An Image Encryption Method Based on Hyperchaotic System Projection Synchronization
An encryption method and ultra-chaotic technology, applied in the field of information technology security, can solve problems such as inability to resist chosen plaintext attacks and known plaintext attacks, confusing operation of missing image pixel positions, cumbersome encryption methods, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
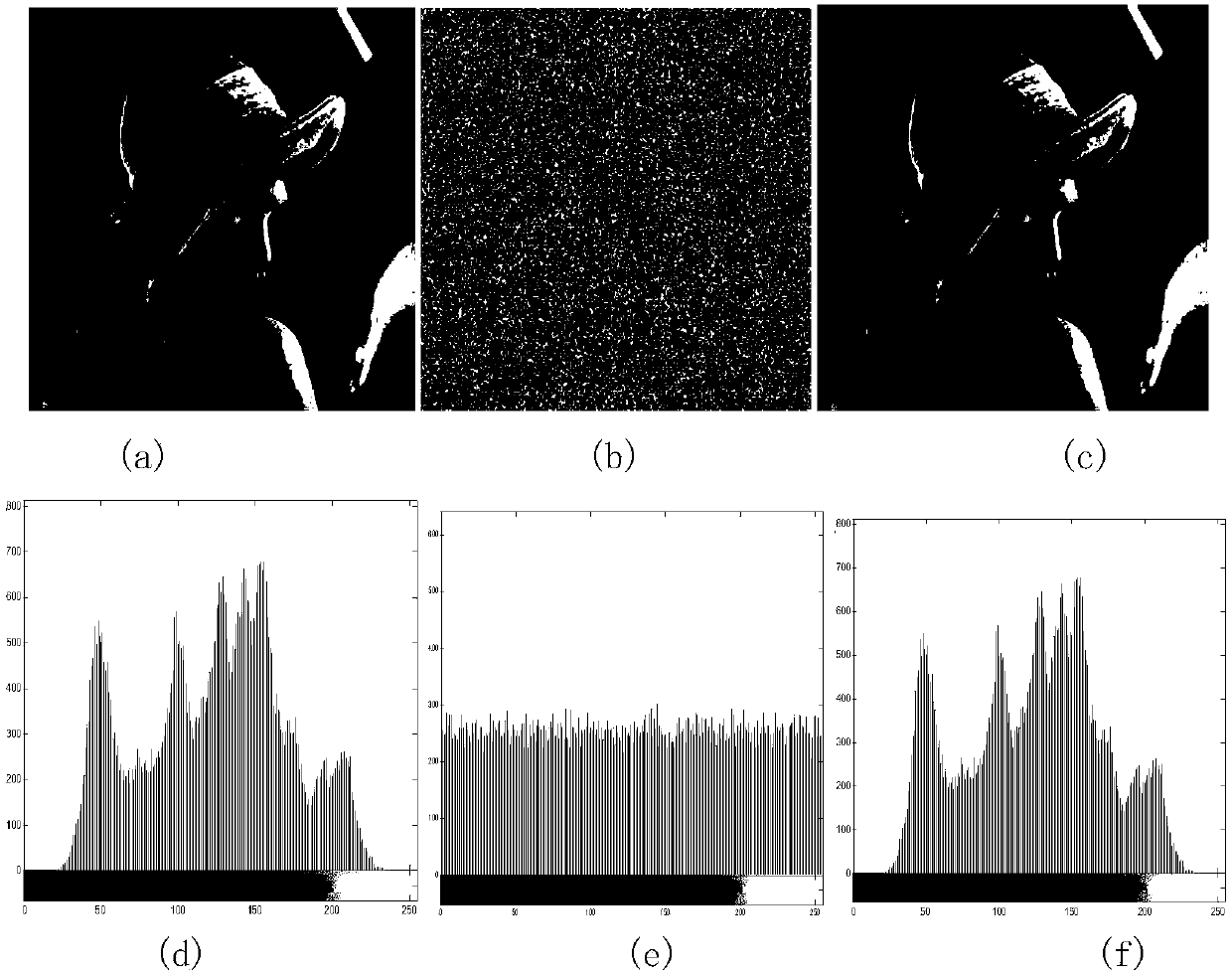
[0109] Experimental environment: The hardware testing platform of this experiment is: Inter(R) Core(TM) i7-4500U CPU, main frequency 1.8Ghz, memory 8.0GB; software platform is: Windows10 operating system and Matlab2012a. The simulation image adopts the Lena image whose gray scale is 256 and the size is 256×256.
[0110] Embodiments of the present invention will be further described below in conjunction with the accompanying drawings.
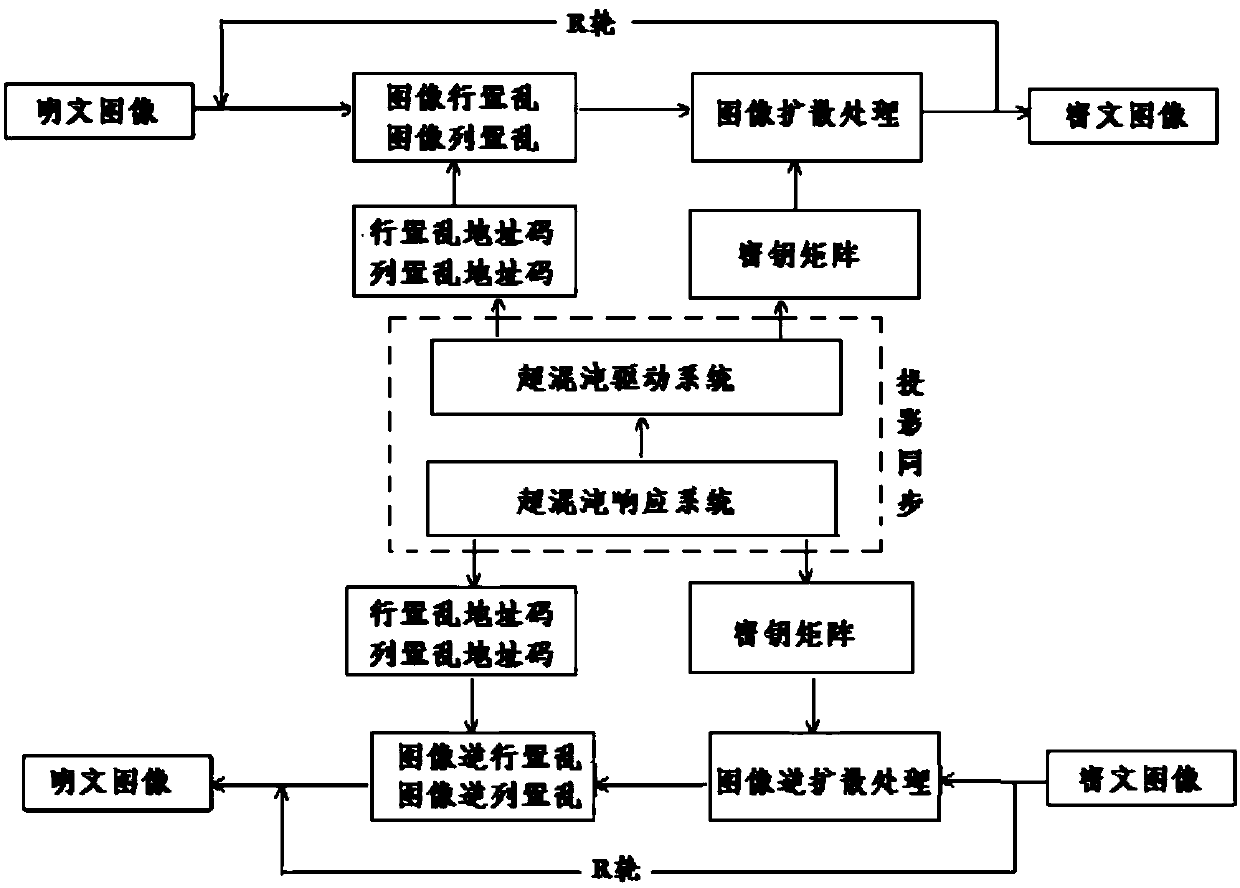
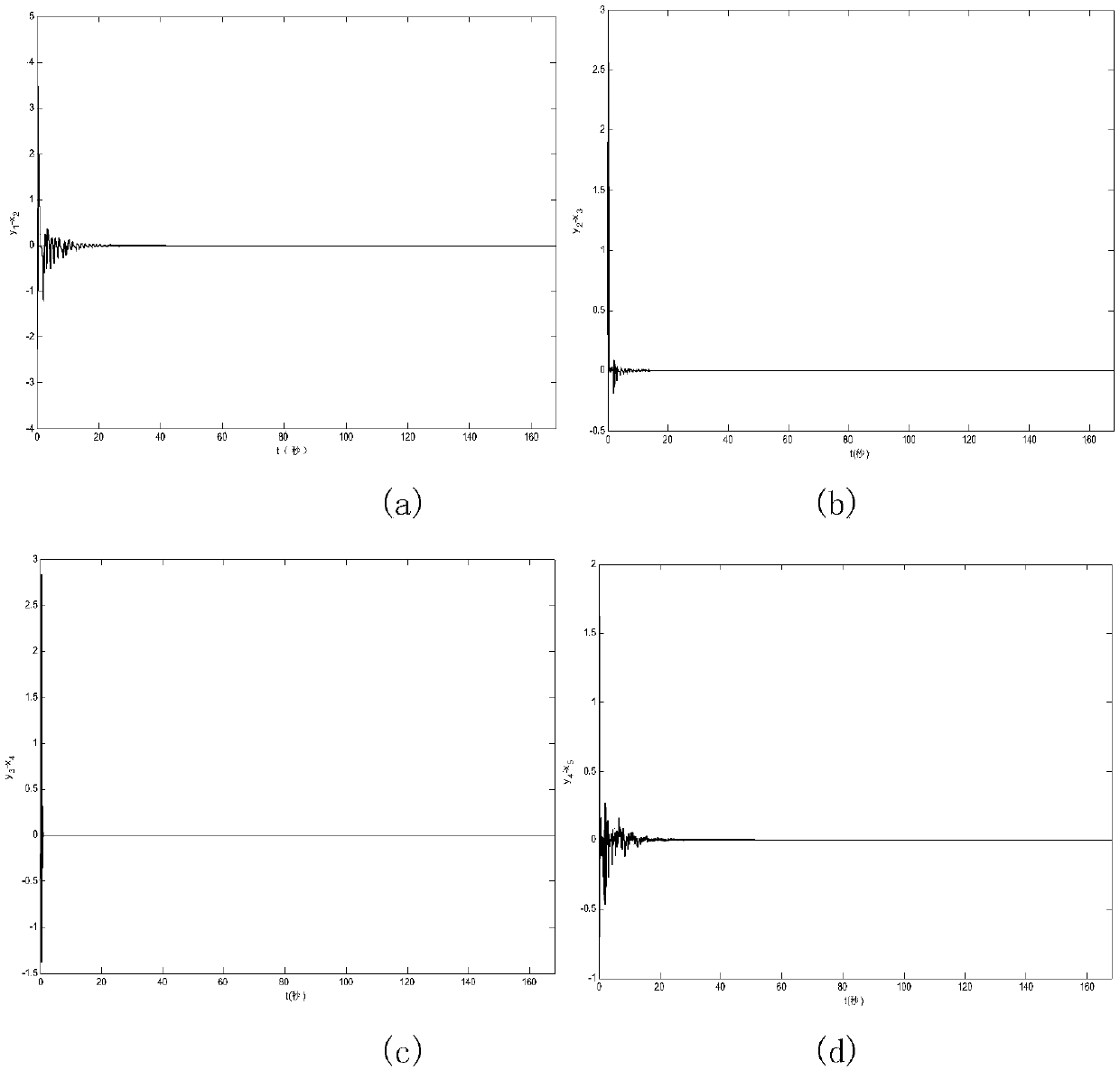
[0111] The image encryption method based on the hyperchaotic system projection synchronization of the present invention includes the process of encrypting and decrypting the original plaintext image.
[0112] The encryption process specifically includes the following steps:
[0113] 1), plaintext image quantization processing: for the original plaintext image whose pixels are m×n and the gray scale level is G, obtain its two-dimensional pixel value matrix A, and use the original plaintext image as the current image;
[0114] In this embodiment...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com