Multi-data encryption system and method of cloud computing system
A data encryption and cloud computing technology, which is applied in the field of cloud computing, can solve the problems of high encryption complexity and low efficiency of cloud computing operation, and achieve high decryption efficiency, avoid data security problems, and make cracking difficult.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
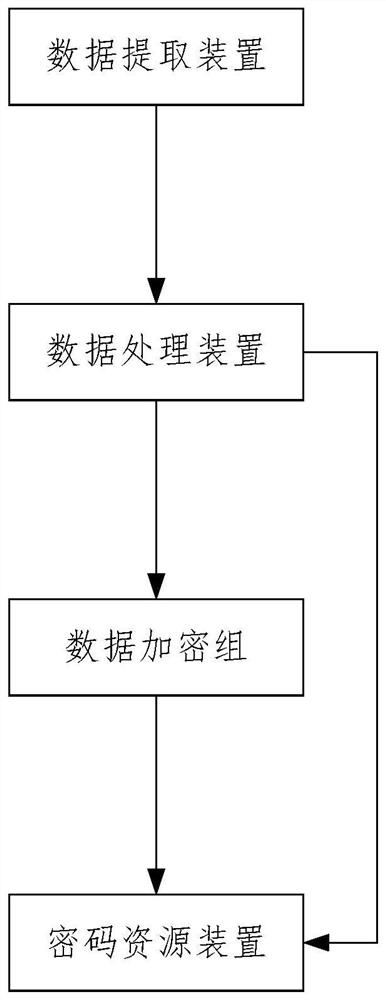
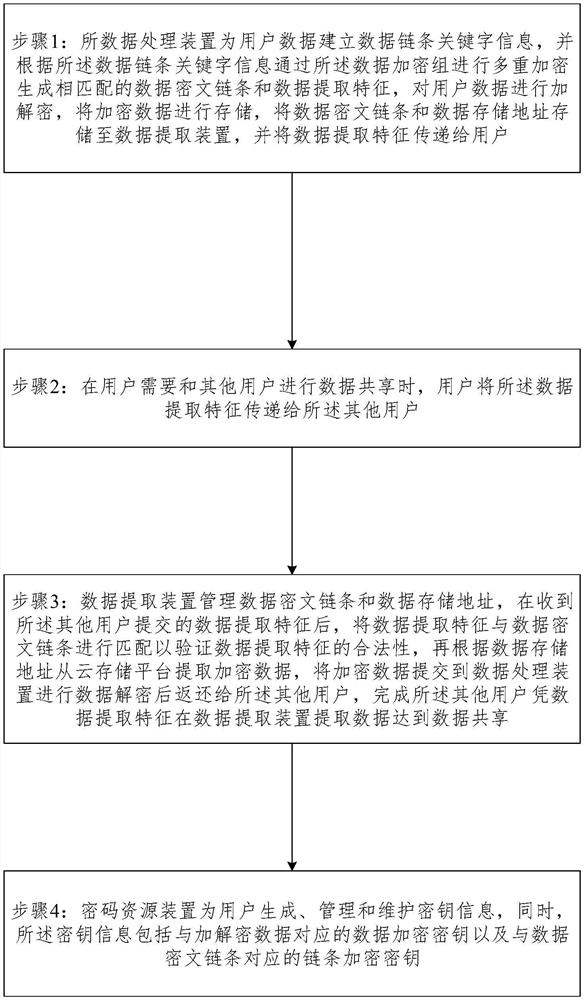
[0032] Such as figure 1 As shown, a multiple data encryption system of a cloud computing system, the system includes: a data extraction device, a data processing device, a data encryption group and a password resource device that are located in a cloud computing environment and connected in sequence; the data processing device is configured It is used to establish data link keyword information for user data, and perform multiple encryptions through the data encryption group according to the data link keyword information to generate matching data ciphertext chains and data extraction features, and encrypt and decrypt user data, Store the encrypted data, store the data ciphertext chain and data storage address in the data extraction device, and pass the data extraction features to the user; when the user needs to share data with other users, the user will pass the data extraction features to the For the other users, the data extraction device is configured to manage the data cip...
Embodiment 2
[0035] On the basis of the previous embodiment, the data encryption group includes: a first data encryption device, a second data encryption device and a third data encryption device; the first data encryption device is configured to perform encryption on the data to be encrypted Randomly divide twice to get three divided data, which are divided into the first data, the second data and the third data, and record the position of the division point in the data to be encrypted when the random division is performed twice at the same time, as Data link connection features, and encrypt the first data to obtain the first encrypted data; the second data encryption device is configured to encrypt the second data to obtain the second encrypted data; the third data encryption device , configured to encrypt the third data to obtain the third encrypted data, and at the same time, based on the data link connection characteristics recorded by the first data encryption device, connect the firs...
Embodiment 3
[0038] On the basis of the previous embodiment, after the data processing device generates the matching data ciphertext chain and data extraction features, it also generates a data integrity check code, and the data integrity check code is stored in the data extraction device ; After the data extraction device extracts the data from the cloud storage platform, it first performs data integrity verification according to the data integrity check code.
[0039] Specifically, in the process of data transmission, it will be affected by various interferences, such as pulse interference, random noise interference and artificial interference, etc., which will cause data errors. In order to control the errors in the transmission process, the communication system must take effective measures to control the generation of errors.
[0040] Commonly used error control methods allow each transmitted data unit to have redundant information sufficient to enable the receiving end to discover err...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com