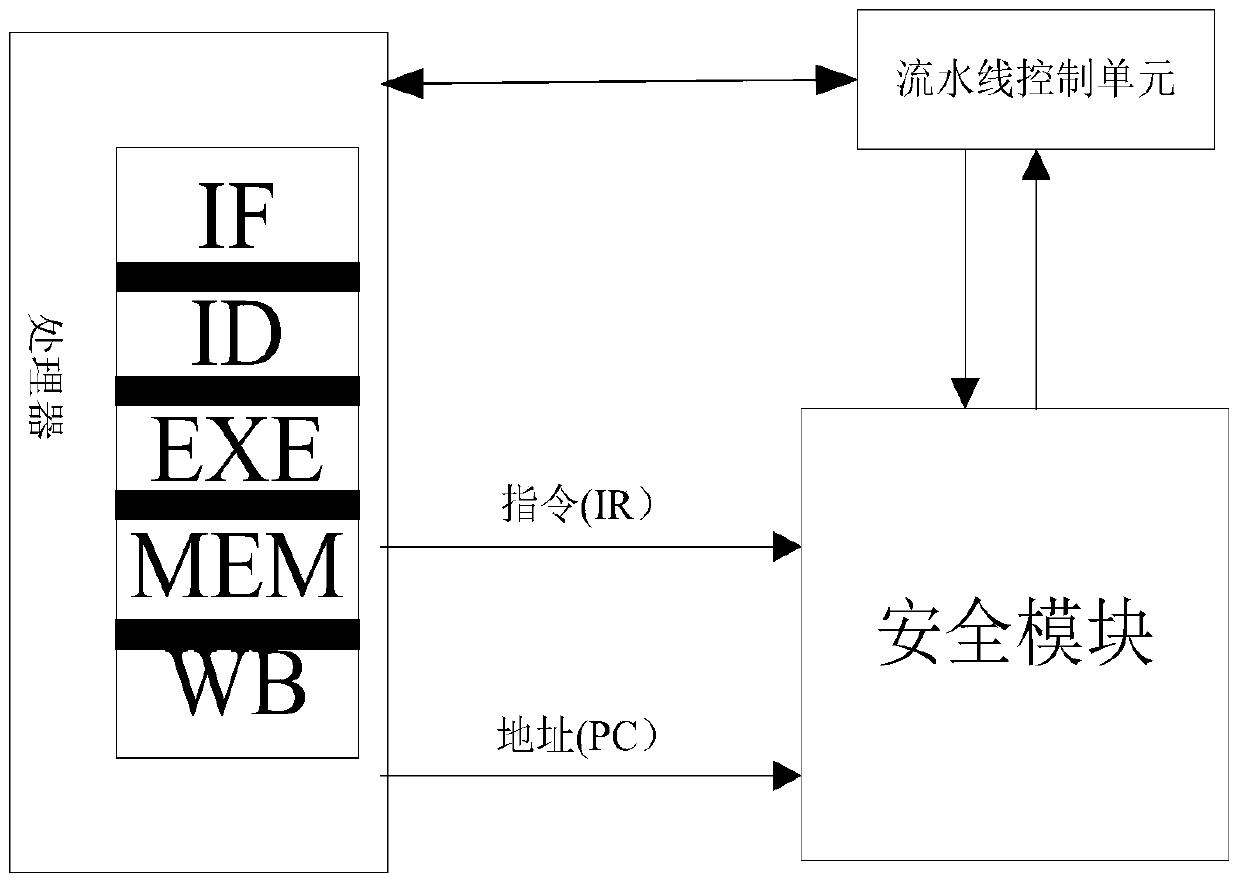
[0022] see figure 1 , figure 2 As shown, the specific implementation is as follows:
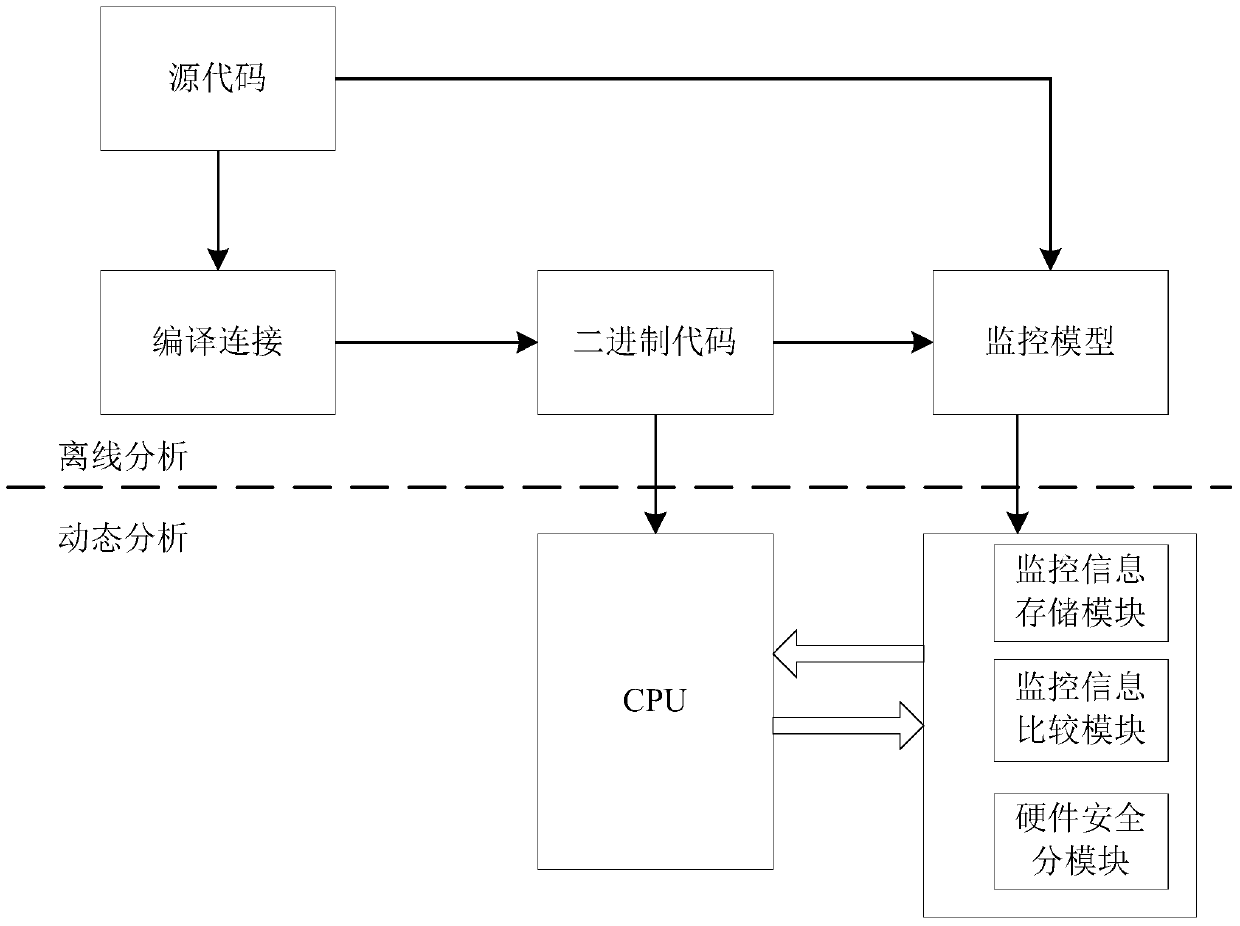
[0023] The present invention is an embedded module with a safety mechanism, which is composed of a monitoring information comparison module, a monitoring information storage module and a hardware safety sub-module. The relationship between the three is: the embedded processor transmits the collected program counter and current instruction value to the monitoring information comparison module, and then processes the data through the monitoring information storage module and the hardware security sub-module.
[0024] figure 1 Describes the overall structure of the safety monitoring mechanism, which mainly includes two parts: offline analysis of the program and real-time dynamic analysis of the program running. The program source code is cross-compiled in the offline analysis stage to generate executable binary code, and extract the required control flow basic block check information and jump instr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com