Unstructured P2P botnet detection method and device based on SAW community discovery
A botnet and unstructured technology, applied in the field of image encryption, can solve the problems of complex topology, difficult to be detected, difficult to obtain complete topology, etc., and achieve good parallelism
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
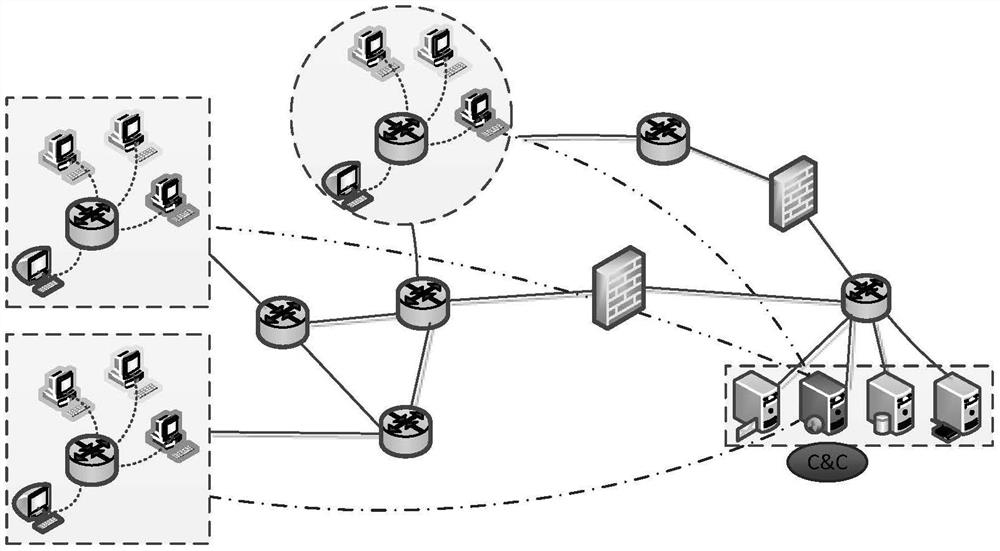
[0065] Such as figure 2 As shown, the embodiment of the present invention provides a kind of unstructured P2P botnet detection method based on SAW community discovery, comprises the following steps:
[0066] S101: Using the ARGUS tool, convert the original pcap format traffic data into netflow format traffic data;
[0067] Specifically, the captured original network traffic is a pcap format data stream, which is composed of several data packets. The data volume is huge and the statistical characteristics are not obvious. Therefore, the ARGUS traffic processing tool is used to aggregate it into a two-way netflow format.
[0068] S102: Use the Flink big data platform to convert the traffic data in netflow format into a quintuple cluster flow, and filter the quintuple cluster flow to obtain a P2P cluster;
[0069] Specifically, this step specifically includes:
[0070] S1021: For the netflow format traffic data of each host H, extract according to the same quaternion to obtain...
Embodiment approach
[0083] As an implementable manner, the construction of the shared neighbor graph specifically includes:
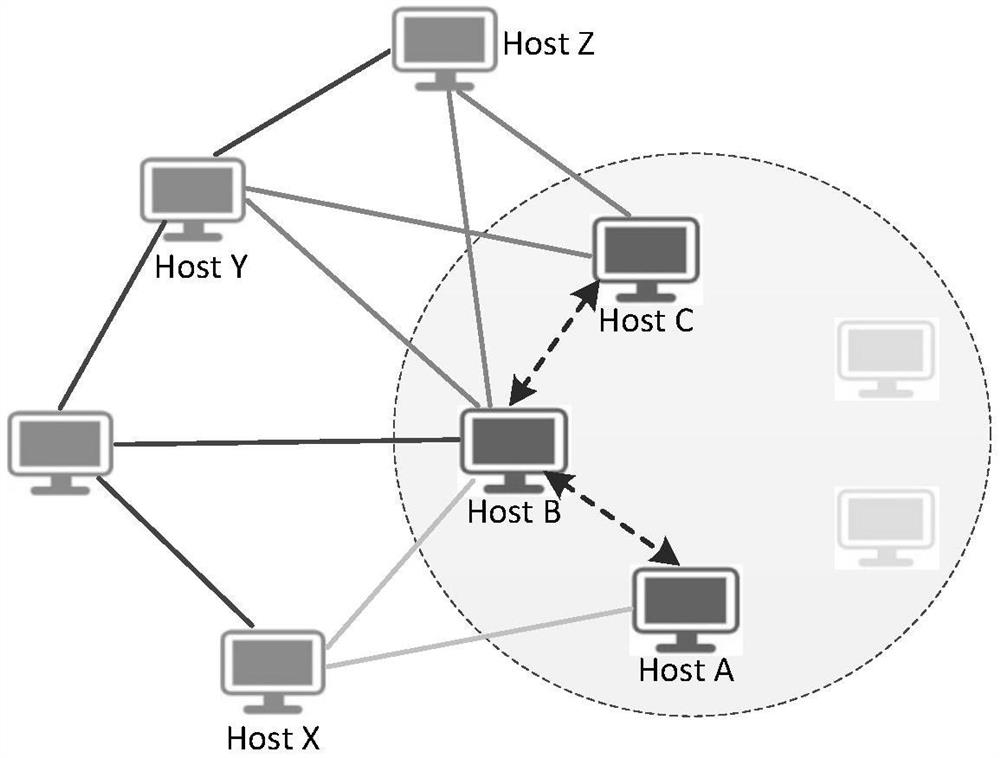
[0084] Initialize the undirected graph G={V,E}, then use the number of the P2P cluster of each host as the vertex V, and set the confidence Sim p2p (H i , H j ) greater than 0 for two P2P clusters p2p (H i ), FF p2p (H j )> As the edge E, the confidence Sim of the two P2P clusters p2p (H i , H j ) as the weight w of edge E ij , taking the resulting undirected graph as a shared neighbor graph.
[0085] For example, if image 3 As shown, hosts A, B, and C are vertices in the interconnection graph. Among them, host A and host B share a neighbor node X, and the weight is 1; host B and host C share two neighbor nodes Y, Z, and the weight is 2. Schematic diagram of a P2P network SNG with 500 nodes produced by using Gephi tool as shown in Figure 4 shown.
[0086] S104: Use SAW to access each vertex in the shared neighbor graph, generate a vertex matrix between verti...
Embodiment 2
[0117] An embodiment of the present invention provides an unstructured P2P botnet detection device based on SAW community discovery, including: a data preprocessing module, a feature extraction module, a shared neighbor graph construction module, a community discovery module, and a classification module; wherein:
[0118] The data preprocessing module is used to convert the original pcap format traffic data into netflow format traffic data. The feature extraction module is used to use the F-link big data platform to convert the traffic data in the netflow format into a quintuple cluster flow, and filter the quintuple cluster flow to obtain a P2P cluster. The shared neighbor graph construction module is used to calculate the weight of the shared neighbor nodes between P2P clusters by using the Jaccard coefficient, and construct the shared neighbor graph. The community discovery module is used to use SAW to access each vertex in the shared neighbor graph, generate a vertex matri...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com