Data transaction processing method and apparatus
A transaction processing and data technology, applied in the field of data security, can solve the hidden problems of identity authentication and transaction data interaction security, and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
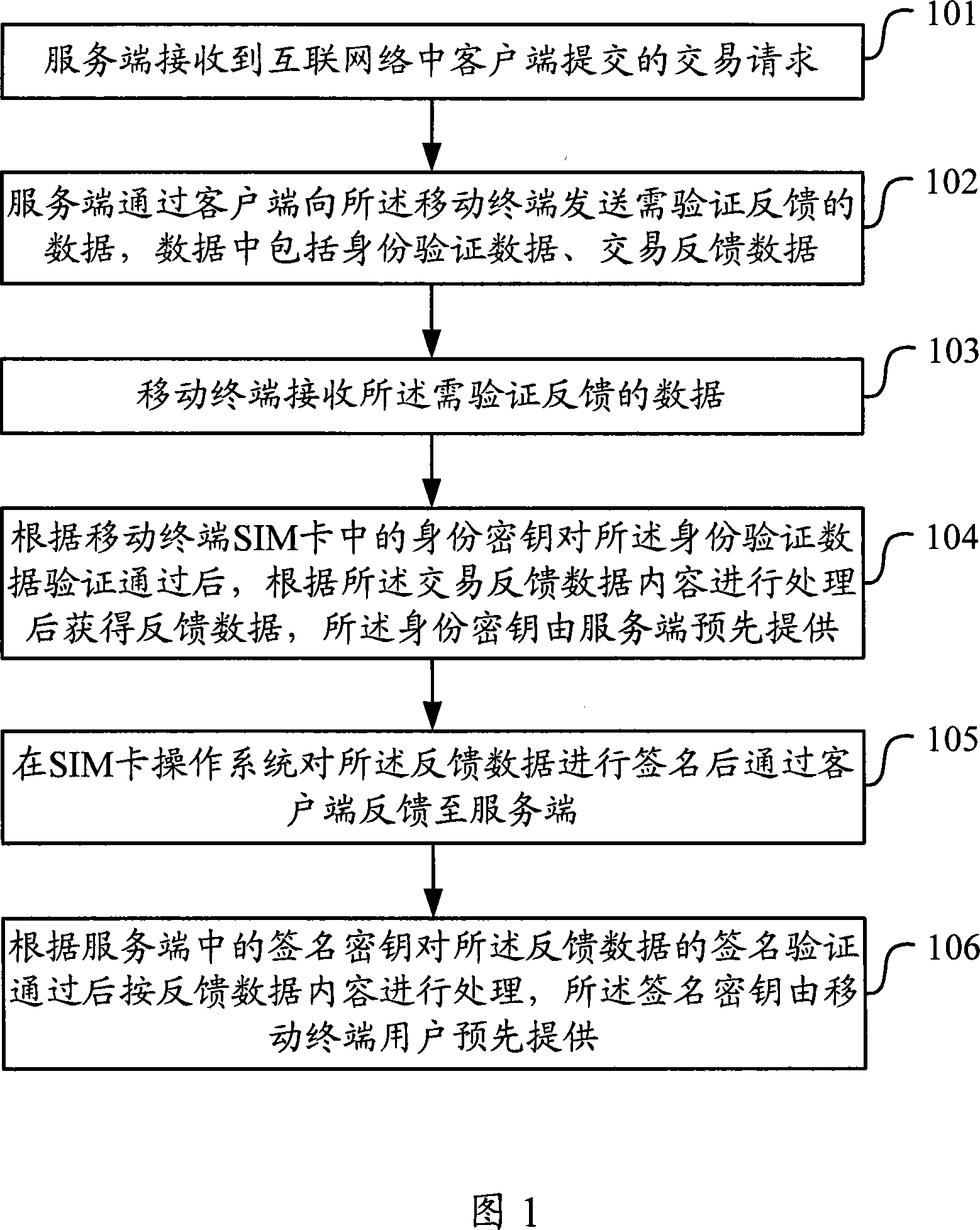
[0111] Figure 7 is a schematic diagram of the implementation process of data transaction processing in Embodiment 1. In this embodiment, the client sends a network transaction command to the mobile terminal to request a security operation. As shown in the figure, the specific transaction authentication may include the following steps:
[0112] Step 701, the user logs in and determines the transaction content.
[0113] The user logs into the client program, enters the network transaction interface of the network transaction service provider, selects the specific content of the network transaction, and inputs transaction-related information.
[0114] Step 702, the client program invokes the RPC program to start the data processing program of the mobile terminal.
[0115] The client program invokes the RPC program, connects with the mobile terminal through the interface module, starts the mobile terminal processing program, and passes in authentication data.
[0116] Step 703 , ...
Embodiment 2
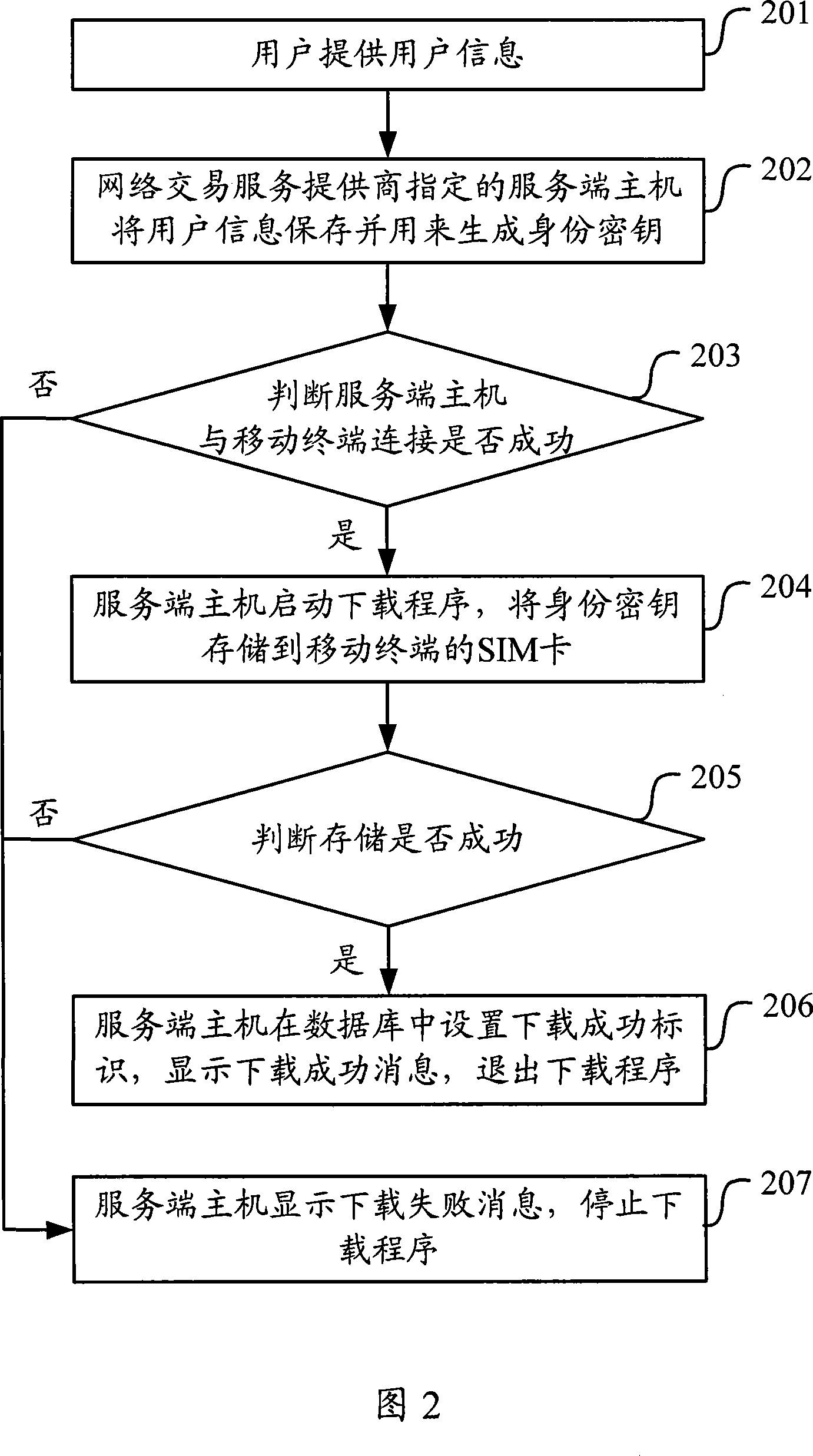
[0130] In the network transaction environment, assume that the client user wants to transfer 500 yuan from his bank account to the bank account designated by the power supply bureau through online banking to complete the payment of the current month's electricity fee. It can be achieved by the following steps:
[0131] First, the user logs into the online banking service on the client terminal, and after completing traditional identity authentication such as password verification, the user sends an application for transferring 500 yuan.
[0132] Then, the client uploads the user's application to the online banking server, and the online banking server generates the key data of the online transaction according to the application sent by the user, and sends these key data back to the client, requiring the user to perform a check on the key data. Digital signature confirmation.
[0133] Thirdly, the client sends the user's mobile terminal a secure operation command to digitally ...
Embodiment 3
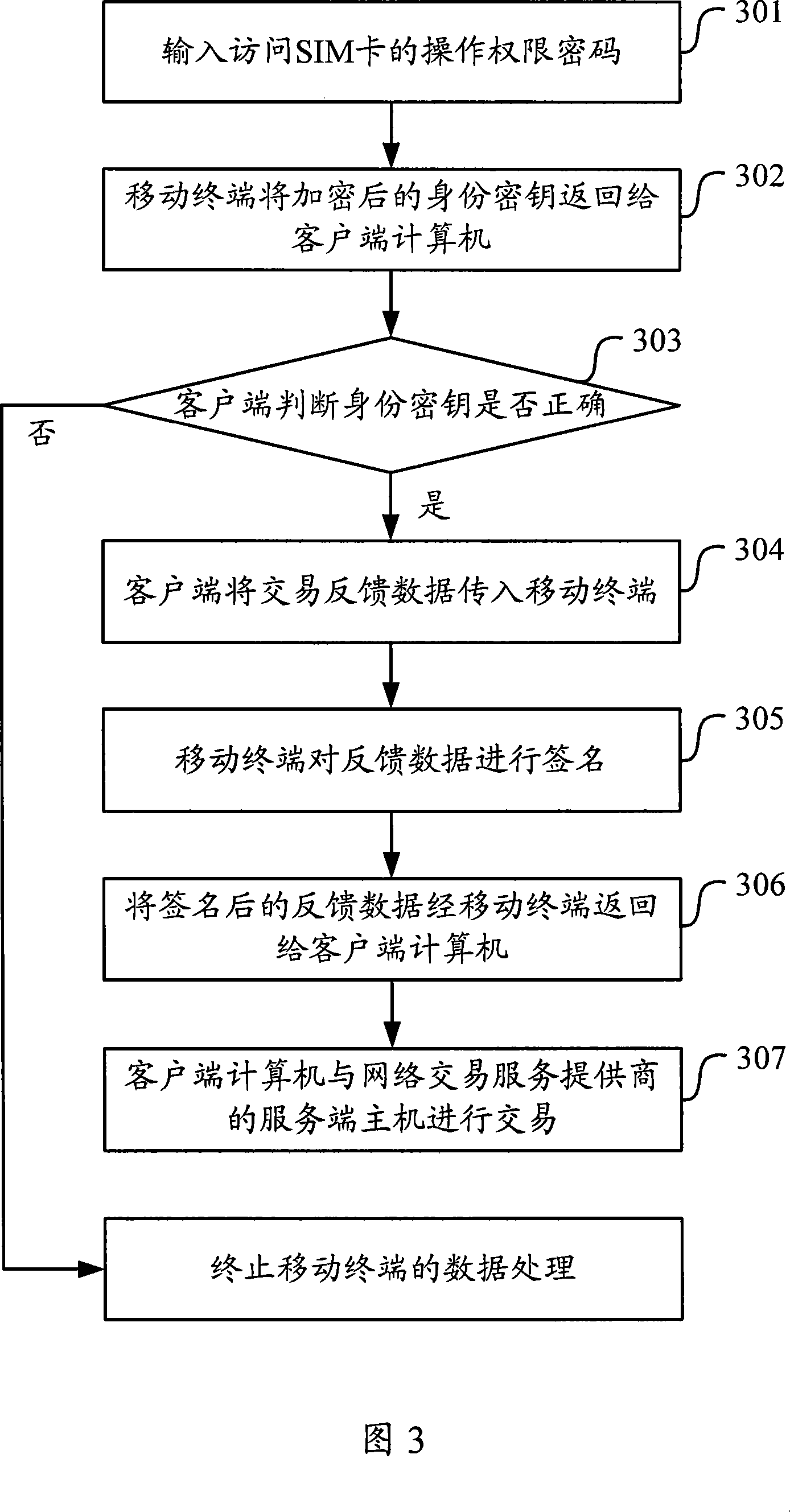
[0137] With the enhancement of the network functions of mobile terminals, mobile terminals have become a network terminal that can replace PCs. The SIM card is encrypted and signed. It can be achieved by the following steps:
[0138] First, the user runs the online shopping mall application in the mobile terminal, logs into the online shopping mall through the GPRS (General Packet Radio Service) network, and establishes a TCP (Transmission Control Protocol, Transmission Control Protocol) connection with the shopping mall server. Commodity information is transmitted between the online mall and the mobile terminal for the mobile terminal user to browse, and the user selects the commodity to be purchased and puts it into the shopping cart.
[0139] Secondly, when the product selection is completed, the mobile terminal sends the shopping list in the shopping cart and the local IMSI number to the online mall server; after the online mall server receives the shopping list, it recor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com