A protocol stack-based brute force attack identification method and device
An attack identification and protocol stack technology, applied in the field of computer networks, can solve the problems of lack of relevant key indicators and low flexibility, and achieve the effects of flexible protection mechanism, wide application prospects and wide application scope.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0063] like Figure 1-5 As shown, a protocol stack-based brute force attack identification method includes:
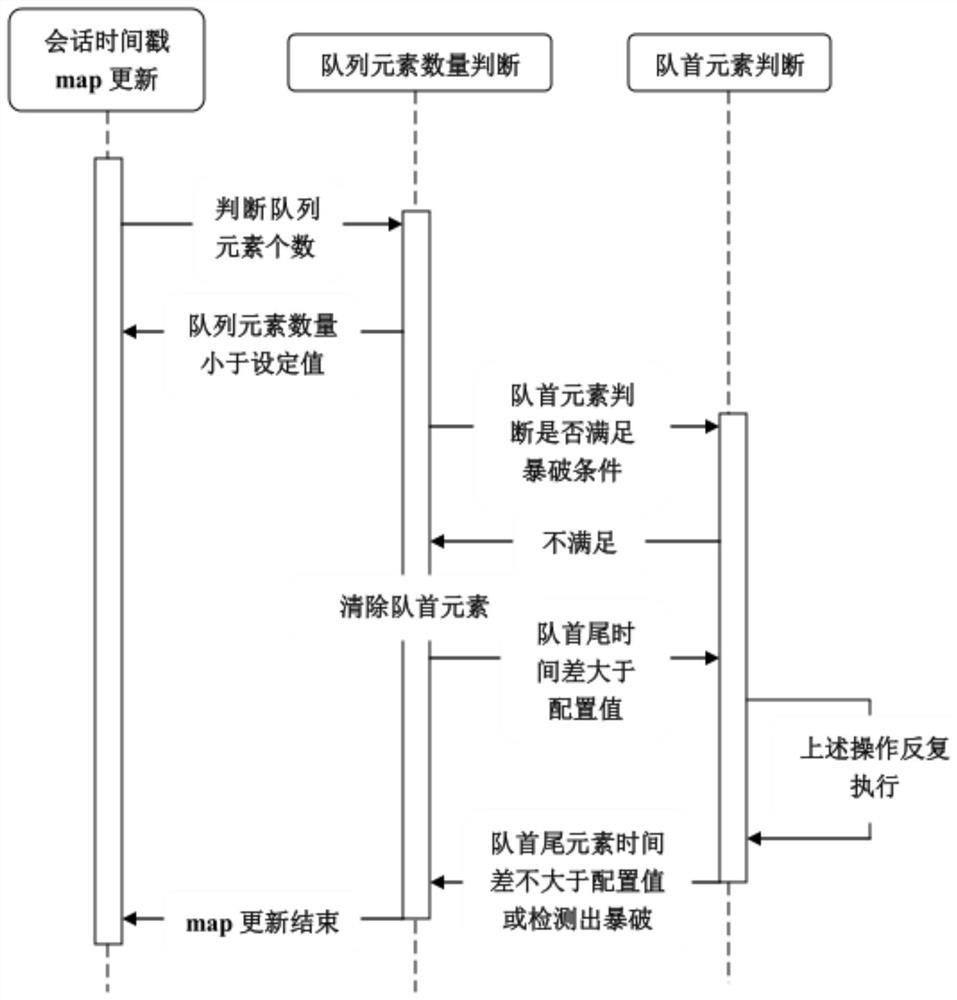
[0064] Read user configuration, set time, frequency, industrial control protocol to be monitored, session timestamp map update mode, and initialize session timestamp map;
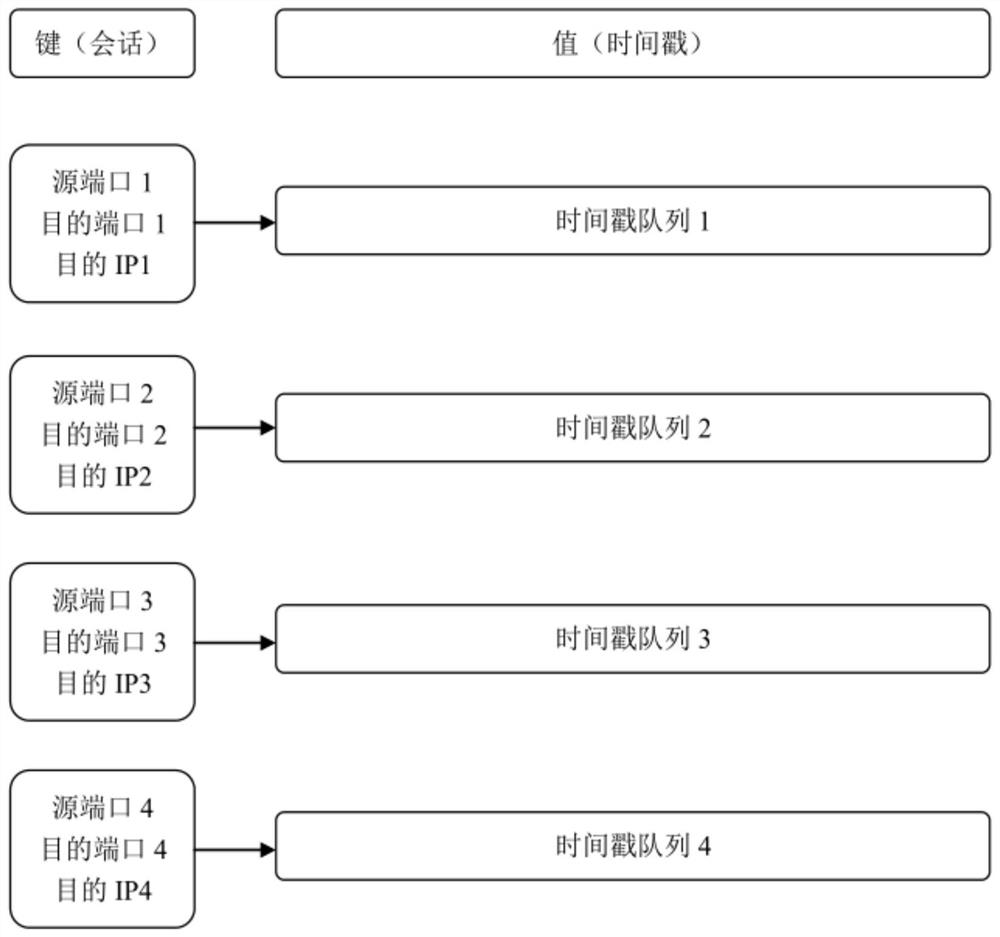
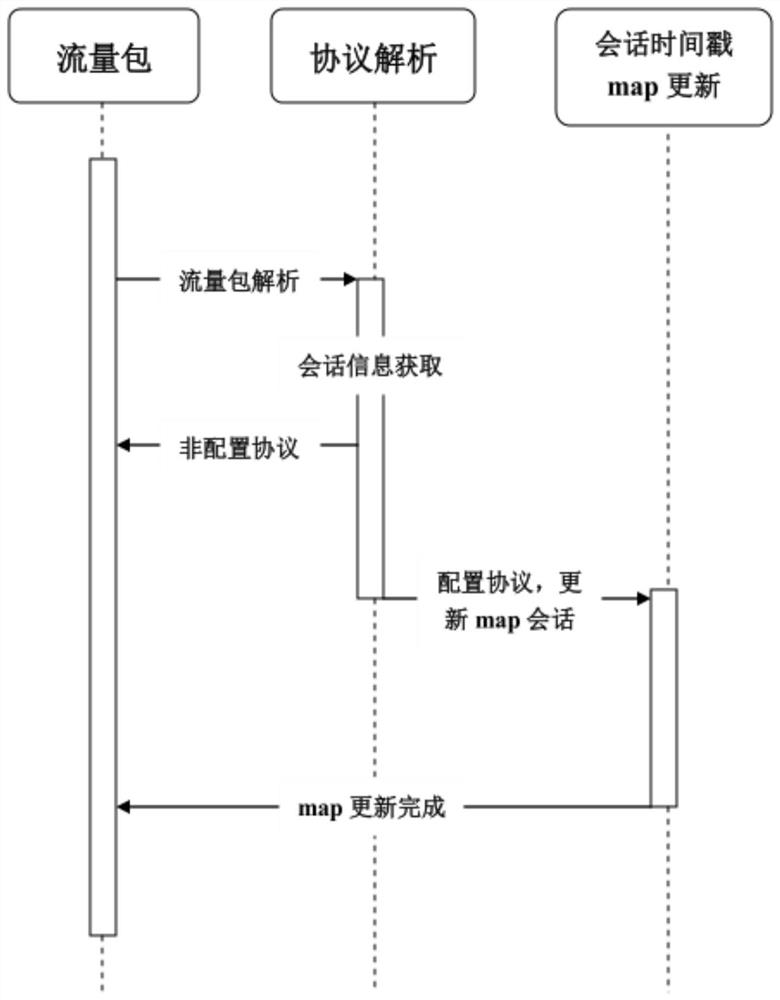
[0065] Obtain the session information and timestamp in the sent data packet; receive the sent data packet and perform TCP protocol analysis on it, obtain the three fields of the source port, destination ip and destination port of the data packet to form a three-element tuple , and the tuple is used as the identifier of a session; for each session, a timestamp queue is maintained to record the arrival time of the session data packets;
[0066] Preferably, when acquiring session information, the protocol type of the data packet is determined through the destination port, and it matches the protocol information configured by the user; if the protocol is not in the protocol list configured by the user,...
Embodiment 2
[0076] like Image 6 As shown, a protocol stack-based brute force attack identification device includes:
[0077] User configuration initialization module 1, used to read user configuration, set time, frequency, industrial control protocol to be monitored, and session timestamp map update mode;
[0078] User configuration initialization module 1 can be X86_64 server, CPU: above 1GHz, memory: above 1G;
[0079] Protocol parsing initialization module 2, used to create real-time packet capture environment, protocol stack initialization, brute force attack detection module loading and initialization;
[0080] The protocol analysis initialization module 2 can be an X86_64 server, CPU: above 1GHz, memory: above 1G, hard disk: above 20G, and configured with a network environment;
[0081] Session information acquisition module 3, for acquiring session information and timestamp in the sent data packet;
[0082] The session information acquisition module 3 can be an X86_64 server, C...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com