Visible light communication-based limited area authority authentication device and file security method
A technology of visible light communication and limited area, which is applied in the direction of secure communication devices, computer security devices, encoding/decoding devices, etc., can solve problems such as no results, achieve improved freedom, clear security boundaries, and expand wireless hardware and software resources Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
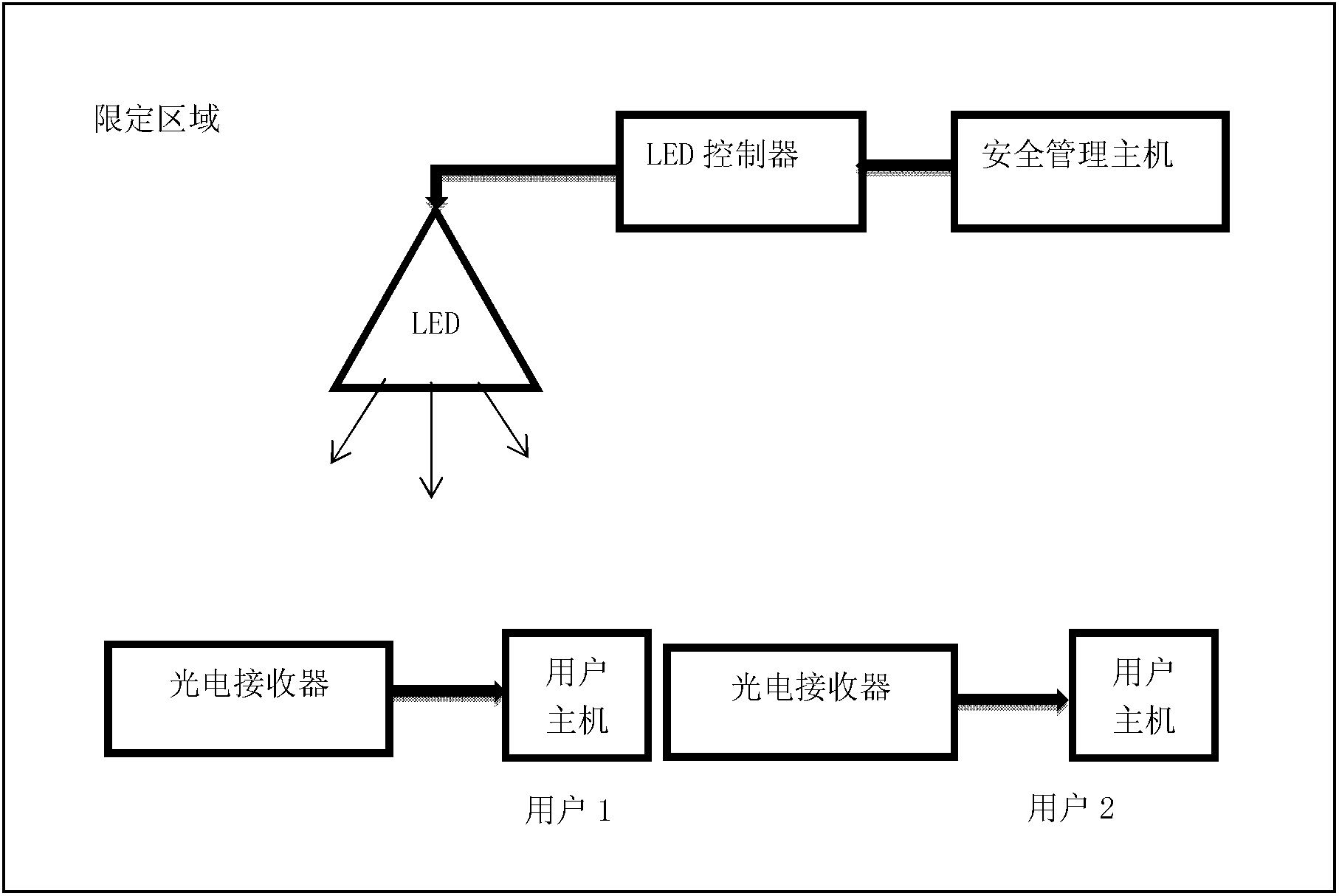
[0037] Such as figure 1 As shown, the limited area authority authentication device based on visible light communication of the present invention includes an LED controller, a photoelectric receiver, a security management host, and a user host. The LED controller is connected with the security management host; the photoelectric receiver is connected with the user host.
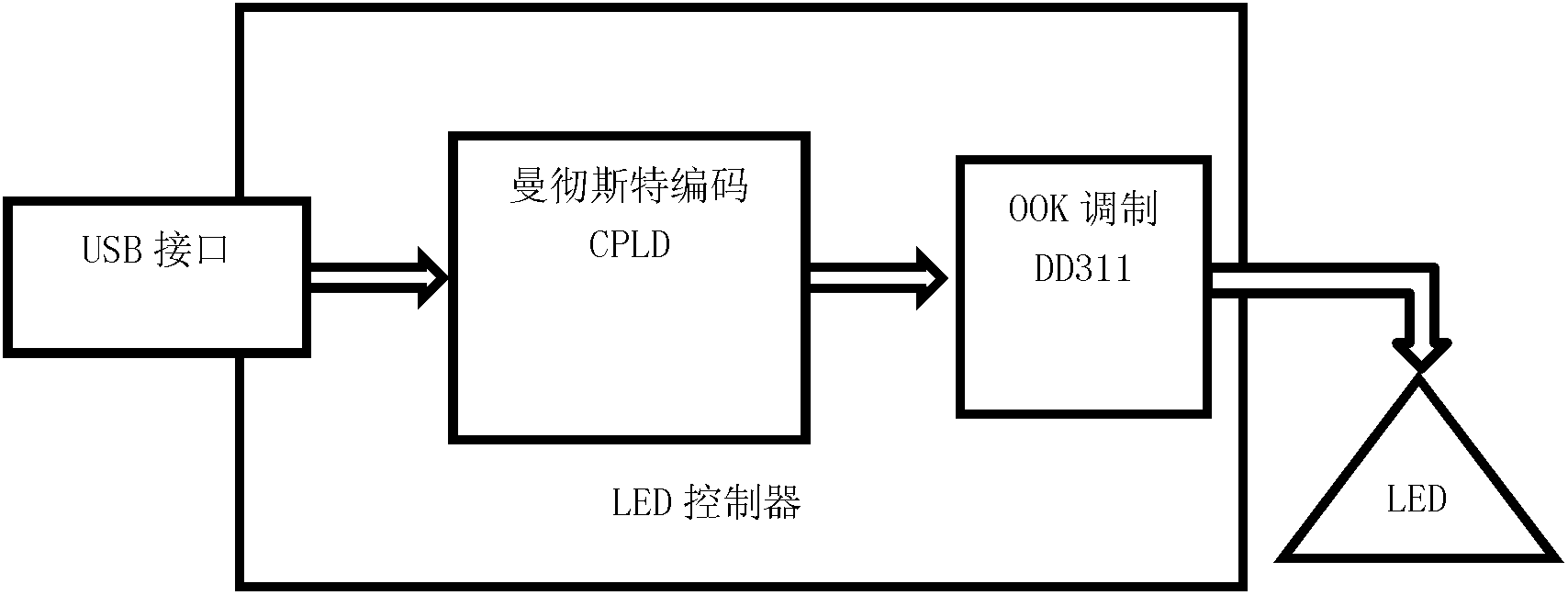
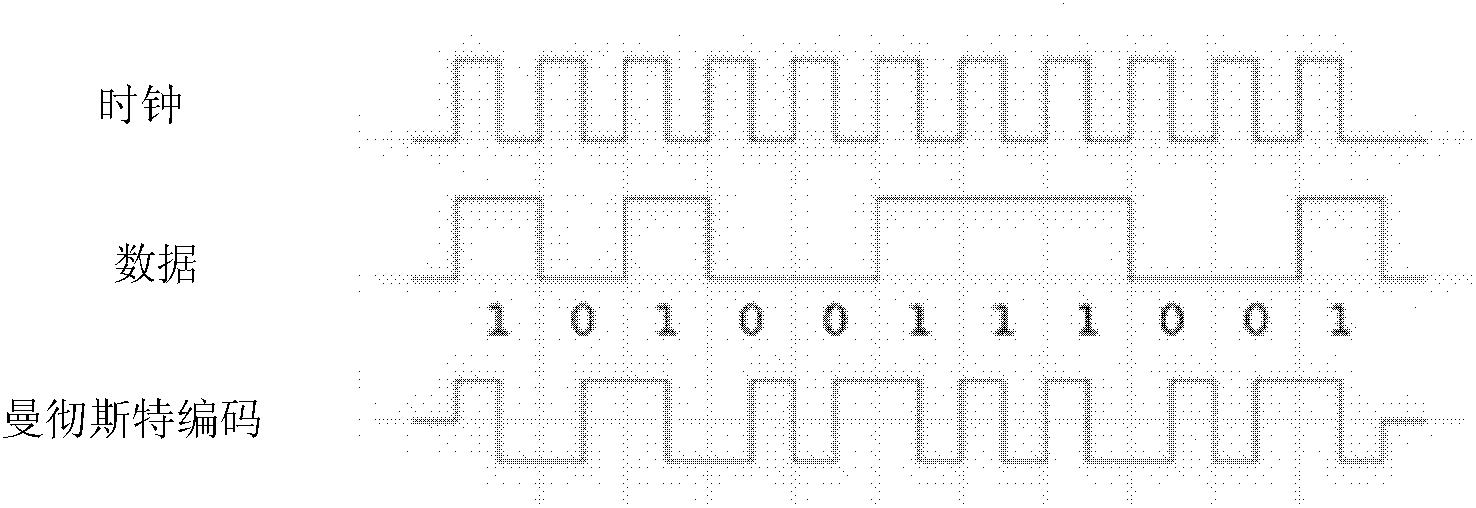
[0038] The LED controller includes an encoding module, a modulation module, an LED driver module, an LED module, and a communication interface module. The LED controller selects a high-security CPLD programmable device as the core device to realize the coding function, such as figure 2 shown. CPLD first obtains information with the security management host through the USB interface module, and then combines the two signals of the clock signal and the data signal into one through Manchester coding, and then uses the DD311 dedicated LED driver chip to perform OOK modulation on the white LED to emit visible lig...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com