A virtual machine kernel dynamic detection system and method based on virtual machine introspection function level
A technology of dynamic detection and detection methods, applied in the field of cloud security, can solve the problems of attackers detecting, breaking through, and unable to apply cloud computing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
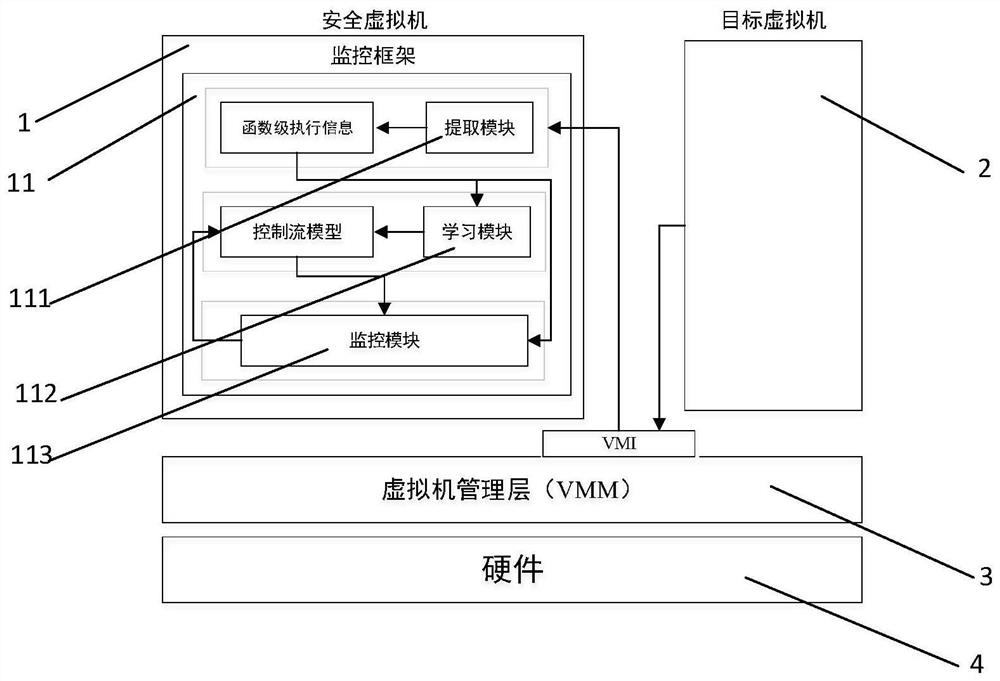
[0047] A virtual machine kernel dynamic detection system based on virtual machine introspection function level, such as figure 1 As shown, it includes a security virtual machine 1, a target virtual machine 2, a virtual machine management layer 3 and hardware 4; the hardware 4 provides a hardware 4 basis for the security virtual machine 1, the target virtual machine 2 and the virtual machine management layer 3, and the The security virtual machine 1 includes a monitoring framework 11, and the monitoring framework 11 includes an extraction module 111, a learning module 112, and a monitoring module 113; the security virtual machine 1 interacts with the target virtual machine 2 through the virtual machine management layer 3, using VMI technology, The secure virtual machine 1 controls the part to be processed in the target virtual machine 2 through the virtual machine management layer 3, and the target virtual machine 2 can also receive the target object concerned in the secure virt...
specific Embodiment approach 2
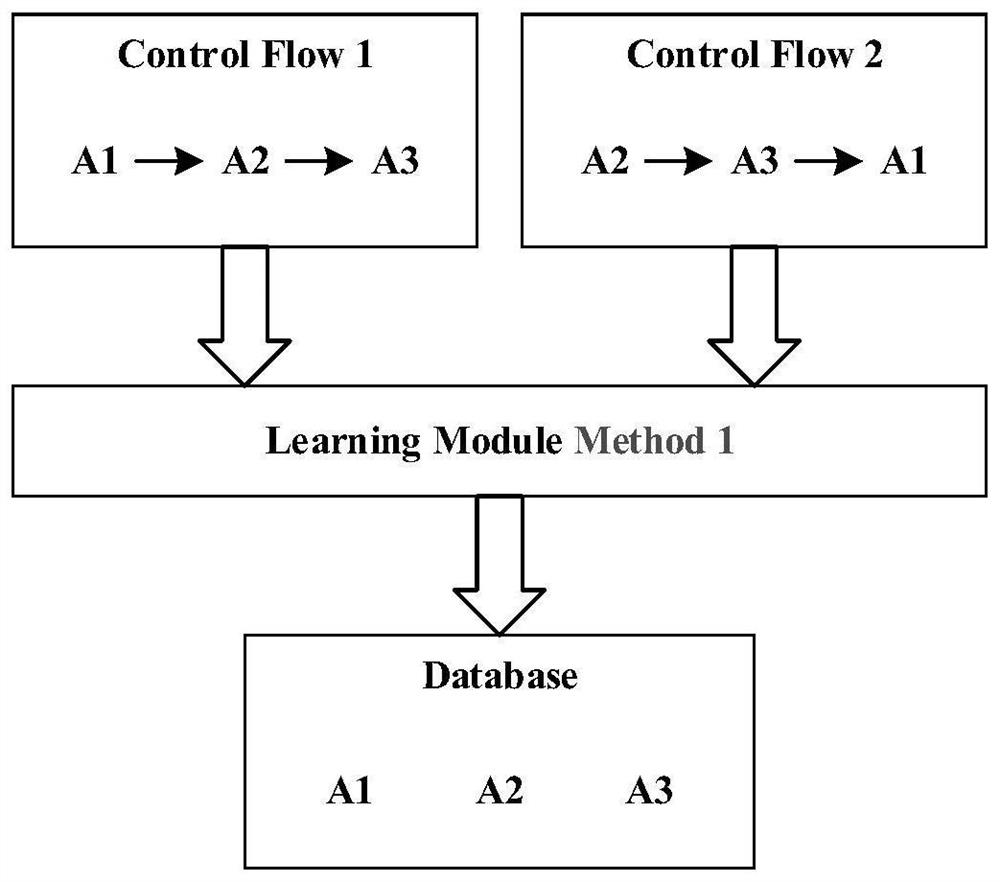
[0053] The virtual machine kernel dynamic detection method based on virtual machine introspection function level includes a dynamic tracking method assisted by static analysis. After the monitoring starts, the method first uses the method of static memory analysis to find the addresses of all sub-functions in the system calls to be tracked, and then dynamically monitors these sub-functions. If these functions are executed, the execution information is recorded, and then analysis and modeling are performed based on the captured information. Because of indirect addressing problems such as call eax, we cannot determine where this instruction will jump to next, so after a static memory analysis we cannot find all the subfunctions of the system calls used. For this reason, we also need to track such instructions, so as to know where the next step will be executed, and then perform static analysis again to obtain the address of the subsequent sub-function for monitoring. This proce...
specific Embodiment approach 3
[0088] Based on the design, we implemented a prototype system on an x86 architecture supported Intel VT server. Our system is implemented on the Xen platform. The Xen virtualization platform was developed by the University of Cambridge in the United Kingdom. It supports multiple virtualization modes and Intel VT technology, and its performance can reach a level close to that of a physical machine operating system. The main part of the implementation includes the monitoring of the start and end of the target system call, the analysis, injection and monitoring of instructions. We introduced a whitelist mechanism in the analysis process, and a context switching processing mechanism in the monitoring process.
[0089] 1. Monitor the start and end of the target system call
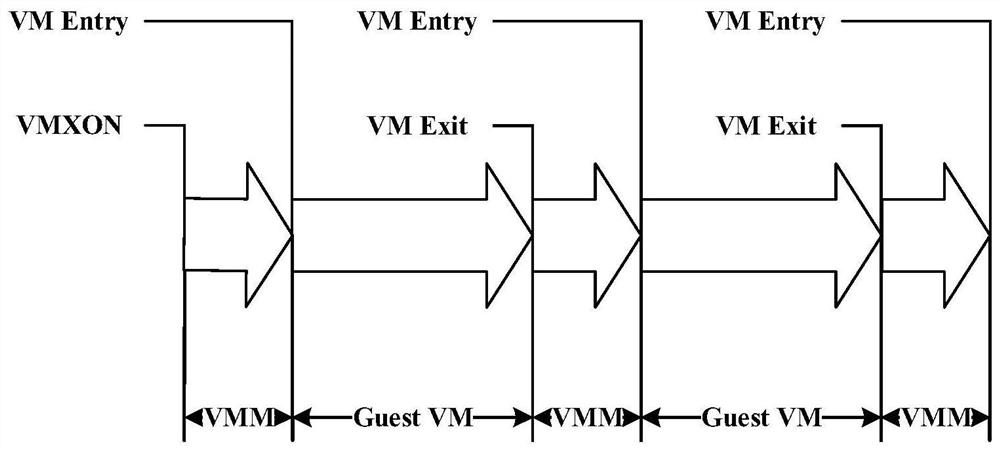
[0090] In the fast system call mechanism, entering and exiting the kernel system call from the user mode requires the assistance of the sysenter and sysexit instructions. After the sysenter instruction is exe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com