Block chain anonymous user auditing method and system applied to block chain client
A blockchain and client-side technology, applied in the blockchain field, can solve problems such as the inability to protect the privacy of participants, and achieve the effect of ensuring supervision and auditing and ensuring privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
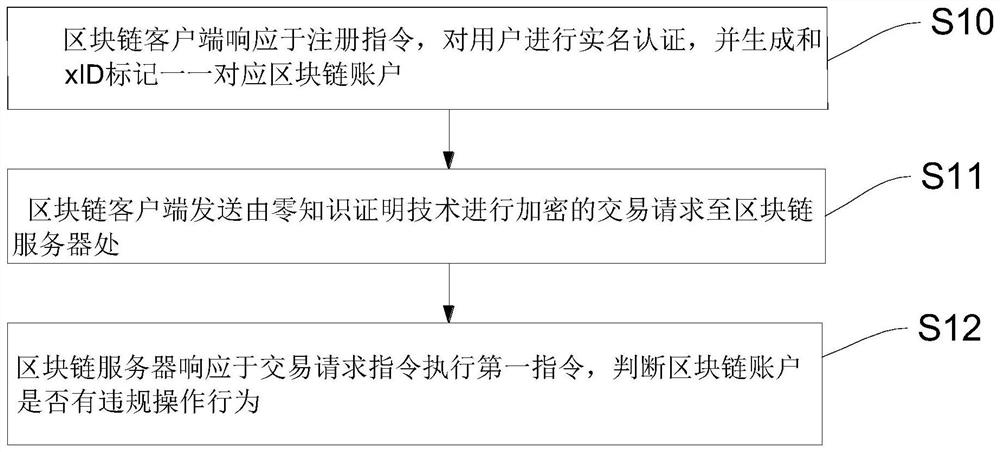
[0047] See figure 1 , figure 1 A flow diagram of a block chain anonymous user auditing method provided in Example 1 of the present invention, a block chain anonymous user auditing method, including the following steps:
[0048] S10, block chain client in response to registration instructions, real-name authentication of the user, and generates a corresponding zone chain account with the XID tag;
[0049] S11, block chain client sends a transaction request to the block chain server by a zero knowledge certificate technology;
[0050] S12, the block chain server performs the first instruction in response to the transaction request instruction, and determines whether the area block chain account has illegal operation behavior.
[0051] In step S10, the generation and XID tag one-one correspondence block chain account includes: block chain client generates EID (Electronic Identity, Citizen Network Electronics Identity), and generates blocks based on EID based on EID Chain account, the...
Embodiment 2
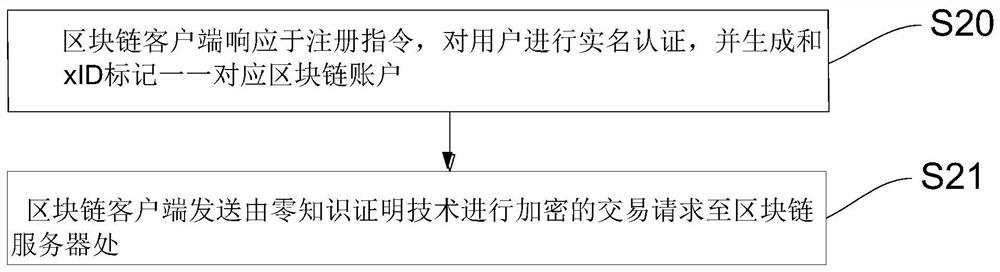
[0072] See figure 2 , figure 2 For the block chain of the block chain of the block chain, the block chain of the block chain, a block chain is an anonymous user auditing method, which is applied to the block chain client, including the following steps:
[0073] S20, block chain client in response to the registration instruction, perform real-name authentication for the user, and generates a corresponding zone chain account with the XID tag;
[0074] S21, the block chain client sends a transaction request from a zero knowledge certificate to the block chain server.
[0075] In step S20, the generation and XID tag one-one correspondence block chain account includes: block chain client generates EID (Electronic Identity, Citizen Network Electronic Identity), and generated block based on EID based on EID Chain account, the EID, block chain accounts are stored in the user information server.
[0076] Among them, the information of the block chain account includes a private key, a publi...
Embodiment 3
[0084] See image 3 , image 3 A flow diagram of the block chain unique user auditing method for the block chain server according to Embodiment 3 of the present invention, a block chain anonymous user auditing method, which is applied to the block chain server, including the following steps
[0085] S30, in response to the transaction request instruction, executes whether or not there is illegal operational behavior in determining the block chain account.
[0086] In step S30, it is also included in response to the periodic review instruction, and the execution of the second instruction judgment area block chain account has illegal operation behavior.
[0087] After the block chain server receives the transaction request, the execution first instruction includes:
[0088] S301, using illegal rules zero knowledge certificate verify that the transaction is violated, if it is verified, there is no violation;
[0089] If it is not possible to verify, the decrypted account data is obtain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com