Multi-channel active type network identity verification system and network identity verification device
A network identity and verification device technology, applied in transmission systems, security devices, wireless communications, etc., can solve the problems of tampering with network transactions, users' money losses, and the inability to effectively verify the authenticity of network users' identities and network transaction security. Strengthening correctness and reliability, improving non-repudiation and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
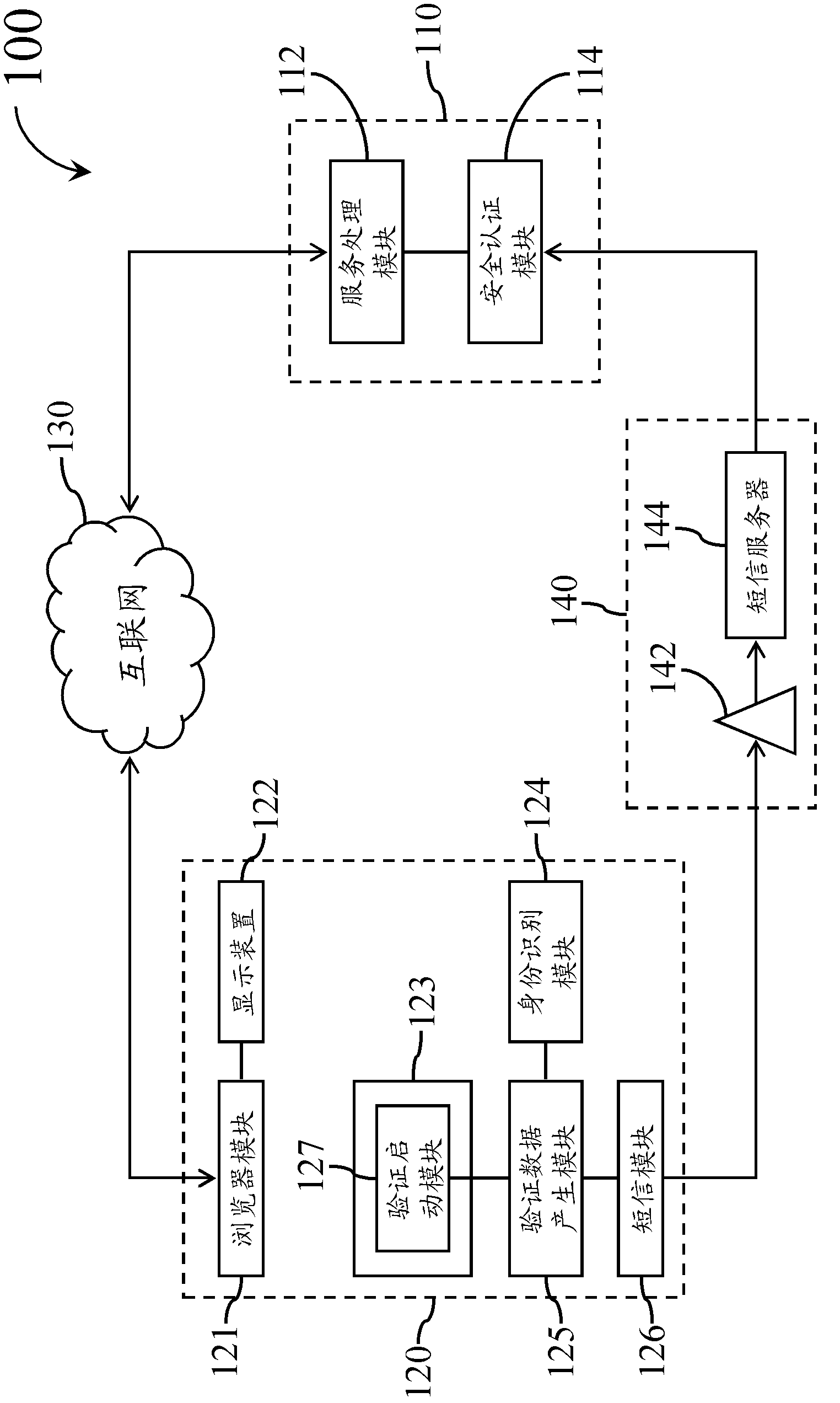
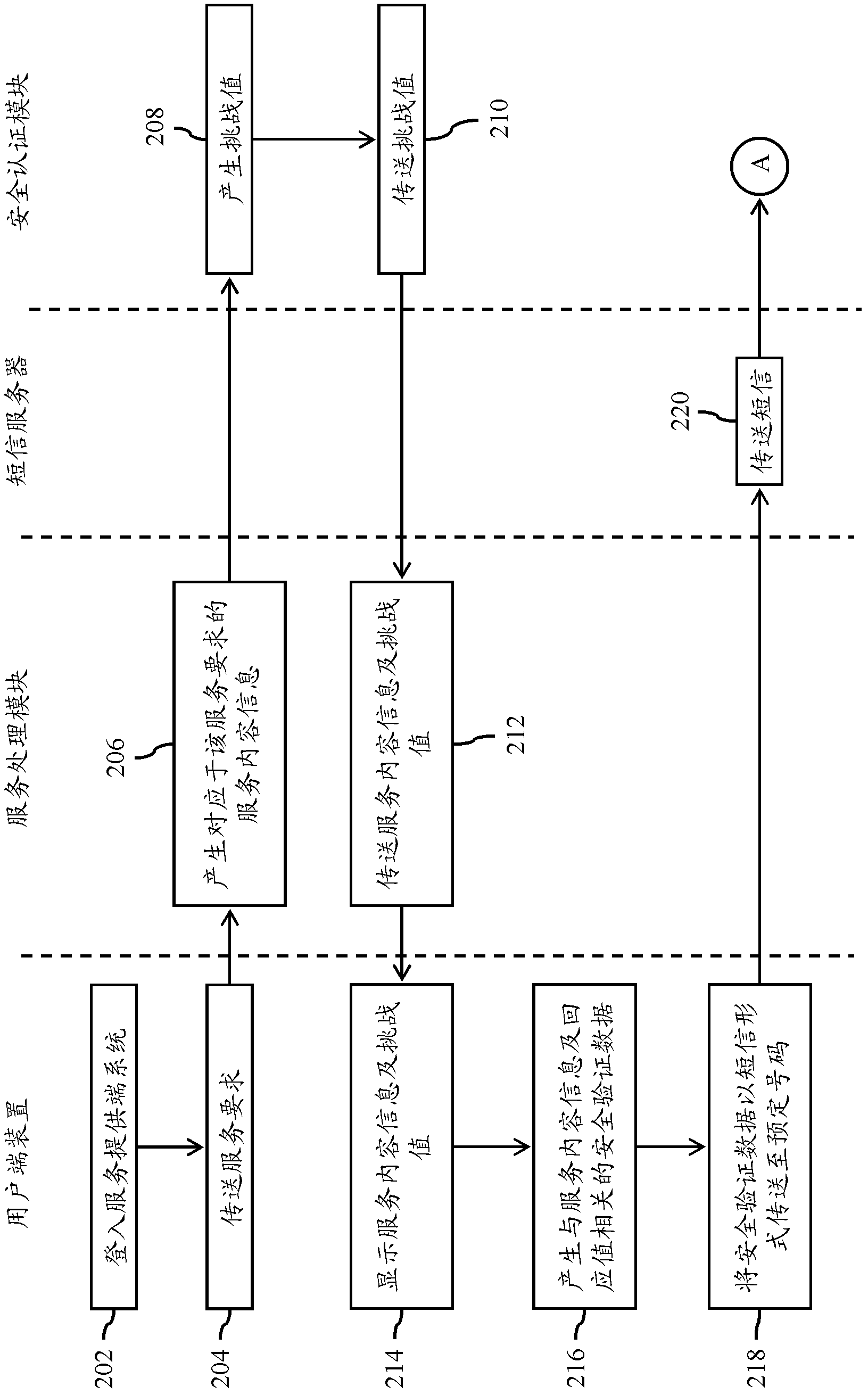
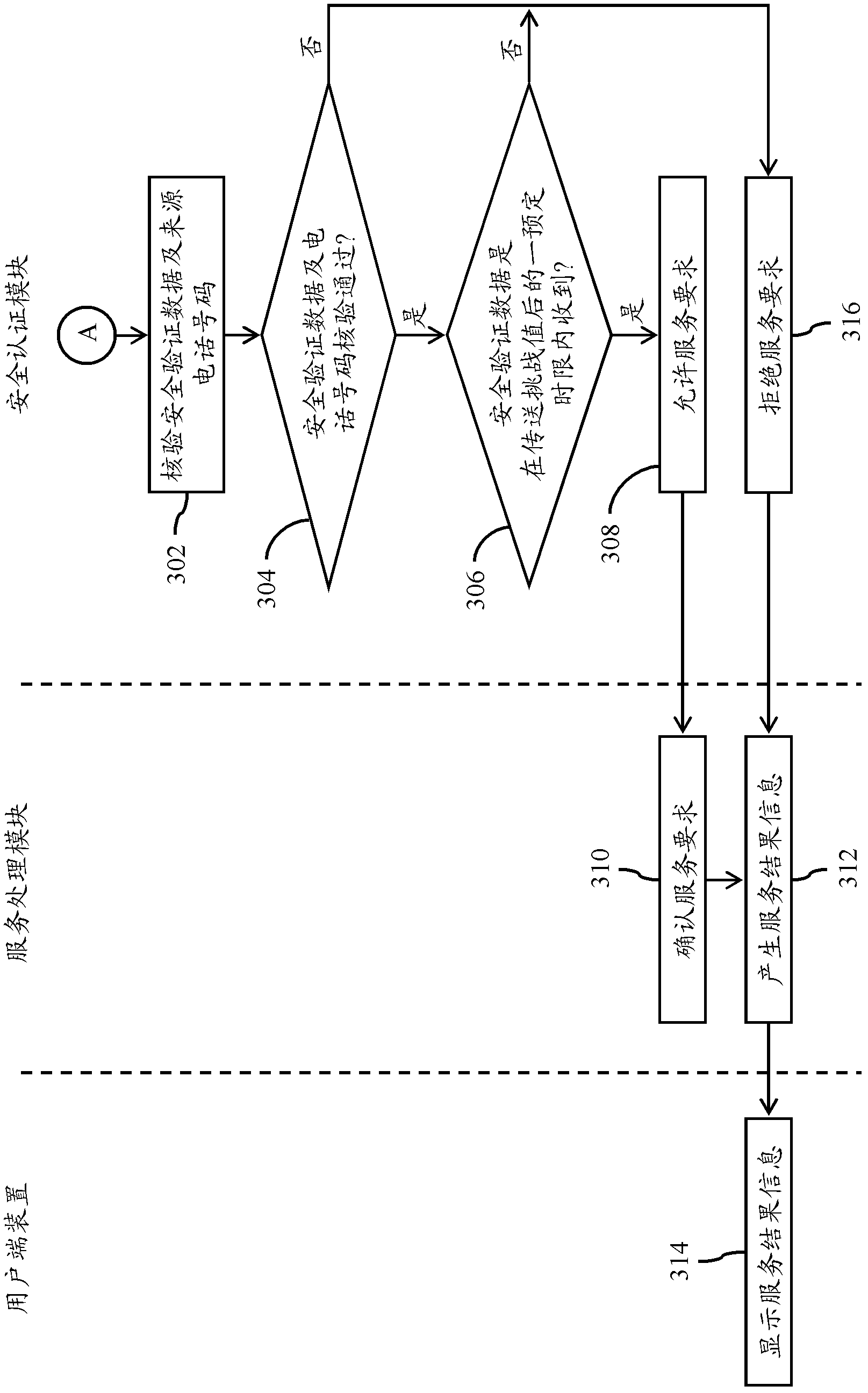
[0022] Embodiments of the present invention will be described below in conjunction with related drawings. In these drawings, the same reference numerals represent the same or similar elements or processes / steps.
[0023] Certain terms are used in the specification and following claims to refer to particular elements. It should be understood by those skilled in the art that the same element may be referred to by different names. This description and the subsequent claims do not use the difference in name as the way to distinguish components, but the difference in function of the components as the basis for distinction. "Includes" mentioned throughout the specification and subsequent claims is an open-ended term, so it should be interpreted as "including but not limited to...".
[0024] The description of "and / or" used herein includes any combination of one or more of the listed items. In addition, unless otherwise specified in this specification, any singular term also inclu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com