Physical layer secure wireless relay communication method based on game theory
A physical layer security and wireless relay technology, applied in wireless communication, security devices, sustainable communication technology, etc., can solve the problems of high encryption algorithm complexity, expensive key management, brute force cracking, etc., to solve the problem of anti-eavesdropping , Improve security capacity, reduce the effect of eavesdropping probability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
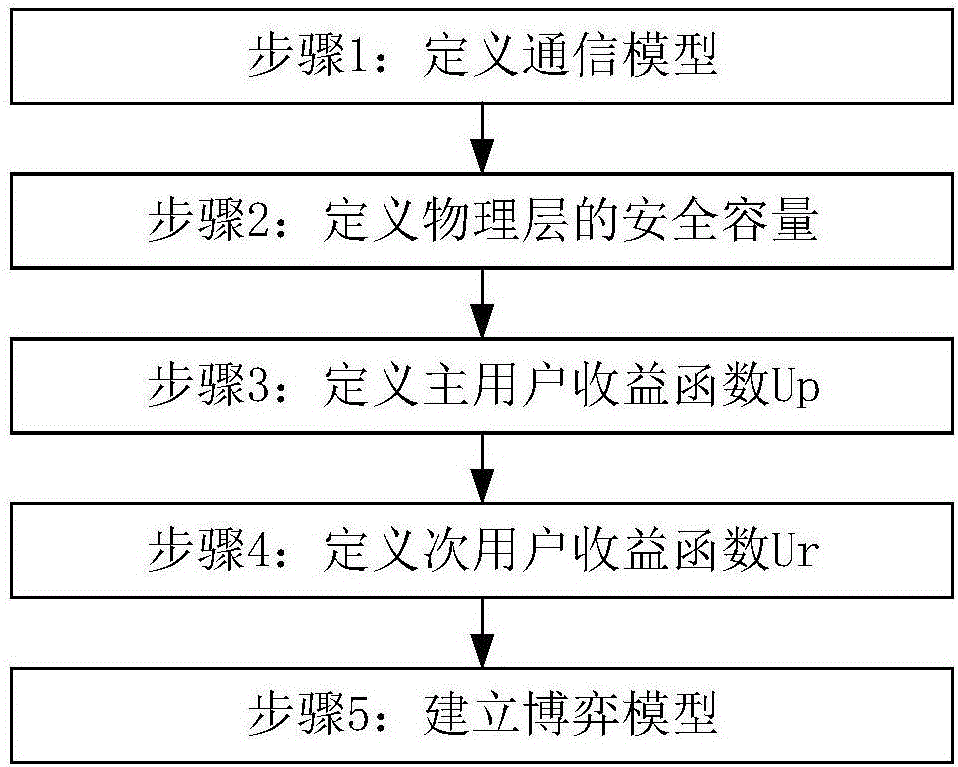
[0036] Such as Figure 1-5 As shown in one of them, the present invention discloses a wireless relay communication method based on game theory physical layer security, which includes the following steps:
[0037] Step 1. Define the communication model:
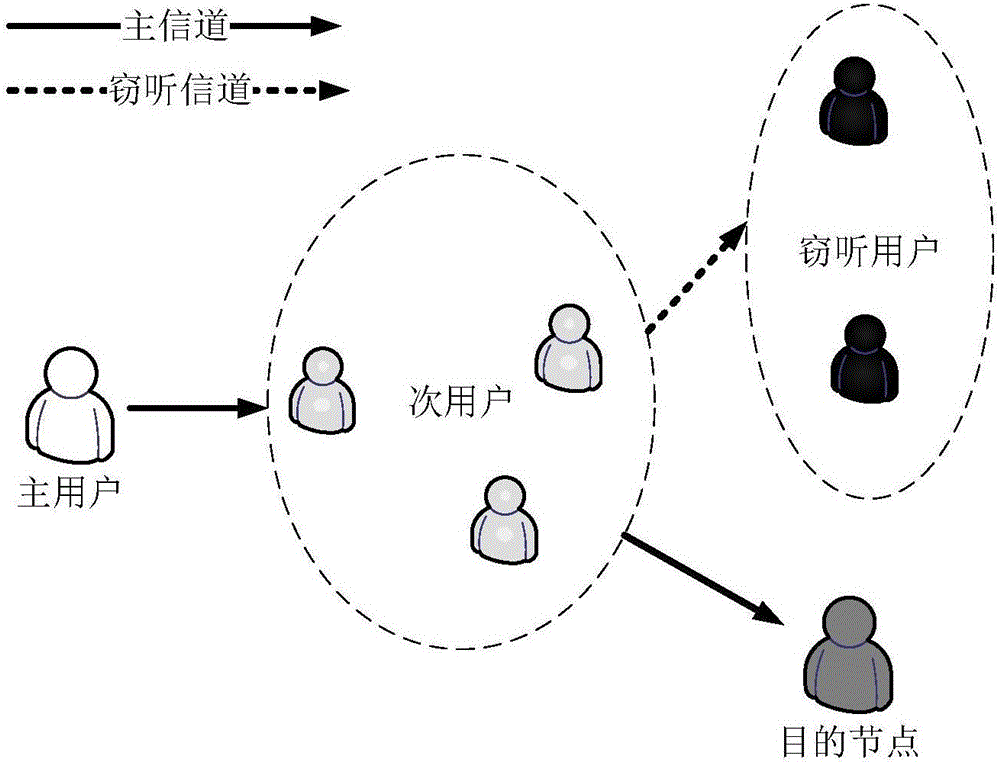
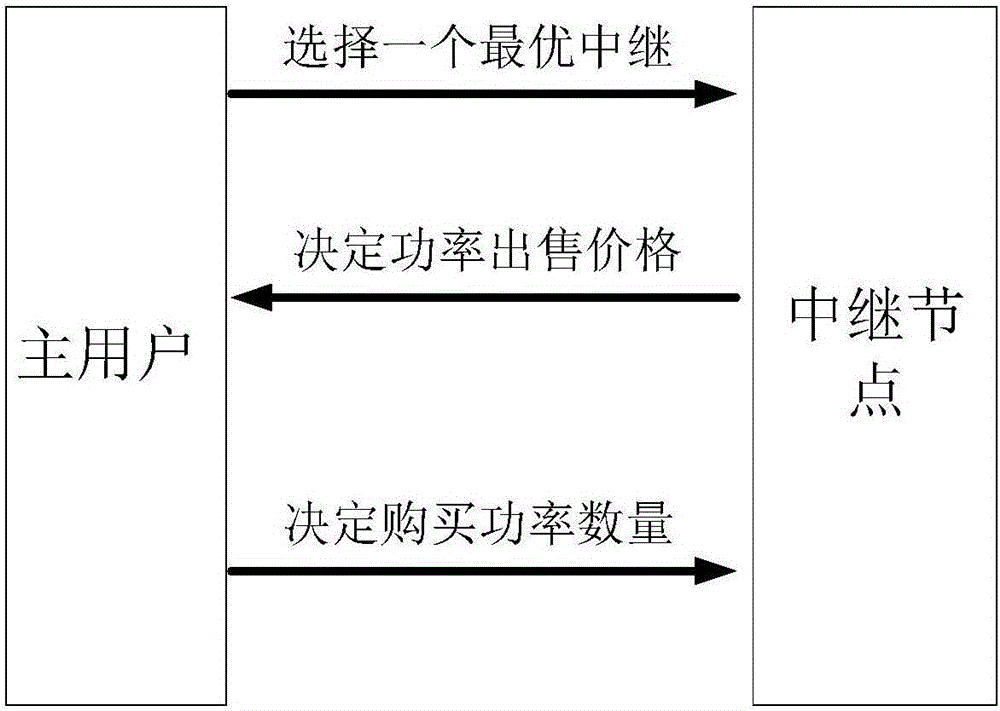
[0038] Such as figure 2 As shown, set a primary user that needs other users to communicate cooperatively, the primary user is the source node; multiple secondary users that can carry out cooperative communication, multiple secondary users are relay nodes; multiple eavesdropping data packets transmitted by secondary users The eavesdropping user; more than one destination node receiving the data packet; the source node sends the data packet to the relay node through the main channel with power P, the relay node sends the data packet to the destination node through the main channel with power O, and the eavesdropping user uses power O eavesdrops on the data packets forwarded by the secondary user through the eavesdropping chan...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com