Quantum signature method based on secret sharing
A secret sharing and quantum technology, applied in the field of quantum signatures based on secret sharing, can solve the problems of high cost, difficulty in preparation and storage of a large number of entangled states, security performance cannot be effectively guaranteed, etc., to achieve improved security and less calculation Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
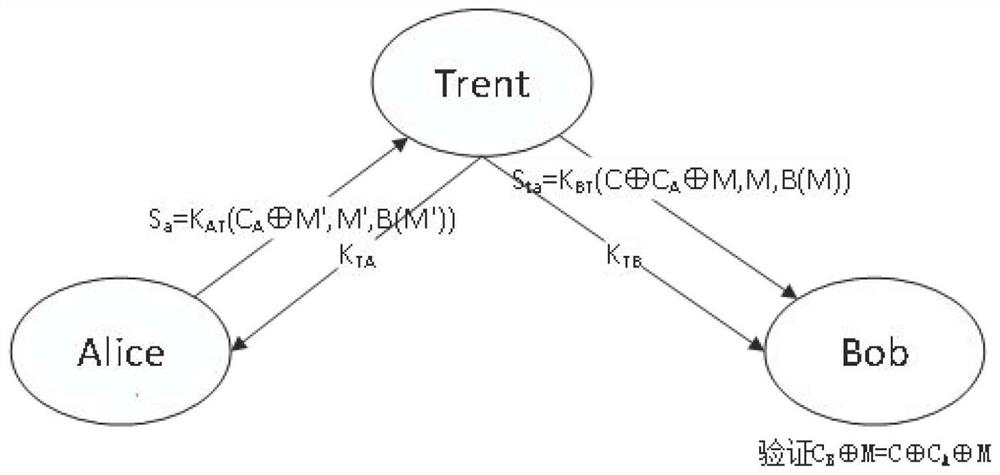
[0030] Embodiment 1 of the present invention discloses a quantum signature method based on secret sharing. The method mainly includes three steps of initialization, signature generation, and signature verification. In this embodiment, the signer Alice, the verifier Bob, and a reliable third party Trent ( Arbitrator) for detailed description of the three steps.
[0031] In the initialization step, it mainly includes three steps:
[0032] S11. The third party Trent issues the first key K to the signer Alice through the quantum key distribution protocol AT , issue the second key K to the verifier Bob BT .
[0033] As a preferred solution, the quantum key distribution protocol in this embodiment can use the BB84 protocol to provide unconditionally secure shared keys for Alice and Bob.
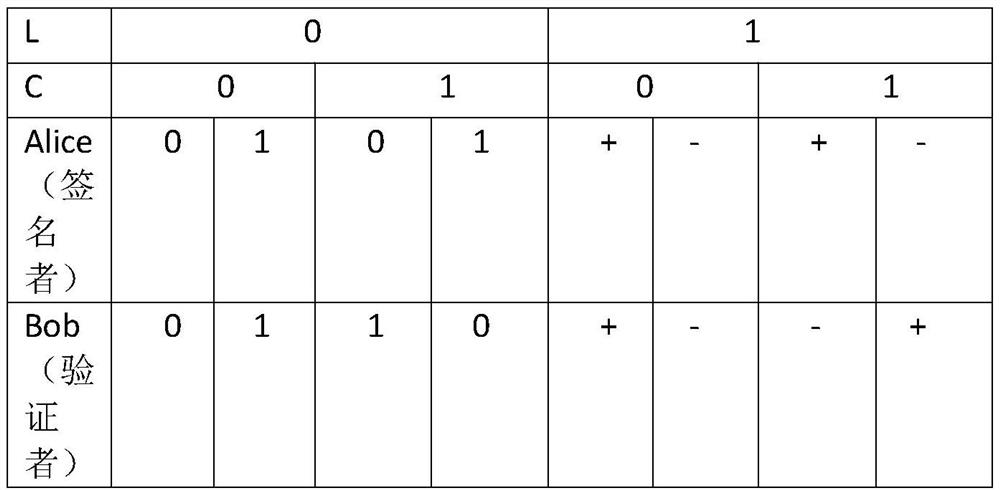
[0034] S12. The third-party Trent randomly creates a classic bit string n-bit. The classic bit string n-bit is a string of length n consisting of 0 and 1. Choose any string as the selection bit ...
Embodiment 2
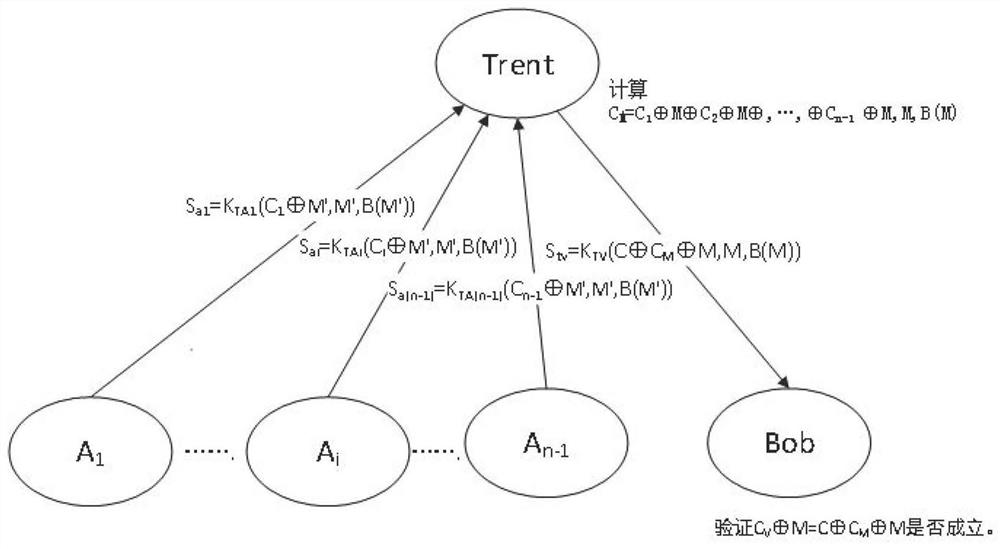
[0049] As an optimization solution, Embodiment 1 can also be extended to multiple quantum signatures, that is, a signer group consisting of multiple signers Alice, a reliable third party Trent, and a verifier Bob. The overall process is that n-1 signer members sign the information M respectively, send the signed information to a reliable third party Trent (third party) for sorting, generate the final signature, and verify it by any verifier after publication. The specific process is as follows:
[0050] initialization:
[0051] (1) Each group member establishes contact with a reliable third party Trent and obtains the corresponding key K TAi , the verifier V and T obtain the key K TV , the key distribution process is the same as the algorithm in Embodiment 1.
[0052] (2) Key C i The distribution process is consistent with the algorithm in Embodiment 1, except that Trent (the third party) creates an n-qubit product state|b 1 ,b 2 ,...,b n >, so that the n-bit qubit b 1...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com