A cross-domain security authentication method based on information separation management
An authentication method and domain security technology, applied in key distribution, which can solve the problems of complex password settings, threats to account security, threats to "password" security, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0084] A cross-domain security authentication method based on information separation management, which includes a registration step and a login step;
[0085] Registration steps include:
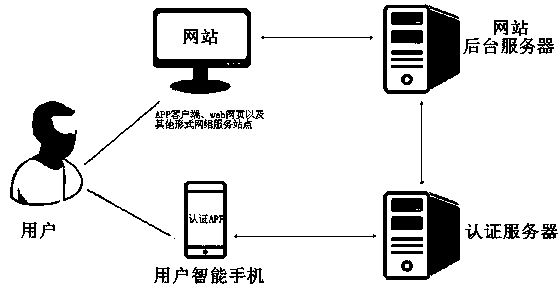
[0086] S1-1. Various websites (including APP clients, web pages, and other forms of network service sites) that need to activate authentication services send requests to the authentication server of the security authentication system to apply for activation of security authentication services; the authentication server authorizes each website to access authentication server permissions;
[0087]S1-2. The user uses a network terminal to access any website, and registers an account on the website (when registering an account on a website, common input information may include mobile phone number, ID number, address, email address and / or user name, etc. One or more of them, the website assigns a registered account IDa to it; wherein, the registered account IDa or other identity information that...
Embodiment 2
[0101] On the basis of Embodiment 1, in order to prevent the data transmitted between the authentication server and the website, between the authentication APP and the authentication server from being intercepted;
[0102] Step S2-1 also includes:
[0103] The authentication server issues the key K0 to the background server of the website;
[0104] The background server of the website uses the key K0 to encrypt the visual verification information Str1 and the user code Ca, and then encrypts and transmits it to the authentication server through SSL encryption. After receiving it, the authentication server decrypts it with the key K0 to obtain the visual verification information Str1 and the user code Ca and recorded in the database;
[0105] After the authentication APP establishes communication with the authentication server, when accessing the authentication server for the first time, the authentication server issues a key K1 to the authentication APP; in step S2-2, the auth...
Embodiment 3
[0107] On the basis of Embodiment 1, in order to confirm the authenticity of the feedback information sent back by the authentication server and prevent the authentication server from being forged, in the registration step, steps S1-4, S2-1, and S2-2 also include:
[0108] S1-4, the background server of the website also generates a random character string Str2 for the username Na;
[0109] S2-1. The background server of the website also transmits the random character string Str2 to the authentication server;
[0110] S2-2. After the authentication server associates the user code Ca of the website, the hardware device identification code IDp, and the identification code X, it also includes:
[0111] A. The authentication server transmits the random character string Str2 and the identification code X to the authentication APP installed on the mobile terminal whose corresponding hardware device identification code is IDp;
[0112] B. The authentication APP uses obfuscation techn...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com