Electronic lock safety system and key distribution method thereof
A technology of security system and key distribution, which is applied in the field of electronic lock security system and key distribution, which can solve the problems of counterfeiting, failure to unlock information destruction, and no security protection for unlocking passwords.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
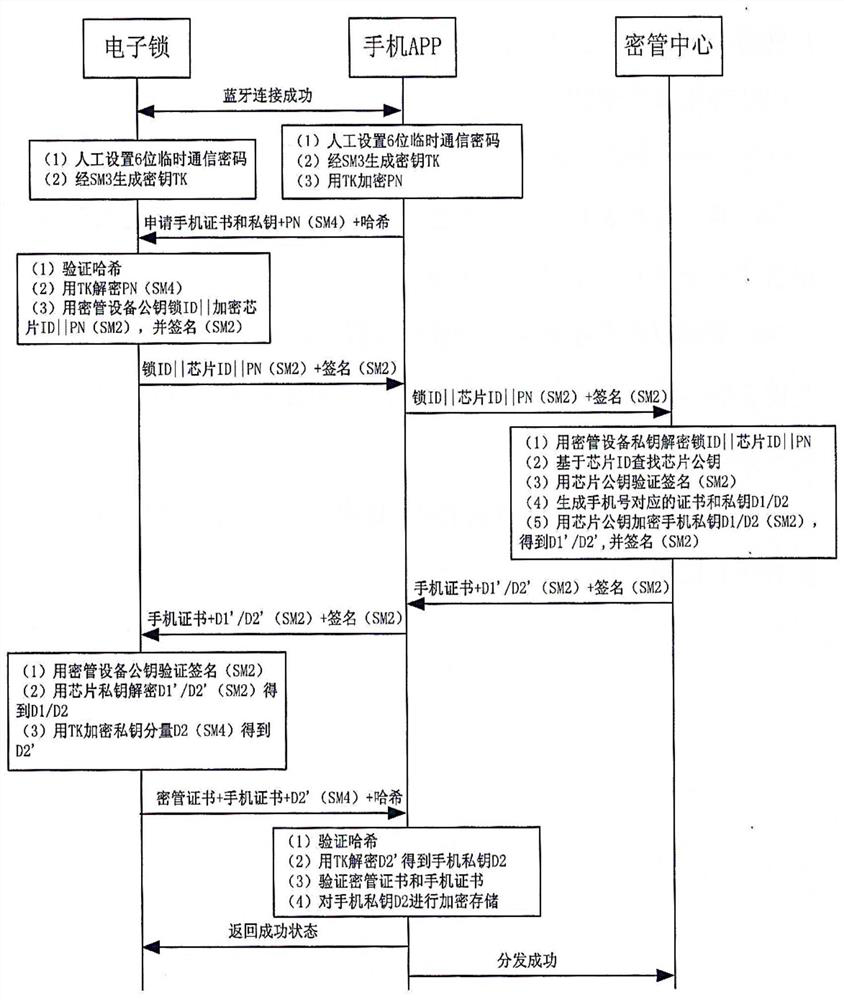
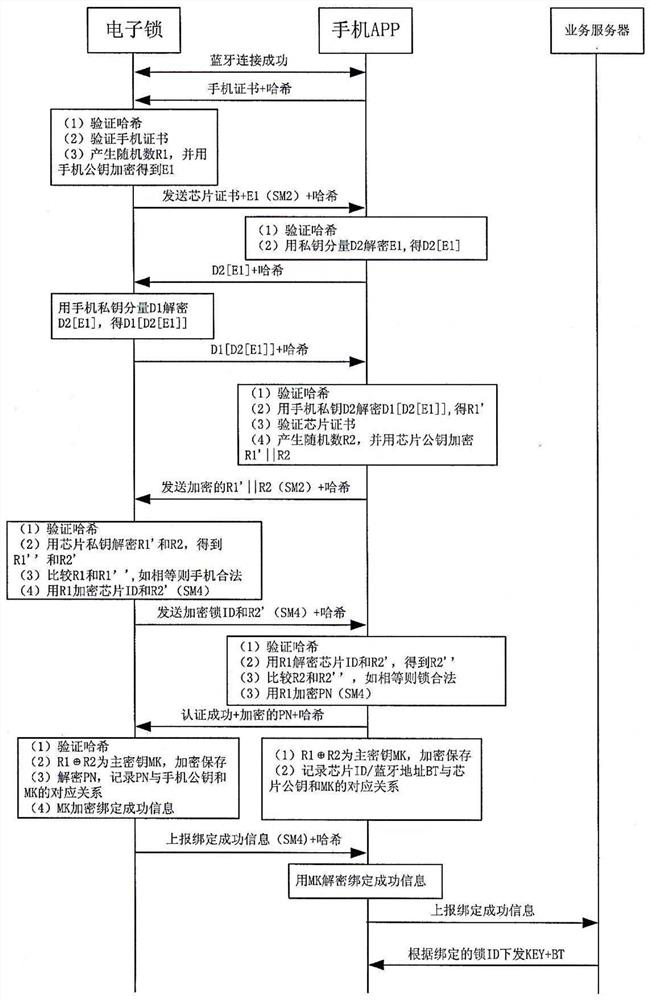
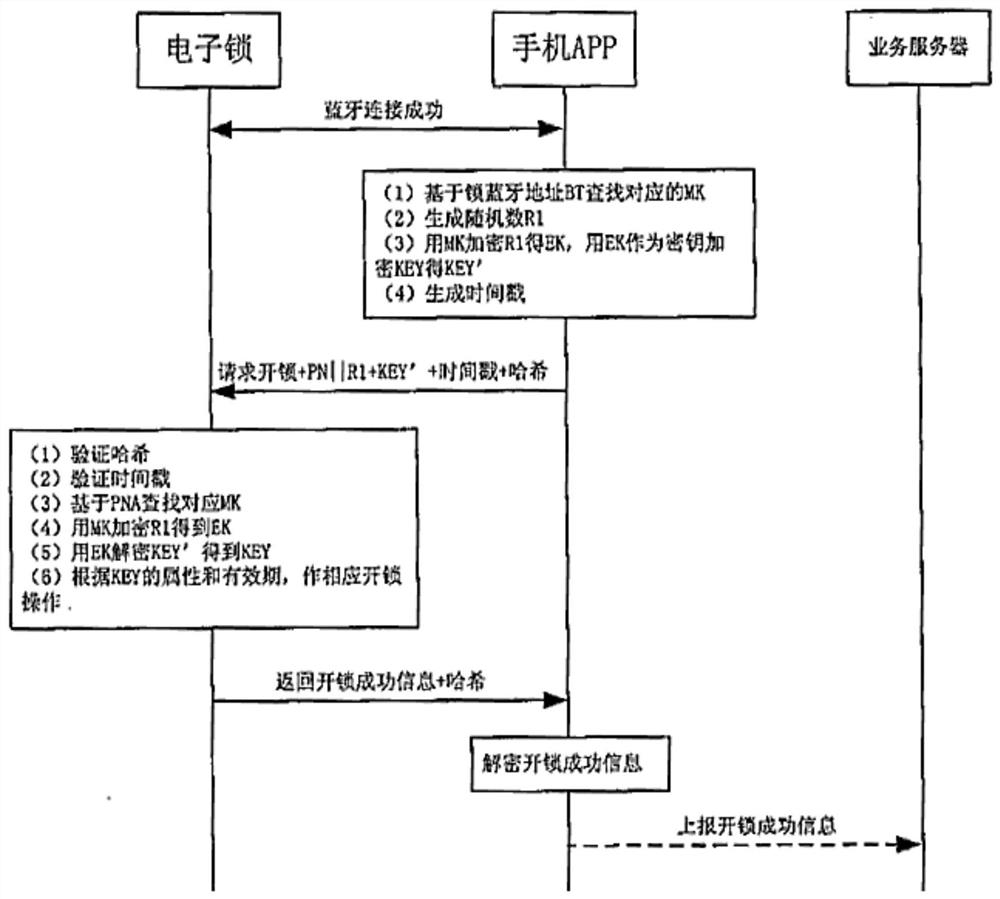
[0076] The electronic lock safety system of the present invention adds safety components on the basis of the electronic lock system. It includes an electronic lock terminal, a mobile communication terminal, a business server terminal, and a secret management center terminal. The electronic lock terminal includes an electronic lock control circuit and an electronic lock safety circuit connected to each other. The electronic lock control circuit is used to execute electronic The lock switch lock action, the electronic lock safety circuit is used to execute the electronic lock safety control program; the mobile communication terminal is based on the control circuit of the mobile communication device, and executes the command sending and receiving for the electronic lock unlock APP and the safety kit control module, and the safety kit control The module is combined with the electronic lock unlocking APP; the secret management center includes a secret management control circuit, and...
specific Embodiment approach 2
[0095] The electronic lock security system of the present application differs from the first embodiment in that the service server is not deployed on Alibaba Cloud, but communicates with the secret management center and the mobile communication terminal through the security gateway.
[0096] On the one hand, the mobile communication terminal communicates with the electronic lock, and on the other hand, it communicates with the operation and maintenance management system of the electronic lock.
[0097] The electronic lock operation and maintenance management system is used to report the unlock status information and manage the security of operation and maintenance information, including the secret management center, security gateway, business server host, business server backup machine, host cipher machine; business server host, business server backup machine On the one hand, it is connected to the security gateway, and at the same time, it is connected back-to-back with the ho...
specific Embodiment approach 3
[0105] In the electronic lock security system of the present invention, the secret management center includes a secret management control circuit, and the secret management control circuit includes a security module, a secret management server, a display, and a key injection adapter, and the interfaces of the secret management server are connected with the security module and the secret management server respectively. , display, key adapter connection.
[0106] The security module includes PCI-E card and USB key.
[0107] The key management server is equipped with a PCI-E interface, a USB interface, a network interface, a VGA interface, and a CD-ROM drive. key adapter.
[0108] The key management server includes a Raid controller, which is used to implement raid5 partitions on the hard disk, and provides guarantee for reliable data storage through disk mirroring.
[0109] In a specific embodiment of the present application, the PCI-E encryption card is built into the key man...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com