Local area network management system
A technology of management system and security management, applied in the field of LAN security management system, can solve the problems of lack, poor usability, lack of peripheral management mechanism, etc., and achieve the effect of normal operation and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The present invention will be further described below in conjunction with the accompanying drawings.
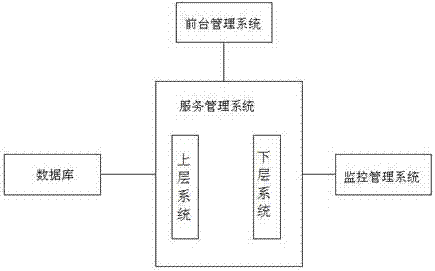
[0019] Such as figure 1 As shown, a local area network security management system includes a front desk management system, a database, a service management system and a monitoring management system, and the front desk management system, the database and the monitoring management system are respectively connected to the service management system;
[0020] The foreground management system provides services for users in the form of WEB services, receives management requests sent by the management browser, and interacts with the application service system;
[0021] The database is used to store parameter information required for system operation, various index information and configuration information of network equipment, user management information, log information and other information related to system operation;
[0022] The service management system includes an uppe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com