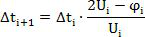Method for dynamically adjusting scheduling opportunity and scheduling quantity of endogenous safety system
A security system and dynamic adjustment technology, applied in the field of network security, can solve problems such as less consideration of scheduling timing and the number of executives, insufficient flexible adjustment capabilities, redundant waste, etc., to achieve balanced security and operating costs, and good security The effect of reducing the risk of system failure and operating cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
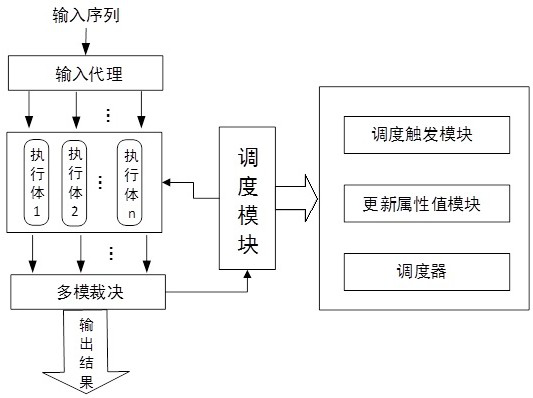
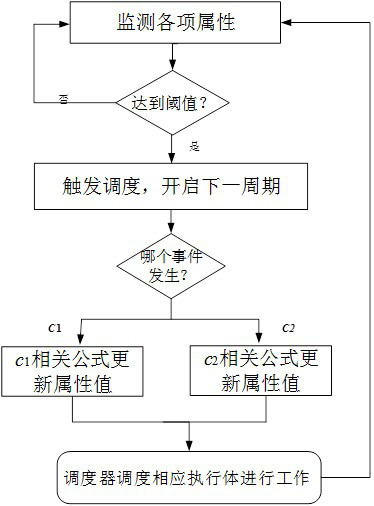
[0094] Suppose there is an SDN defense system designed with DHR architecture, and use n i =5 controllers with different structures and the same functions are used as heterogeneous executives, and the scheduling work duration is Δt i = 5 minutes, the abnormal threshold is =3. During the work process, the attacker uses the vulnerability to launch a tentative attack on the system. The number of attacks in one minute is less than 20. The number of abnormal heterogeneous executives detected by the scheduling module has never exceeded the abnormal threshold. =3 will not switch the scheduling process C 2 , the system works normally until the end of the scheduling cycle, and the scheduling enters the next cycle. This switch is performed by C 1 Event triggering; the scheduling triggering module encapsulates the corresponding information that the working time of this scheduling period is 5 minutes, the abnormal threshold value is 3, and the number of execution bodies is 5, and then...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com