VPN (Virtual Private Network) traffic quick recognition method for high-speed network
A high-speed network and identification method technology, applied in the field of cyberspace security, can solve problems such as unrealistic resource consumption, inability to apply high-speed networks, and affect accuracy, so as to achieve good practicability and application prospects, good identification stability, and privacy protection The effect of sexual problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
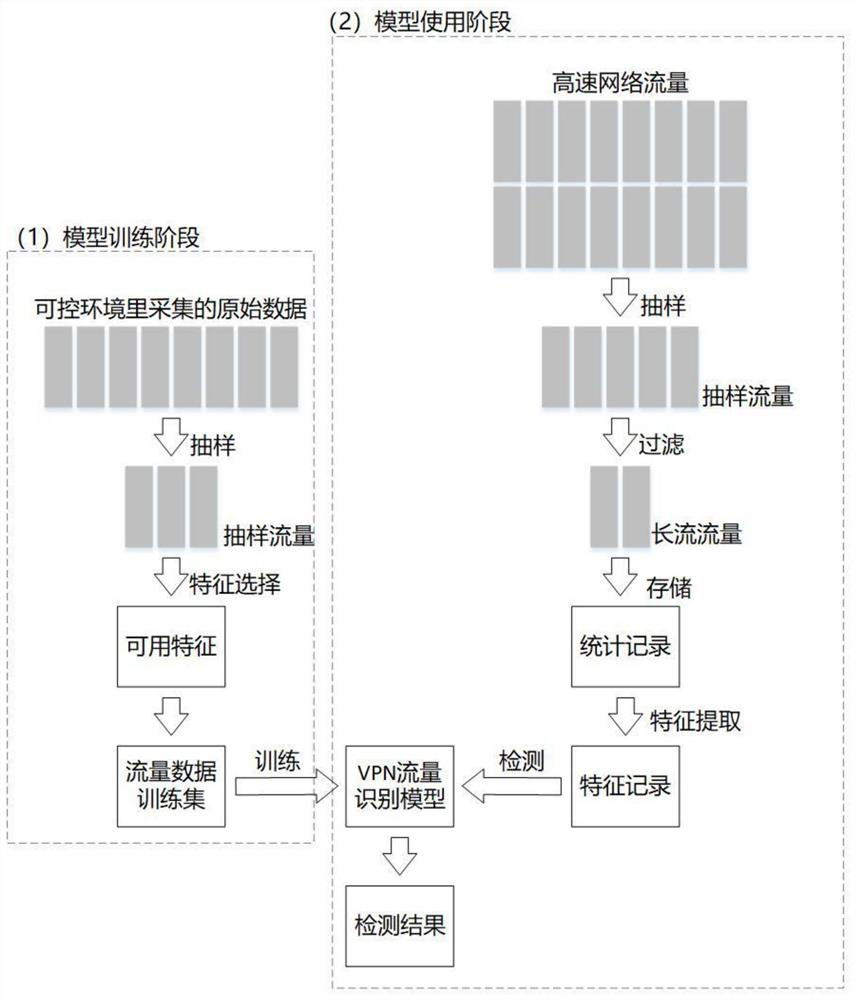
[0068] Embodiment 1: the present invention proposes a kind of high-speed network-oriented VPN traffic fast identification method, and its structural framework is as follows figure 1 shown, including the following steps:
[0069] (1) Collect and save VPN traffic data and common traffic data for model training;
[0070] The specific process of this step is as follows:
[0071] (1.1) Install VPN proxy tools, among which V2RayN is installed on the PC side, V2RayNG is installed on the mobile side, and V2Ray proxy plug-in is installed on the router;
[0072] (1.2) Start tcpdump to start VPN traffic data collection;
[0073] (1.3) Use VPN proxy tools for network access;
[0074] (1.4) Stop collecting after the network access ends, and store the VPN flow data file (.pcap) between the currently collected host end and the VPS;
[0075] (1.5) Start tcpdump to start ordinary traffic data collection;
[0076] (1.6) Turn off the VPN proxy service and use common applications to operate...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com