Cloud data security protection method
A data security and cloud technology, applied in electrical components, transmission systems, etc., can solve the problems of using leaked cloud data, protection loopholes, unauthorized access by tenants, etc., to improve security, realize security protection, and solve user privacy leakage. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
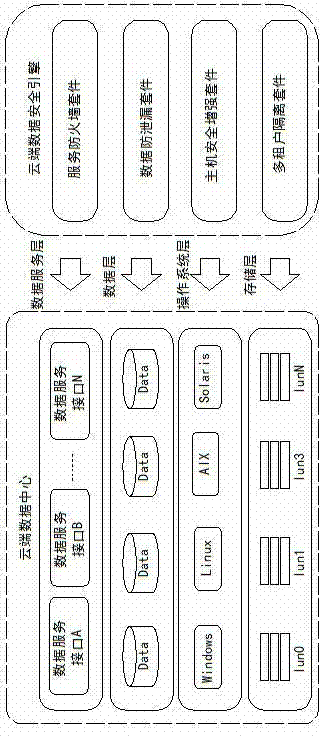
[0022] as attached figure 1 As shown, the cloud data security protection method of the present invention deeply protects the security of cloud data through measures such as cloud host security enhancement, cloud multi-tenant data isolation, cloud data leakage prevention, and service firewall. There are four levels of data layer and data service layer to realize all-round security protection for cloud data.
[0023] The cloud data security protection method proposed by the present invention can be realized by four security suites including cloud host security enhancement, cloud multi-tenant data isolation, cloud data leakage prevention and service firewall.
[0024] The service firewall uses service access control technology to realize the security control and service availability protection of data services. It is mainly composed of functional modules such as service interface interception, strong authentication and authorization, protocol compliance check, attack filtering, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com