A blockchain-based cloud data integrity detection method and system
A data integrity, data integrity technology, applied in the field of cloud storage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0047] The integrity detection method of the block chain-based cloud data provided by the present invention, such as
[0048] figure 1 As shown, the main steps include:
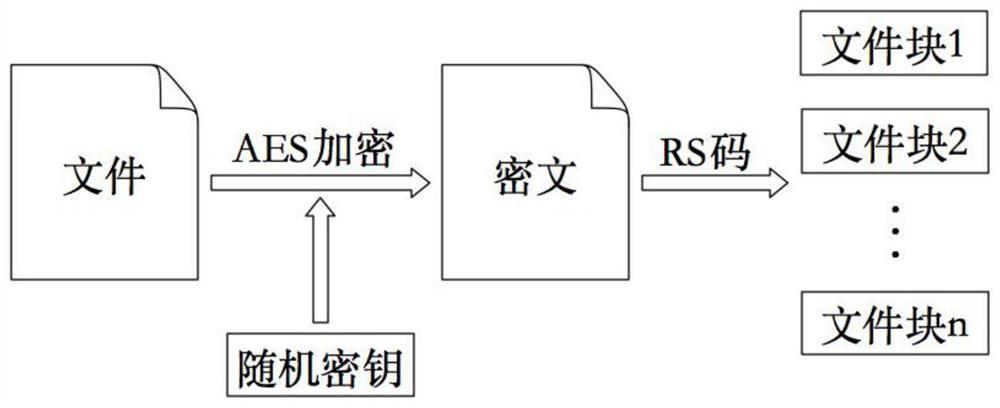
[0049] Step 1: The user processes the file using an encryption algorithm and an erasure code to obtain multiple file blocks.
[0050] The processing includes encrypting the file. The purpose of encrypting the file is to prevent the data content from being accessed by untrusted users. In the cloud storage scenario, the user's files may contain private and confidential information, and the user does not trust the cloud service provider. Therefore, in order to prevent the cloud service provider from reading the content of the user's file and ensure data security, the file needs to be encrypted before uploading.
[0051] Specifically, the encryption process may choose to use a symmetric encryption algorithm or an asymmetric encryption algorithm to encrypt the file according to different scenarios. When the fi...
Embodiment 2
[0100] Another embodiment of the present invention also provides a cloud data integrity detection system, such as Figure 4 As shown, the system includes: user upload module, cloud acceptance module, user detection module and cloud detection module. in,
[0101] The user upload module is used to process the file and upload it to the cloud acceptance module. For specific methods, please refer to steps 101, 102 and 103 in Example 1;
[0102] The cloud acceptance module is used for the cloud to verify the received data block and digital signature. If the verification is successful, the data block will be re-signed and uploaded to the blockchain network, and the address returned by the blockchain network will be returned Pass the user upload module, the specific method can refer to steps 104 and 105 in Example 1;
[0103] The user detection module is used for the user to verify the integrity of the cloud data, obtain the stored data from the cloud acceptance module, and the bloc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com