Network authentication service system and method
A network authentication and service method technology, applied in the field of network authentication service system, can solve the problems of not being able to guarantee that information will not be stolen, violating Web services, and not being able to guarantee the security of Web services, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
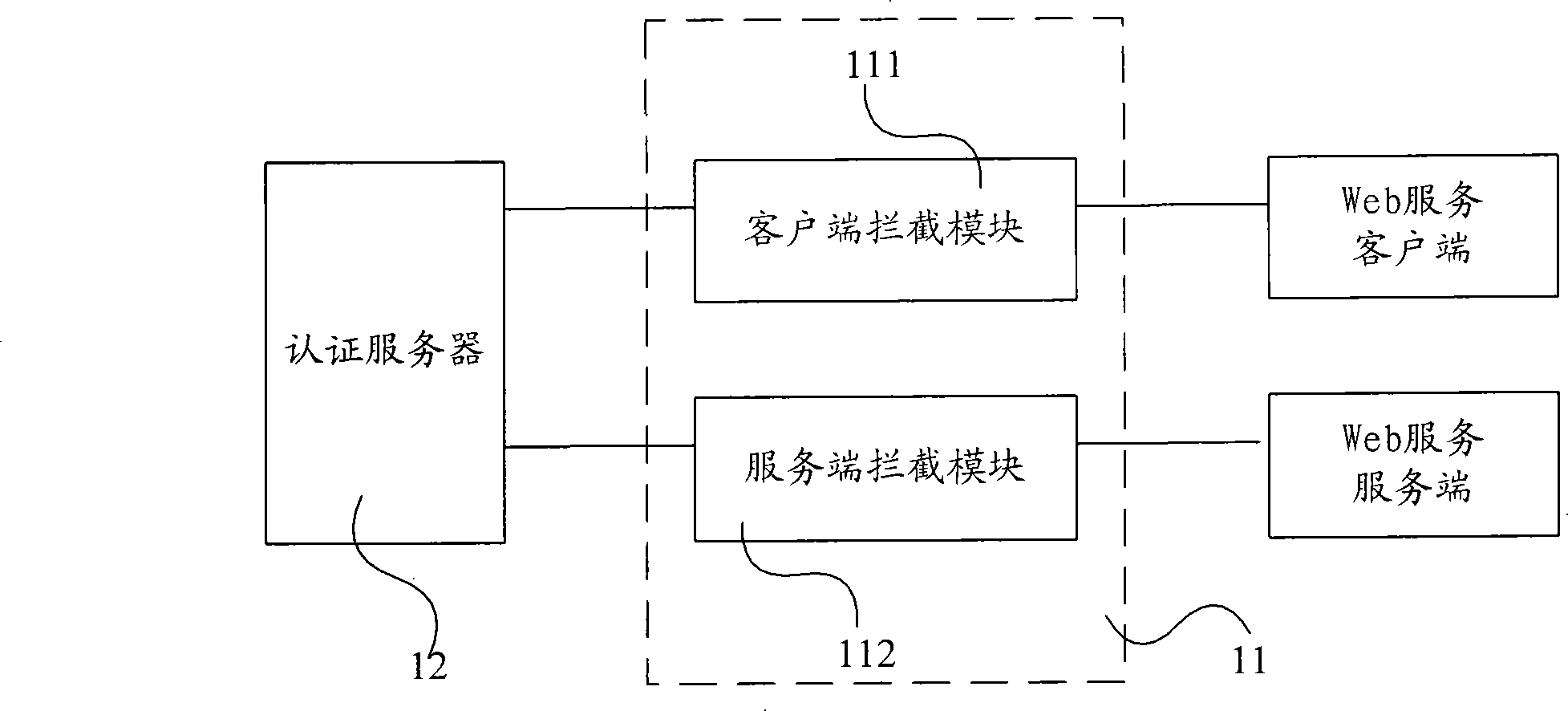
[0028] Figure 5 It is a flow chart of Embodiment 1 of the network authentication service method of the present invention. This embodiment includes: intercepting messages exchanged by the application layer, and performing authentication processing on the intercepted messages, specifically including:
[0029] Step 51: the Web service security device (for example, the client sends an intercepting module) intercepts the request message sent by the Web service client;
[0030] Step 52: The Web service security device (for example, the client sends an intercepting module) encrypts the request message (for example, applies for an authentication code from the authentication server and matches the authentication code to the request message) to obtain an encrypted message , and send the encrypted message to the Web service server;
[0031]Step 53: Web service safety device (for example, server receiving interception module) receives encrypted message (in actual application, encrypted ...
Embodiment 2
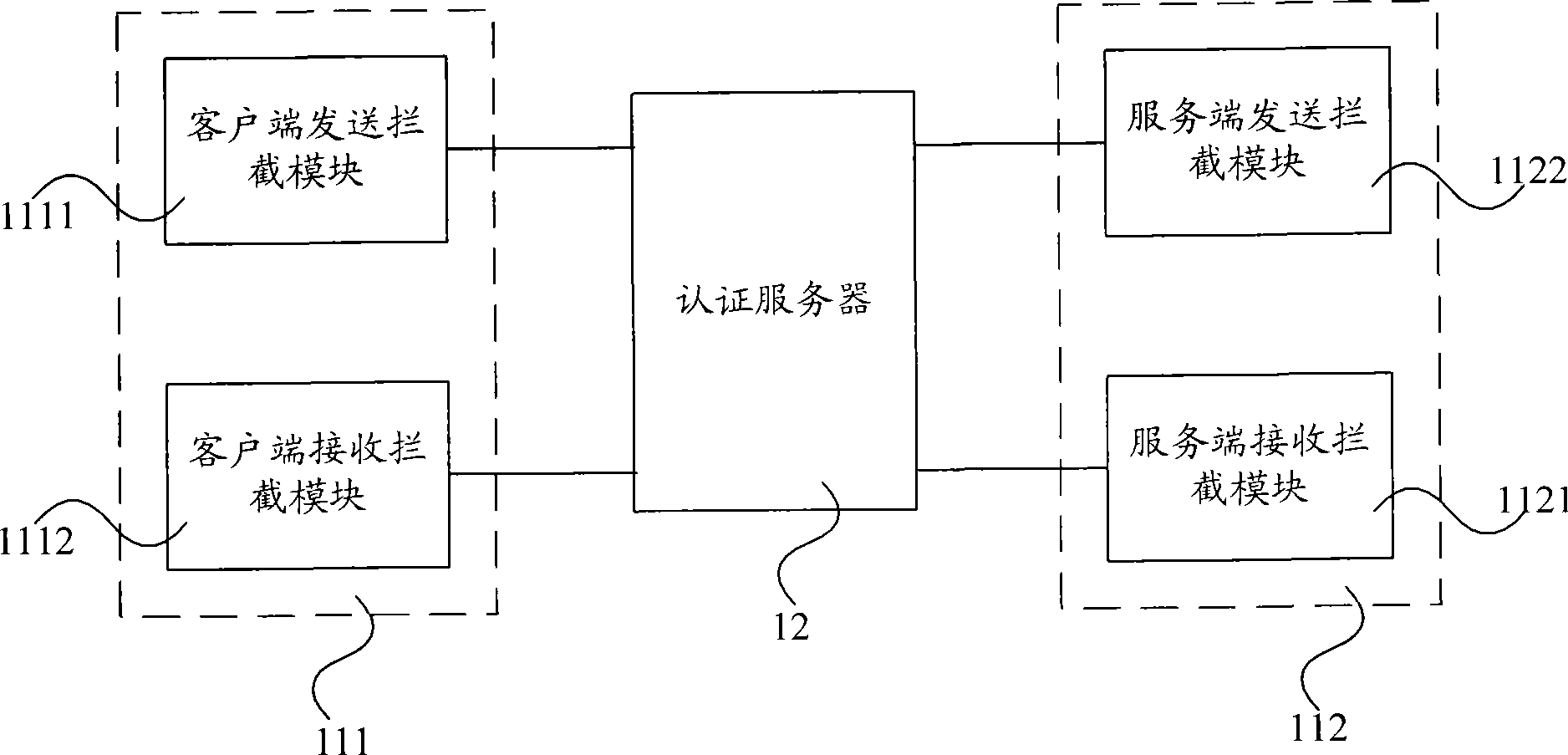
[0034] Image 6 It is a flowchart of Embodiment 2 of the network authentication service method of the present invention, and this embodiment includes:
[0035] Step 60: The Web service client sends a SOAP request message.
[0036] Step 61: The client sends the interception module (client OutHandler) to intercept the received request message. According to the regulations of WS-Security, the request message includes a message body and a message header, and the message header includes information such as a user account configured by the client. Interception can be implemented on the Web service client through configuration, such as by registering the OutHandler service in the Web service. When the Web service client sends a SOAP request message to the Web service server, the client OutHandler will implement interception according to the configuration file. this request message. The OutHandler service pre-processes the SOAP request message sent by the client, adds WS-Security i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com