Source code vulnerability detection method for code graph representation learning based on graph convolution network
A vulnerability detection and convolutional network technology, applied in neural learning methods, biological neural network models, instruments, etc., can solve problems such as low learning efficiency of graph structure, missed vulnerability reporting, and failure to consider function call data dependencies, etc., to reduce leakage The effect of increasing the reporting rate, improving the accuracy rate, and reducing the scale
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
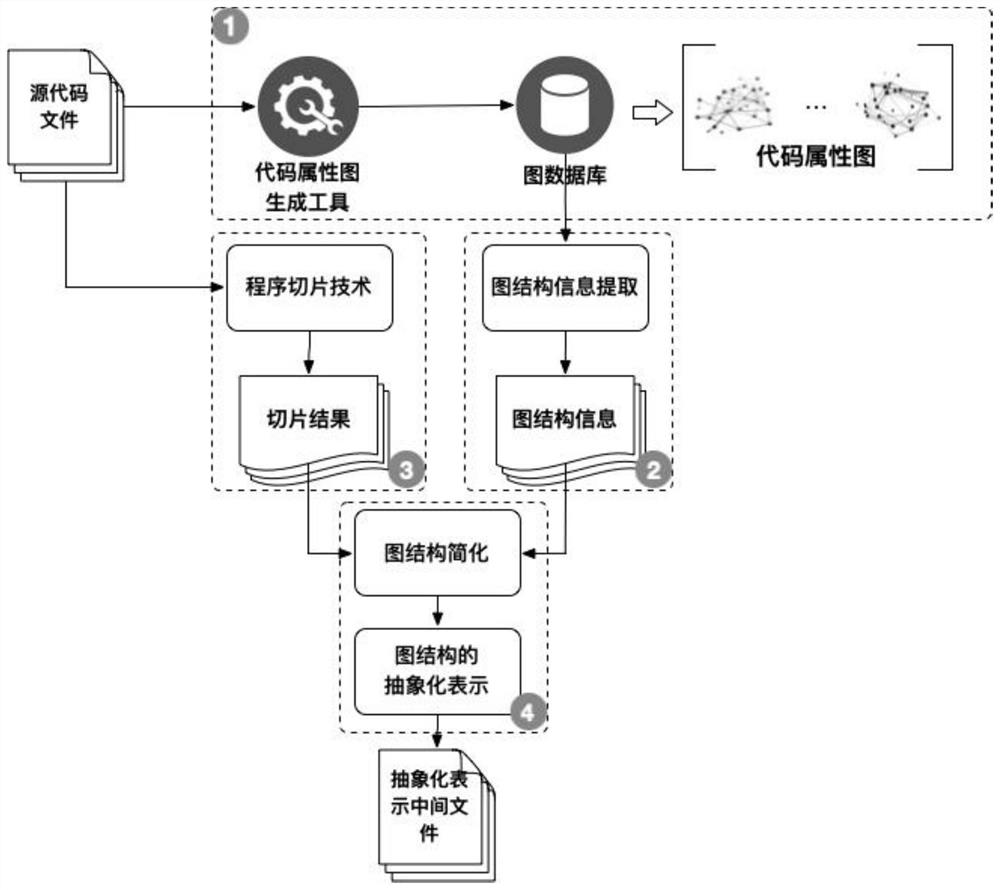
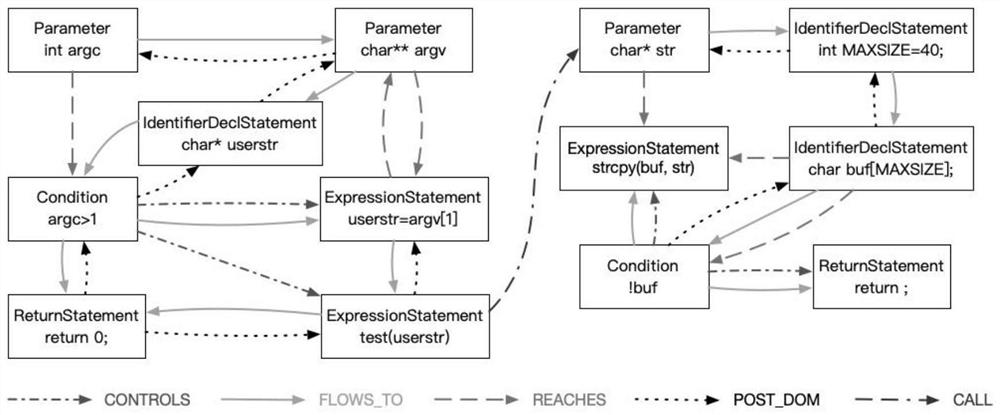
[0057] Taking a source file with 1088 lines of code as an example, the result of slicing the program according to a possible vulnerability key point is only 48 lines of statements, as shown below:
[0058]
[0059] The vulnerability contained in this source file occurs on line 29. When using the strcpy function, strcpy is used without verifying the result of the stonesoup_buffer applied by malloc. If the malloc application fails, the use of strcpy will also cause illegal memory access.
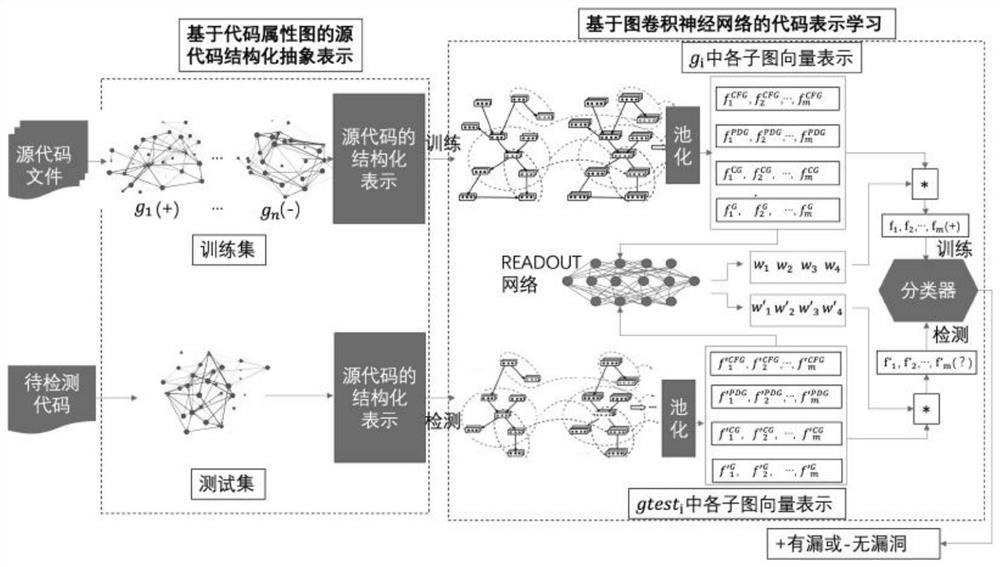
[0060] The method proposed by the present invention can detect that the code contains loopholes related to unsafe function calls after performing graph representation learning on the code based on the graph convolutional network. Long codes like this, when using other traditional deep learning models (such as LSTM and GRU) that use serialized data as input, may lose key contextual information during batch learning, resulting in traditional deep learning models Does not adapt well to codes o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com