Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
33results about How to "Limited computing power" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
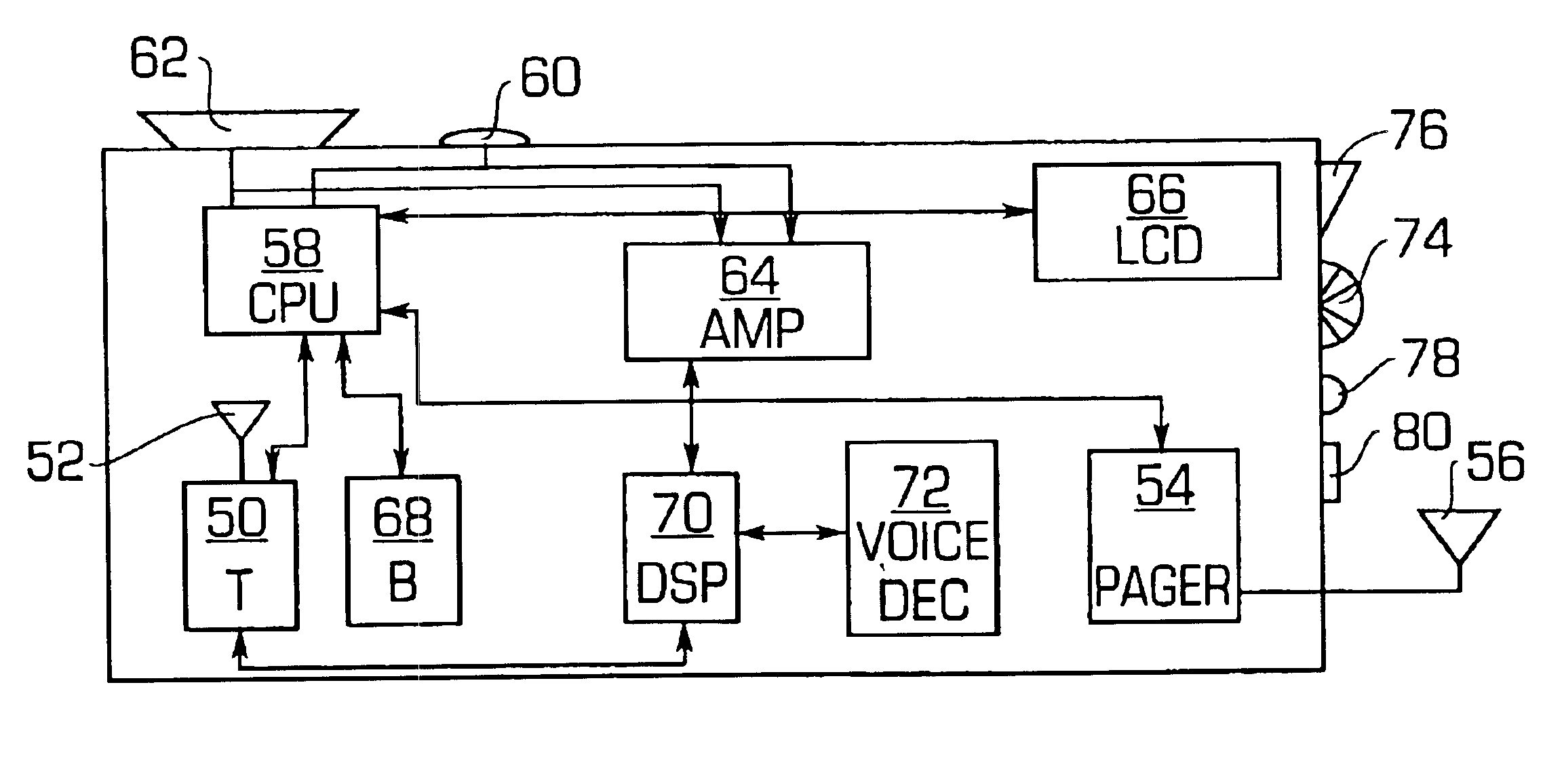
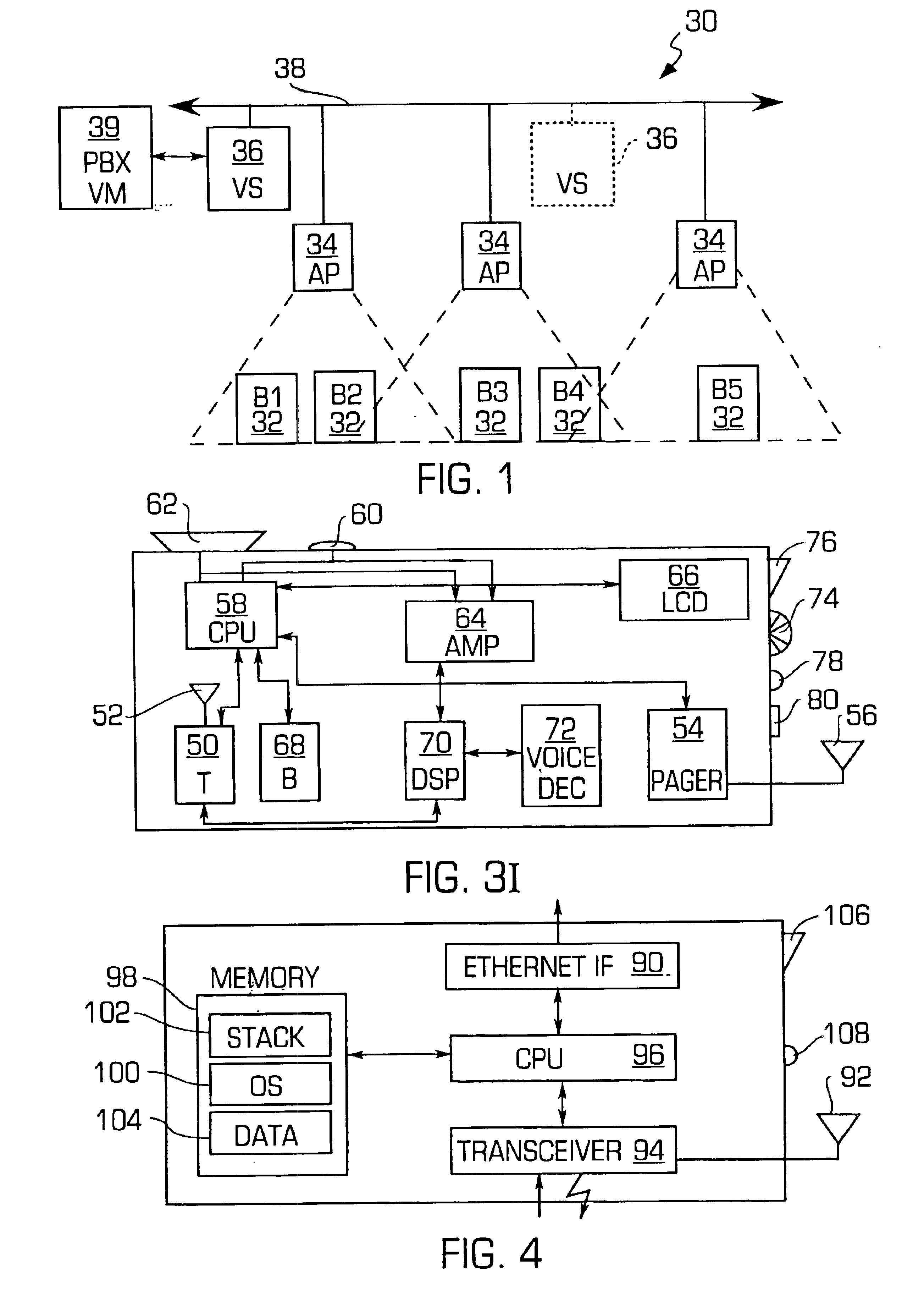
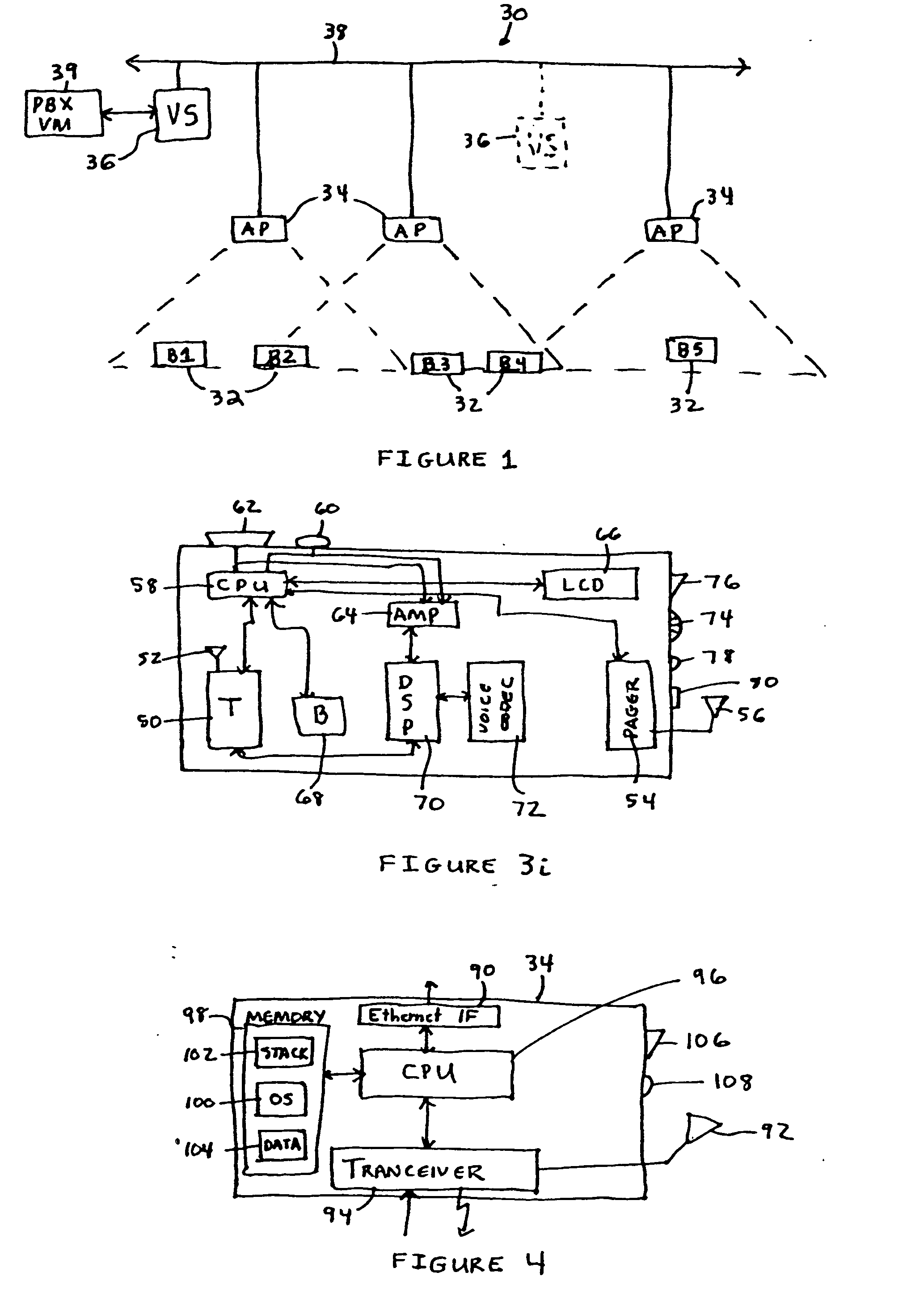
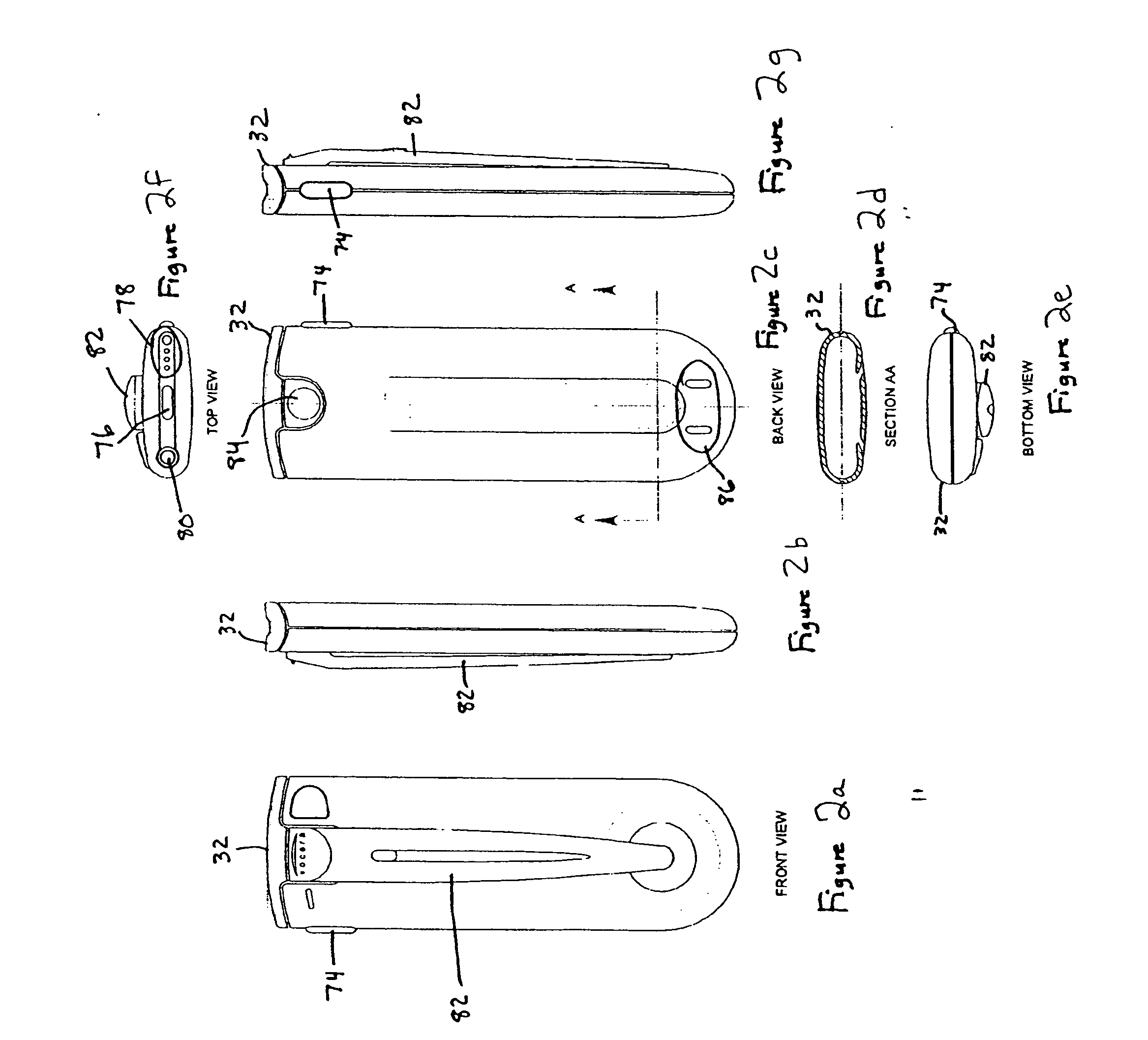
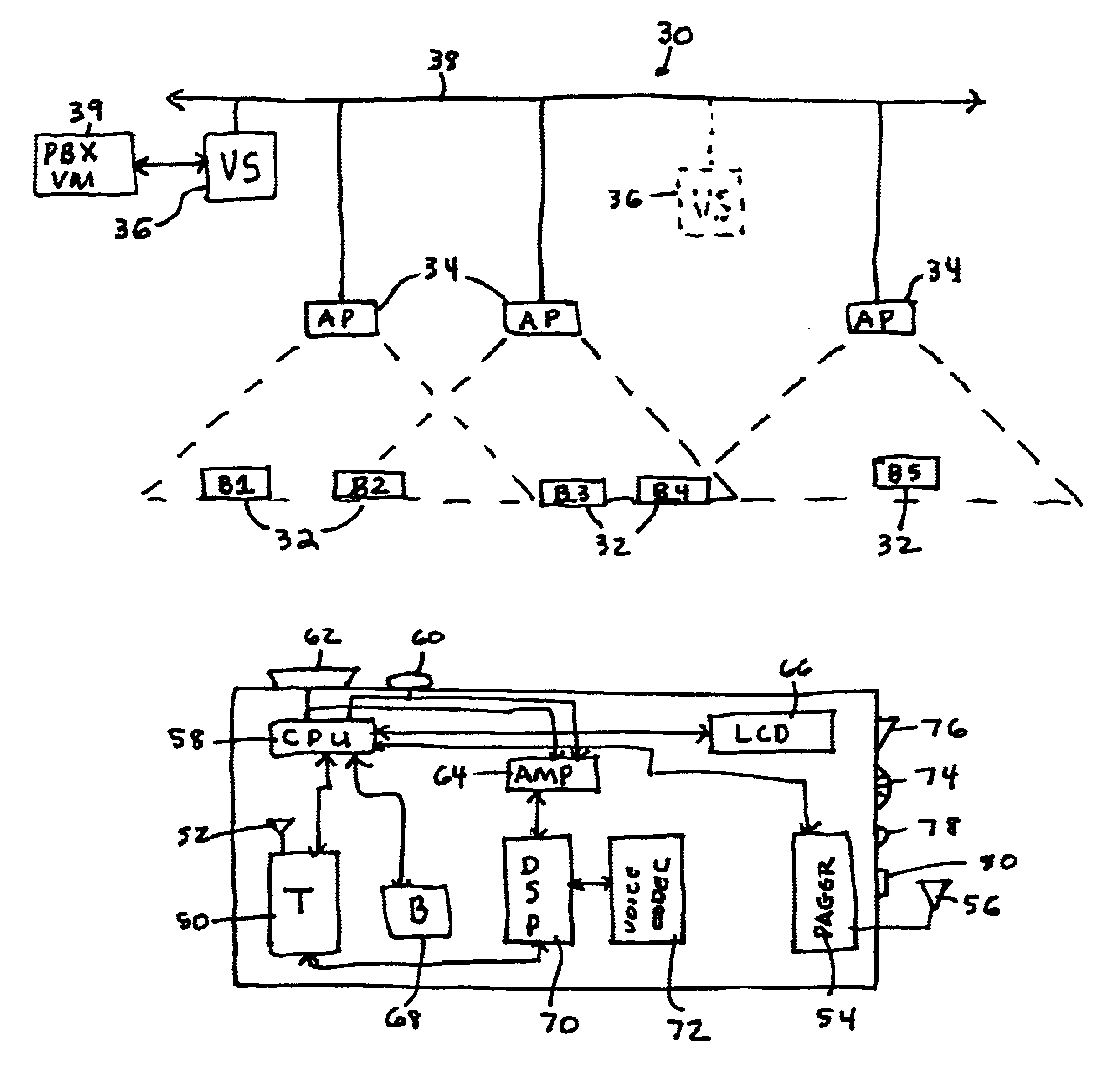
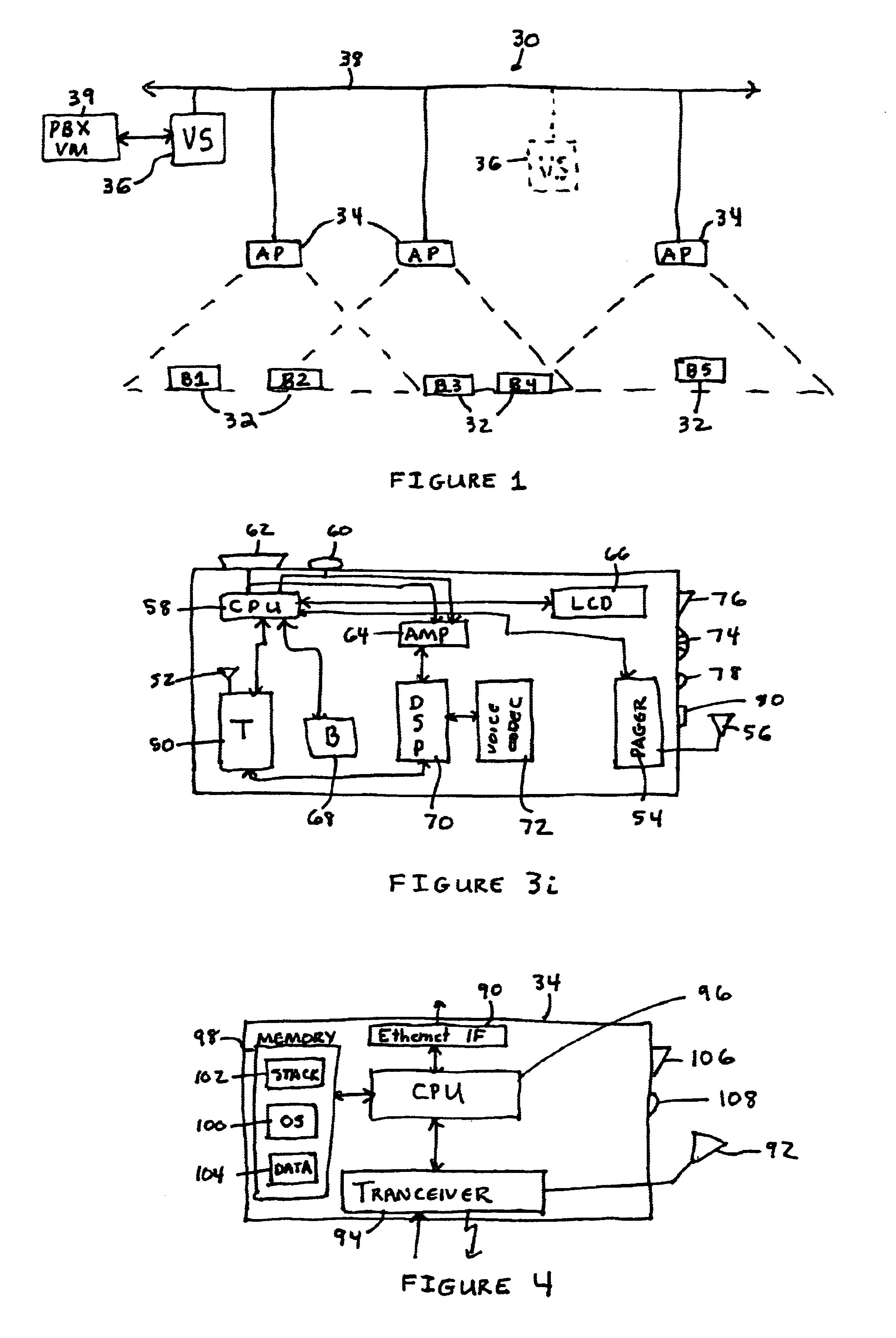
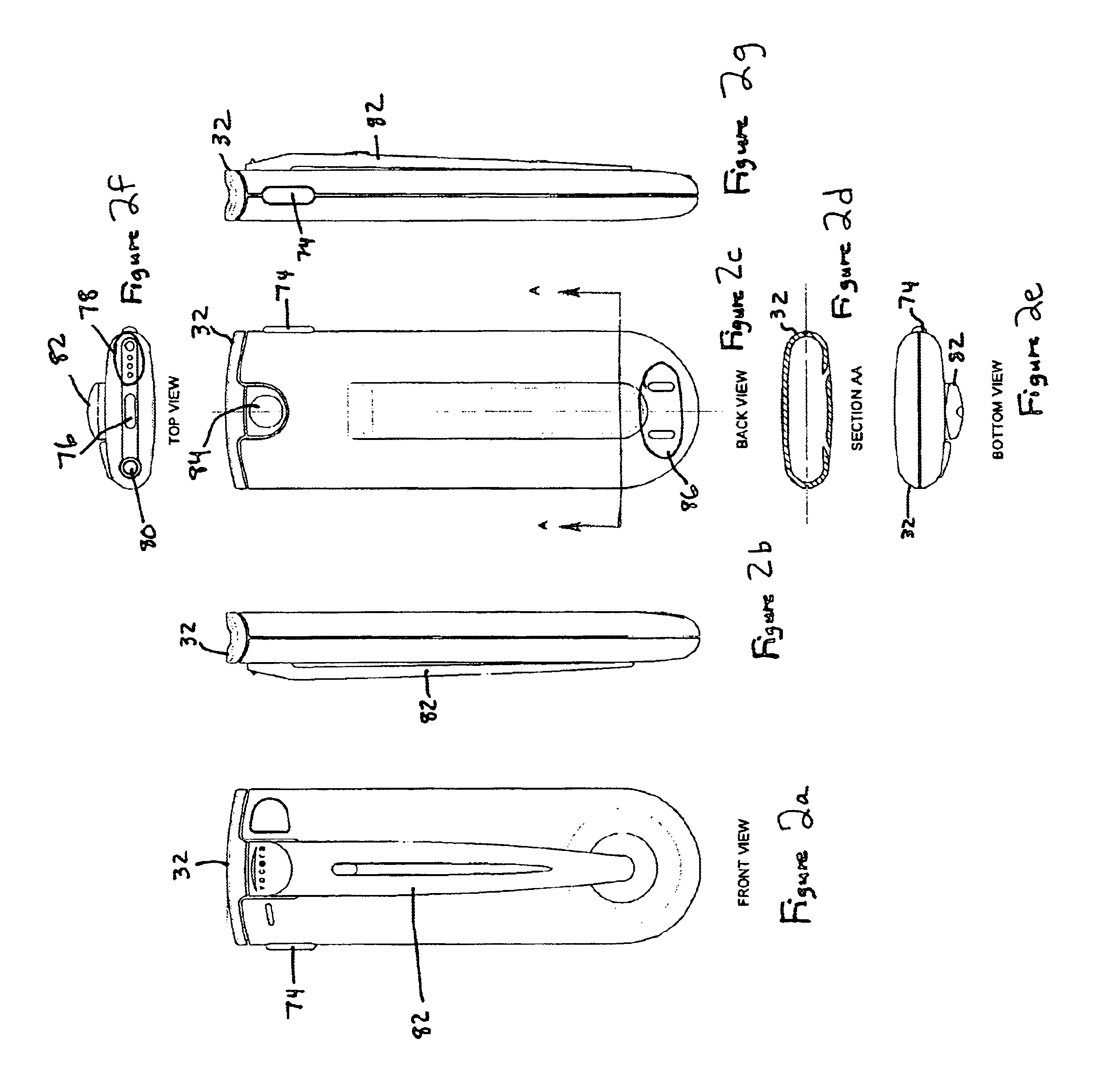
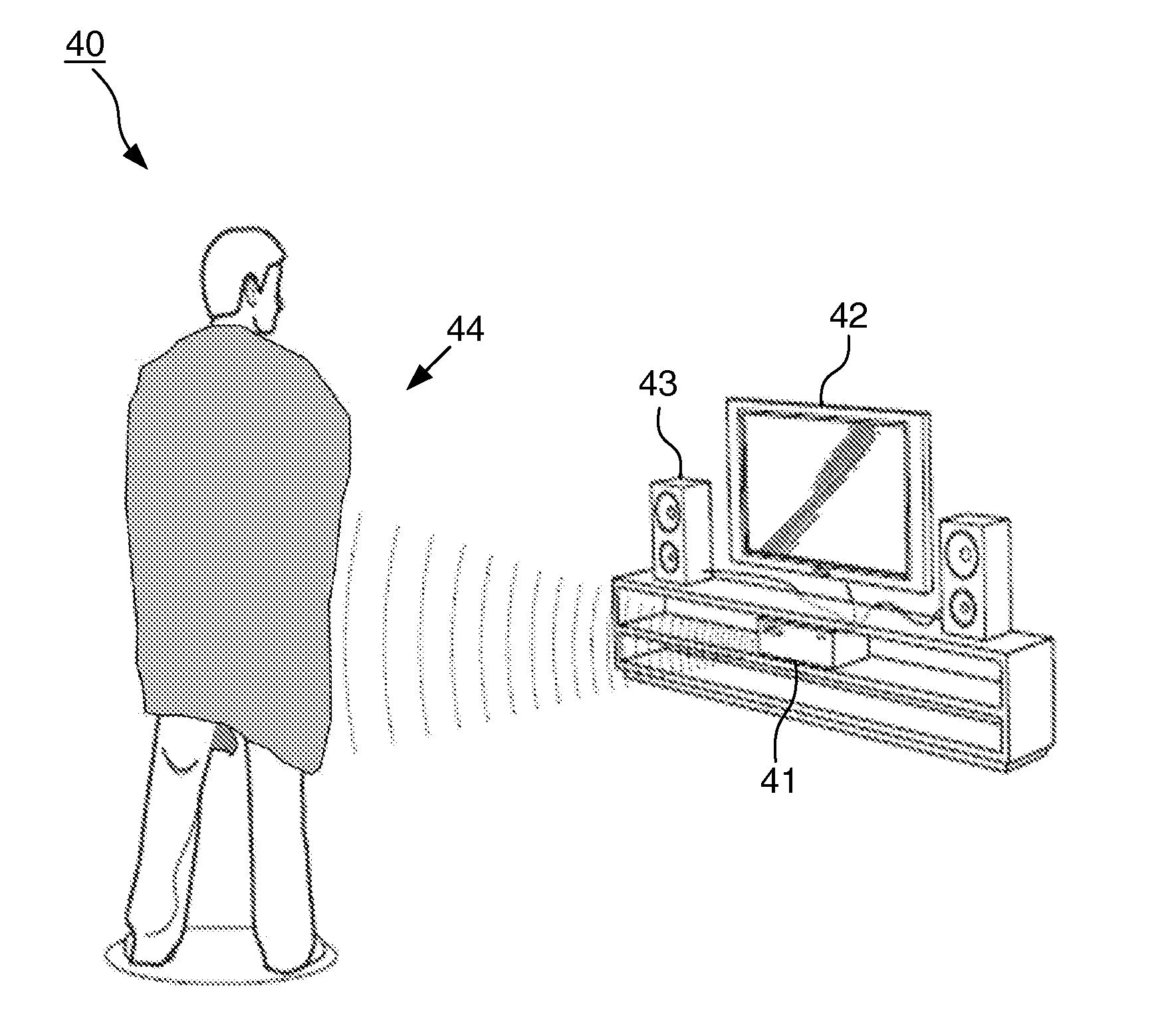
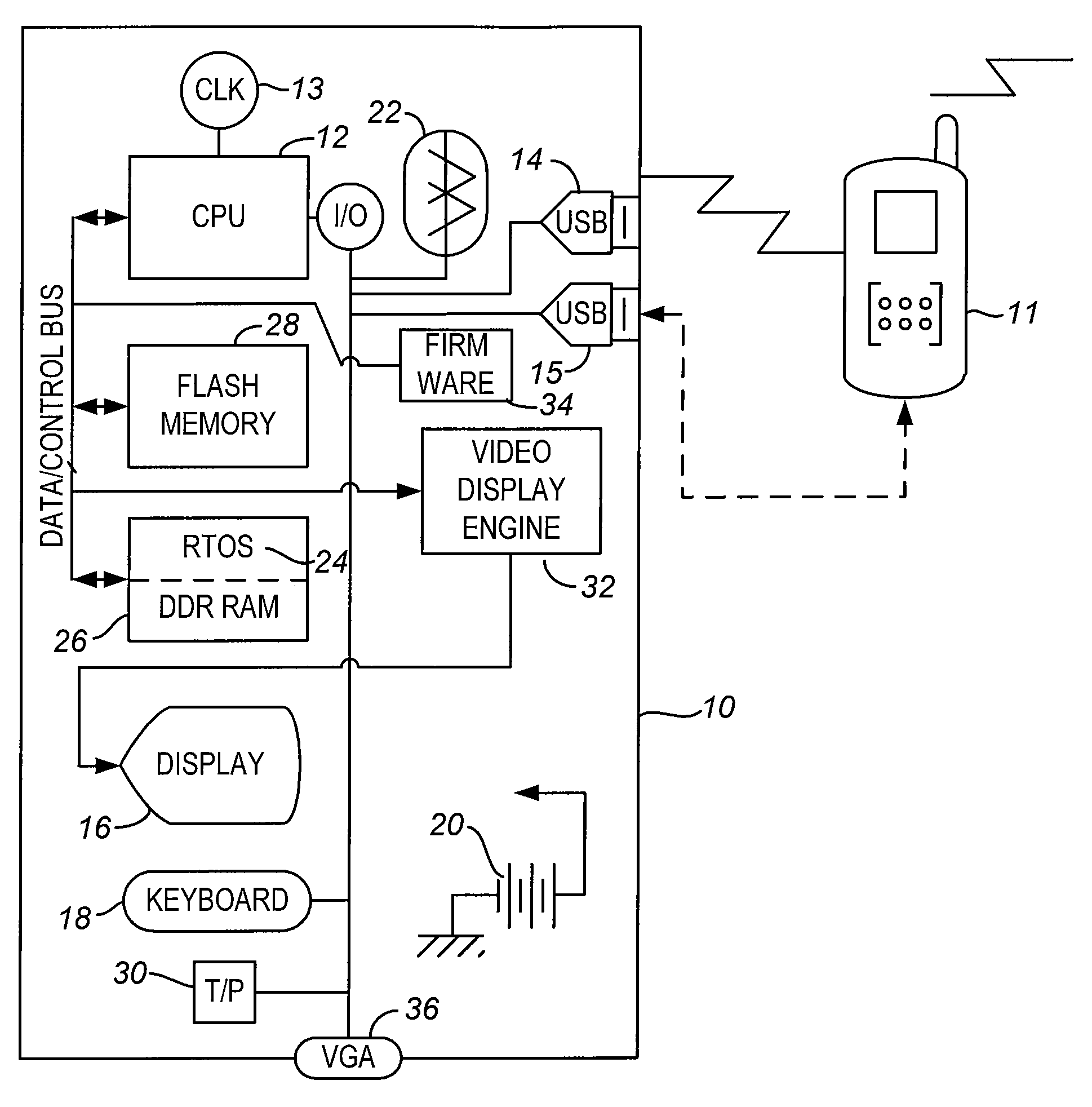
Voice-controlled wireless communications system and method
InactiveUS6892083B2Limited computing powerLimited rangeCordless telephonesSubstation speech amplifiersCommunications systemWireless access point
A wireless communication system has a central computer, one or more wireless access points and one or more personal badges that communicate wirelessly with the one or more wireless access points. The badges provide the user with a communications device that permits the user to initiate telephone calls and conferences, receive telephone calls, receive pages and be located within a particular environment.
Owner:VOCERA COMM
Voice-controlled wireless communications system and method
InactiveUS20050170863A1Limited computing powerLimited rangeSubstation speech amplifiersDevices with wireless LAN interfaceCommunications systemCommunication device
A wireless communication system has a central computer, one or more wireless access points and one or more personal badges that communicate wirelessly with the one or more wireless access points. The badges provide the user with a communications device that permits the user to initiate telephone calls and conferences, receive telephone calls, receive pages and be located within a particular environment.
Owner:VOCERA COMM
Voice-controlled wireless communications system and method
InactiveUS6901255B2Limited compute powerLimited computing powerCordless telephonesSubstation speech amplifiersSpeech controlWireless access point
A wireless communication system has a central computer, one or more wireless access points and one or more personal badges that communicate wirelessly with the one or more wireless access points. The badges provide the user with a communications device that permits the user to initiate telephone calls and conferences, receive telephone calls, receive pages and be located within a particular environment.
Owner:VOCERA COMM
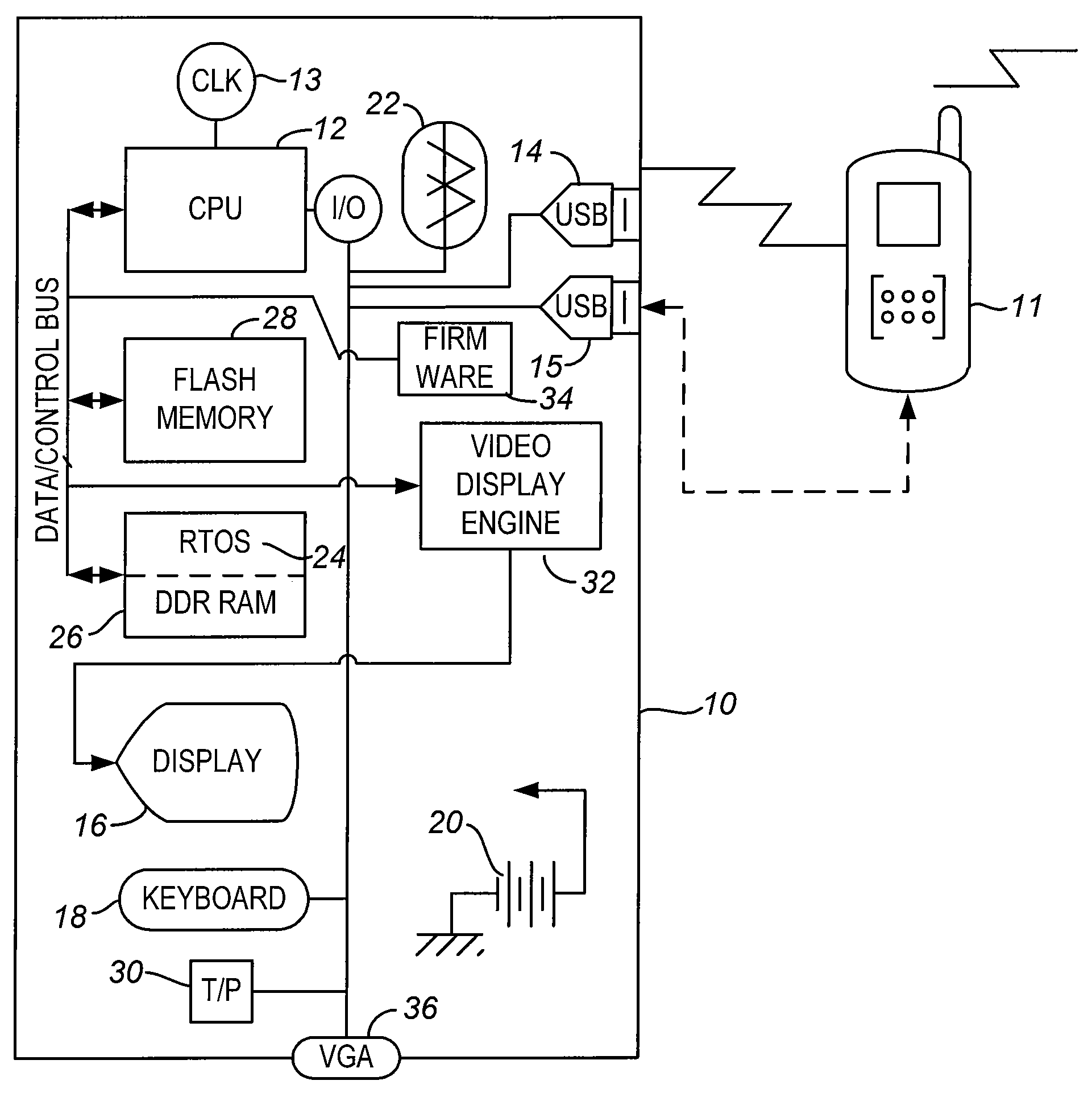
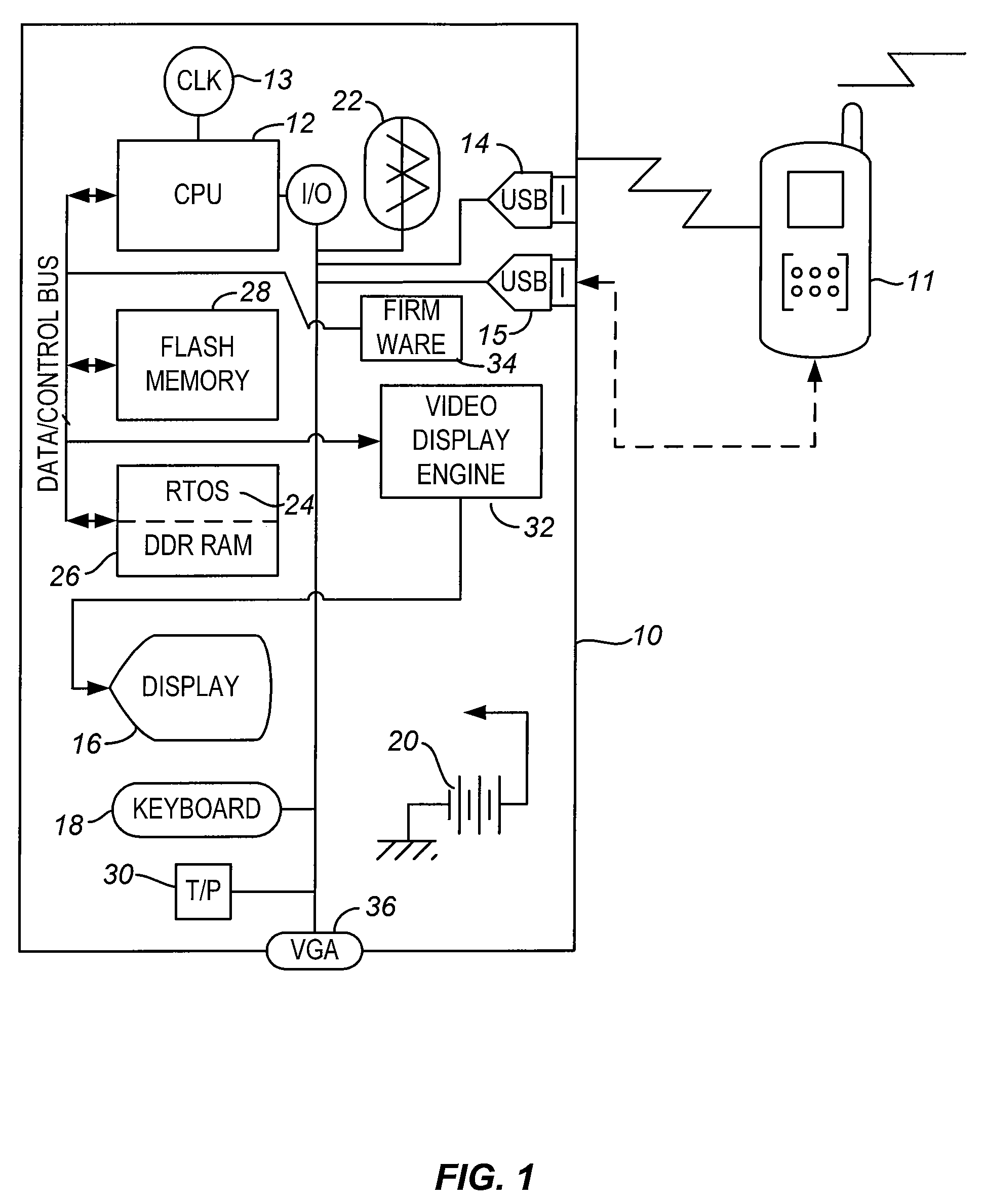
Client device for cellular telephone as server
InactiveUS20100063994A1Easy to processAssure integrityMultiple digital computer combinationsDevices with bluetooth interfacesOperational systemUser input
A new class of thin client called a trans client for operation with a smart cellular telephone as its server does not contain its own user interface (UI) and operating system (OS) and has no capability to run user programs as a standalone apparatus. Its purpose and capability is to display remote content and to provide user input interface. It is built with the slowest processing and lowest power consumption possible with the lowest cost and has security features to assure integrity of operations.
Owner:CELIO TECHNOLOGY CORPORATION
Foldable tactile display
InactiveUS9134796B2Function increaseLimited computing powerInput/output for user-computer interactionGraph readingTouch SensesDisplay device
The present invention relates to a foldable tactile display (1) and a method of operating it. The foldable tactile display comprises a plurality of actuators (2), one or more sensors (3-6), and a computing unit (7). The computing unit is able to control the plurality of actuators in response to the received command signals and sensor signals. In an embodiment, the tactile foldable display is used in connection with multimedia content. The foldable tactile display may be in the form of a tactile blanket.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
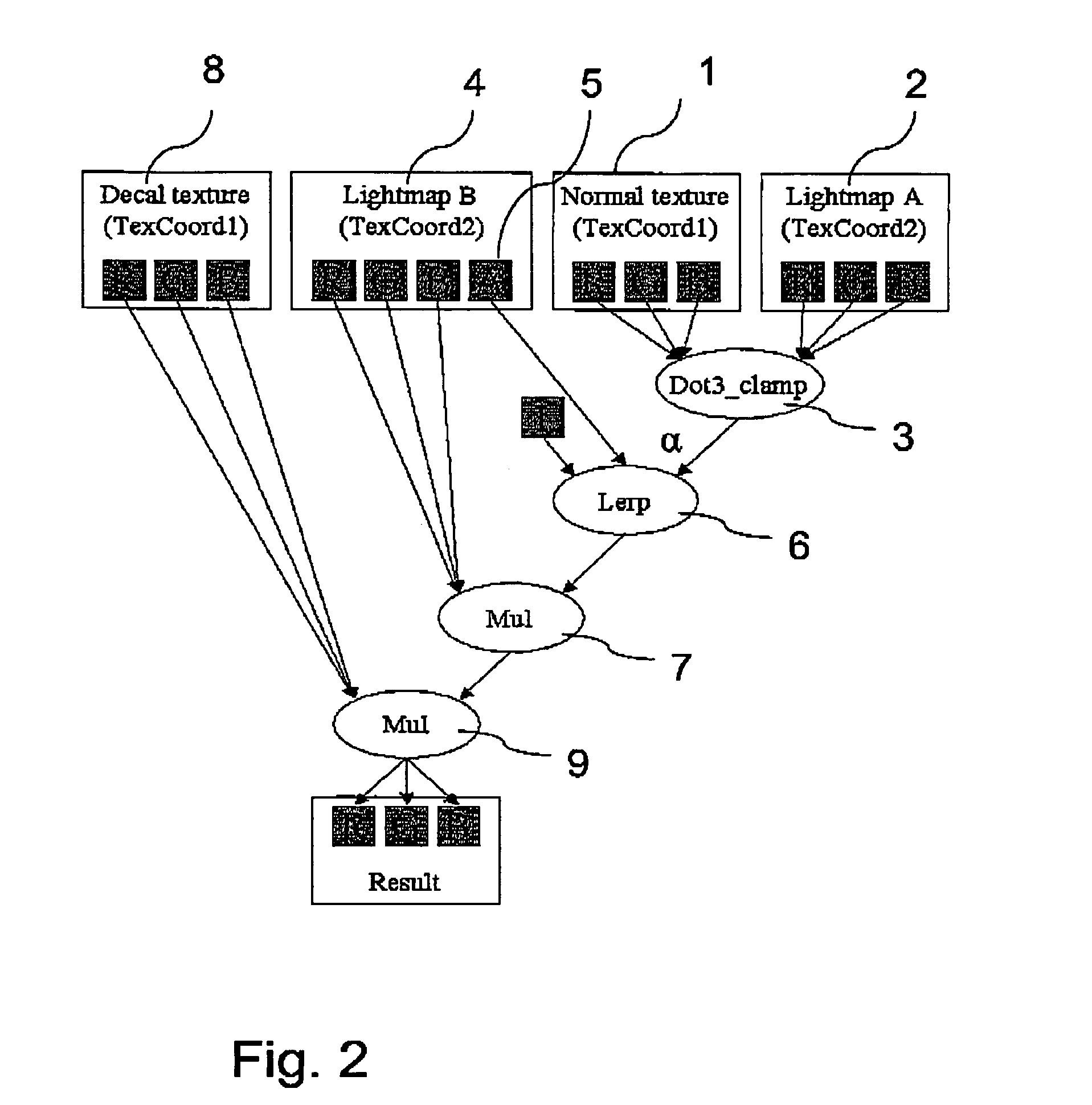
Method and computer program product for lighting a computer graphics image and a computer
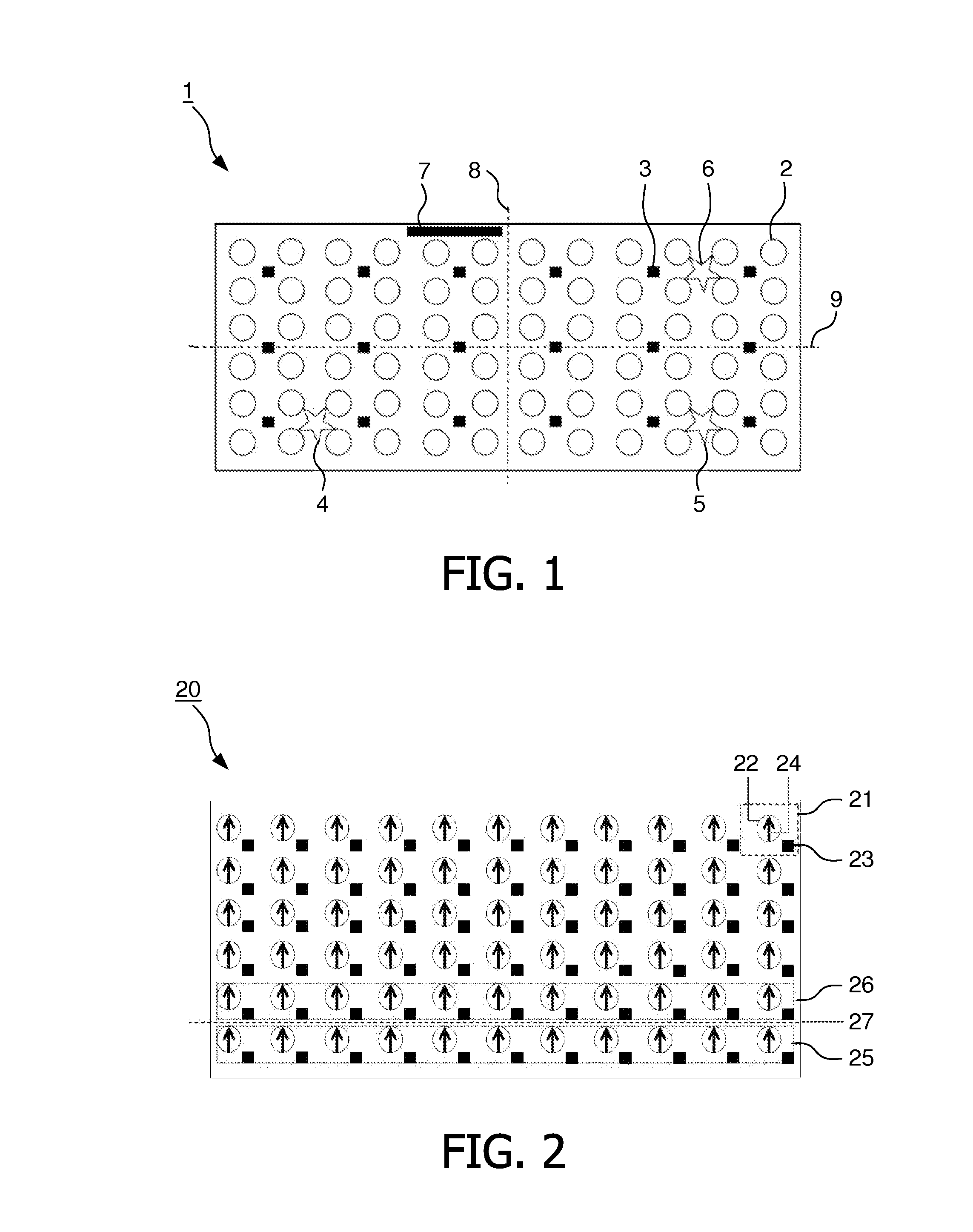
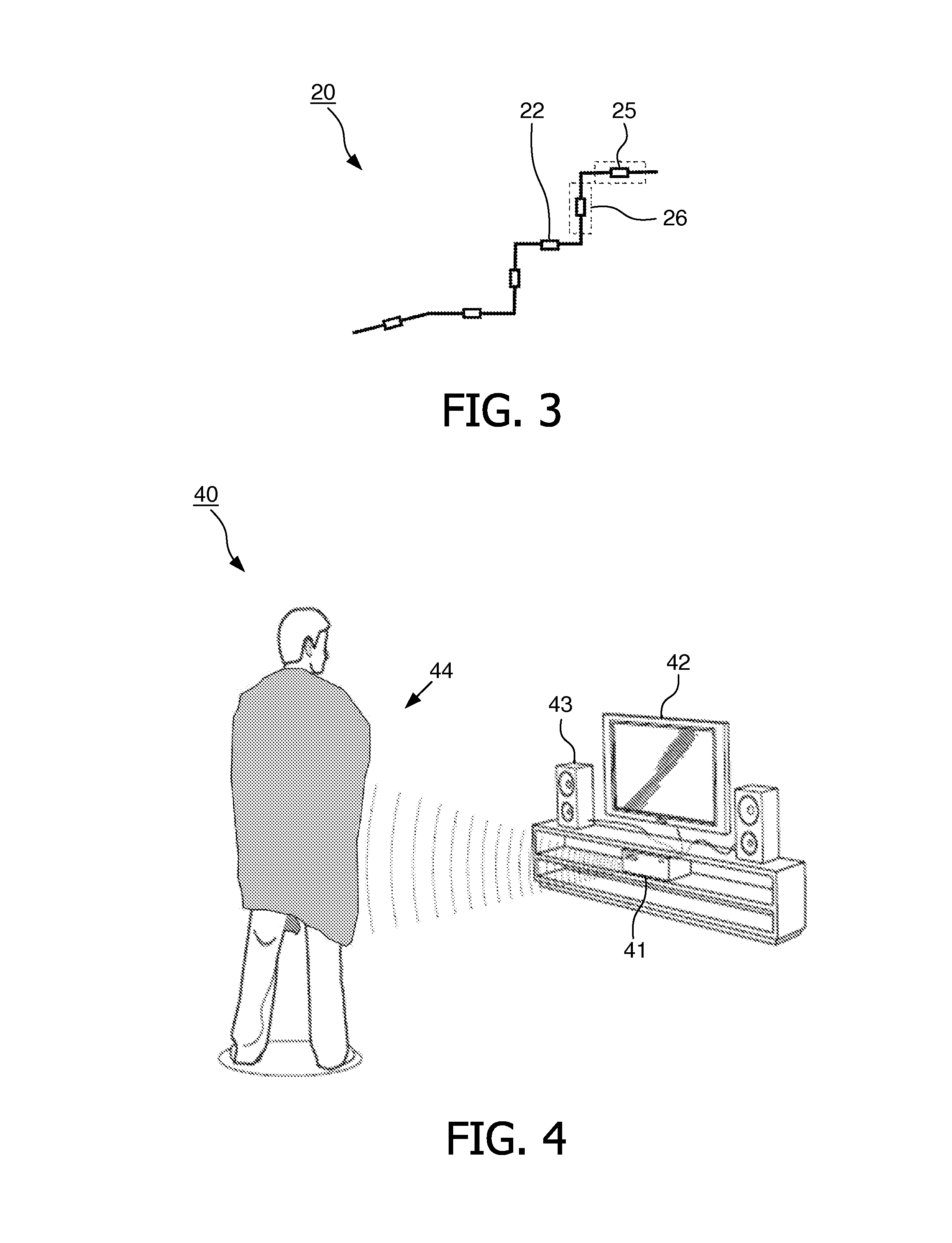
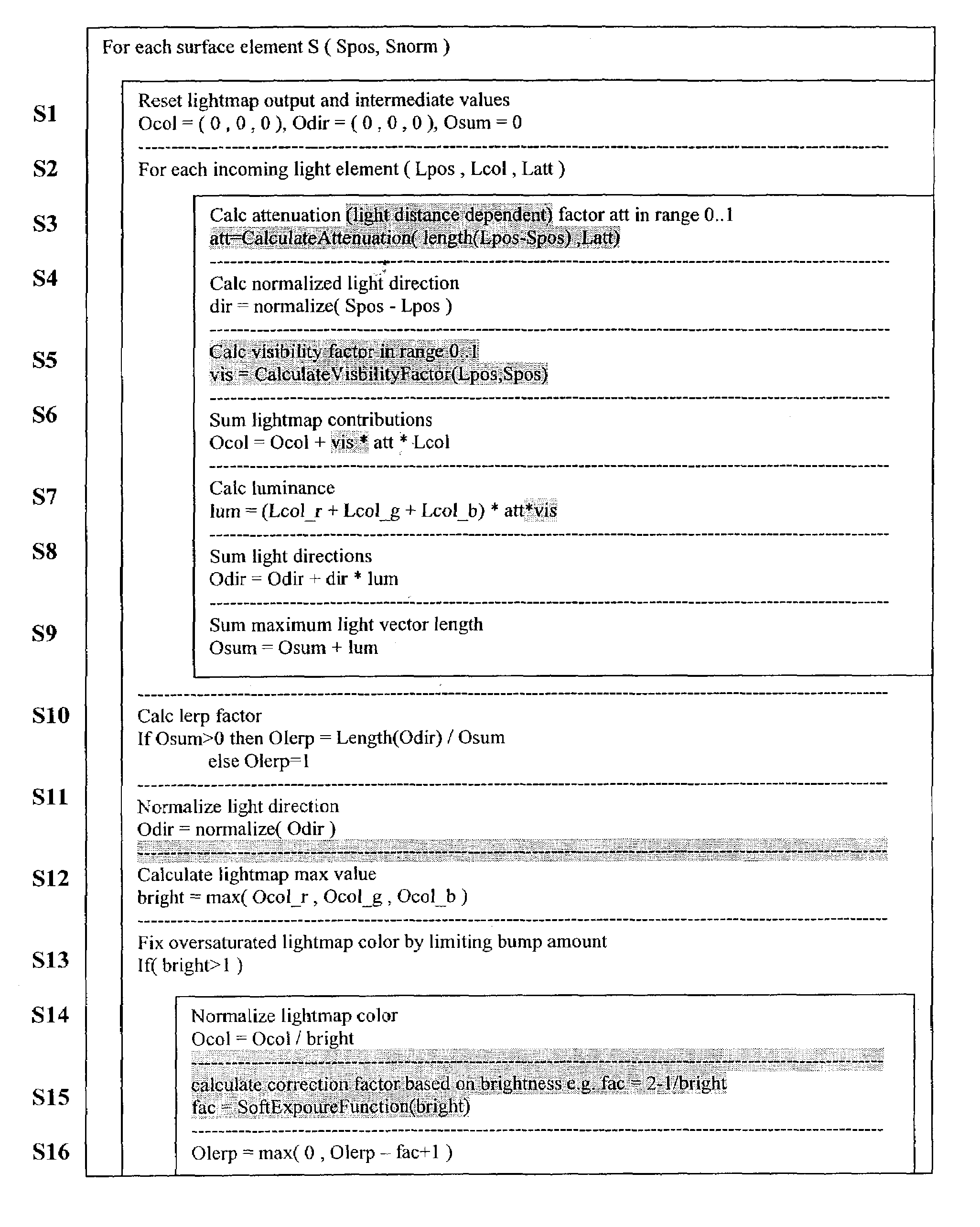
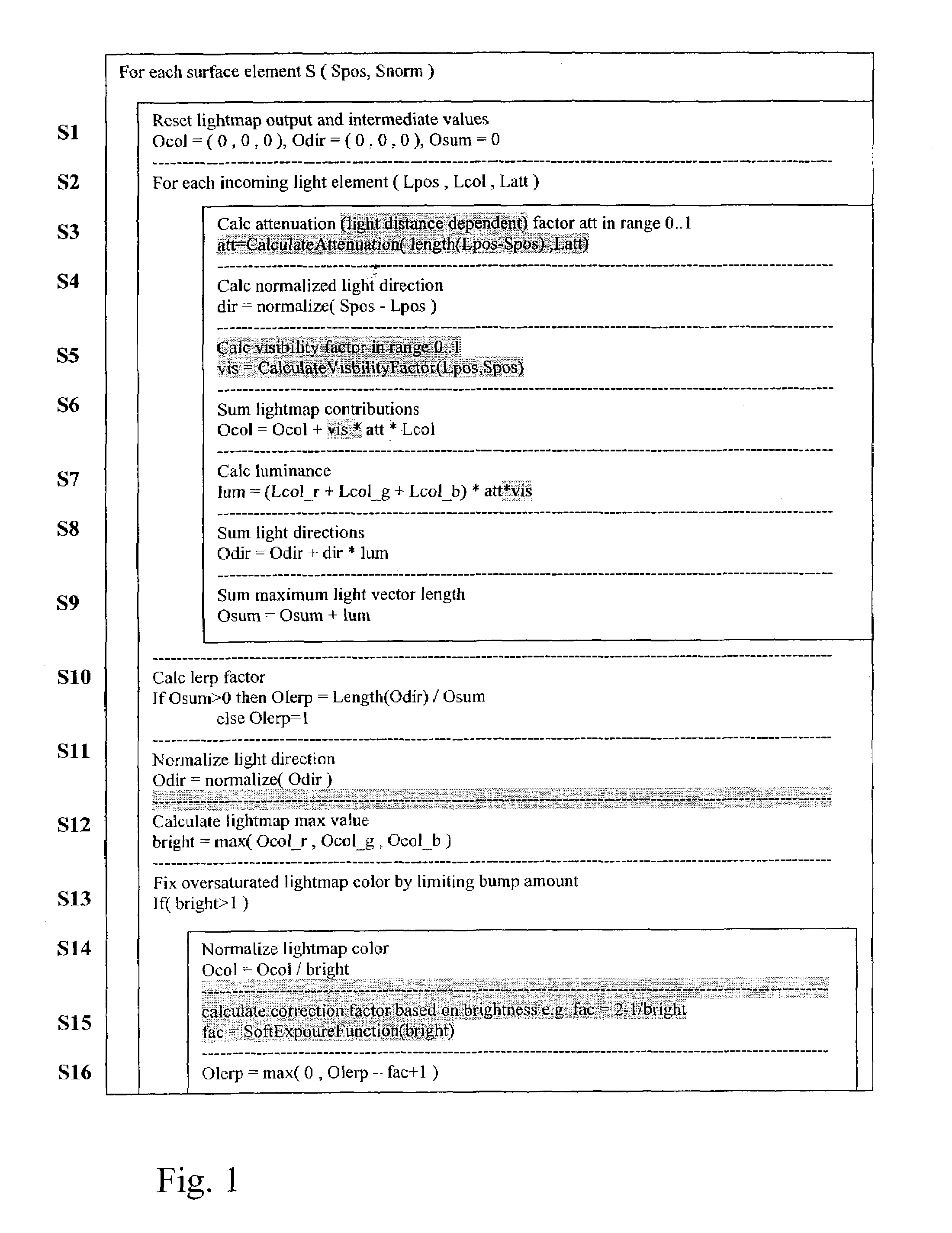
The invention relates to a method to and a computer program product for lighting a computer graphics image to be rendered. It is assumed that a plurality of light sources illuminate one or more objects of the scene to be rendered thus causing a complex lighting situation. For reducing the complexity of the lighting situation and saving computing time the lighting condition is pre-calculated by approximating at least two and preferably all light sources by a single fictitious light source in a pre-calculating step. In the step of pre-calculating, there is computed an approximated light direction for at least two selected ones of the light sources and an approximated light color for the selected light sources by weighting color contributions thereof. The step of pre-calculating is performed for selected areas of a surface of objects present in the scene and results in coefficients that are stored, for these selected areas, in a lightmap or in vertices representing the object surface. The coefficients are retrieved by subsequent method steps for rendering the computer graphics image using the approximated light condition. The invention applies not only to diffuse lighting but is, with a minor modification, also of use for calculating specular lighting.
Owner:CRYTEK IP HLDG
Deletion of content in digital storage systems
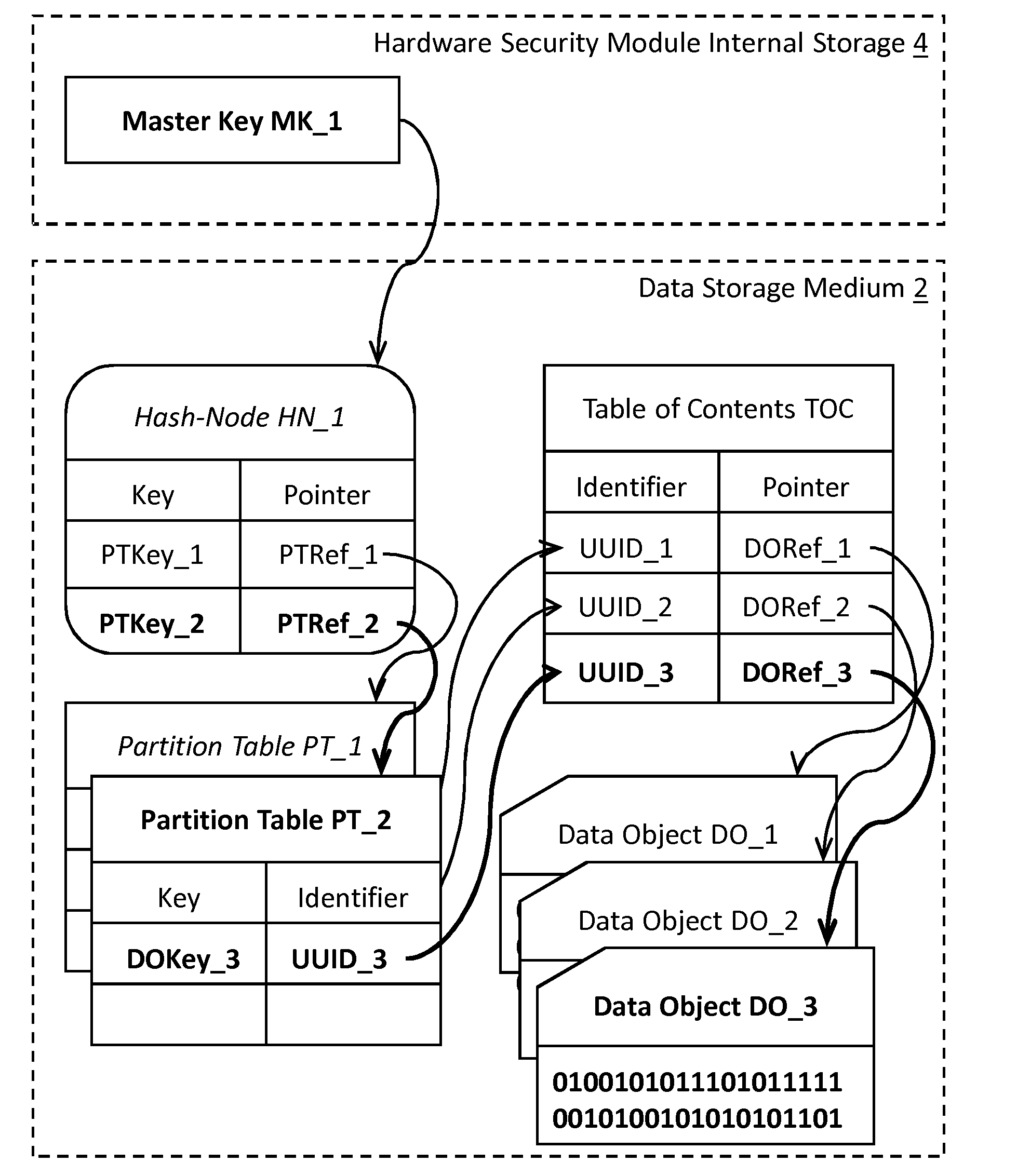
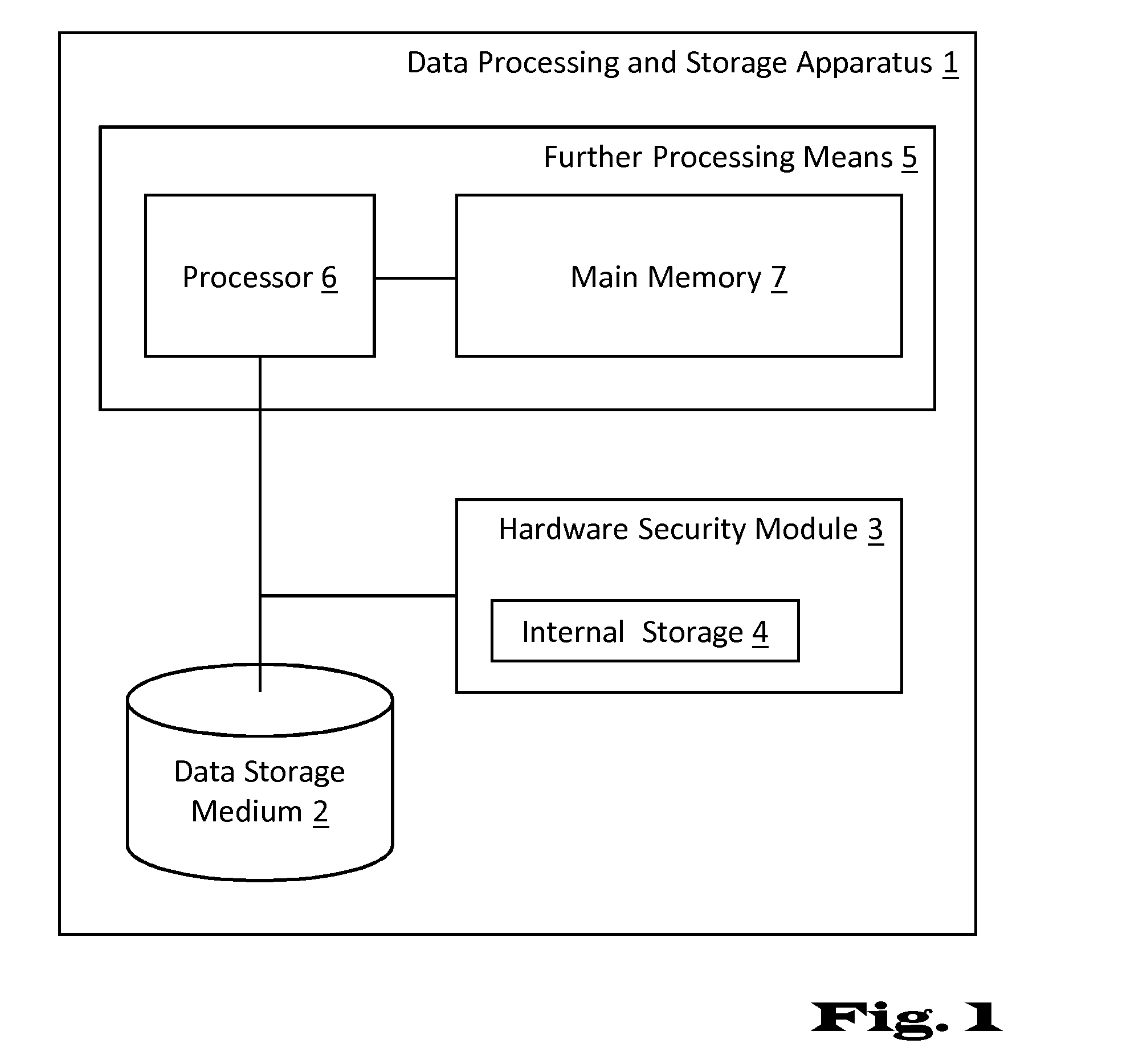
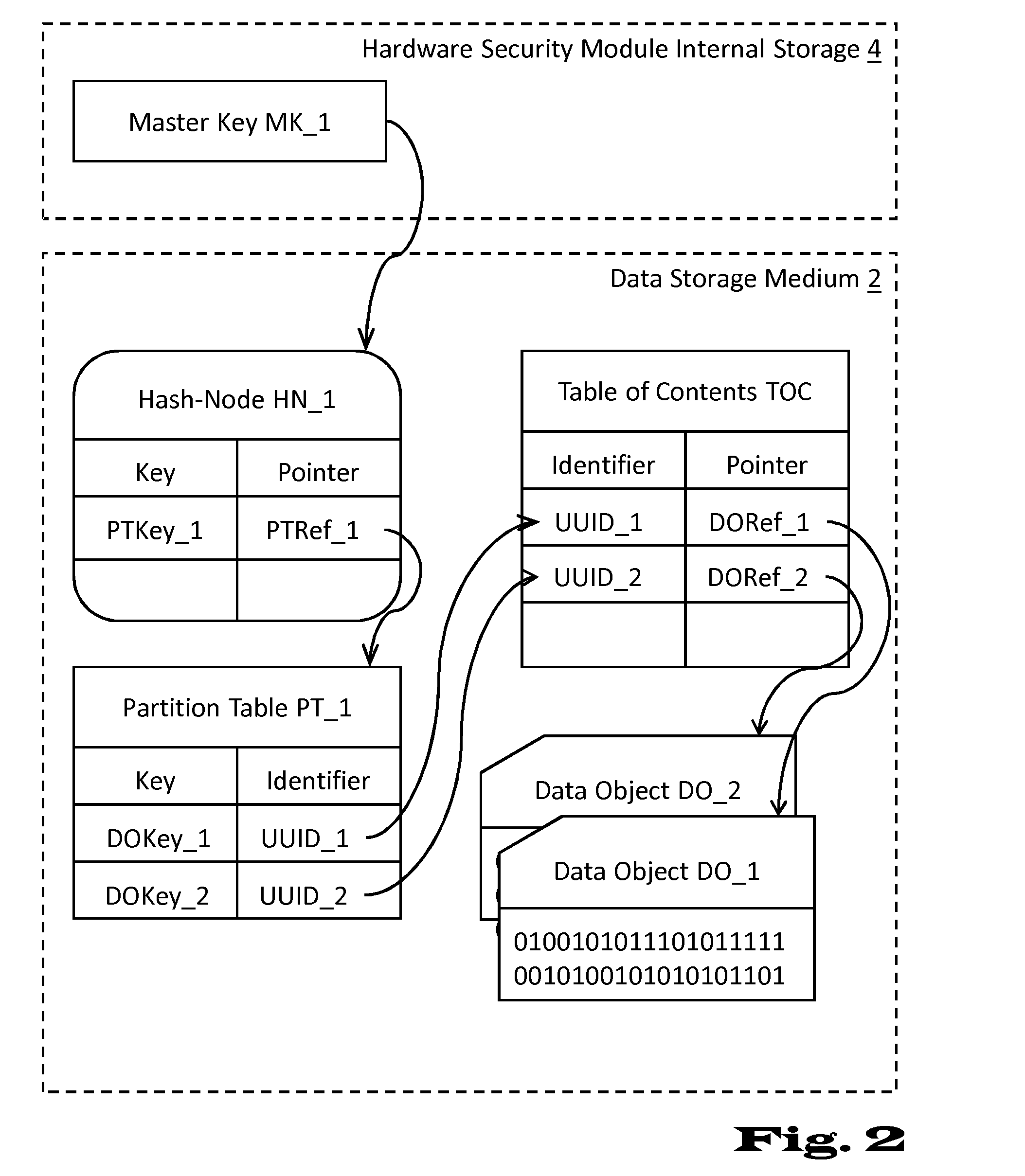
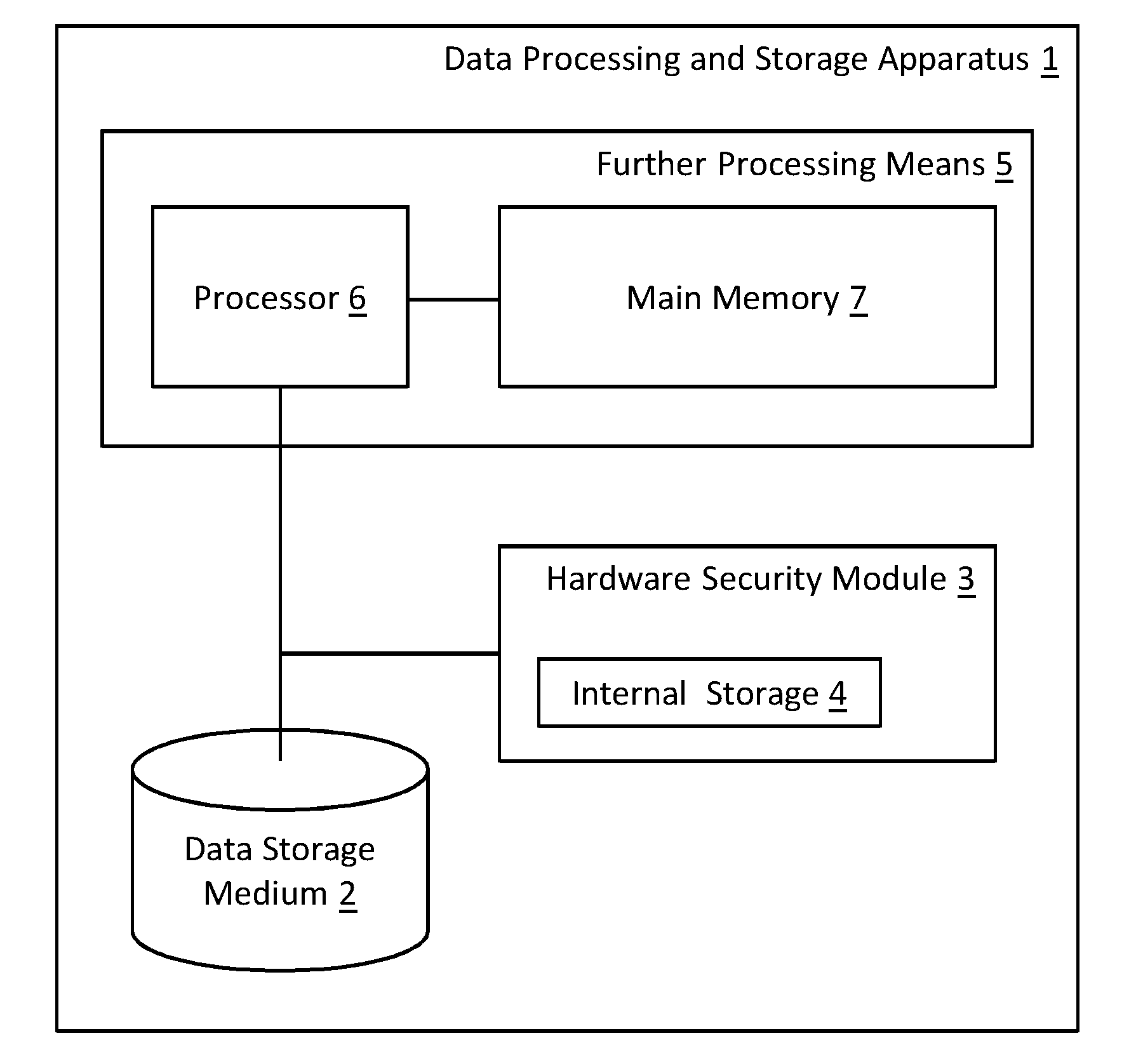
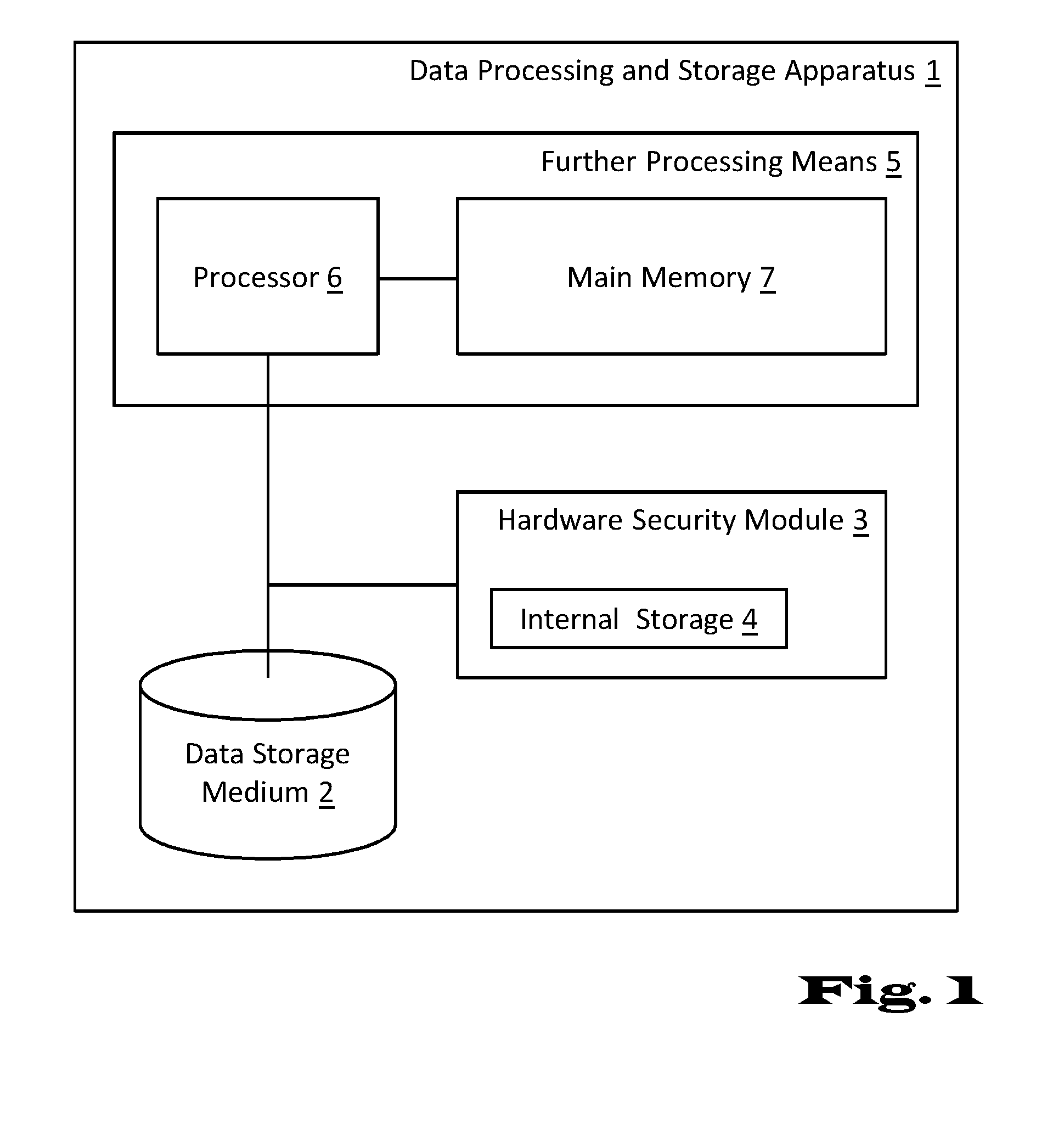
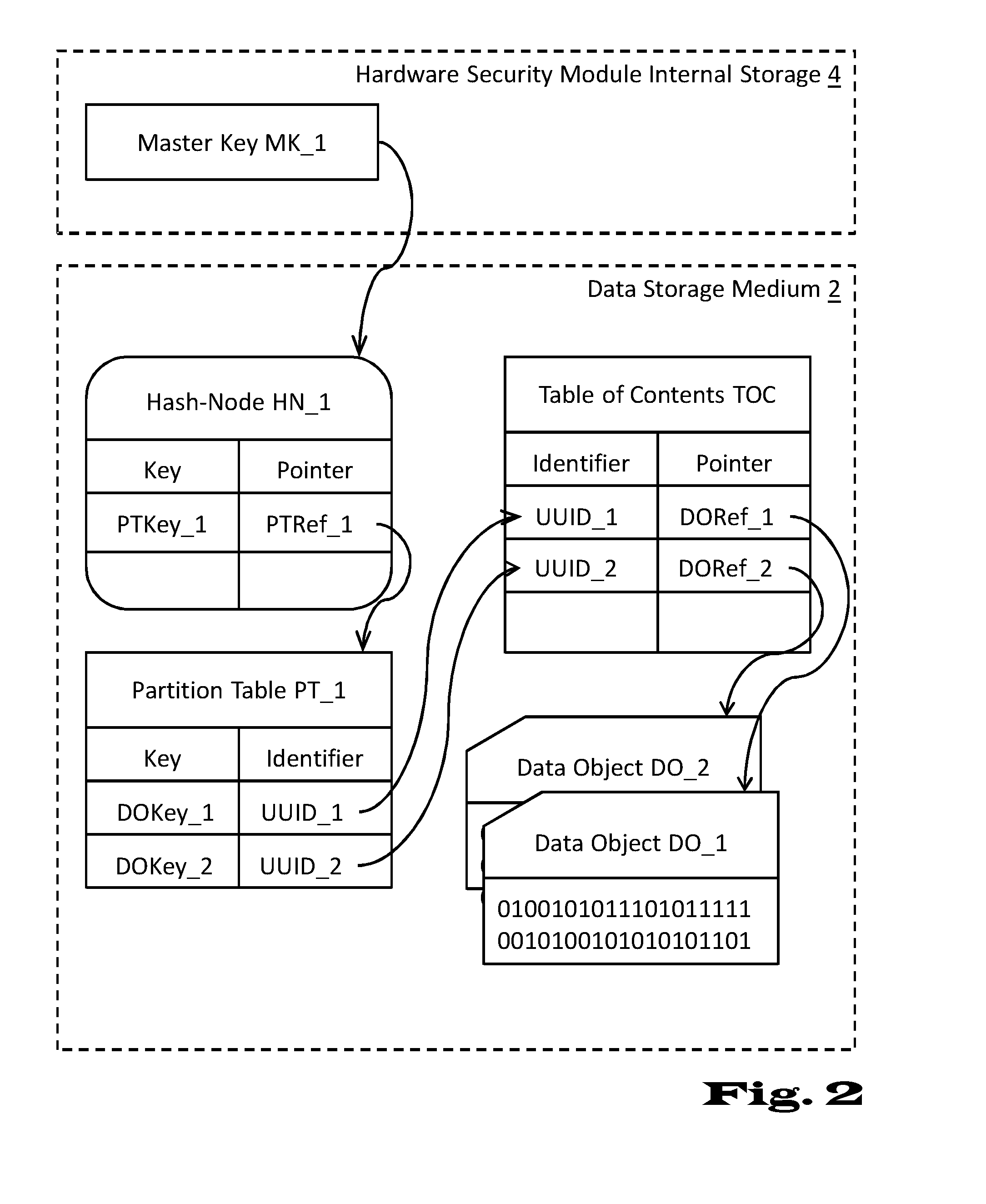
InactiveUS20150143136A1Good storage bandwidth/throughputImprove security levelMemory architecture accessing/allocationMultiple keys/algorithms usageHardware security moduleParallel computing
A data processing and storage apparatus has a hardware security module and a data storage medium storing encrypted data objects and a hierarchical data maintenance structure of encrypted partition tables and hash-nodes forming a rooted tree, where a given partition table comprises a first reference to a given encrypted data object and a first cryptographic key for decryption thereof, where a given hash-node comprises a second reference to a partition tables or hash-node and a second cryptographic key being suitable for decryption thereof, and where the root node is decipherable using a master cryptographic key stored in the hardware security module, the given data object being assigned to the root node via the first and second references of the given partition table and the given hash-nodes forming a set of successive nodes in the rooted tree.
Owner:IBM CORP
Foldable tactile display
ActiveUS20120032906A1Versatile in useFunction increaseTactile signalling systemsInput/output processes for data processingTouch PerceptionDisplay device
The present invention relates to a foldable tactile display (1) and a method of operating it. The foldable tactile display comprises a plurality of actuators (2), one or more sensors (3-6), and a computing unit (7). The computing unit is able to control the plurality of actuators in response to the received command signals and sensor signals. In an embodiment, the tactile foldable display is used in connection with multimedia content. The foldable tactile display may be in the form of a tactile blanket.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
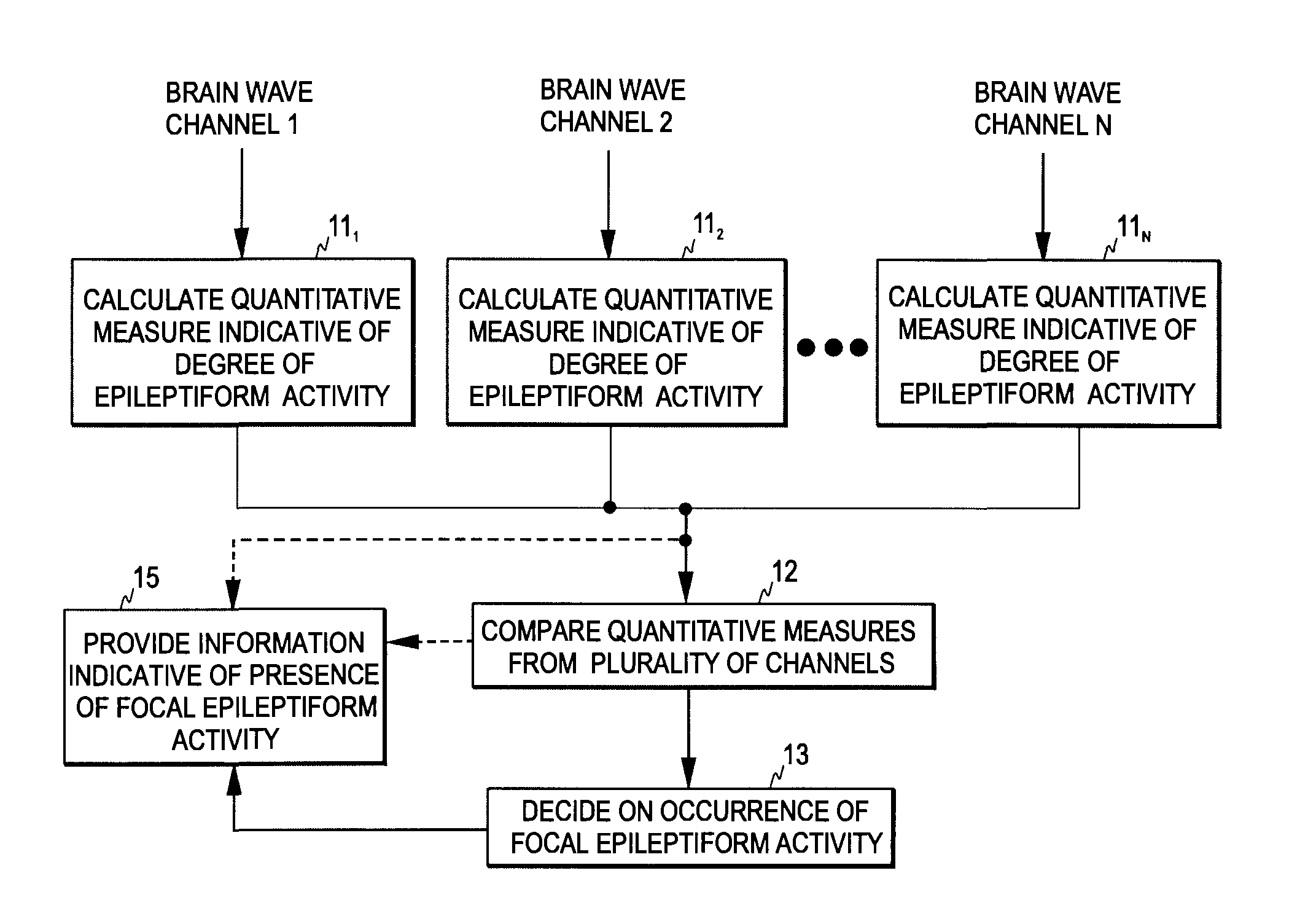
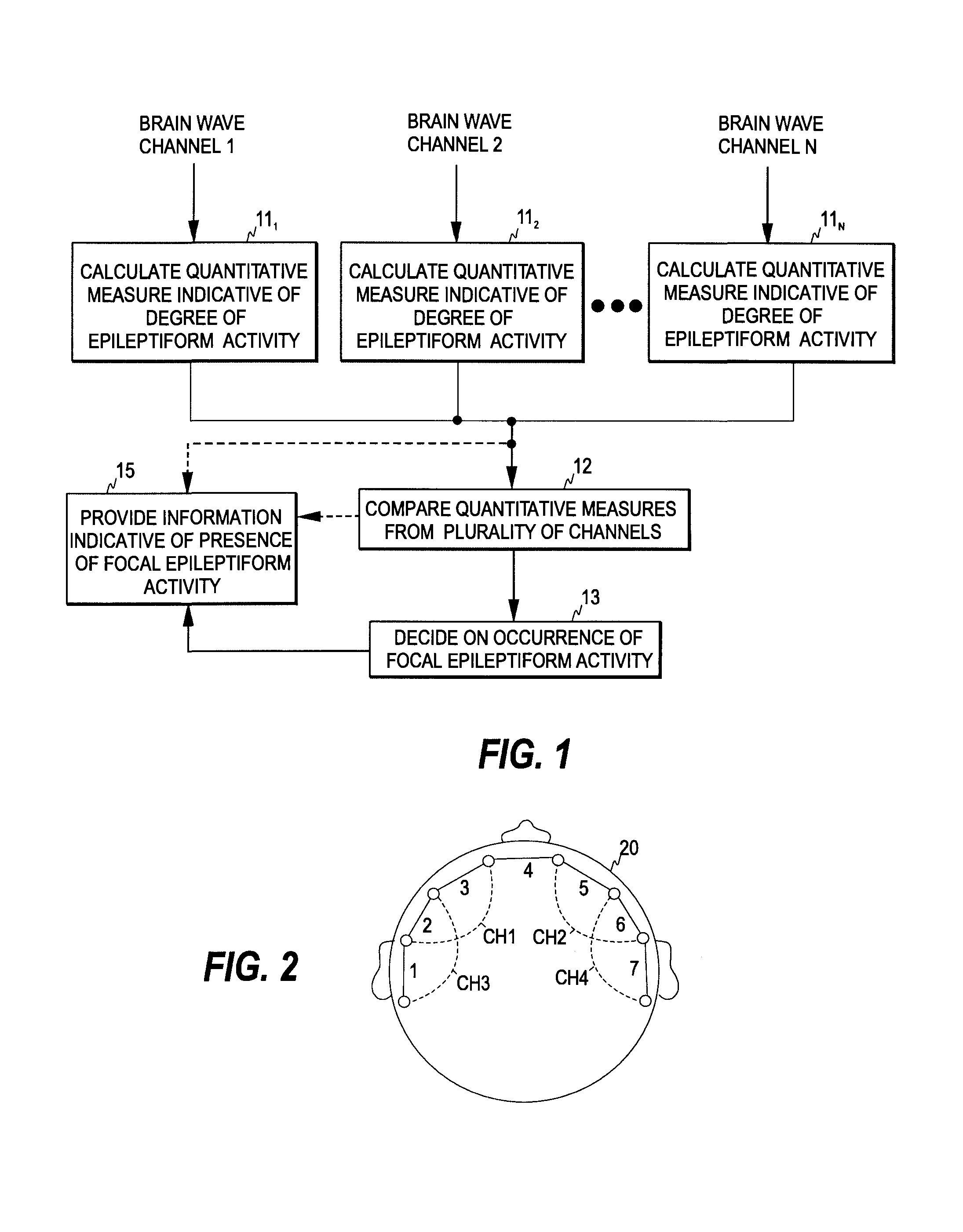
Detection of focal epileptiform activity
The invention relates to detection of focal epileptiform activity. In order to accomplish an EEG-based mechanism that enables the detection and localization of focal epileptiform activity, a first plurality of brain wave signals is obtained from a subject and a signal-specific measure indicative of the degree of epileptiform activity is determined for at least some of the first plurality of brain wave signals, thereby to obtain a second plurality of signal-specific measures. An indication of the presence of focal epileptiform activity is provided based on the second plurality of signal-specific measures. This may involve, for example, a comparison of the signal-specific measures. If significant mutual differences are detected in the measures, focal epileptiform activity is detected.
Owner:GENERAL ELECTRIC CO
Multiple module encryption method
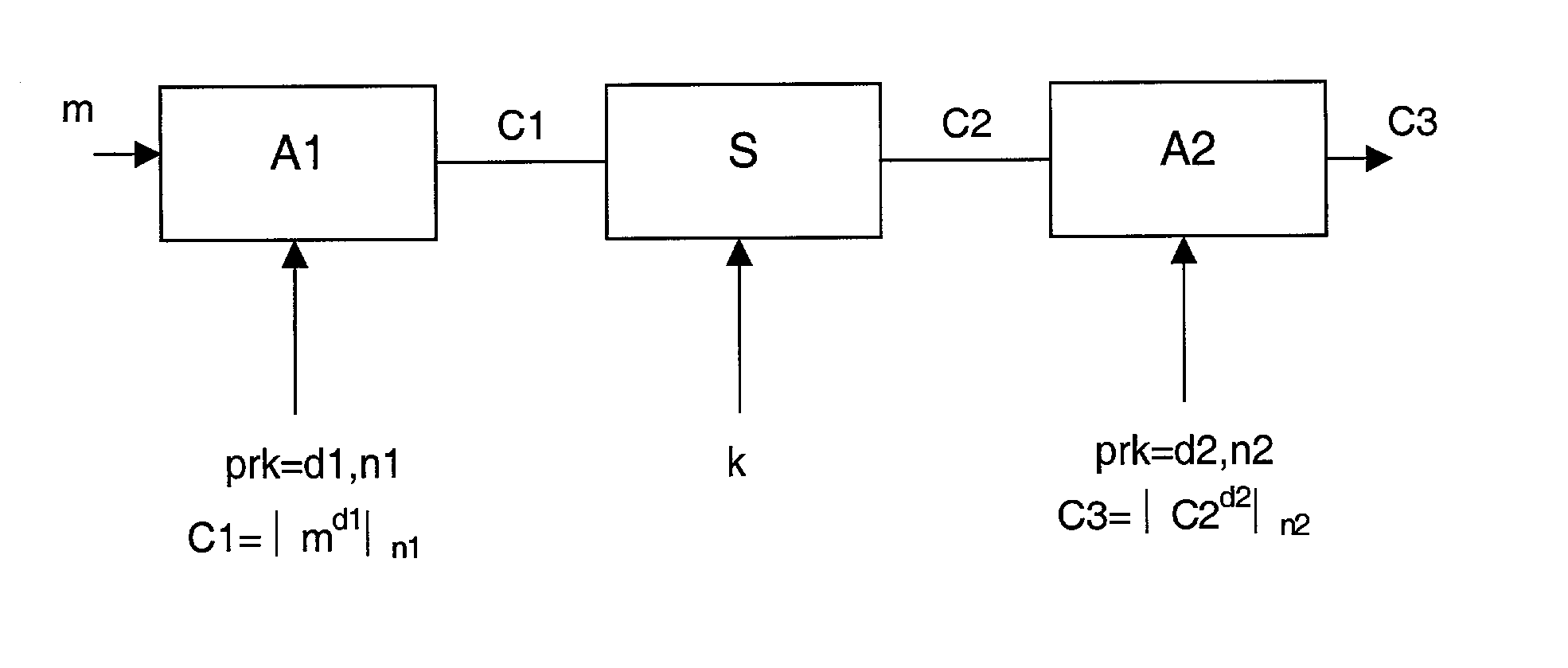
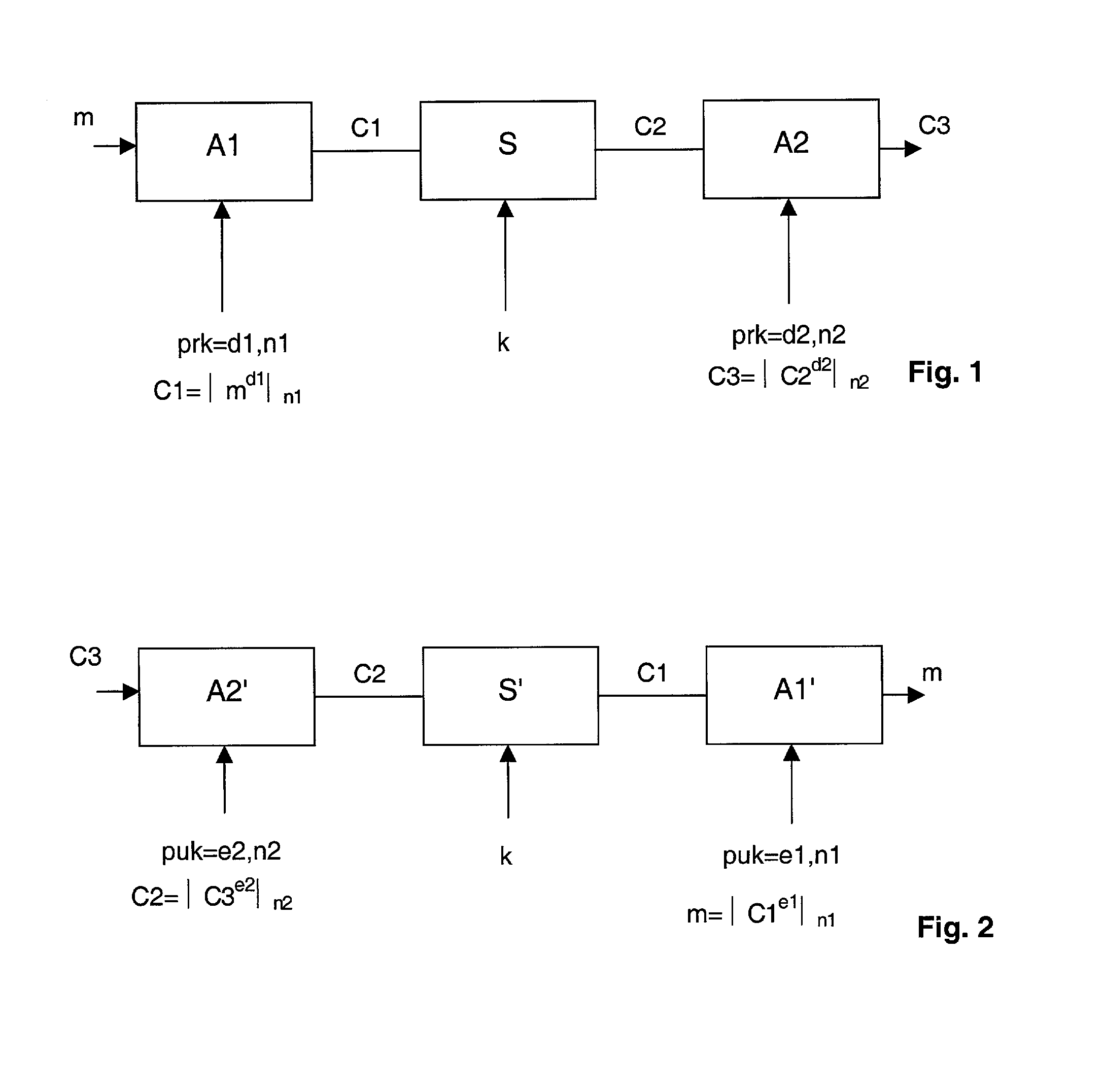
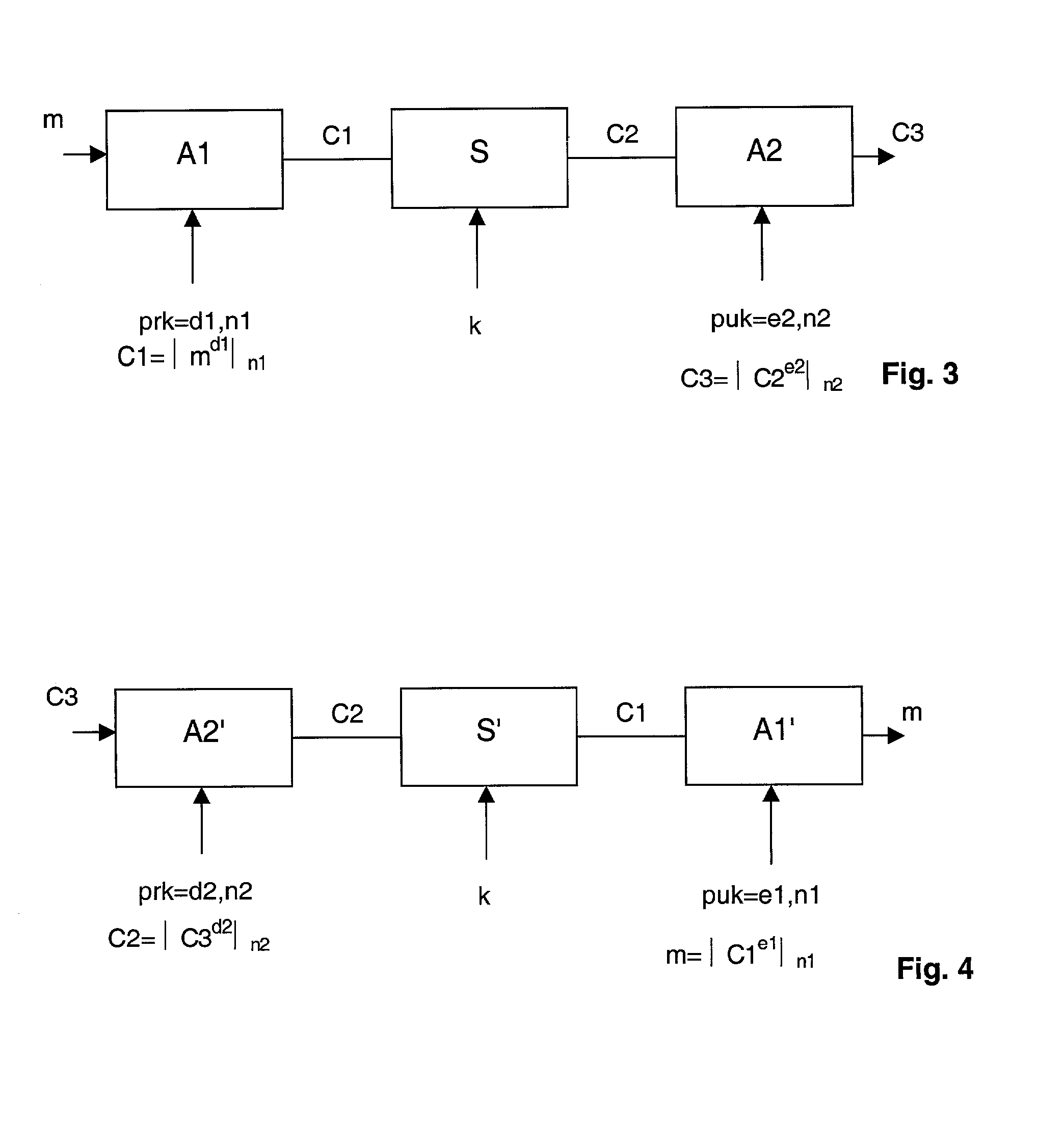
InactiveUS7190790B1Preserve invulnerability characteristicLimited computing powerEncryption apparatus with shift registers/memoriesPublic key for secure communicationPower analysisAttack strategy
The present invention proposes an encryption / decryption method able to resist against various attack strategies such as Simple Power Analysis, Timing Analysis or Differential Power Analysis. The method is carried out by a plurality of encryption / decryption modules arranged in series, wherein an encryption / decryption module, different from the first module, starts encryption / decryption operations as soon as said module receives a part of the results of encryption / decryption operations from the immediately preceding encryption / decryption module.
Owner:NAGRAVISION SA
Device and method for coding a data signal and device and method for decoding a data signal
InactiveUS20100231426A1Quality improvementLimited amountSpeech analysisCode conversionData informationData signal
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Method and system for classifying a terrain type in an area
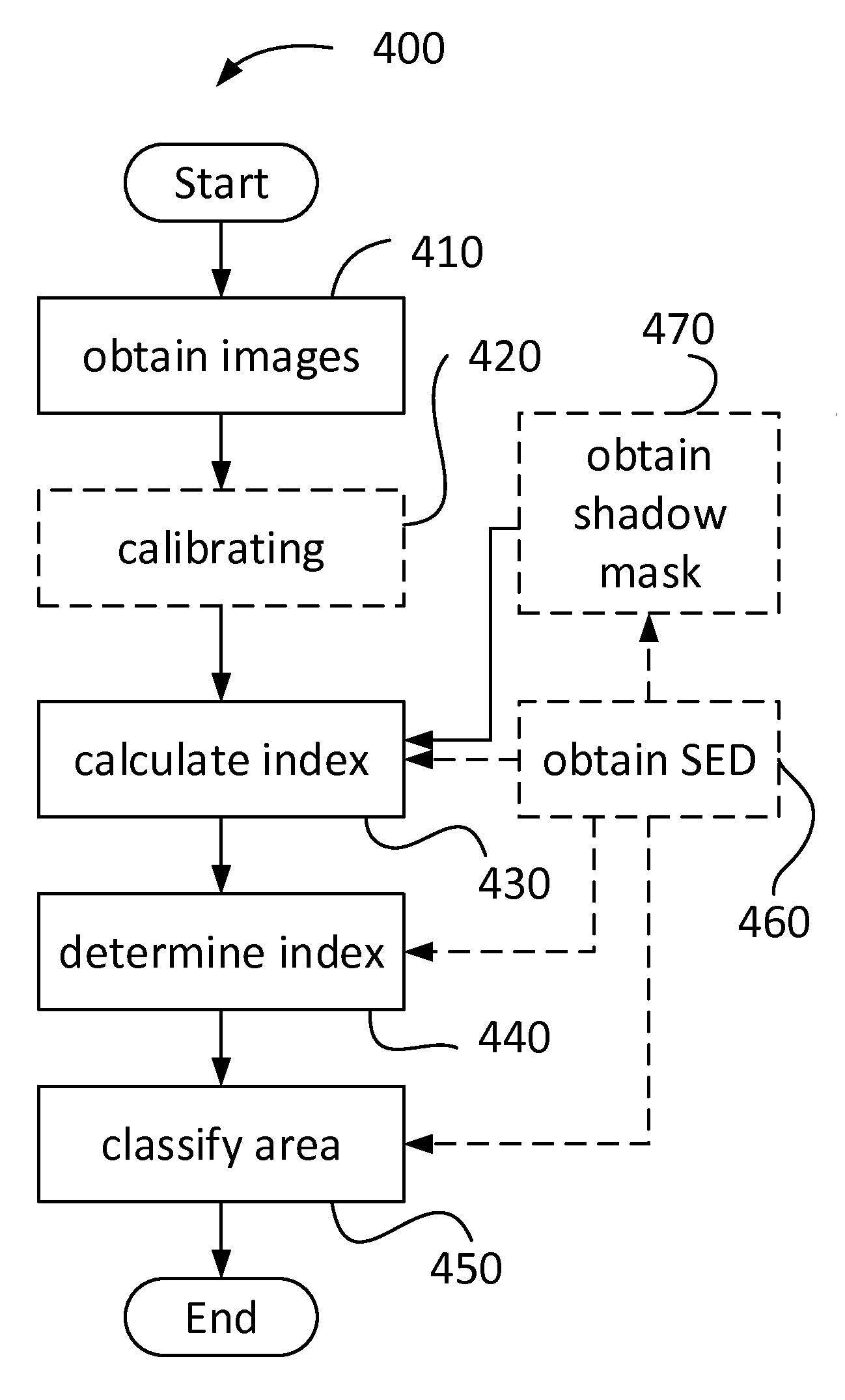
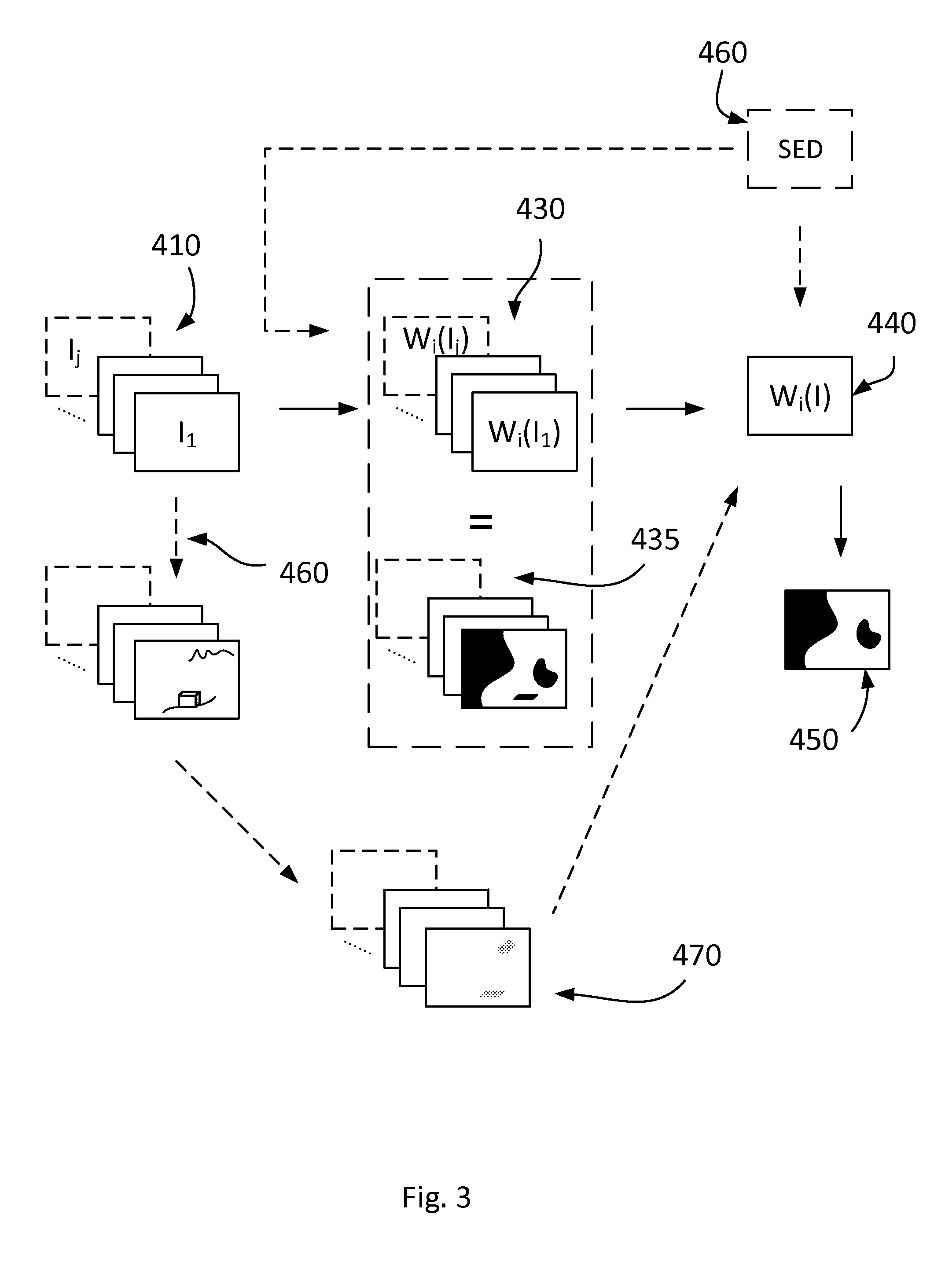
A method for classifying a terrain type in an area is provided, which method comprises the steps of: obtaining a plurality of overlapping aerial images of the area; calculating at least one terrain type index for each part of each of the aerial images which lies in the area, where the at least one terrain type index represents the terrain type; determining at least one terrain type index for each part of the area based on the calculated at least one terrain type index for each part of each of the aerial images; and classifying the parts of the area for which at least one pre-determined conditions is met as containing the terrain type, wherein at least one of the at least one predetermined condition relates to a value of the determined at least one terrain type index. An associated system and computer program product are also provided.
Owner:MAXAR INT SWEDEN AB
Method and device for locating a magnetic object
ActiveUS20150057969A1Reduce electricity consumptionReduce in quantityDigital computer detailsSpeed measurement using gyroscopic effectsMagnetic tension forceClassical mechanics
A method for locating a moving magnetic object, comprising: determining the position or the orientation of the magnetic object from measurements of an array of N (an integer greater than 5) tri-axial magnetometers mechanically linked to one another with no degree, the method also comprises the reiteration of the following steps. Estimating the position of the magnetic object relative to the array of magnetometers from measurements of the magnetometers made in a preceding iteration or from a measurement of a sensor distinct from the magnetometers of the array of magnetometers so that this estimation is obtained before making a new measurement using the magnetometers of the array; computing the distance between each magnetometer and the estimated position of the magnetic object; eliminating the Ni magnetometers closest to this estimated position, where Ni is a positive integer number strictly less than N; making a new measurement, by each non-eliminated magnetometer, of the magnetic field generated or modified by the magnetic object; and determining a new position or a new orientation of the magnetic object from the new measurements of the magnetometers which have not been eliminated and without taking into account new measurements made by the eliminated magnetometers, so as to obtain a new location of the magnetic object.
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES
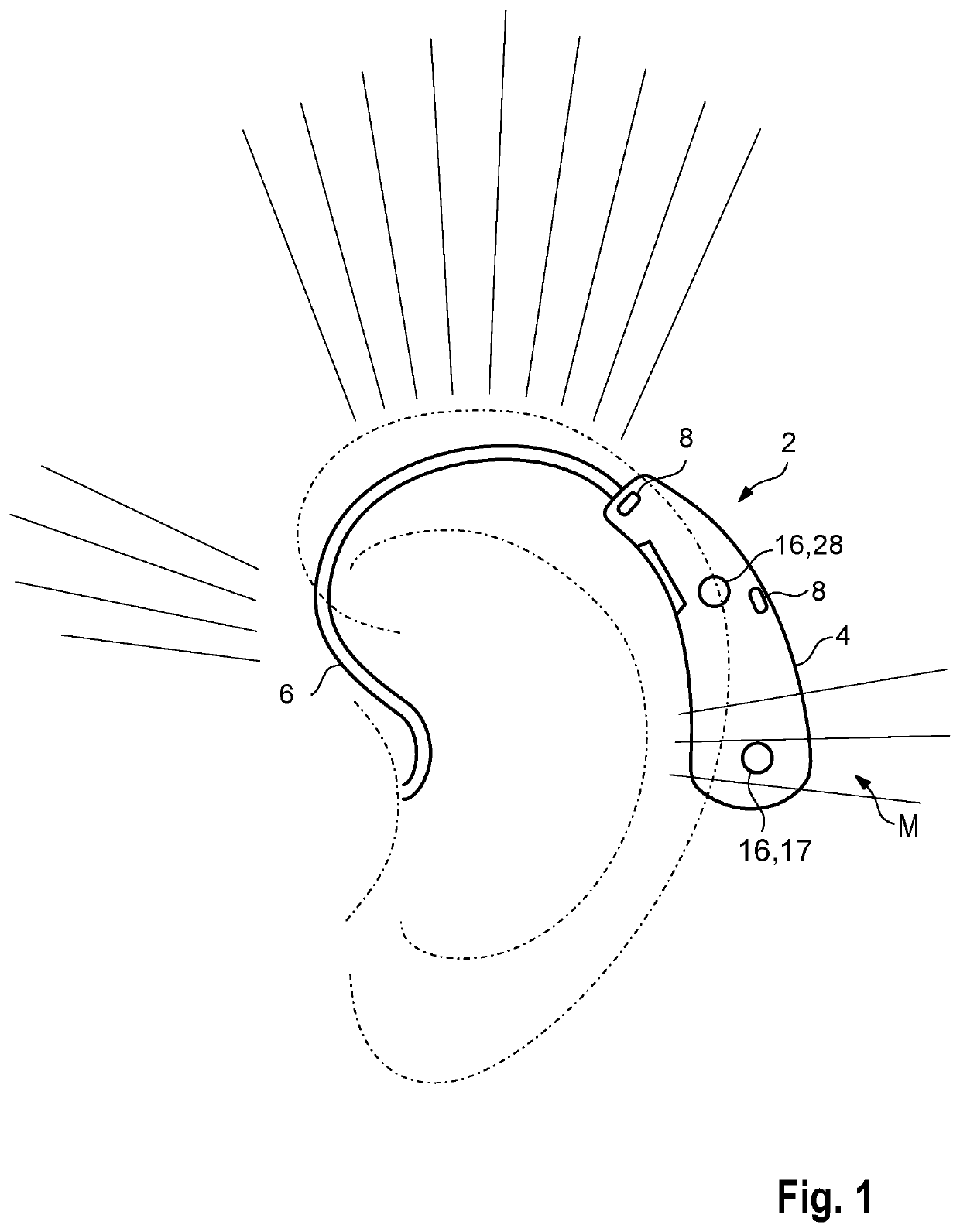
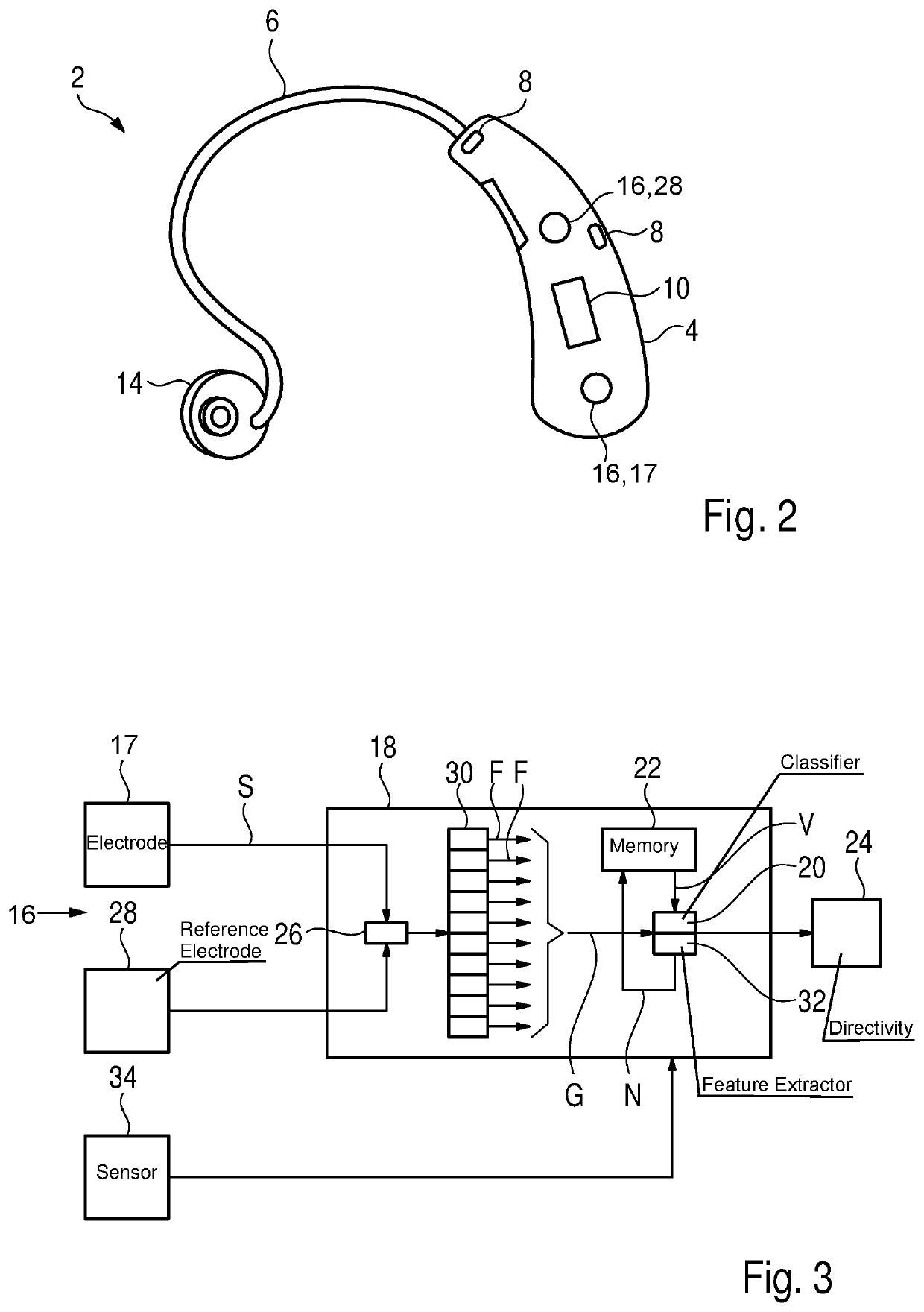
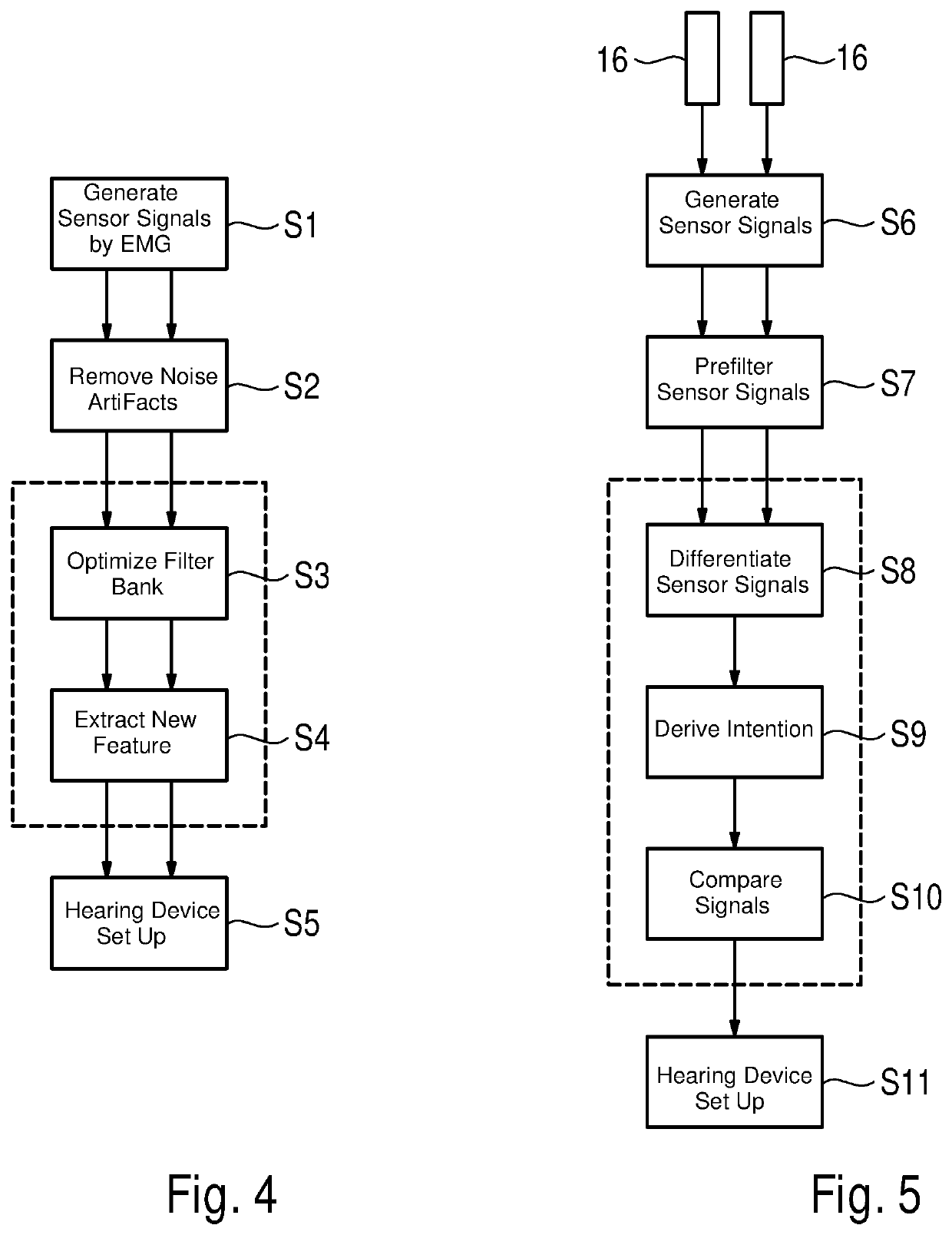
Method for operating a hearing device and hearing device
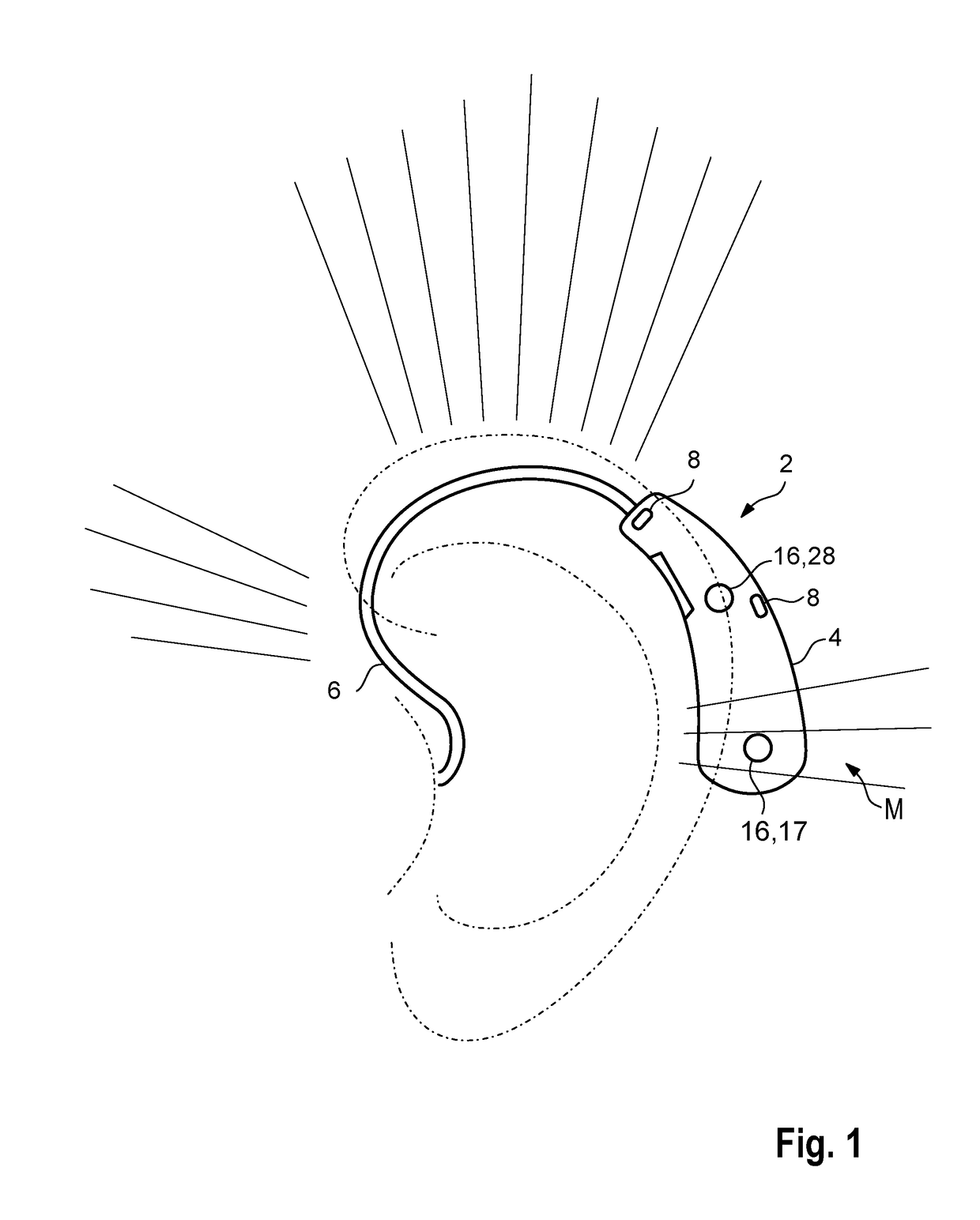
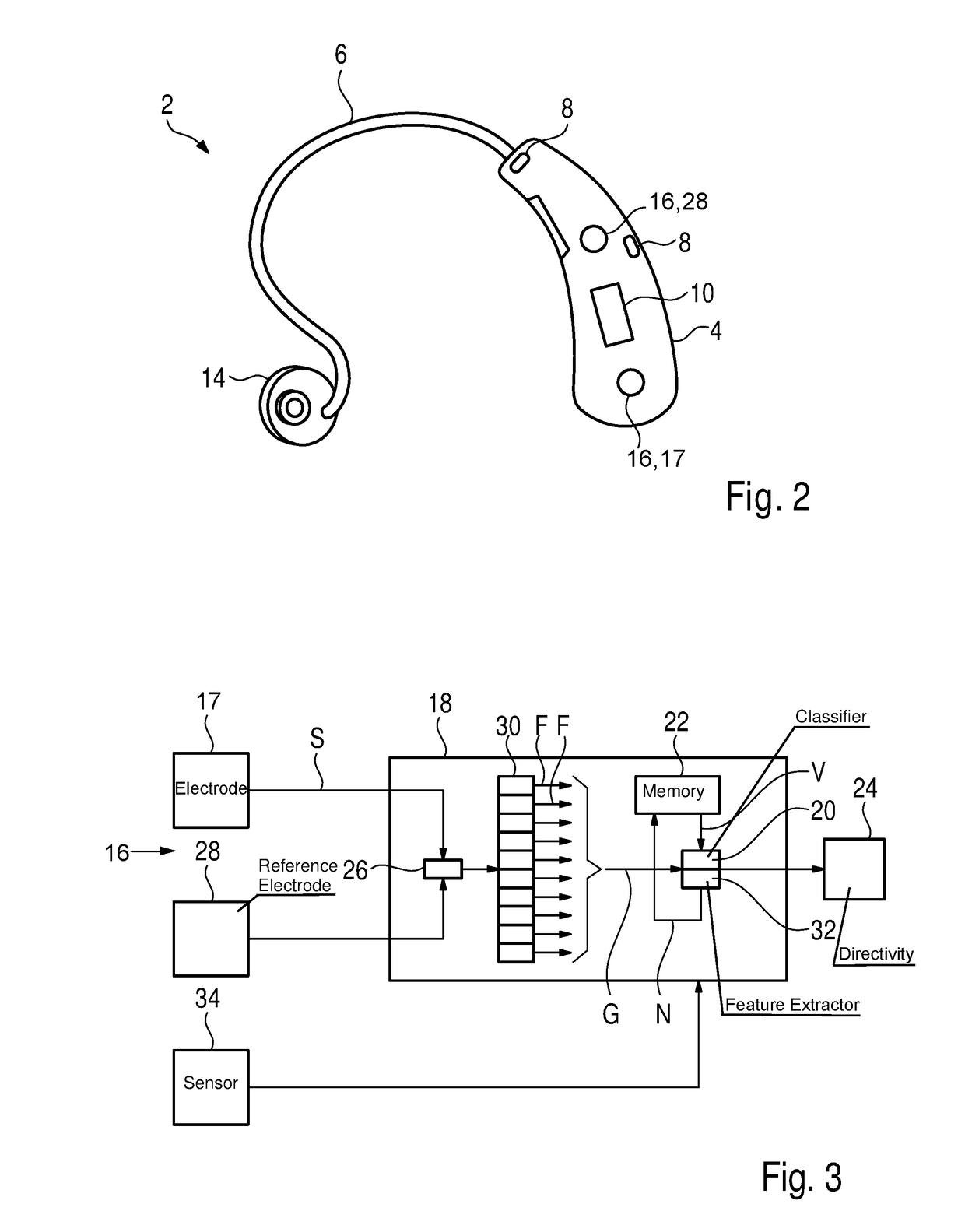
ActiveUS20190052978A1Suitable for useCompact formHearing device active noise cancellationElectromyographyFeature vectorHearing apparatus
A method operates a hearing device for a user. In the method, electromyography is performed, in which a muscle activity of an auricular muscle of the user is measured by an electrode array. The muscle activity is continuously measured to detect a complex activity profile of the auricular muscle, in which the user's intention is coded. The electrode array generates a sensor signal that is classified by means of a classifier, and in this classification process, the muscle activity is decoded and the underlying intention is determined by examining whether the sensor signal has a previously known feature vector. The previously known feature vector is assigned to an operating mode of the hearing device, which is set when the sensor signal has the previously known feature vector.
Owner:SIVANTOS PTE LTD
Deletion of content in digital storage systems
ActiveUS20160164683A1Improve security levelLimited computing powerMemory architecture accessing/allocationMultiple keys/algorithms usageHardware security moduleParallel computing
A data processing and storage apparatus has a hardware security module and a data storage medium storing encrypted data objects and a hierarchical data maintenance structure of encrypted partition tables and hash-nodes forming a rooted tree, where a given partition table comprises a first reference to a given encrypted data object and a first cryptographic key for decryption thereof, where a given hash-node comprises a second reference to a partition tables or hash-node and a second cryptographic key being suitable for decryption thereof, and where the root node is decipherable using a master cryptographic key stored in the hardware security module, the given data object being assigned to the root node via the first and second references of the given partition table and the given hash-nodes forming a set of successive nodes in the rooted tree.
Owner:INT BUSINESS MASCH CORP
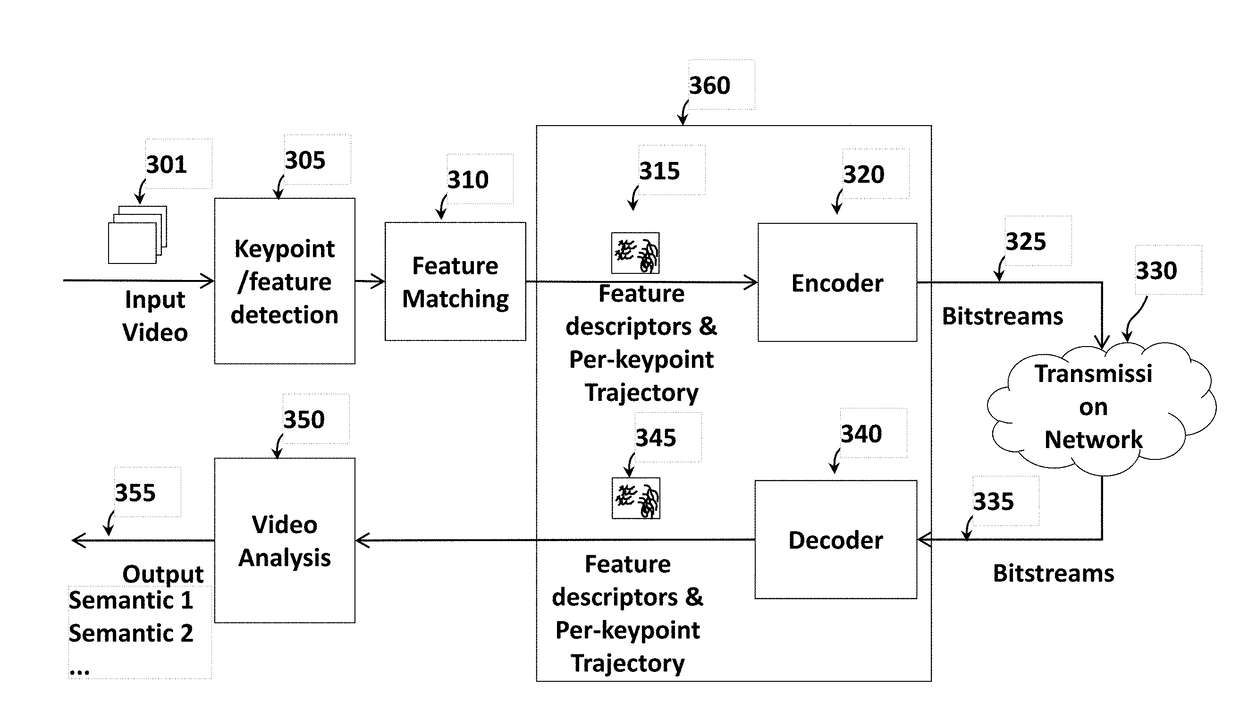
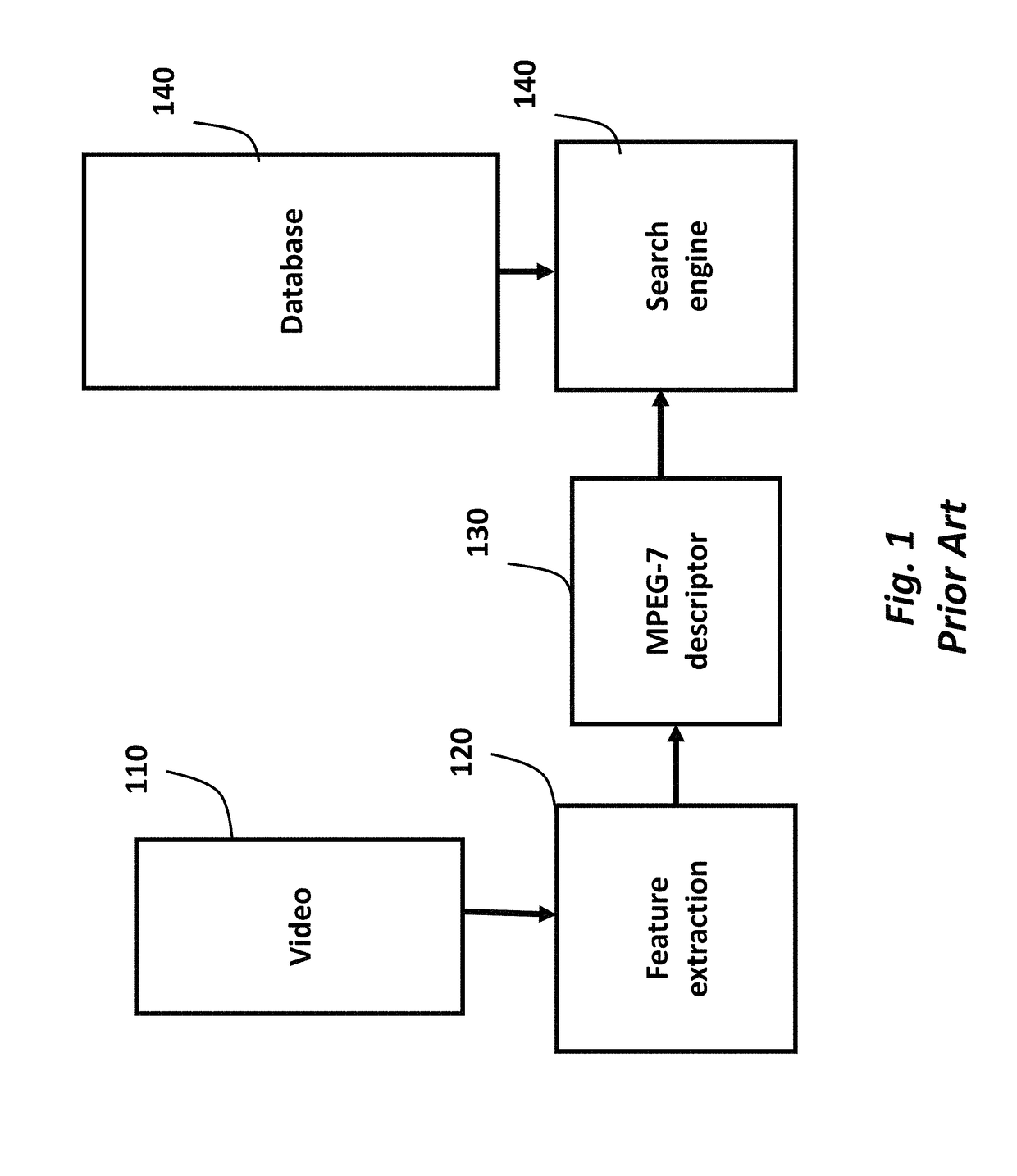
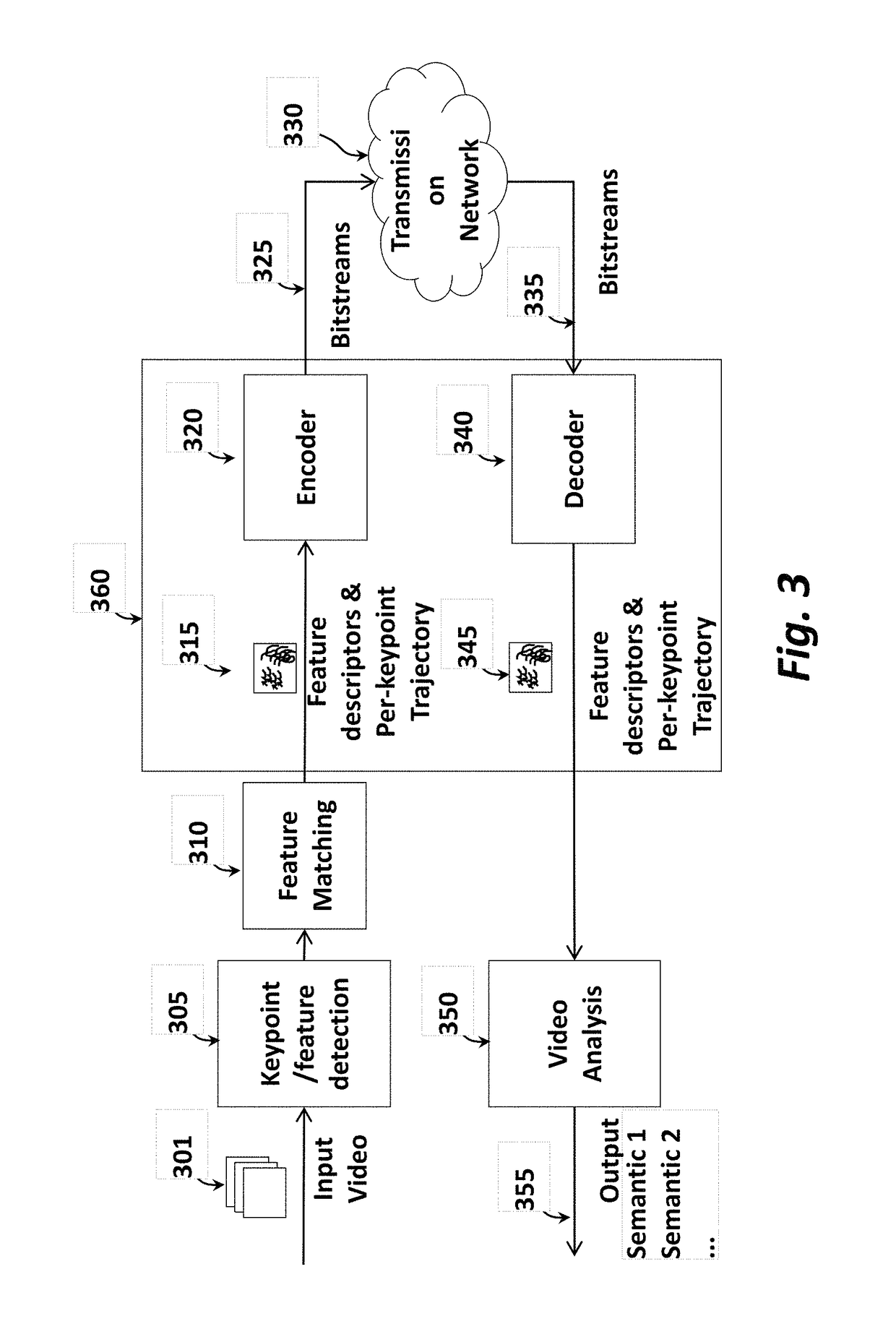
Method and Apparatus for Keypoint Trajectory Coding on Compact Descriptor for Video Analysis
ActiveUS20170214936A1Limited costLow costCharacter and pattern recognitionDigital video signal modificationComputer visionFeature descriptor
A method processes keypoint trajectories in a video, wherein the keypoint trajectories describe motion of a plurality of keypoints across pictures of the video over time, by first acquiring the video of a scene using a camera. Kkeypoints and associated feature descriptors are detected in each picture. The keypoints and associated features descriptors are matched between neighboring pictures to generate keypoint trajectories. Then, the keypoint trajectories are coded predictively into a bitstream, which is outputted.
Owner:MITSUBISHI ELECTRIC RES LAB INC
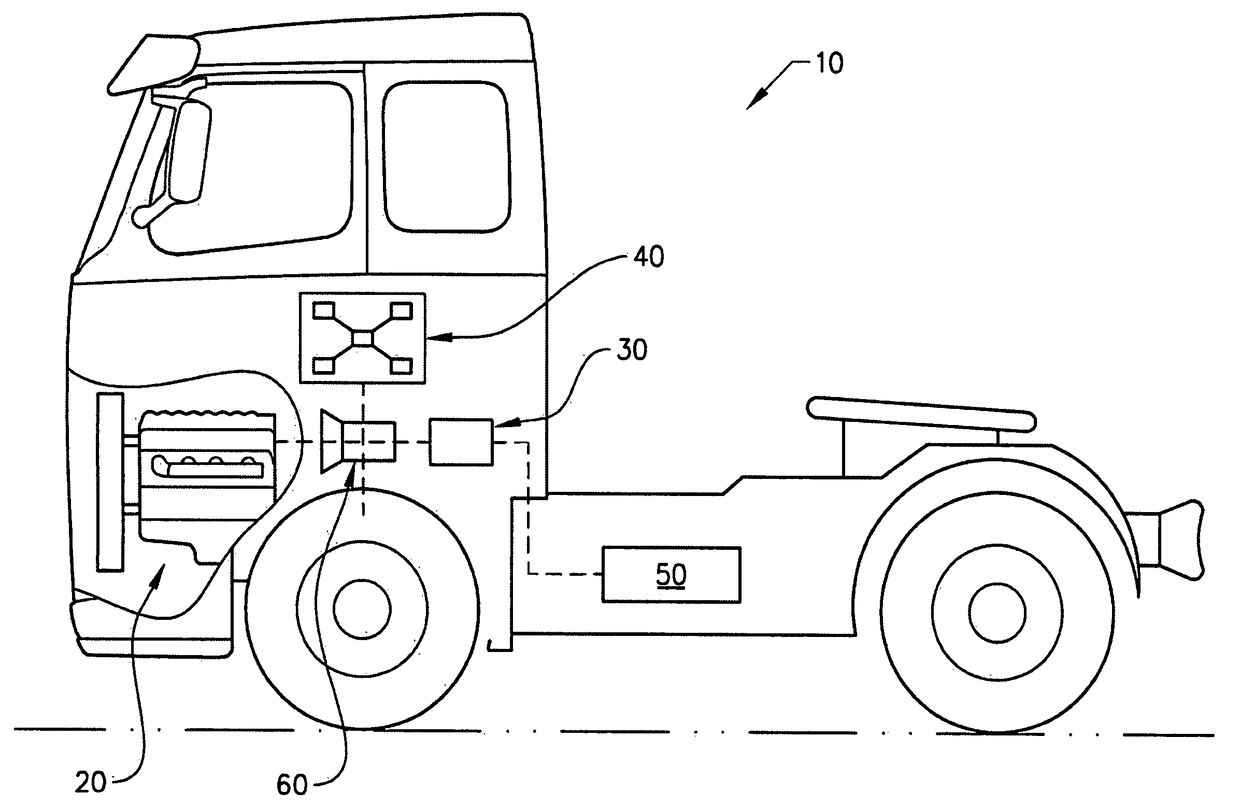
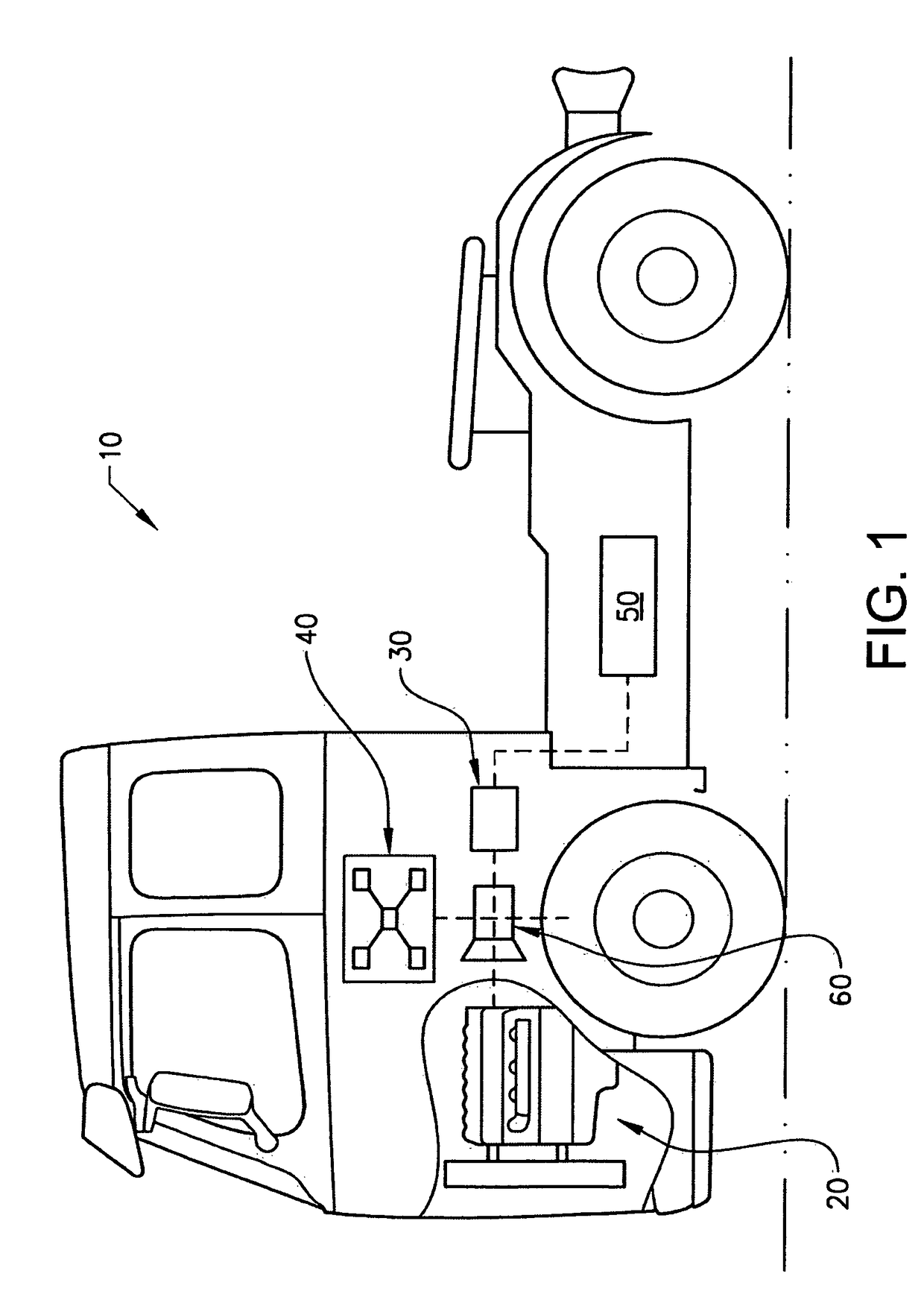
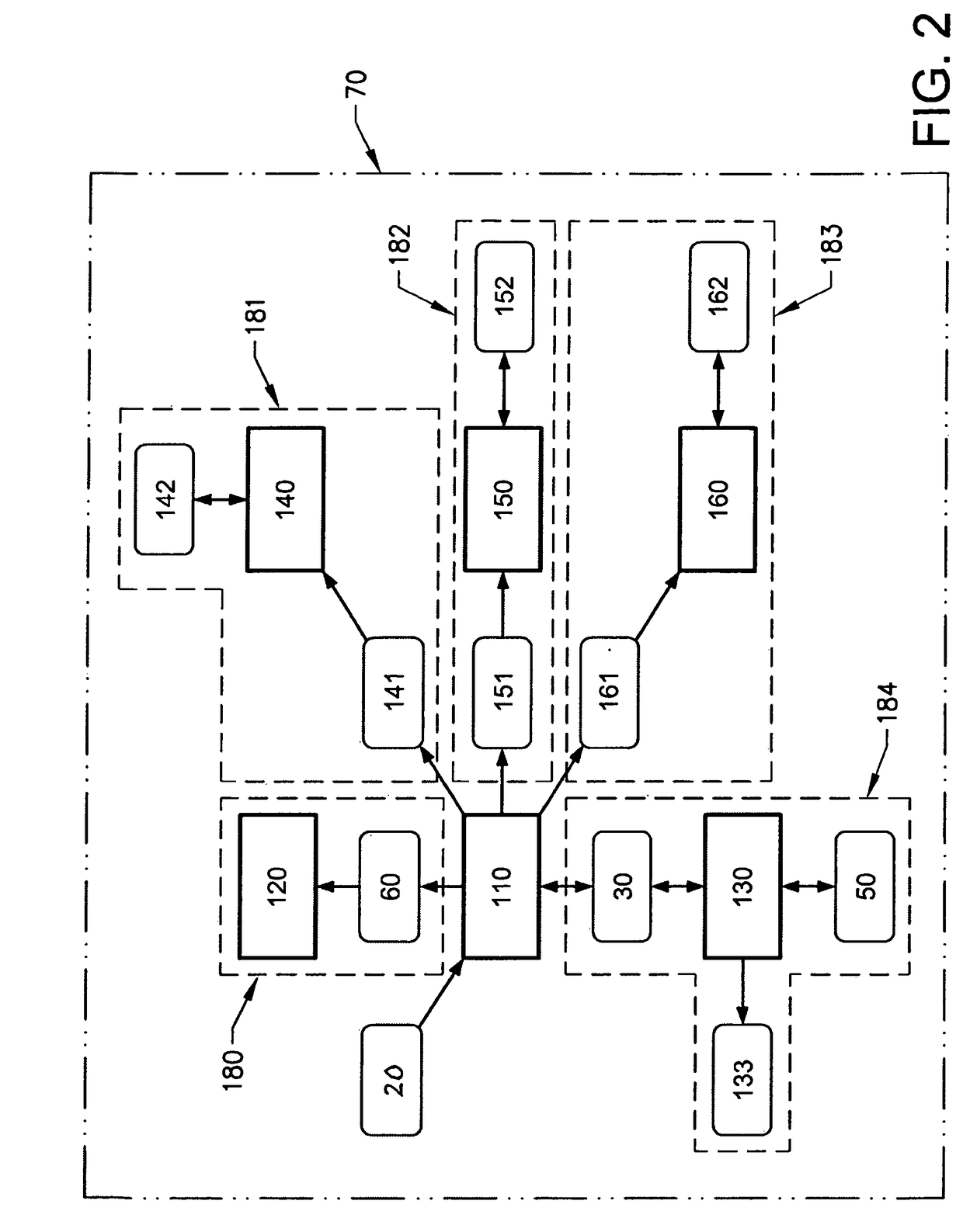
A method performed by a control unit for controlling energy flows of a vehicle
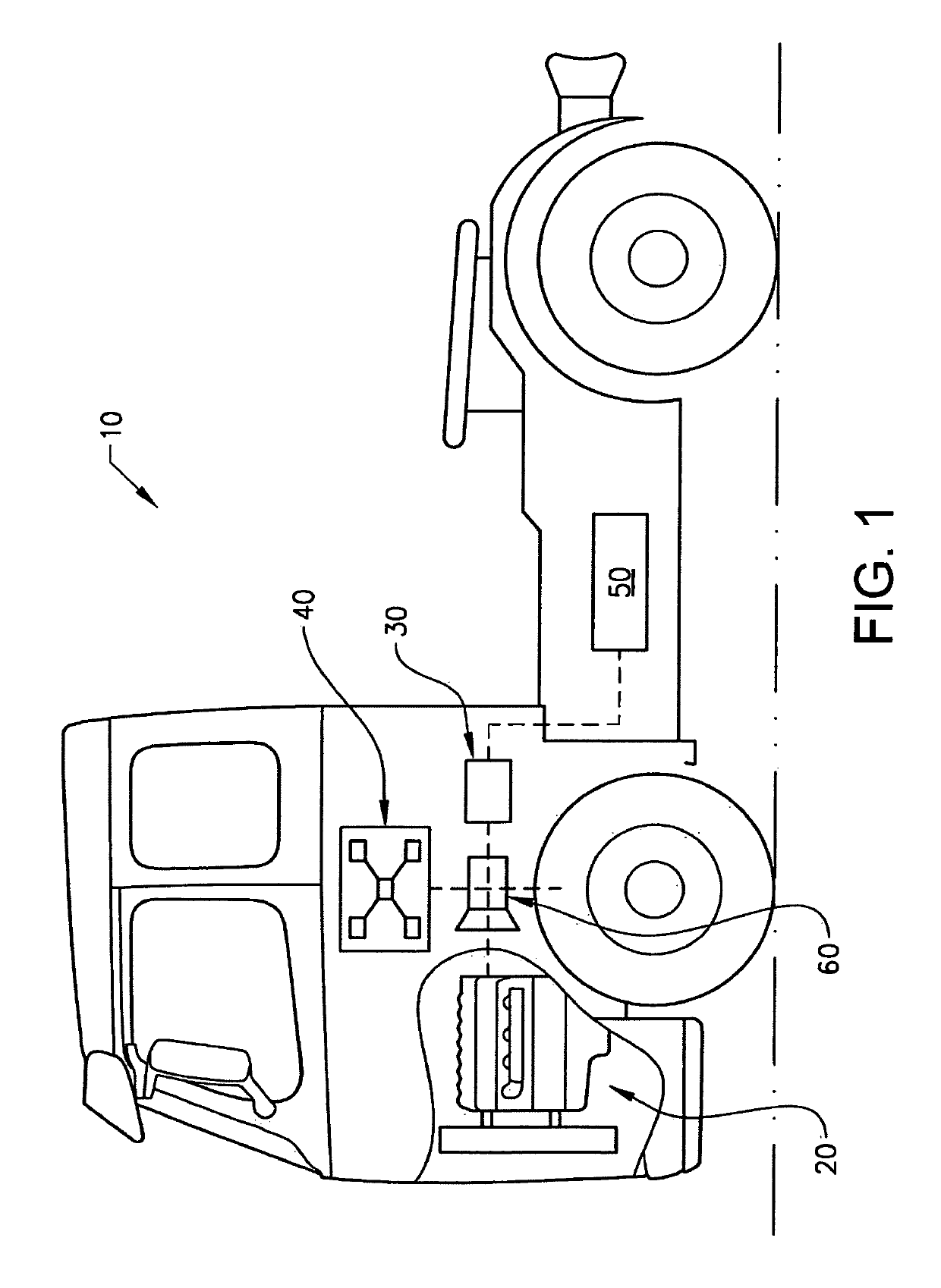
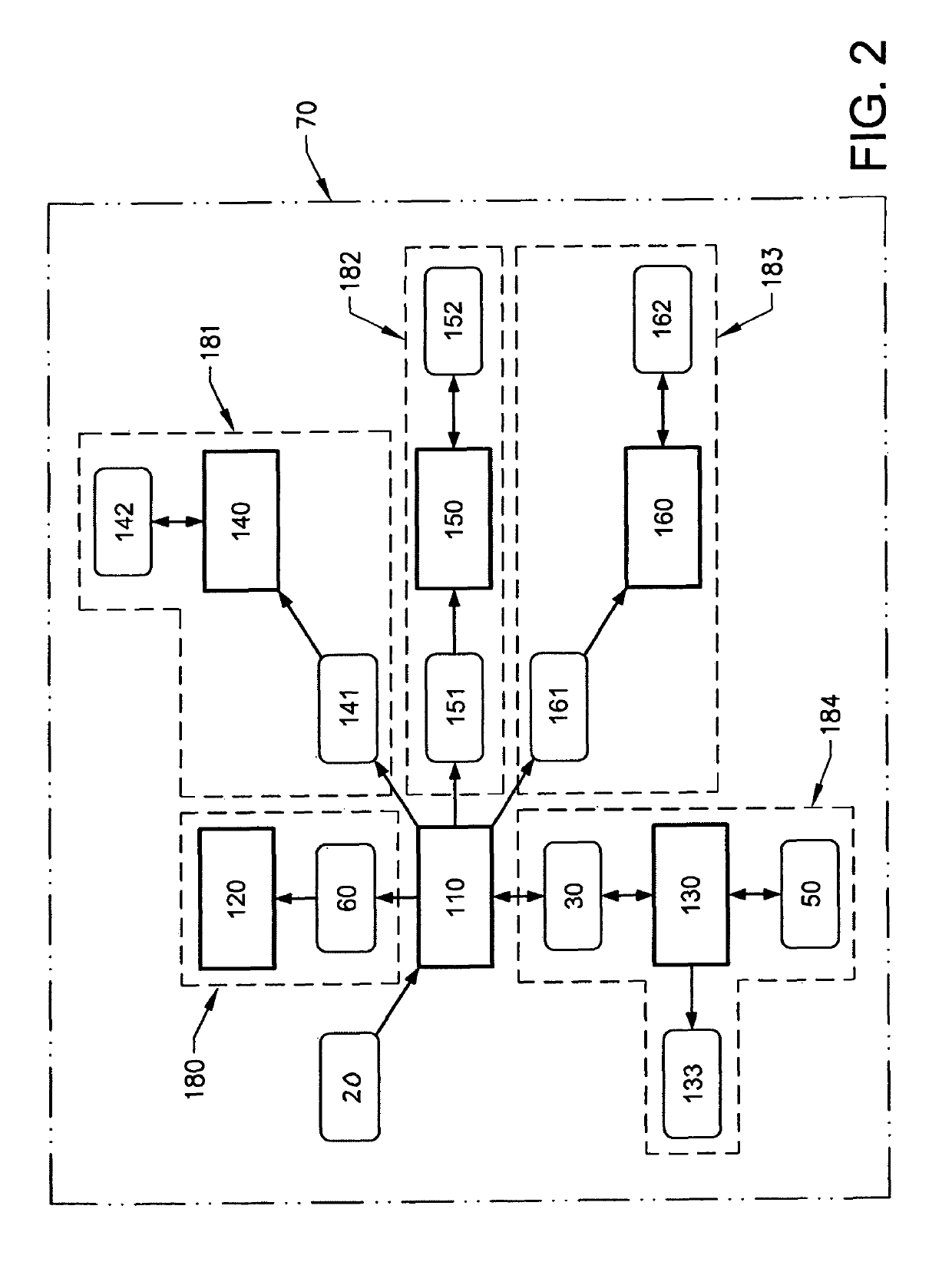
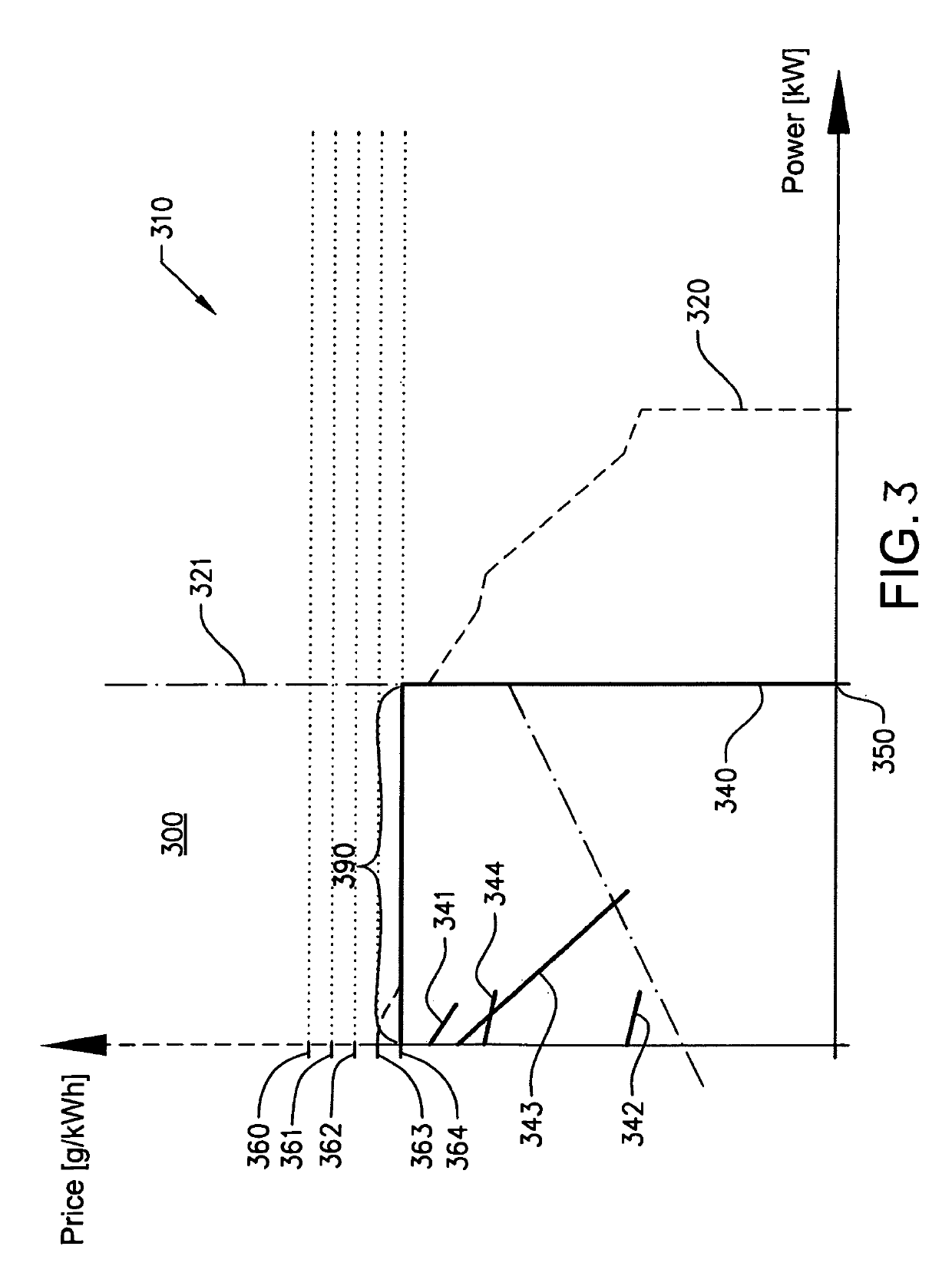
ActiveUS20170297557A1Limited computing powerHybrid vehiclesInternal combustion piston enginesForms of energyEnergy system
In a method performed by a control unit for controlling energy flows of a vehicle, where the vehicle includes a vehicle energy system which in turn includes a plurality of energy subsystems. Within each energy subsystem one form of energy is used. The energy subsystems are operationally connected by converters, wherein converters are devices converting at least one form of energy to another form of energy. By setting a price, limits for the converters converting energy between the energy subsystem the energy flows of the vehicle can be controlled by the control unit such that at least during period of times the order in which the energy subsystems of the vehicle is provided with energy can be changed.
Owner:VOLVO LASTVAGNAR AB
Method and system for classifying a terrain type in an area
ActiveUS20160171279A1Easy to classifyReliable resultsImage enhancementImage analysisTerrainAerial photography
A method for classifying a terrain type in an area is provided, which method comprises the steps of: obtaining a plurality of overlapping aerial images of the area; calculating at least one terrain type index for each part of each of the aerial images which lies in the area, where the at least one terrain type index represents the terrain type; determining at least one terrain type index for each part of the area based on the calculated at least one terrain type index for each part of each of the aerial images; and classifying the parts of the area for which at least one pre-determined conditions is met as containing the terrain type, wherein at least one of the at least one predetermined condition relates to a value of the determined at least one terrain type index. An associated system and computer program product are also provided.
Owner:MAXAR INT SWEDEN AB
Method and apparatus for keypoint trajectory coding on compact descriptor for video analysis
ActiveUS10154281B2Low costLimited computing powerCharacter and pattern recognitionDigital video signal modificationPattern recognitionBitstream
A method processes keypoint trajectories in a video, wherein the keypoint trajectories describe motion of a plurality of keypoints across pictures of the video over time, by first acquiring the video of a scene using a camera. Keypoints and associated feature descriptors are detected in each picture. The keypoints and associated features descriptors are matched between neighboring pictures to generate keypoint trajectories. Then, the keypoint trajectories are coded predictively into a bitstream, which is outputted.
Owner:MITSUBISHI ELECTRIC RES LAB INC
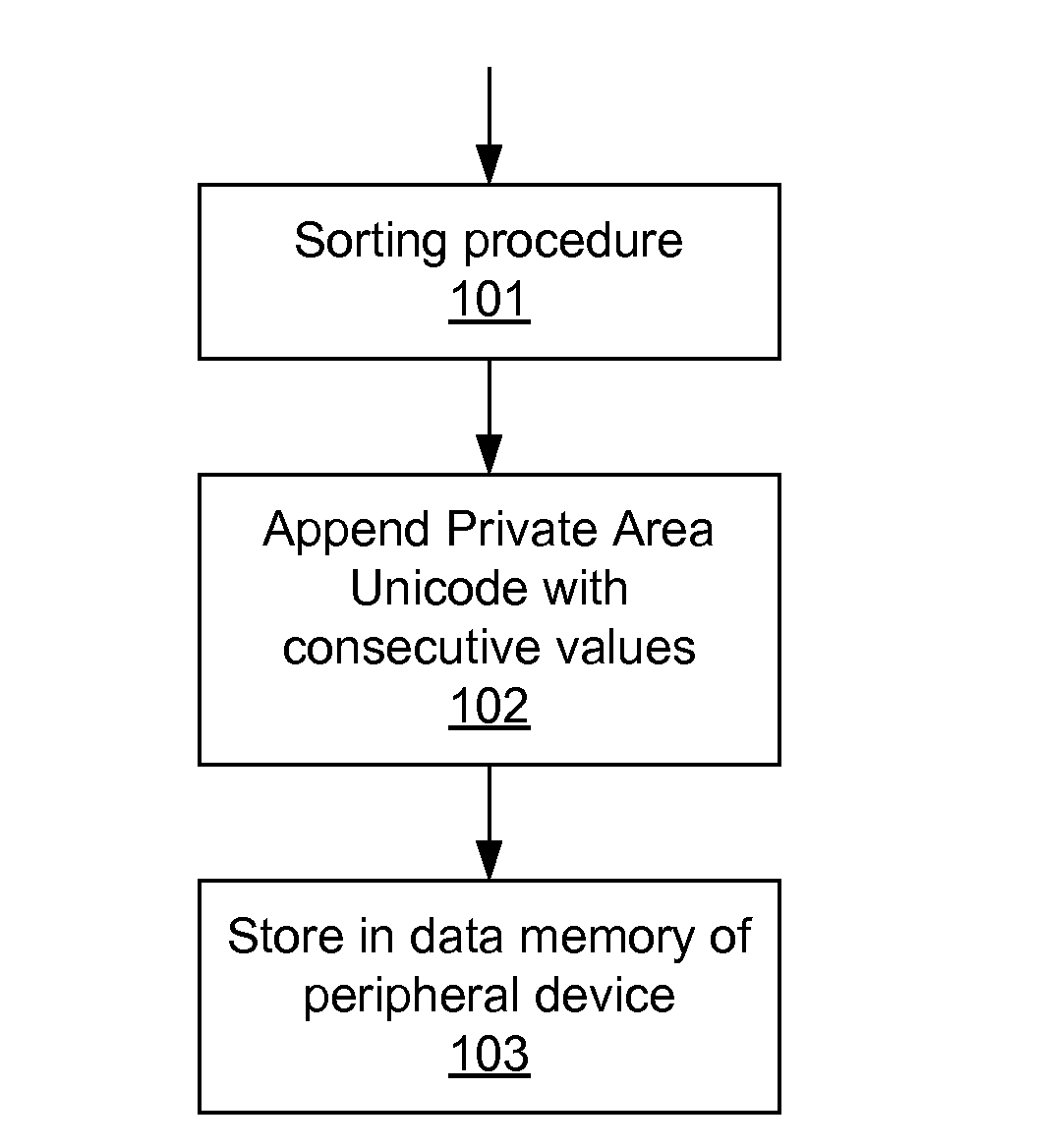
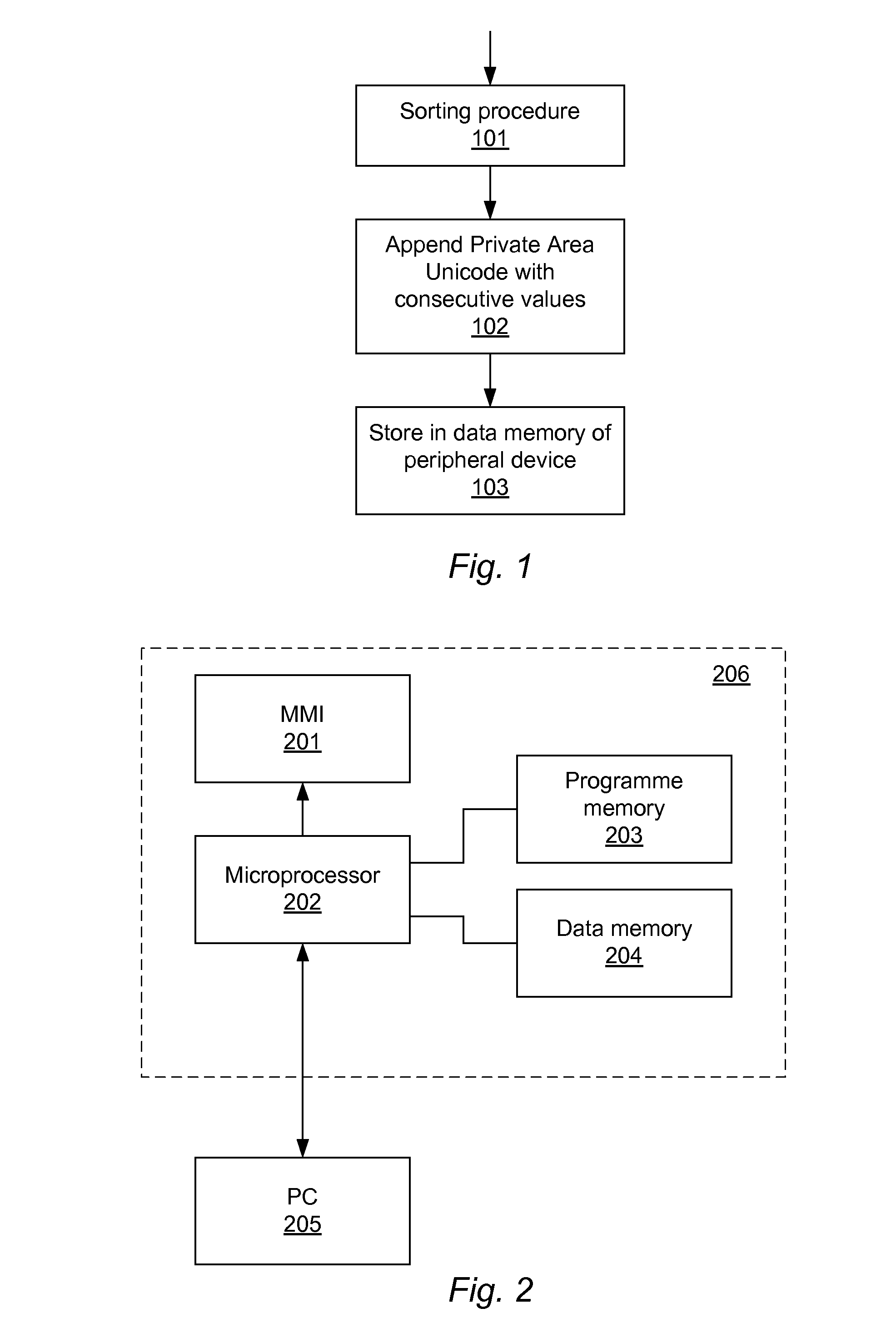
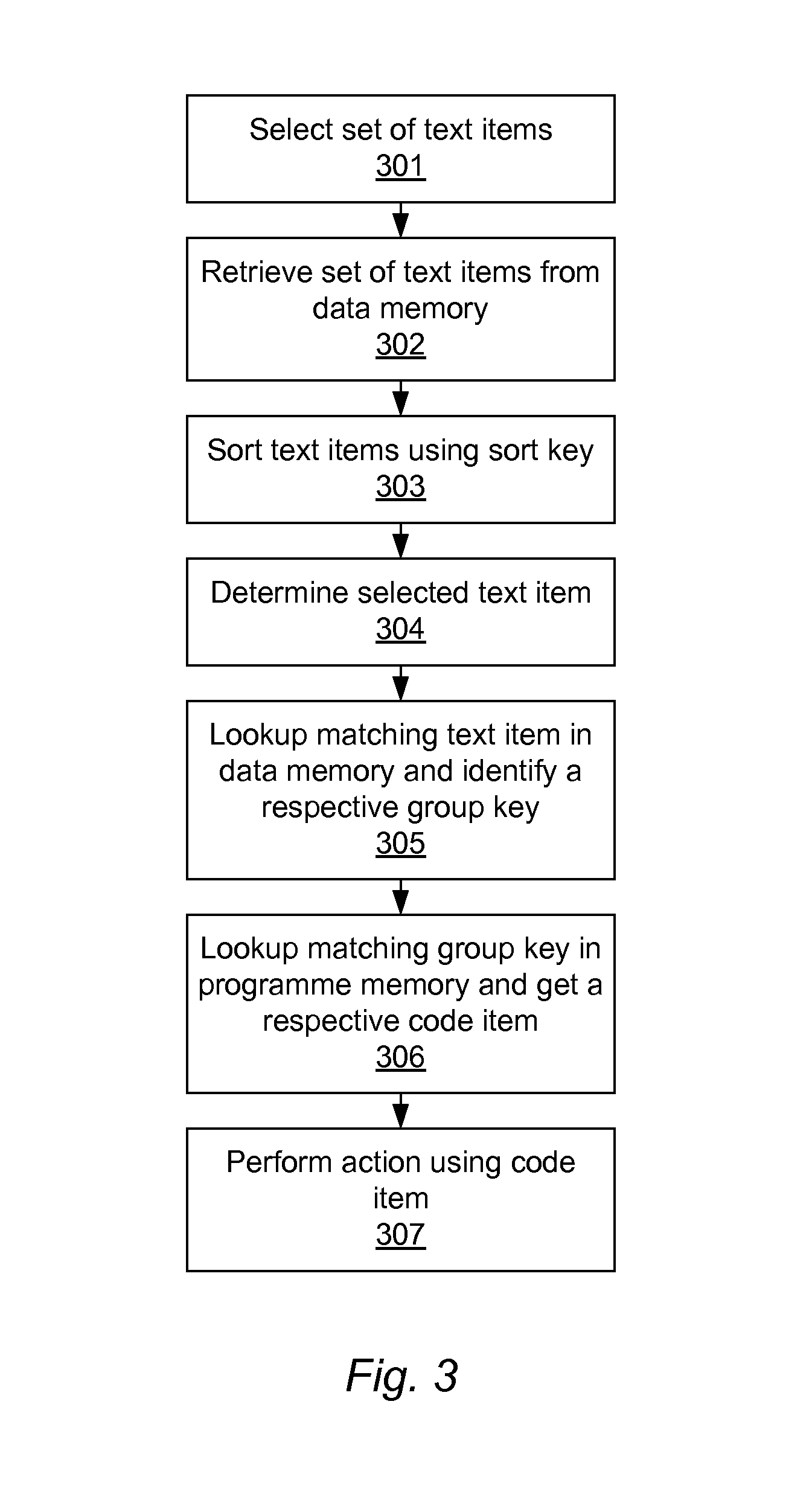
Computer-implemented method of arranging text items in a predefined order
ActiveUS20120323936A1Simple man-machine interfaceEnhanced interactionData sortingText database indexingWorld Wide WebTest item
A computer-implemented method of and a device, such as a base station for a headset, for arranging text items in a predefined order, comprising storing, in the memory of a peripheral device, a collection of multiple text items arranged in multiple sets of text items and in multiple groups of text items; storing a respective code item with a respective group of text items; and storing a sort key that has values that designate a predefined order of the text items in each set. The sort key is appended to the text items and comprises at least one character with a value within the Private Use range of the Unicode format.
Owner:GN NETCOM
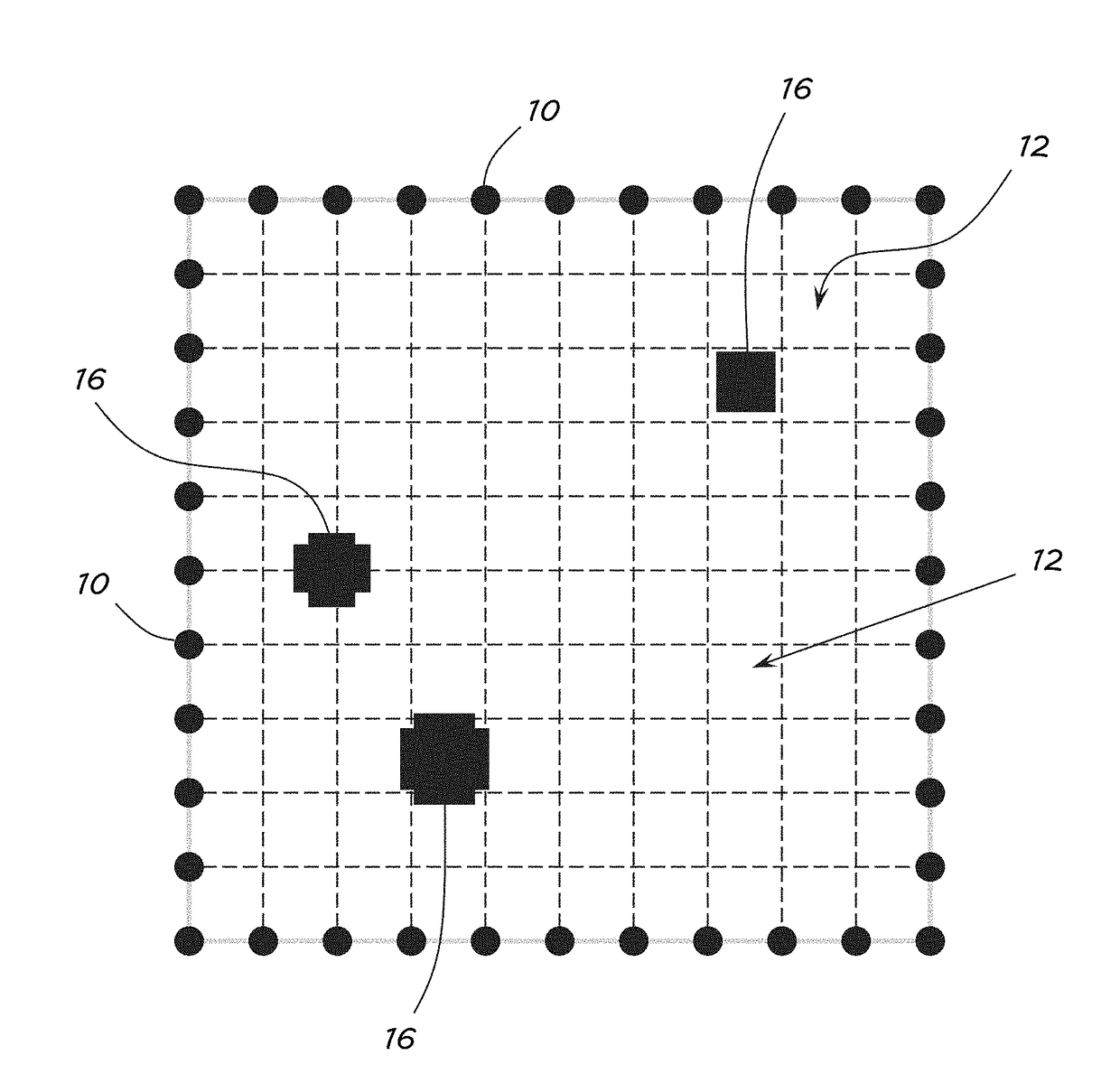
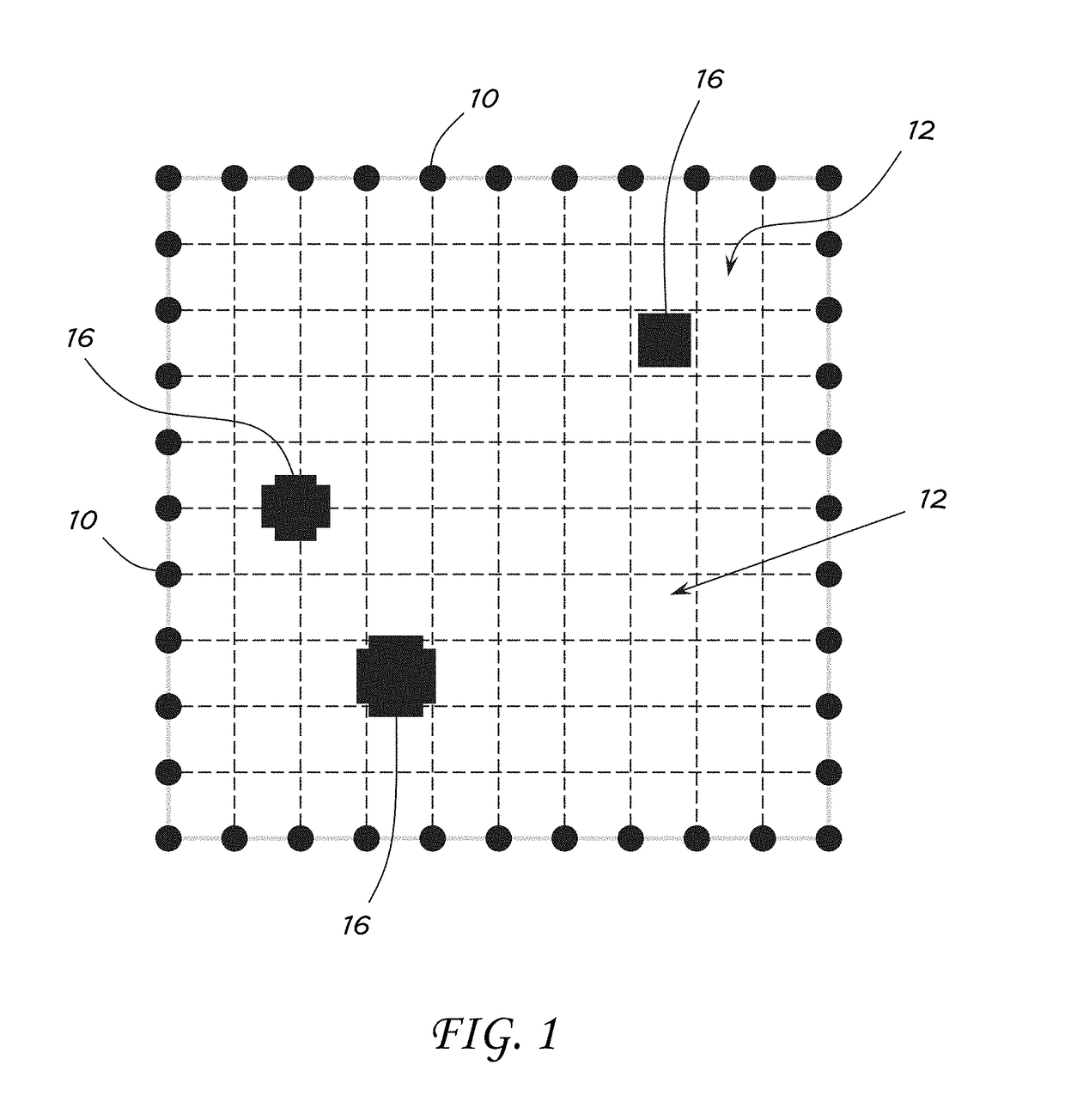
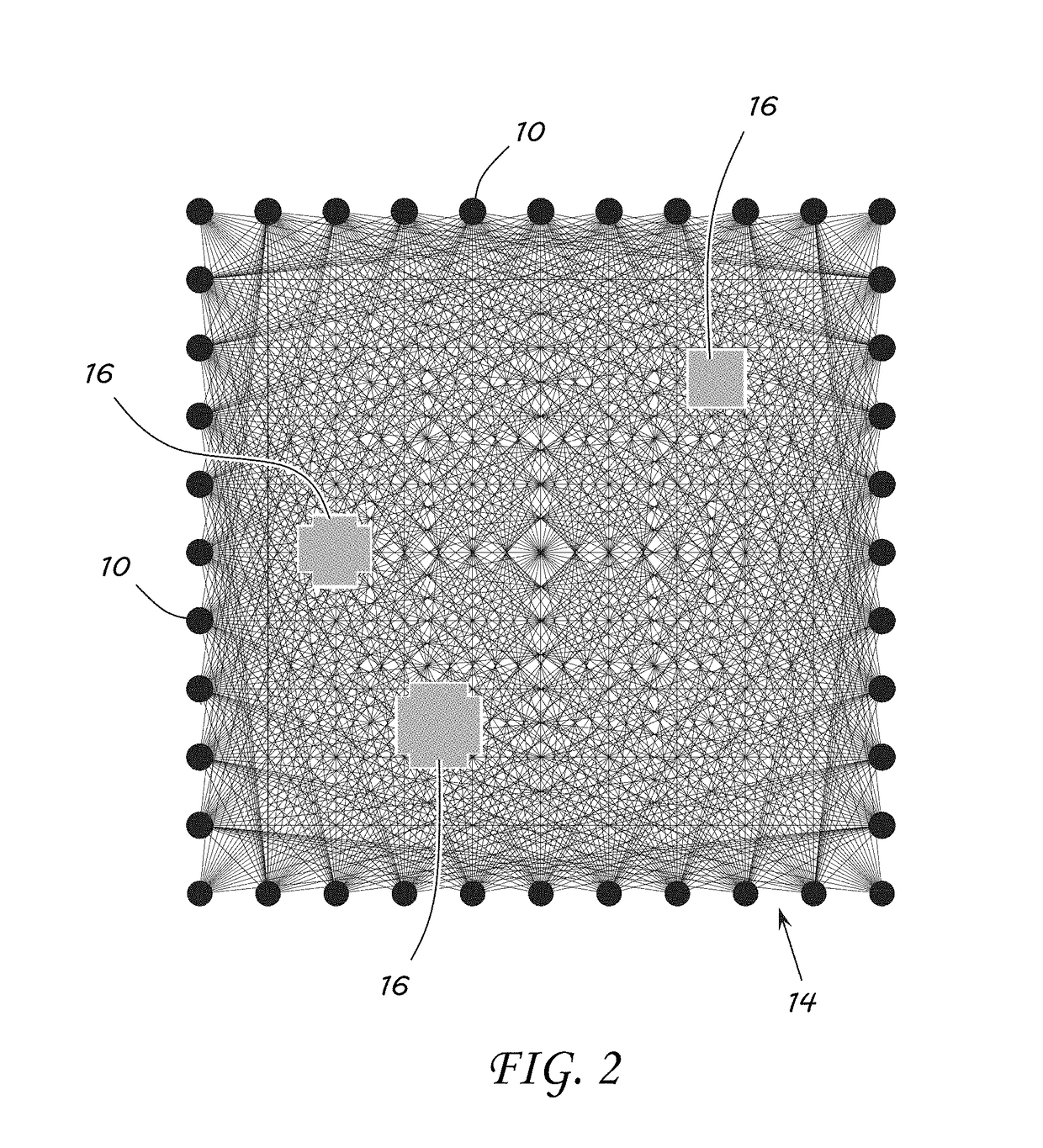
System and Method for Radio Tomographic Image Formation
A system and method for generating radio tomographic images is provided. A plurality of transceivers positioned around a region to be imaged is divided into a plurality of pixels. A control apparatus is configured to cause each of the plurality of transceivers in turn to send a signal to each of the other transceivers. The control apparatus is further configured to determine an attenuation in the received signals, generate weighing, derivative, and attenuation matrices from the signals, group the pixels into a plurality of provinces, select each province in turn and solve for a change in attenuation in each of the pixels while setting the pixels in other provinces to zero, aggregate solutions from each of the provinces into a rough estimate, re-solve each province using the aggregated rough estimate, aggregate the re-solved solutions from each province into a refined estimate, and generate an image from the refined estimate.
Owner:THE UNITED STATES OF AMERICA AS REPRESETNED BY THE SEC OF THE AIR FORCE
Client device for cellular telephone as server
InactiveUS8165558B2Assure integrityEasy to processNear-field transmissionMultiple digital computer combinationsOperational systemUser input
A new class of thin client called a trans client for operation with a smart cellular telephone as its server does not contain its own user interface (UI) and operating system (OS) and has no capability to run user programs as a standalone apparatus. Its purpose and capability is to display remote content and to provide user input interface. It is built with the slowest processing and lowest power consumption possible with the lowest cost and has security features to assure integrity of operations.
Owner:CELIO TECHNOLOGY CORPORATION
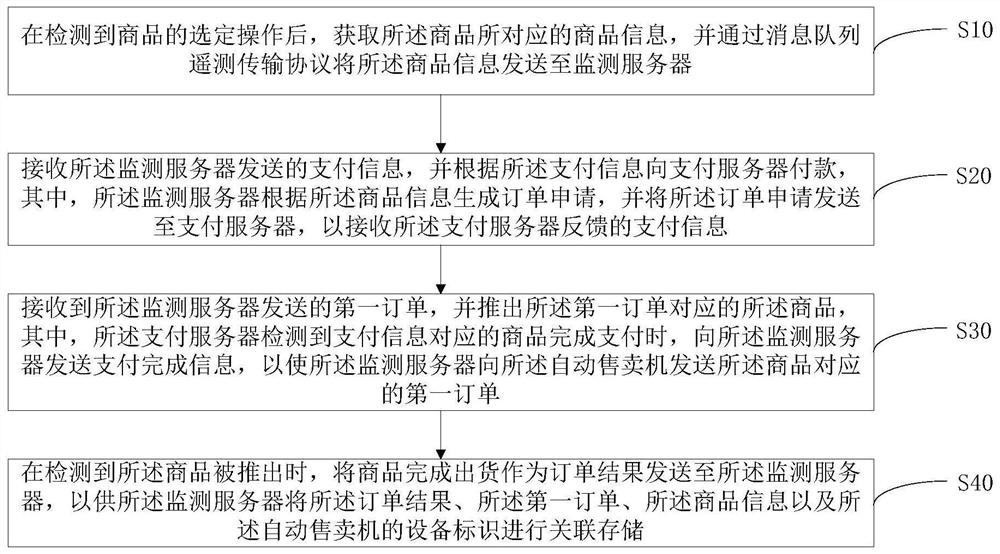
Delivery method of vending machine, vending machine and readable storage medium
PendingCN112651795AEasy to traceLimited computing powerPayment architectureBuying/selling/leasing transactionsMessage queueTransmission protocol
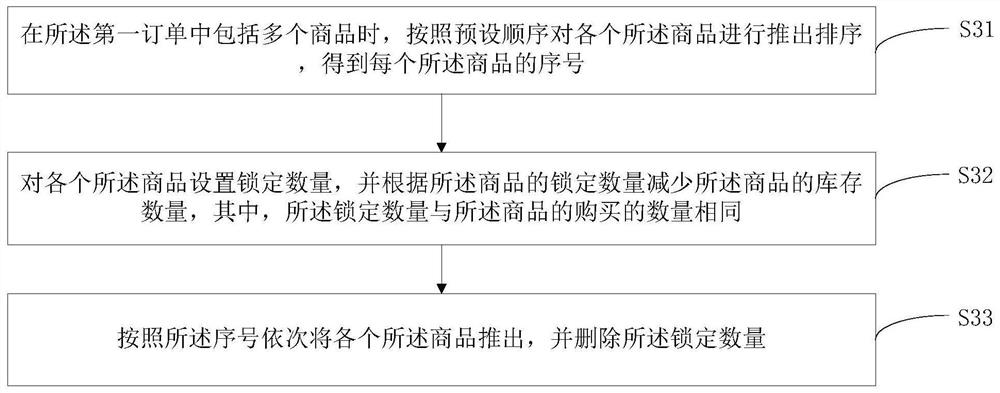
The invention discloses a delivery method for a vending machine, and the method comprises the following steps: obtaining the commodity information corresponding to a commodity after the selection operation of the commodity is detected, and transmitting the commodity information to a monitoring server through a message queue telemetry transmission protocol; receiving payment information sent by the monitoring server, and performing payment on the payment server according to the payment information; receiving a first order sent by the monitoring server, and pushing out a commodity corresponding to the first order; and when it is detected that the commodity is pushed out, delivering the commodity as an order result to be sent to a monitoring server, so that the monitoring server associates and stores the order result, the first order, the commodity information and the equipment identifier of the vending machine. The invention further discloses a vending machine and a readable storage medium. The monitoring server can trace back the reason why the vending machine is abnormal according to the stored information and the monitoring process.
Owner:SHENZHEN ZHILAI SCI & TECH
Method and data processing device for determining a spacing of rolling elements
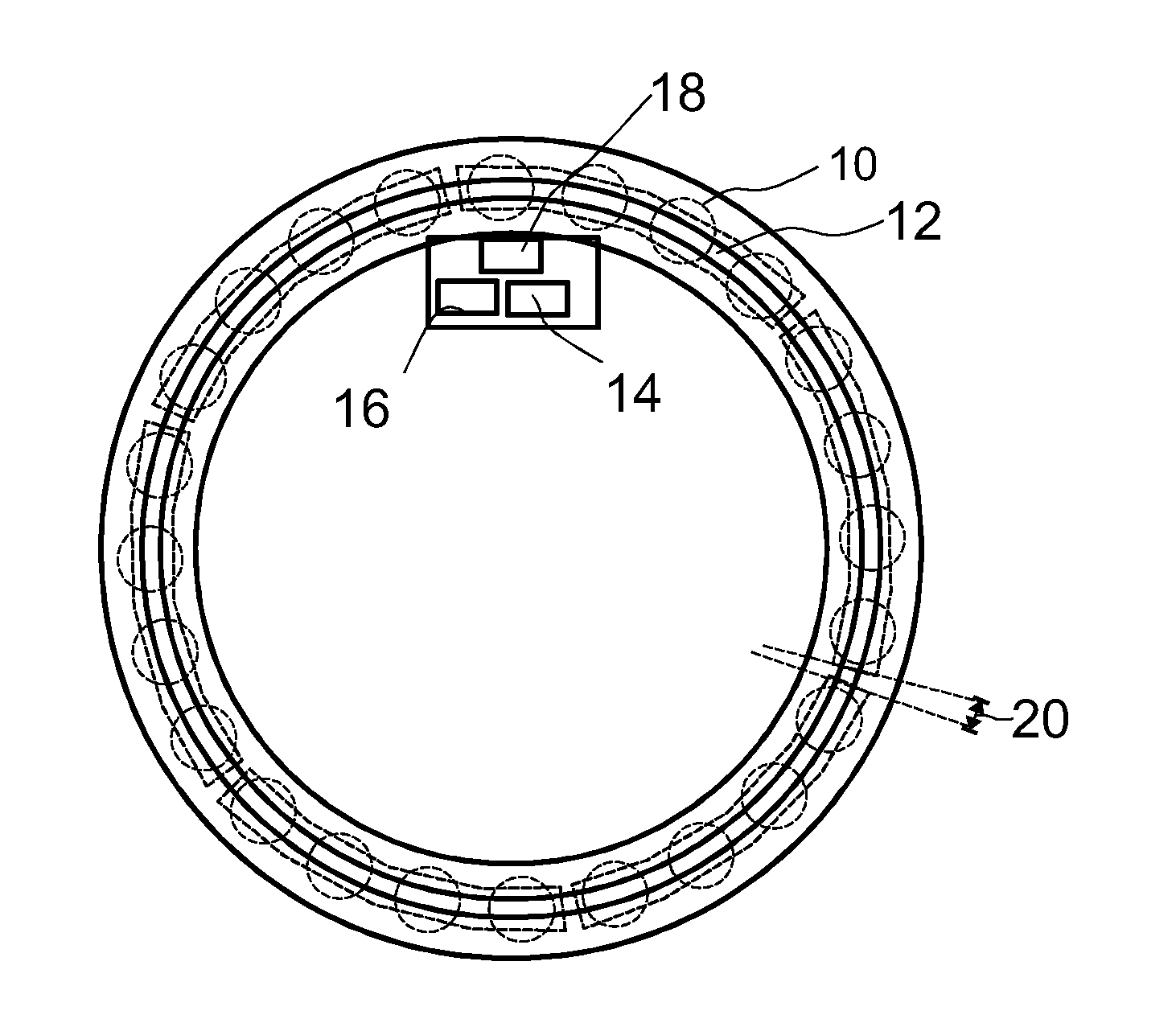
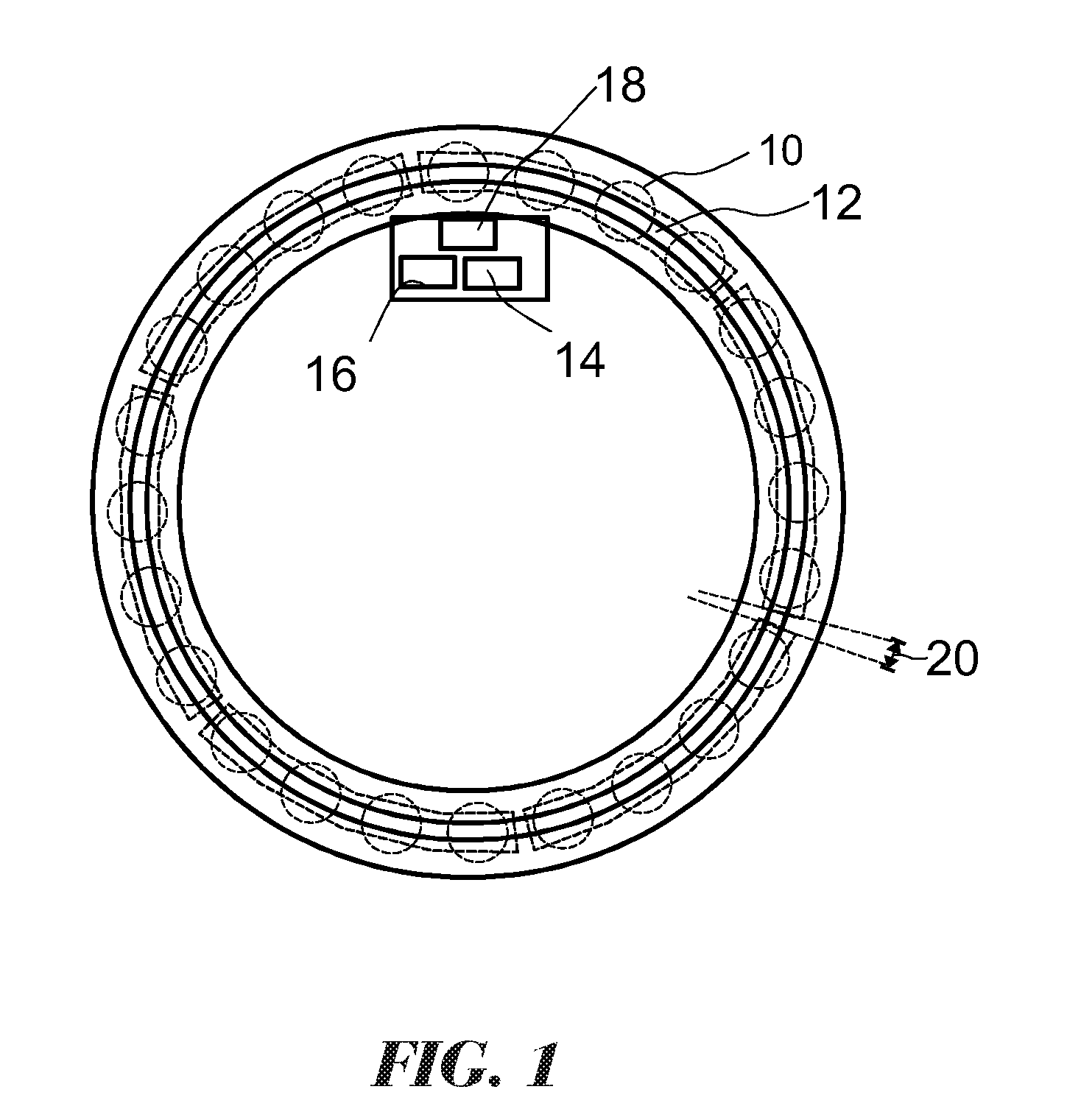
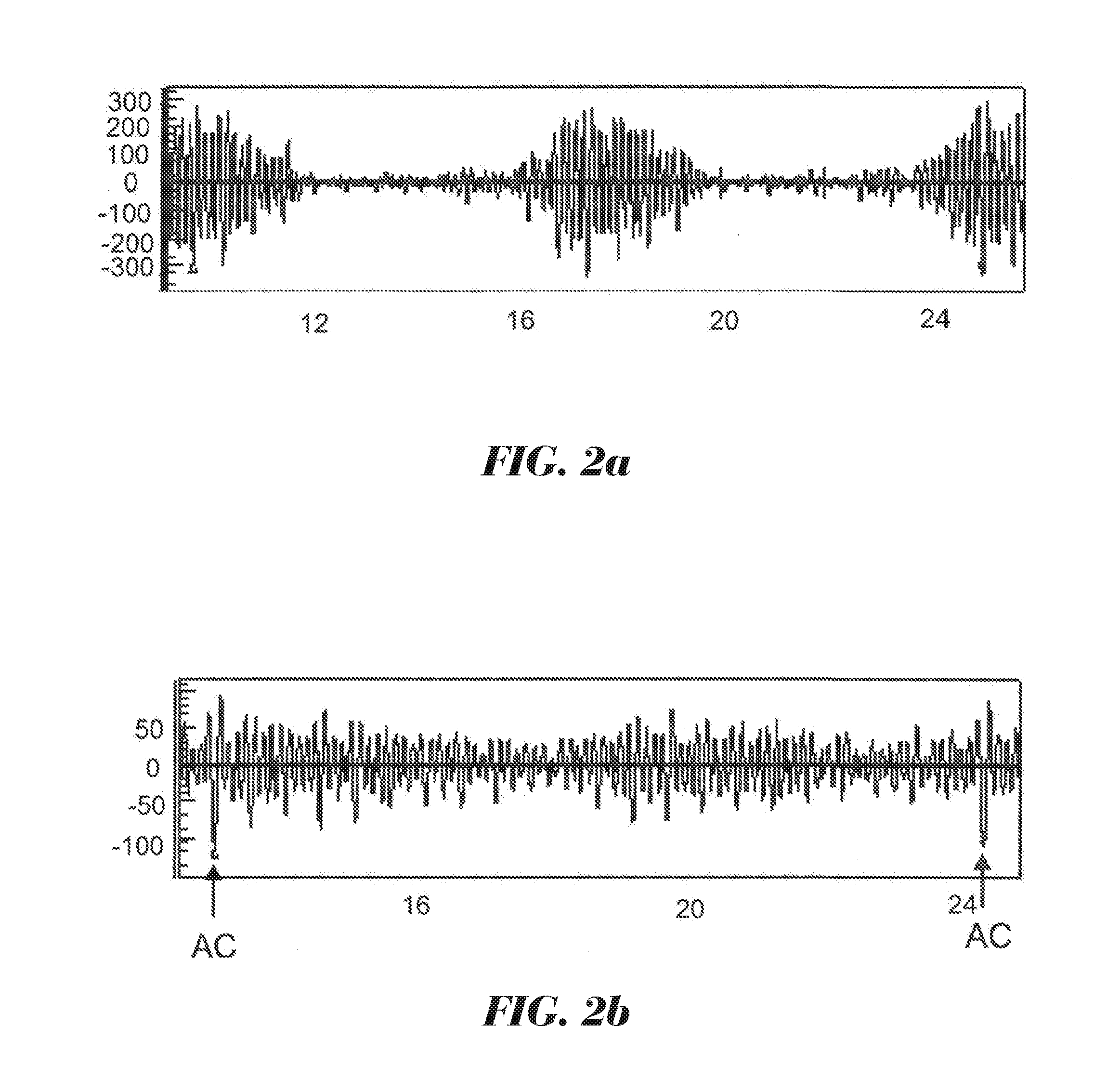
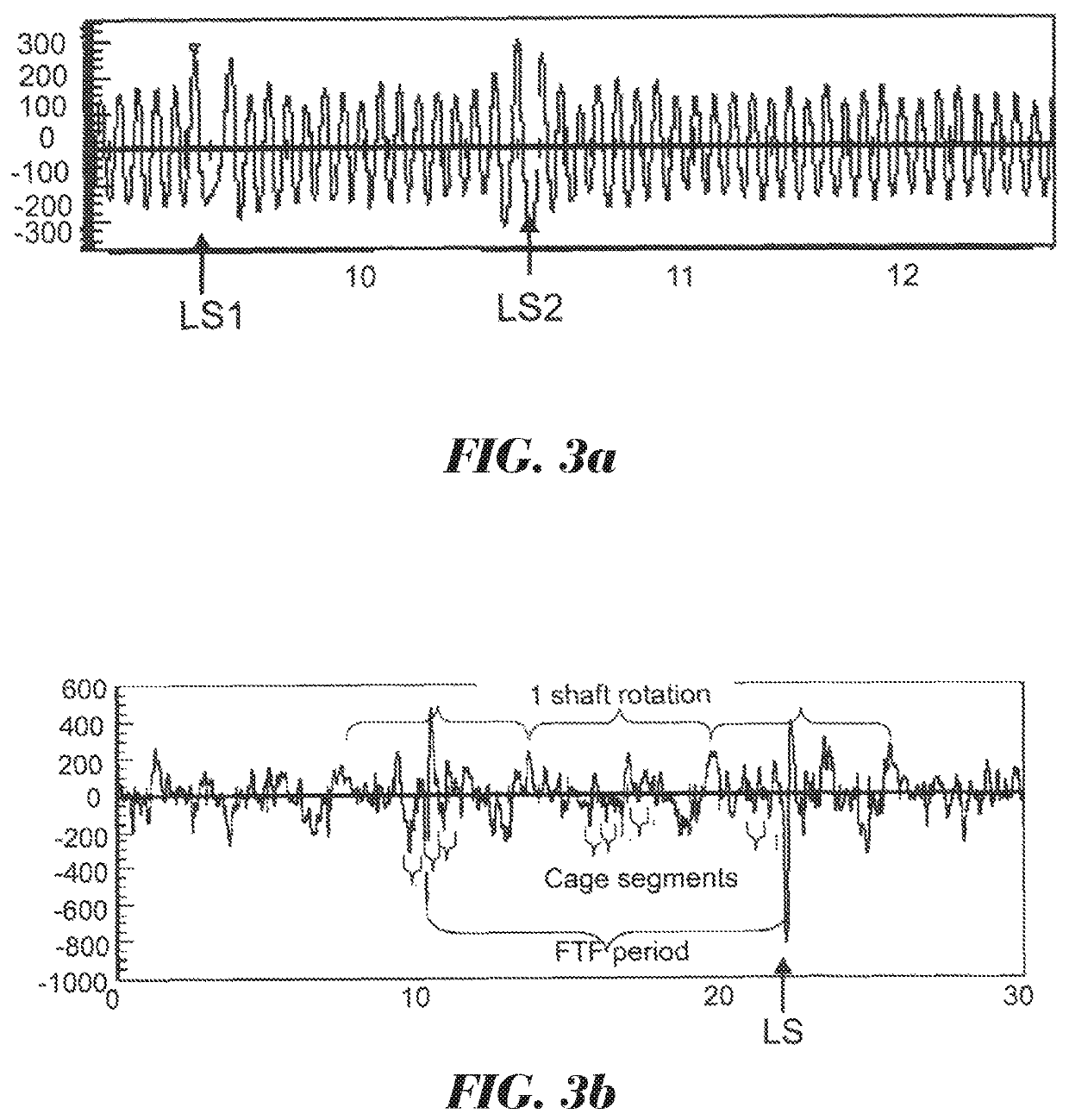
ActiveUS20160103037A1Reliable and simple wayLimited computing powerRolling contact bearingsMachine bearings testingEngineeringMechanical engineering
A method for detecting roller spacings in a roller bearing having at least one row of rollers wherein the rollers in the row are held by at least one cage, preferably by a plurality of roller cages. The method uses roller load induced strain signals for determining the roller spacings.
Owner:AB SKF
Method for operating a hearing device and hearing device
ActiveUS10609494B2Suitable for everyday useStrong signalHearing device active noise cancellationElectromyographyEar AuricleHearing apparatus
A method operates a hearing device for a user. In the method, electromyography is performed, in which a muscle activity of an auricular muscle of the user is measured by an electrode array. The muscle activity is continuously measured to detect a complex activity profile of the auricular muscle, in which the user's intention is coded. The electrode array generates a sensor signal that is classified by means of a classifier, and in this classification process, the muscle activity is decoded and the underlying intention is determined by examining whether the sensor signal has a previously known feature vector. The previously known feature vector is assigned to an operating mode of the hearing device, which is set when the sensor signal has the previously known feature vector.
Owner:SIVANTOS PTE LTD
Method and device for locating a magnetic object
ActiveUS9778016B2Reduce in quantityLimit required computation powerElectric/magnetic detectionPoint coordinate measurementsMagnetic tension forceArray data structure
Owner:COMMISSARIAT A LENERGIE ATOMIQUE ET AUX ENERGIES ALTERNATIVES
Digital mission preparation system
PendingUS20220358725A1Reduce volumeLimited computing powerMaps/plans/chartsImage data processingSoftware engineeringNetwork on
A system for preparing a mission from a digital mapping, includes a mission editor generating mission elements that can change over the course of several determined temporal phases, including on a network a mission server, a mapping server, a server for sharing at least one centre of the map and a plurality of augmented reality headsets, at least one of the augmented reality headsets, called master headset, being able to generate at least one command for modifying the centre, each headset being able to receive at least two sets of elevation and terrain tiles from the mapping server, the mission server interfacing with the headsets to share and update the mission elements and to change them over time.
Owner:AIRBUS DEFENCE & SPACE
Method performed by a control unit for controlling energy flows of a vehicle
ActiveUS10351124B2Limited computing powerHybrid vehiclesInternal combustion piston enginesForms of energyEnergy system
In a method performed by a control unit for controlling energy flows of a vehicle, where the vehicle includes a vehicle energy system which in turn includes a plurality of energy subsystems. Within each energy subsystem one form of energy is used. The energy subsystems are operationally connected by converters, wherein converters are devices converting at least one form of energy to another form of energy. By setting a price, limits for the converters converting energy between the energy subsystem the energy flows of the vehicle can be controlled by the control unit such that at least during period of times the order in which the energy subsystems of the vehicle is provided with energy can be changed.
Owner:VOLVO TRUCK CORP
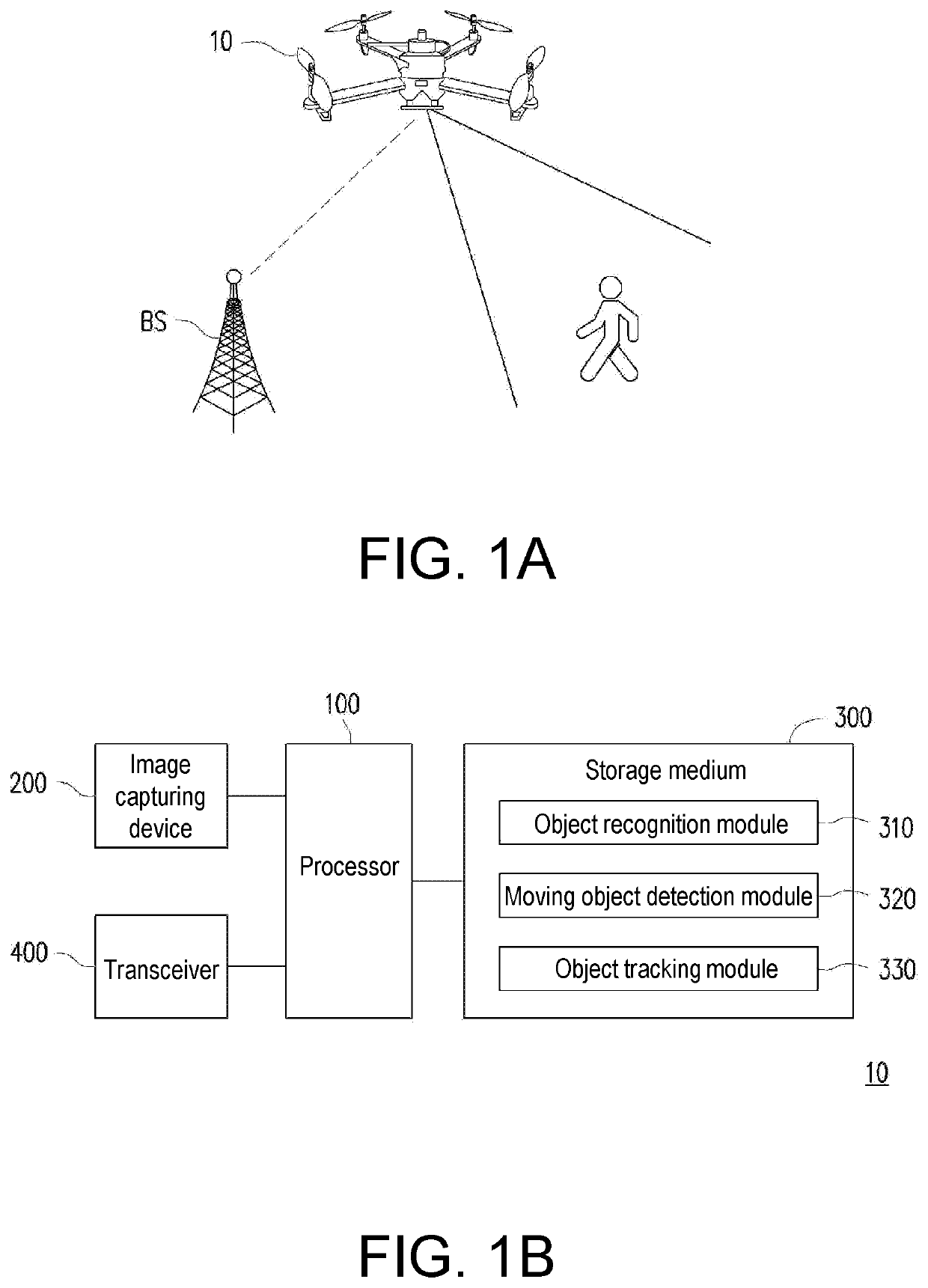
Unmanned aerial vehicle and image recognition method thereof
PendingUS20210291980A1Overcome inaccurate recognitionAccurate detectionImage enhancementImage analysisComputer graphics (images)Uncrewed vehicle
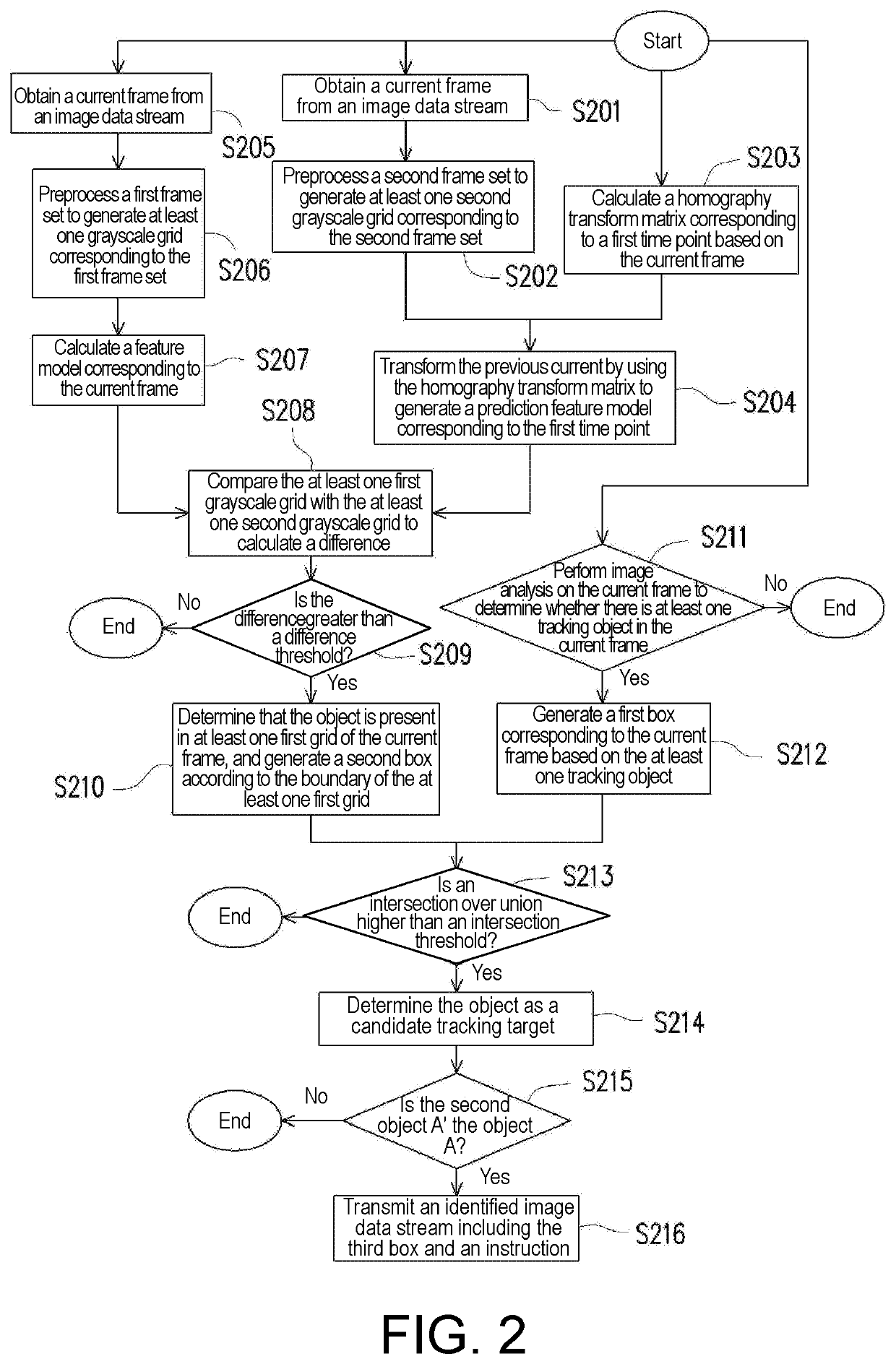
The invention relates to an unmanned aerial vehicle (UAV) and an image recognition method applied to a UAV. The image recognition method includes: obtaining an image data stream, wherein the image data frame includes a current frame; performing image recognition on an object in the current frame to generate a first box corresponding to the current frame; detecting movement of the object to generate a second box corresponding to the current frame; and determining the object as a tracking target according to the first box and the second box. A moving object can be accurately identified, detected, and tracked according to the UAV and the image recognition method provided in embodiments of the invention.
Owner:CORETRONIC
Method and data processing device for determining a spacing of rolling elements
ActiveUS10564069B2Reliable and simple wayLimited computing powerRolling contact bearingsMachine bearings testingStructural engineeringMechanical engineering
Owner:AB SKF
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com