Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
58results about "Circuits to prevent unauthorised copying/reproduction" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
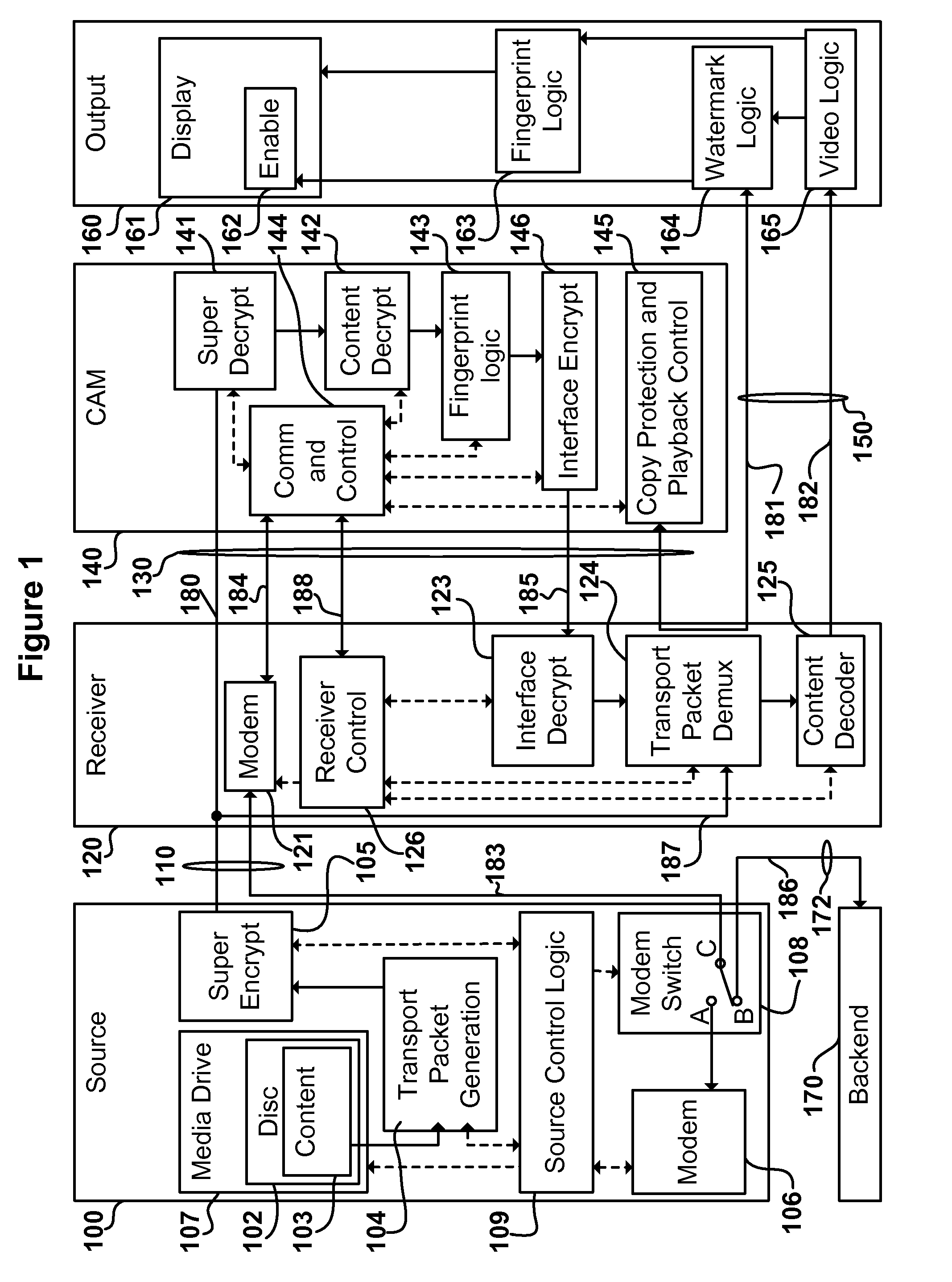
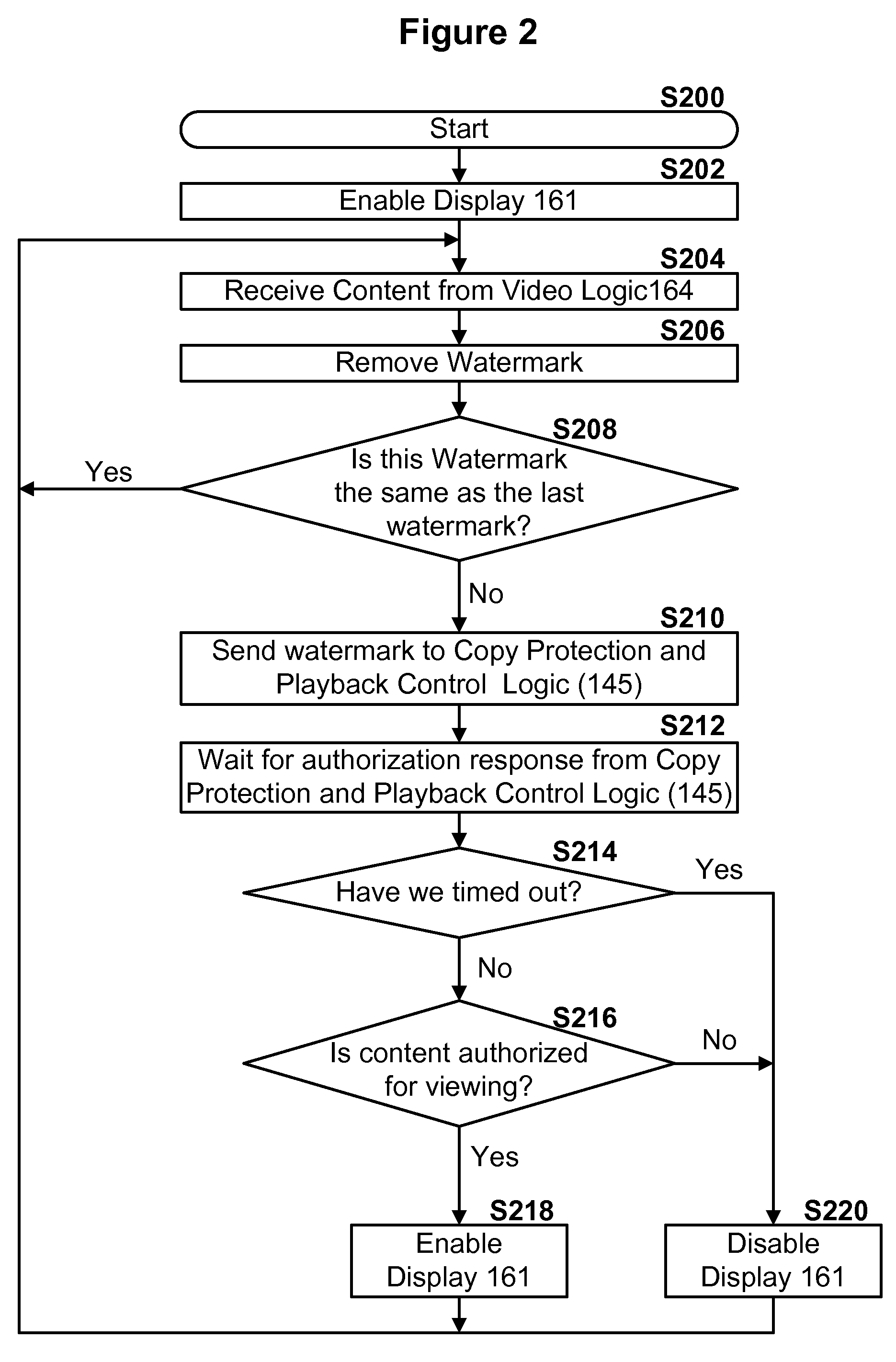
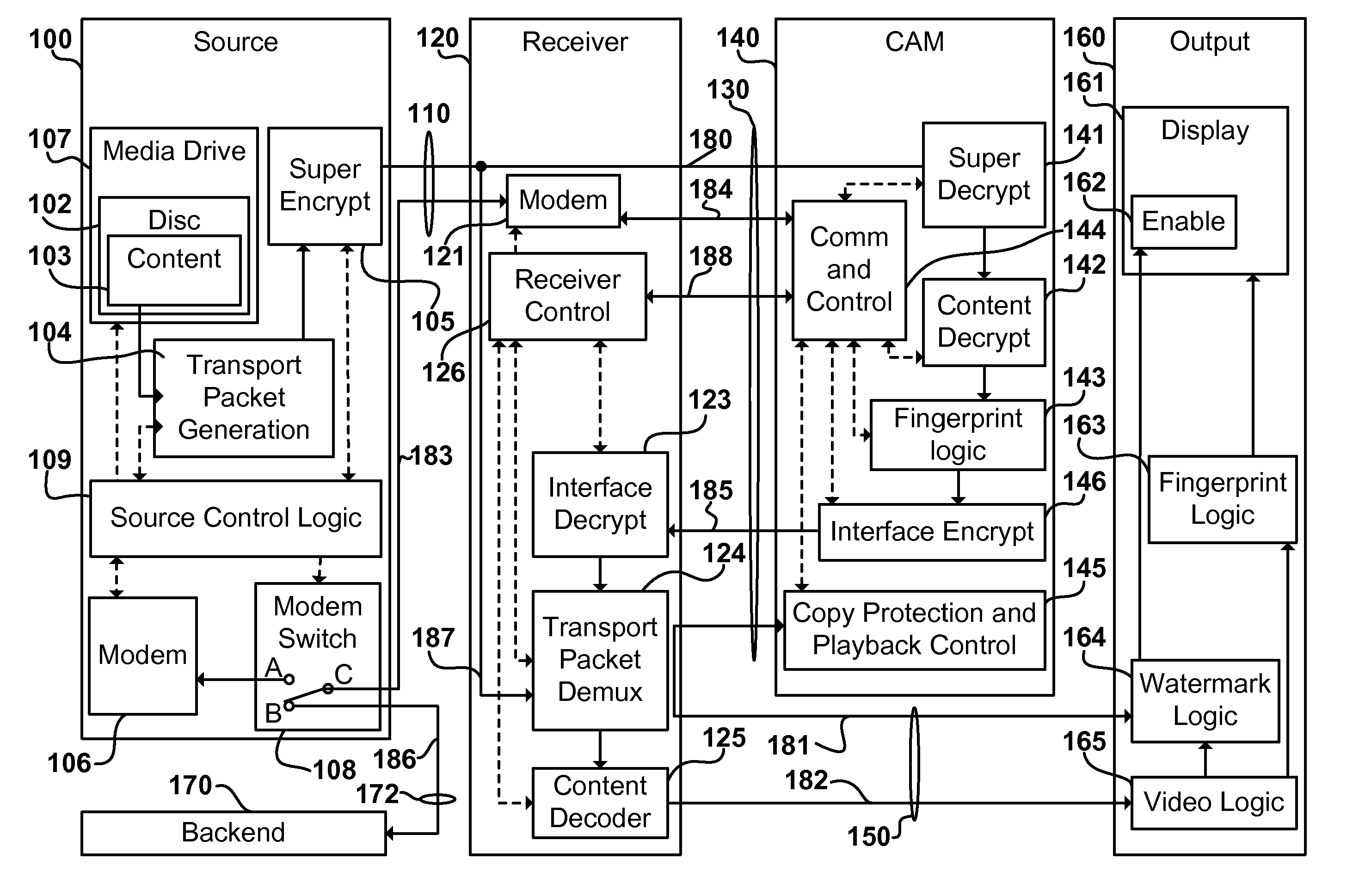
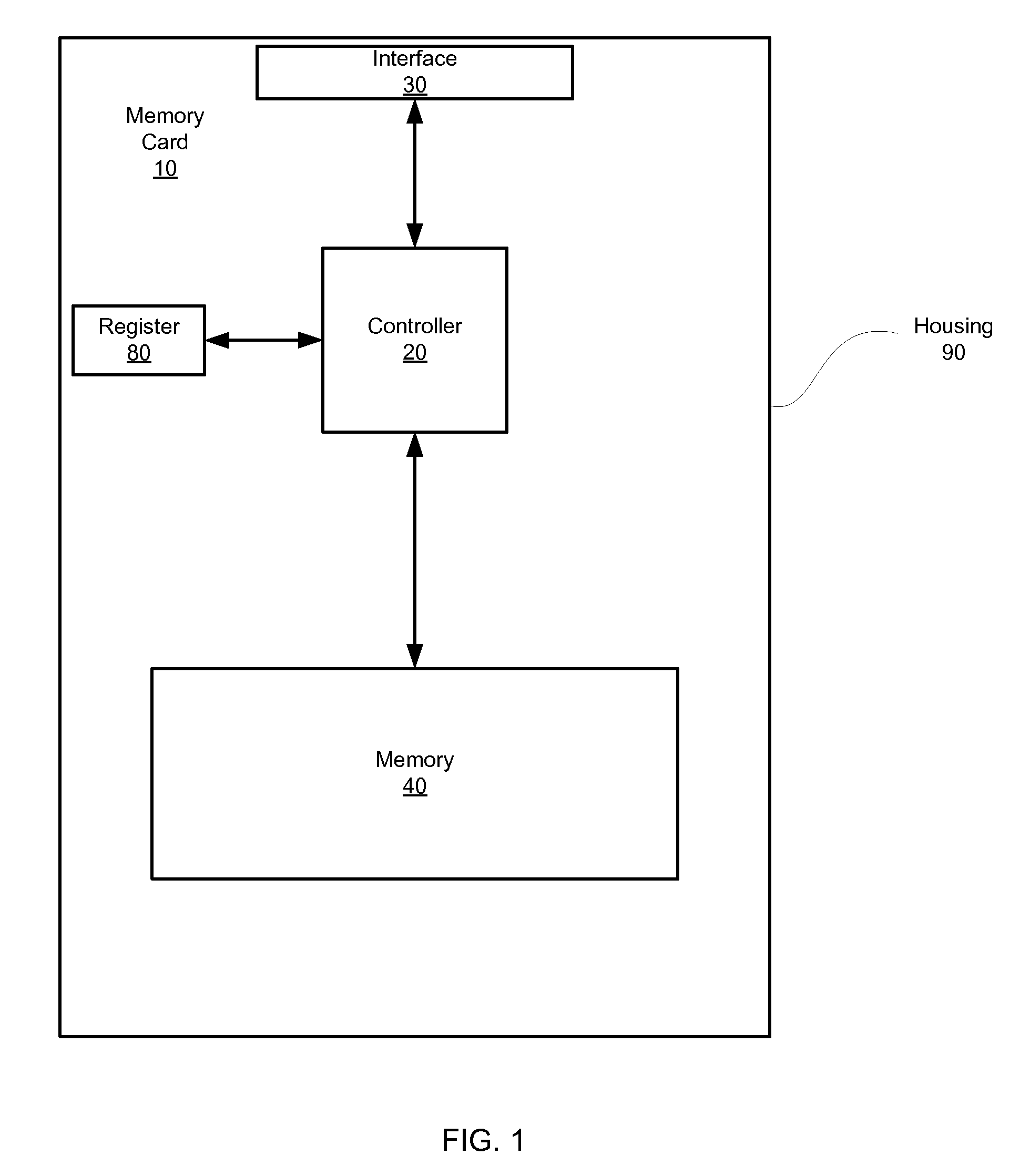
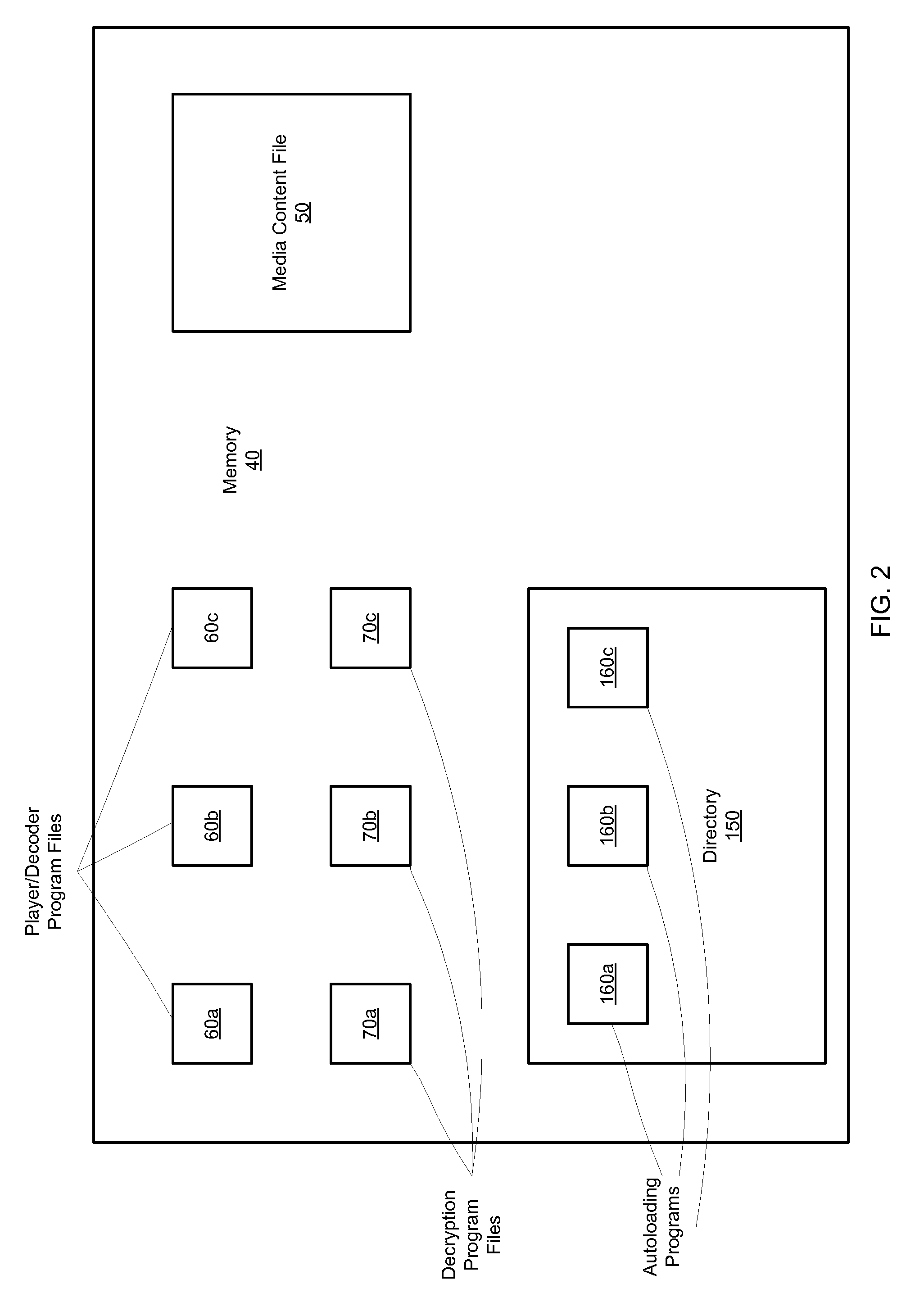
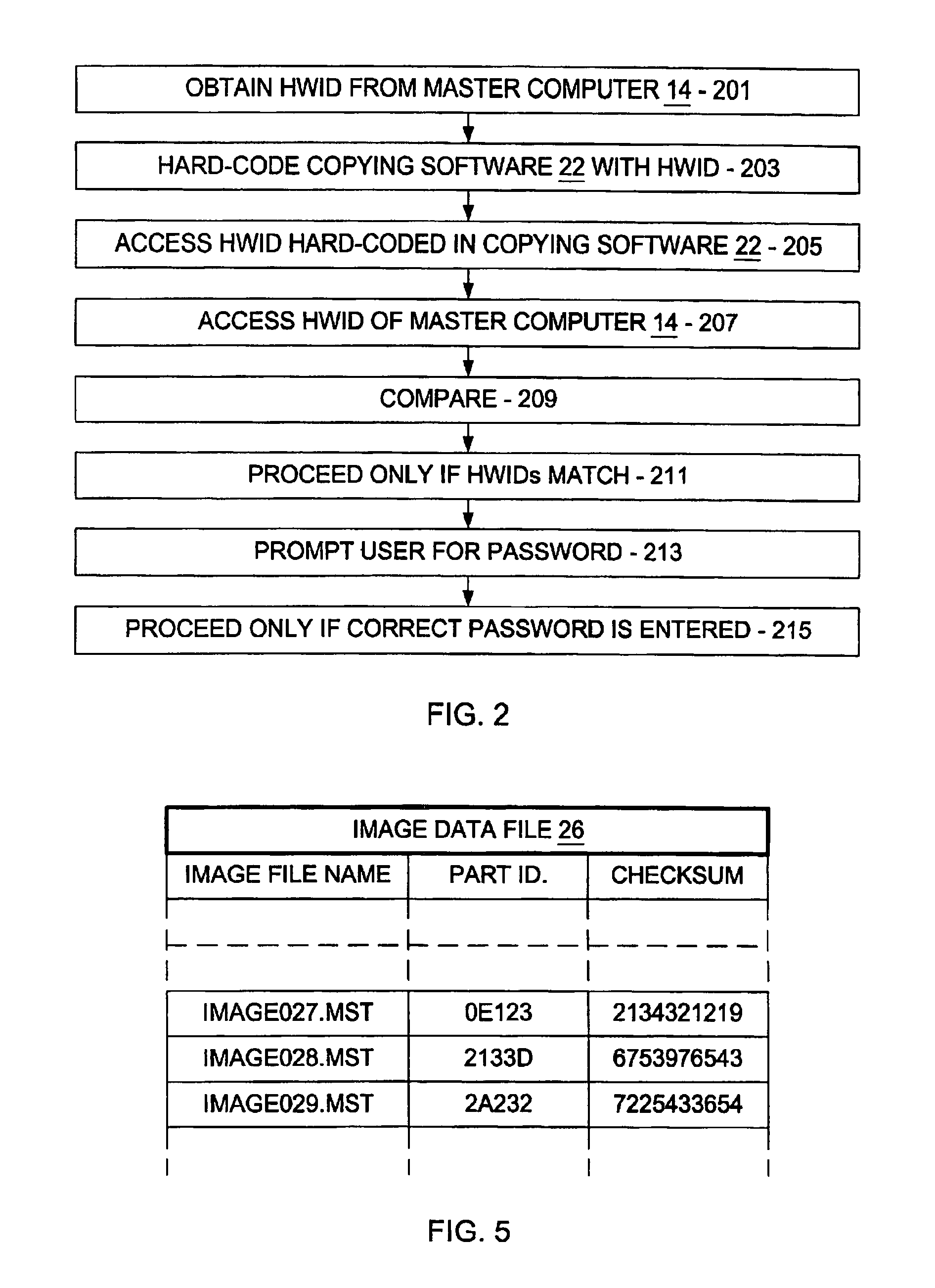
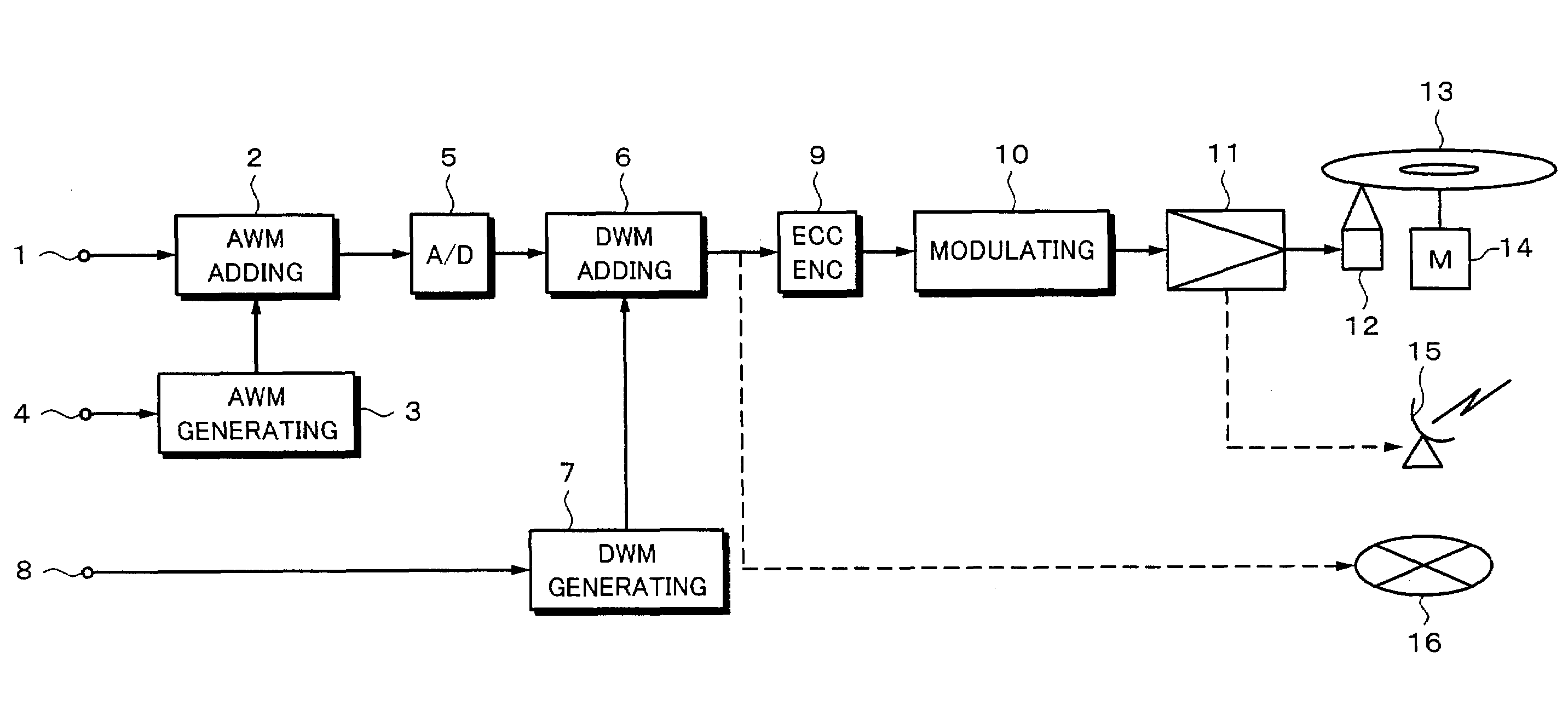
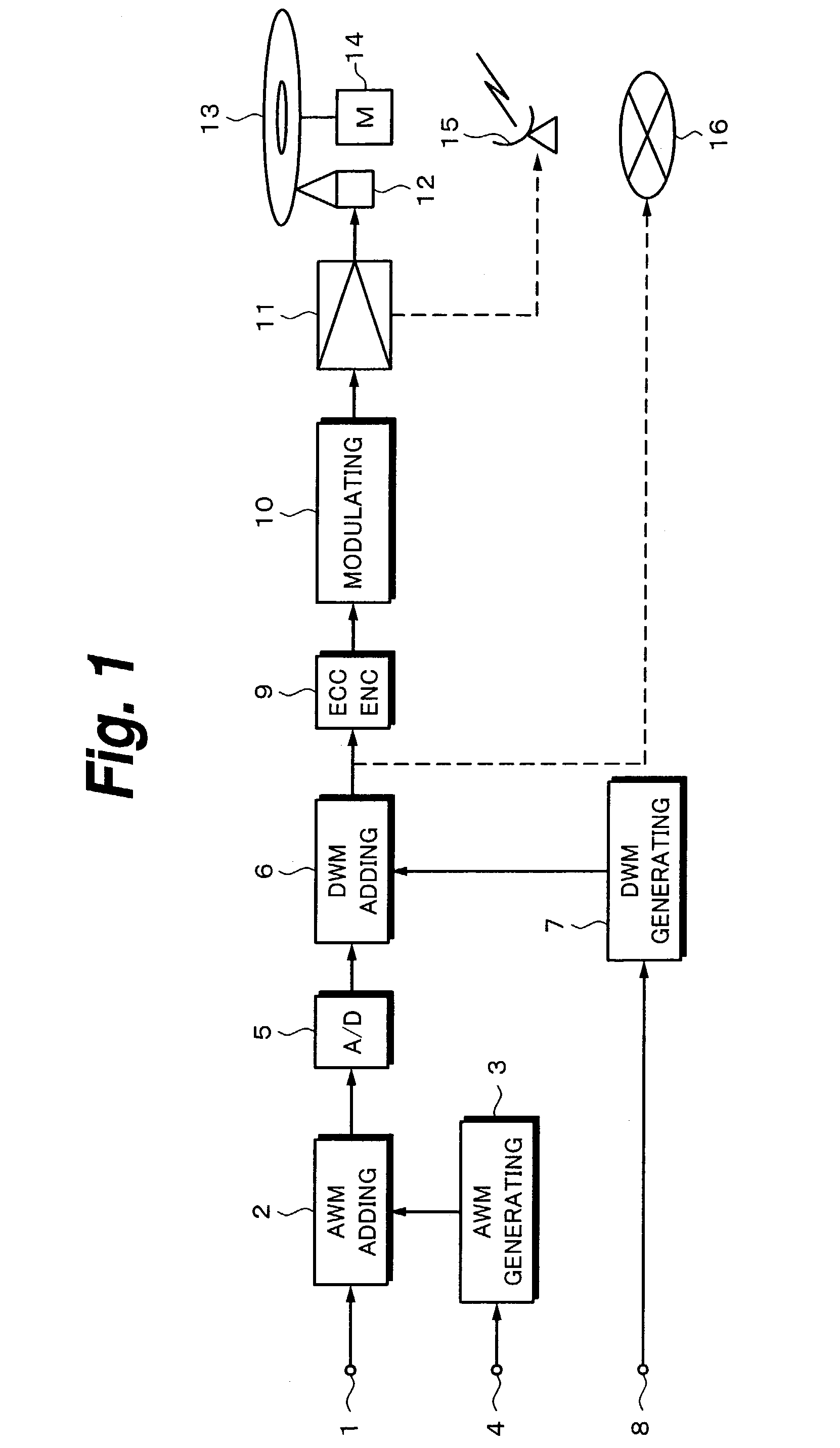
Digital content distribution system and method
InactiveUS7162642B2Prevent unauthorized accessObtaining unauthorized accessDigital data processing detailsUser identity/authority verificationContent distributionDigital content
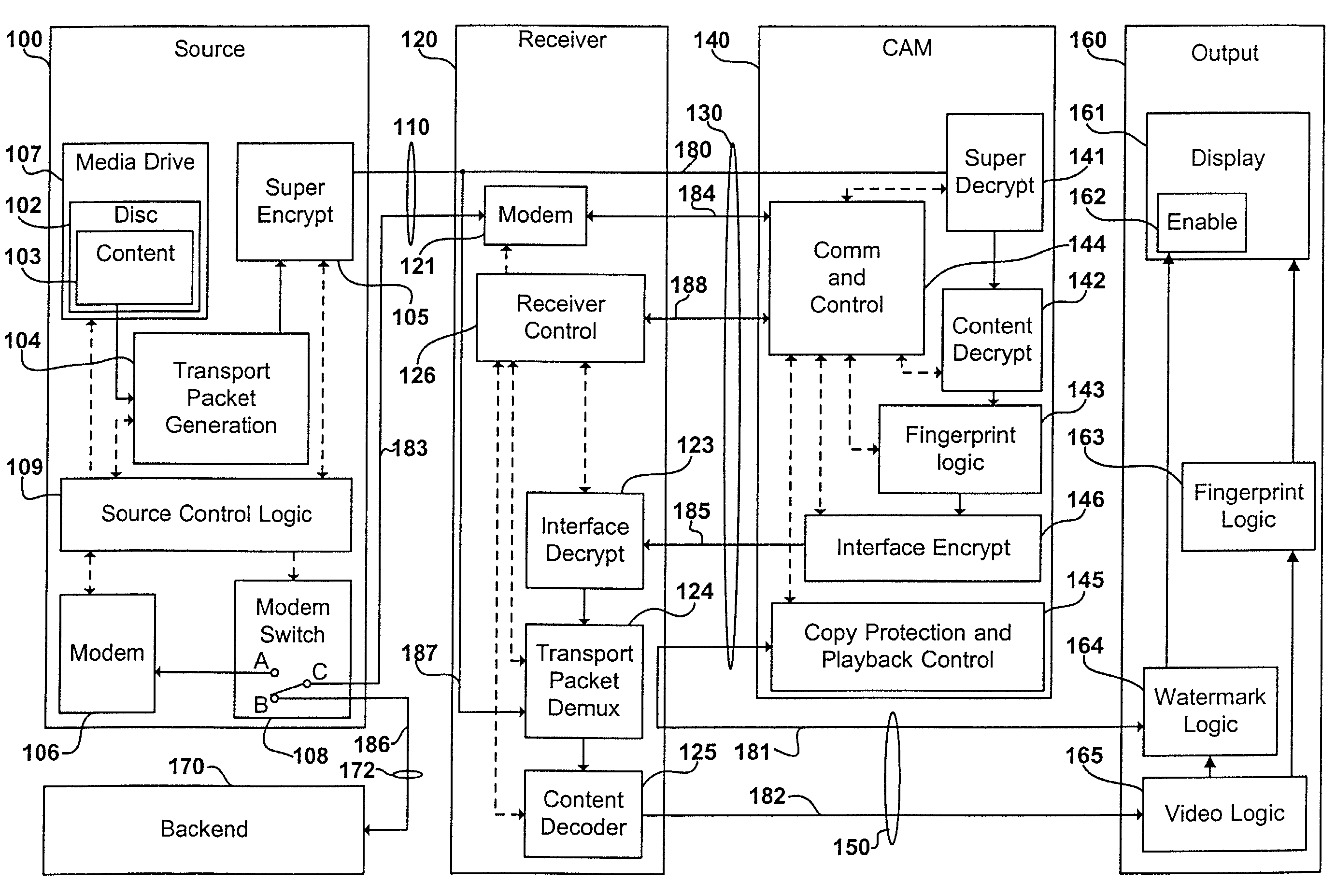
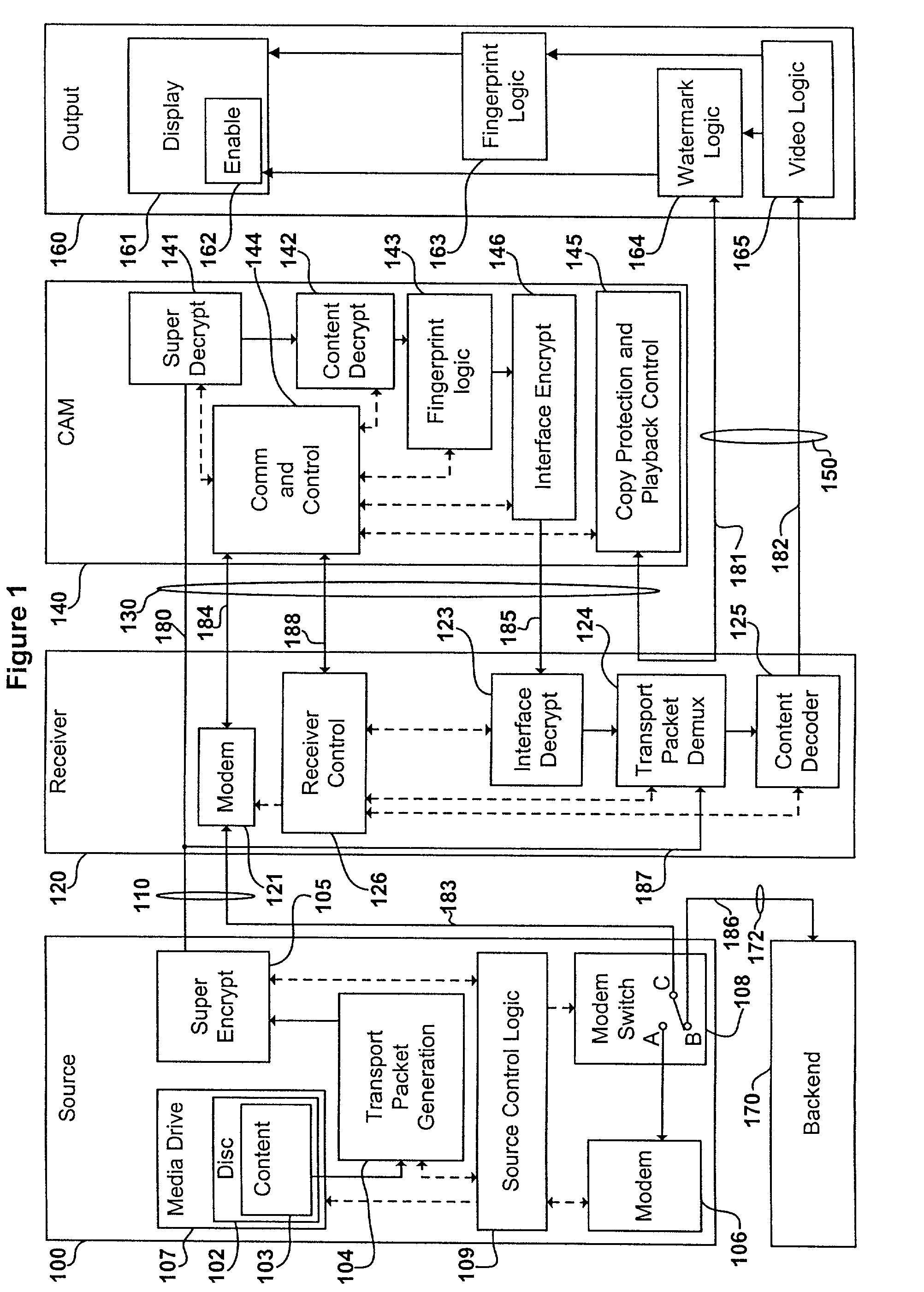
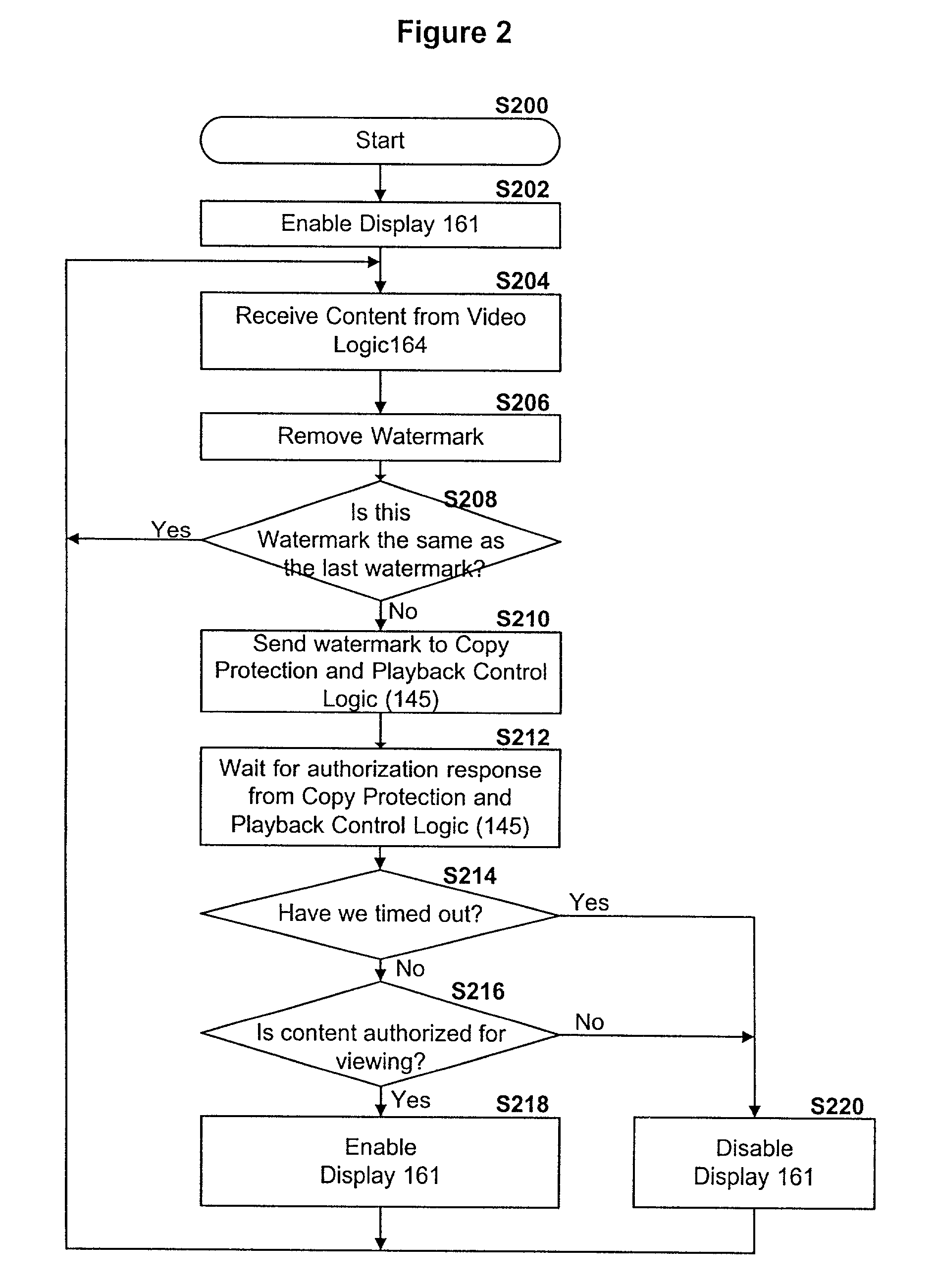
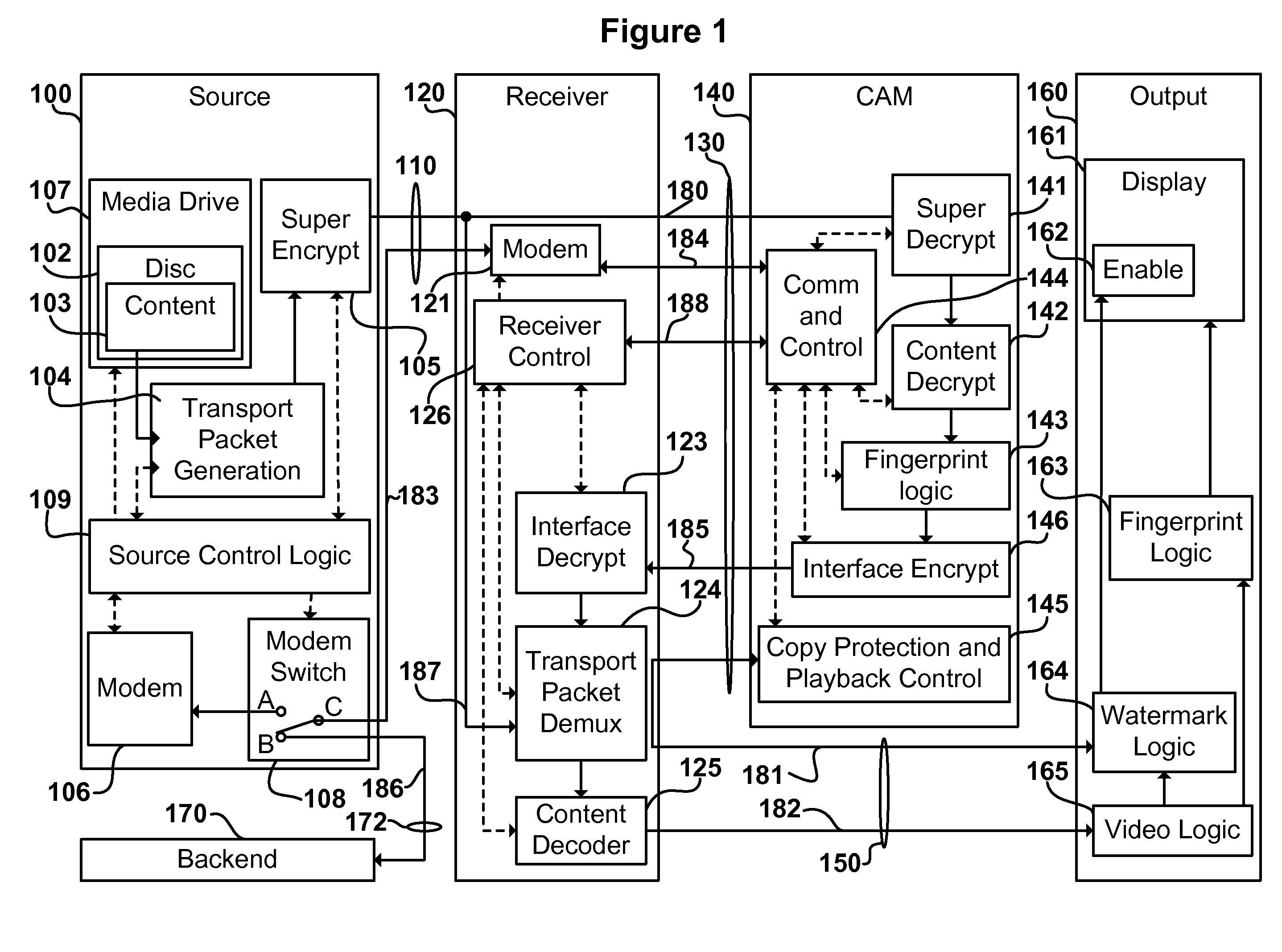
A content distribution system and method which prevents unauthorized access to secured content such as movies and music. The apparatus includes a source, a receiver, an authorized security device such as a conditional access module (CAM) for decrypting authorized content, an output device for outputting content and a backend for managing accounts and system operations. One aspect of this invention provides a mechanism for providing secured content on a medium such as a DVD optical disc. These devices may verify that there is authorization to play the secured content, add watermarks to the secured content, convert the secured content to a displayable form and provide a means for preventing output of the secured content.
Owner:GOOGLE LLC
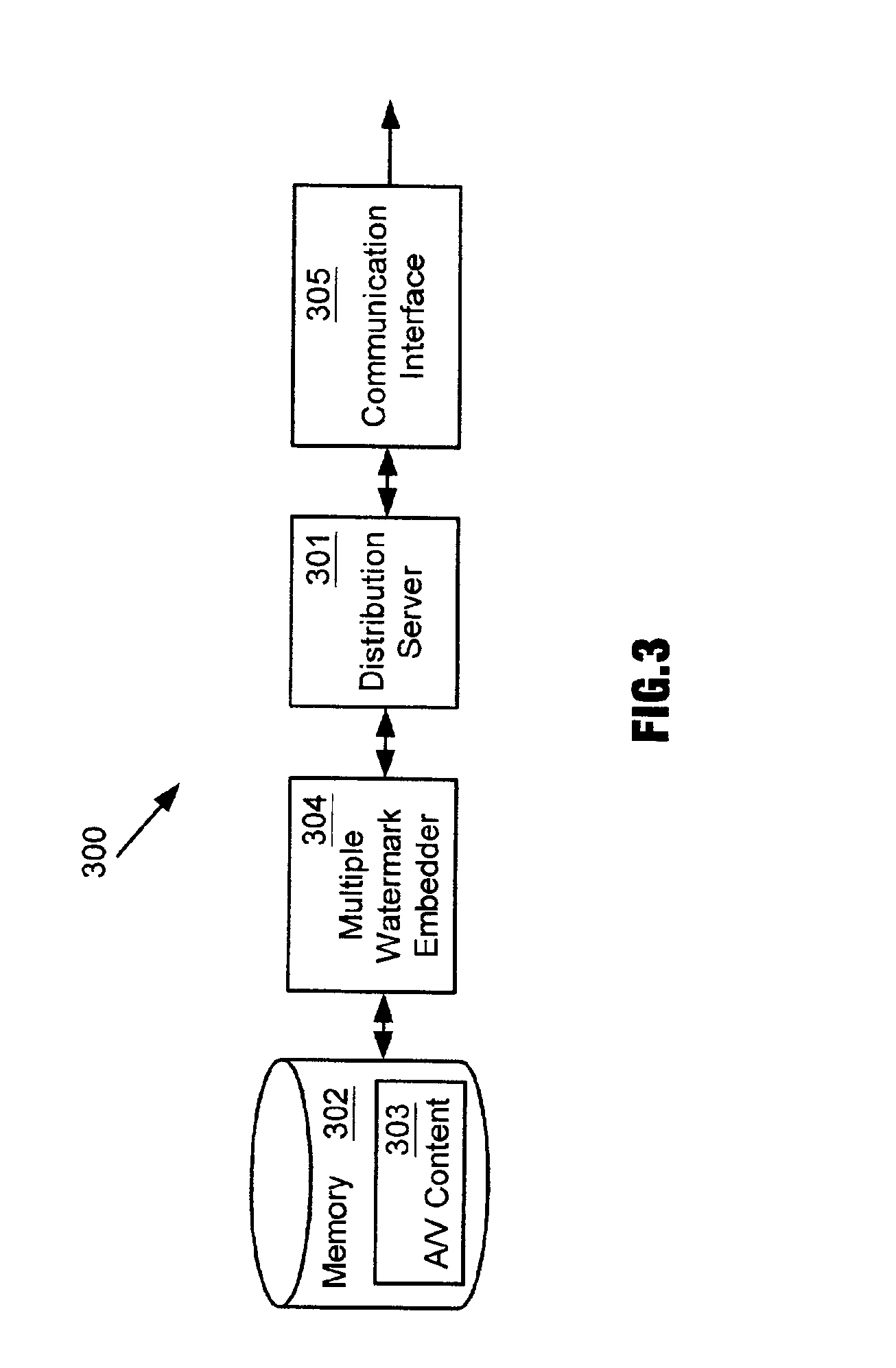
Enhanced copy protection of proprietary material employing multiple watermarks
InactiveUS6931536B2Enhanced copyEnhanced play protectionDigital data processing detailsUser identity/authority verificationComputer hardwareCopy protection
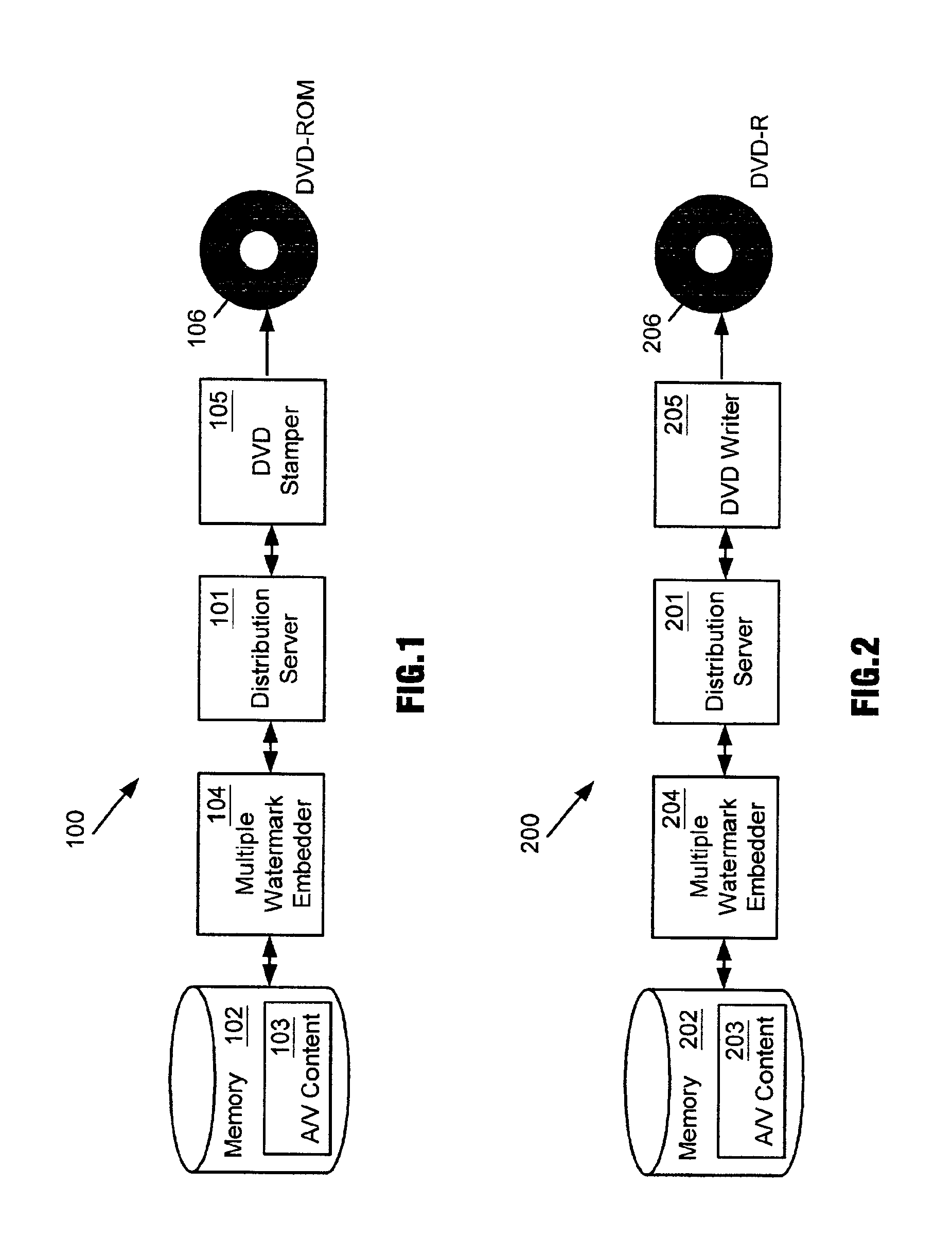
A method and apparatus for distributing proprietary material employs multiple watermarks embedded in the proprietary material for enhanced copy protection. A first watermark is to be processed by programmable and non-programmable devices configured to process the first watermark for copy protection of the proprietary material. If a programmable device eliminates the first watermark so that unauthorized copies of the proprietary material can be made, then non-programmable devices configured to process a second watermark as well as the first watermark look for and process the second watermark for copy protection of the proprietary material upon their failure to detect the first watermark.
Owner:MARKING OBJECT VIRTUALIZATION INTELLIGENCE LLC
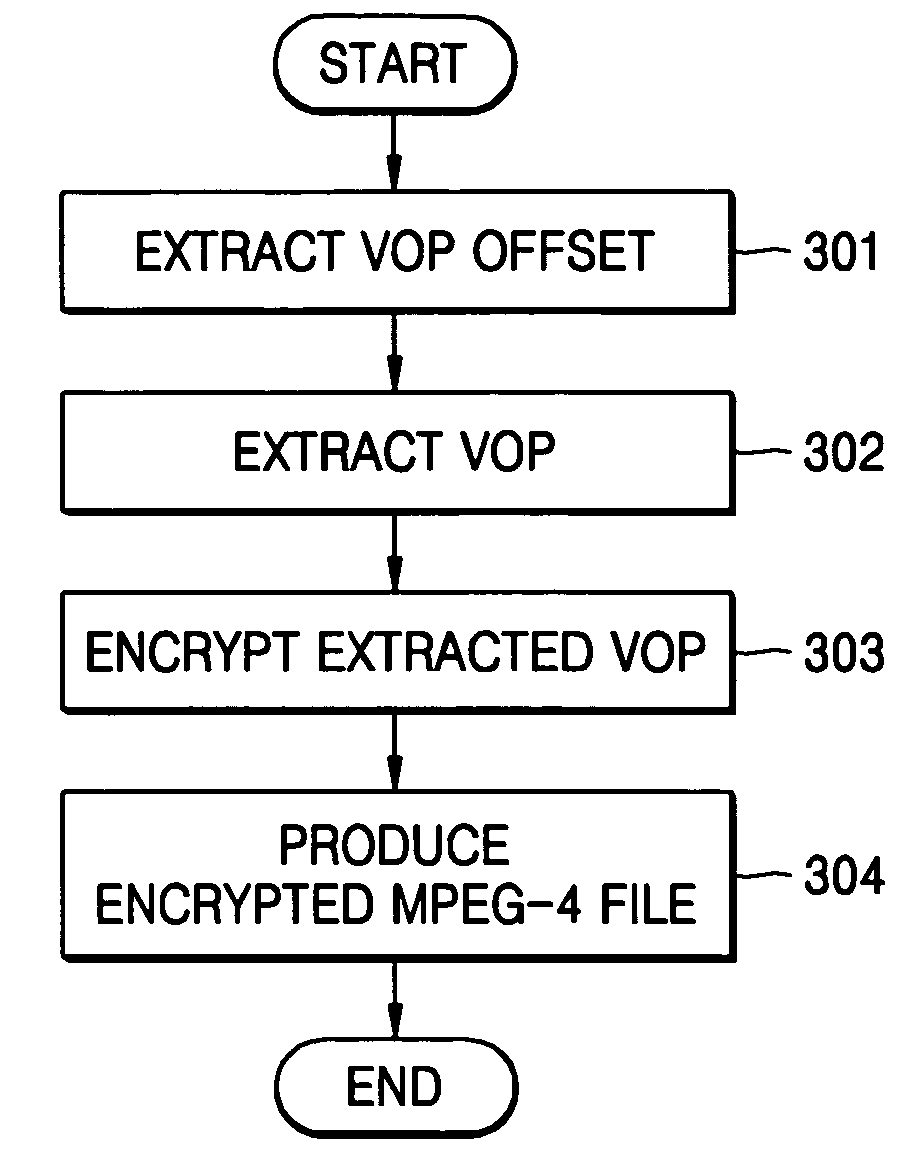
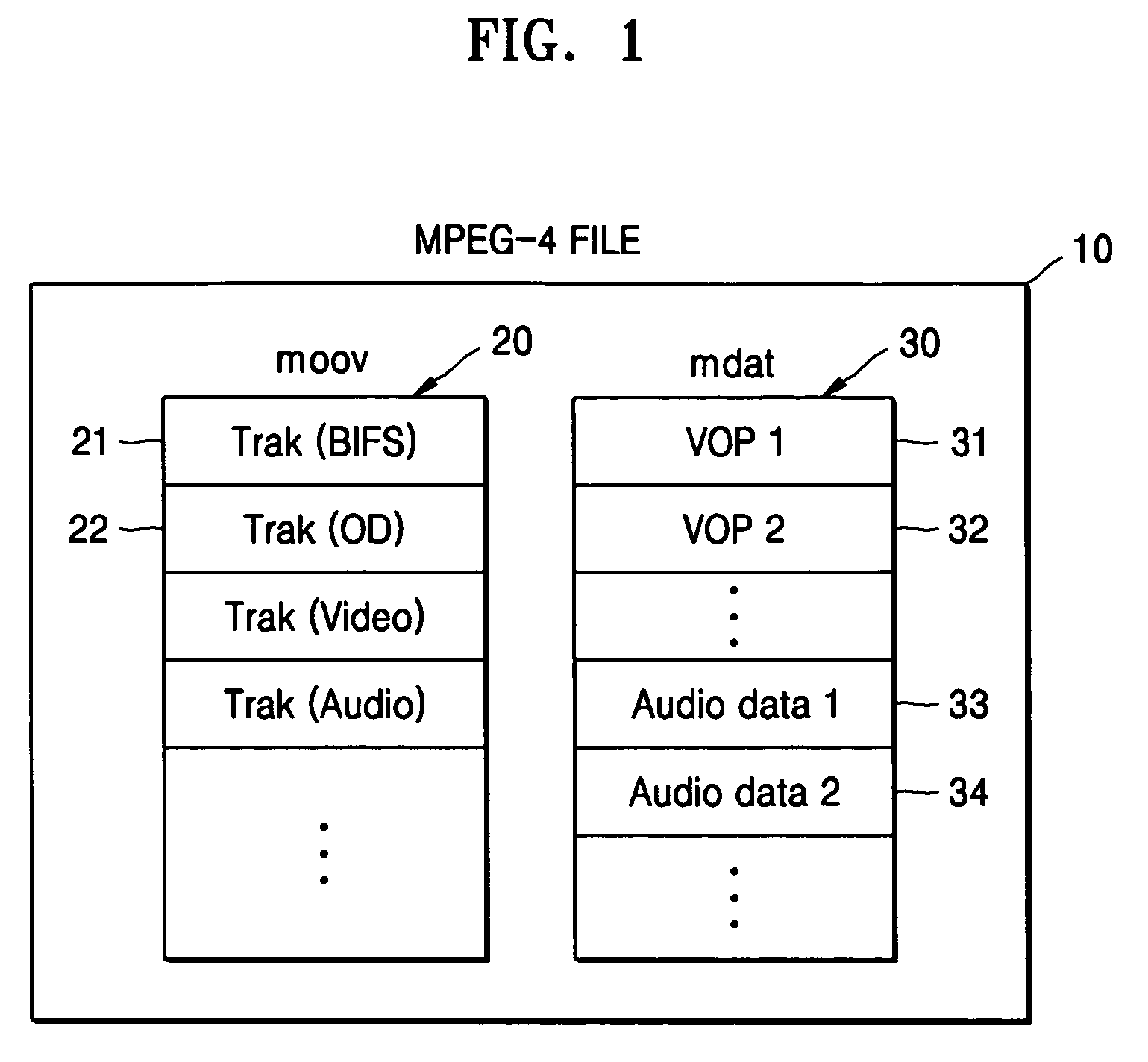
Motion picture file encryption method and digital rights management method using the same
InactiveUS20050123136A1Efficient use ofTelevision system detailsKey distribution for secure communicationComputer graphics (images)Digital rights management
A method of encrypting a motion picture file and a method of digital rights management using the same, wherein encryption method includes: extracting information on the location of at least one video sample, which is a real-time streaming unit, from meta-data of the motion picture file; extracting the video samples based on the location information; encrypting the extracted video samples, excluding a start code within a video sample header of each extracted video sample, based on predetermined encryption information; and producing an encrypted motion picture file by recombining the encrypted video samples. Since the file is encrypted in units of video object planes (VOPs) while maintaining an MEPG-4 file format, the encryption method can be easily applied to a completed file format and streaming service is also possible.
Owner:IND ACAD COOP GRP OF SEJONG UNIV +1
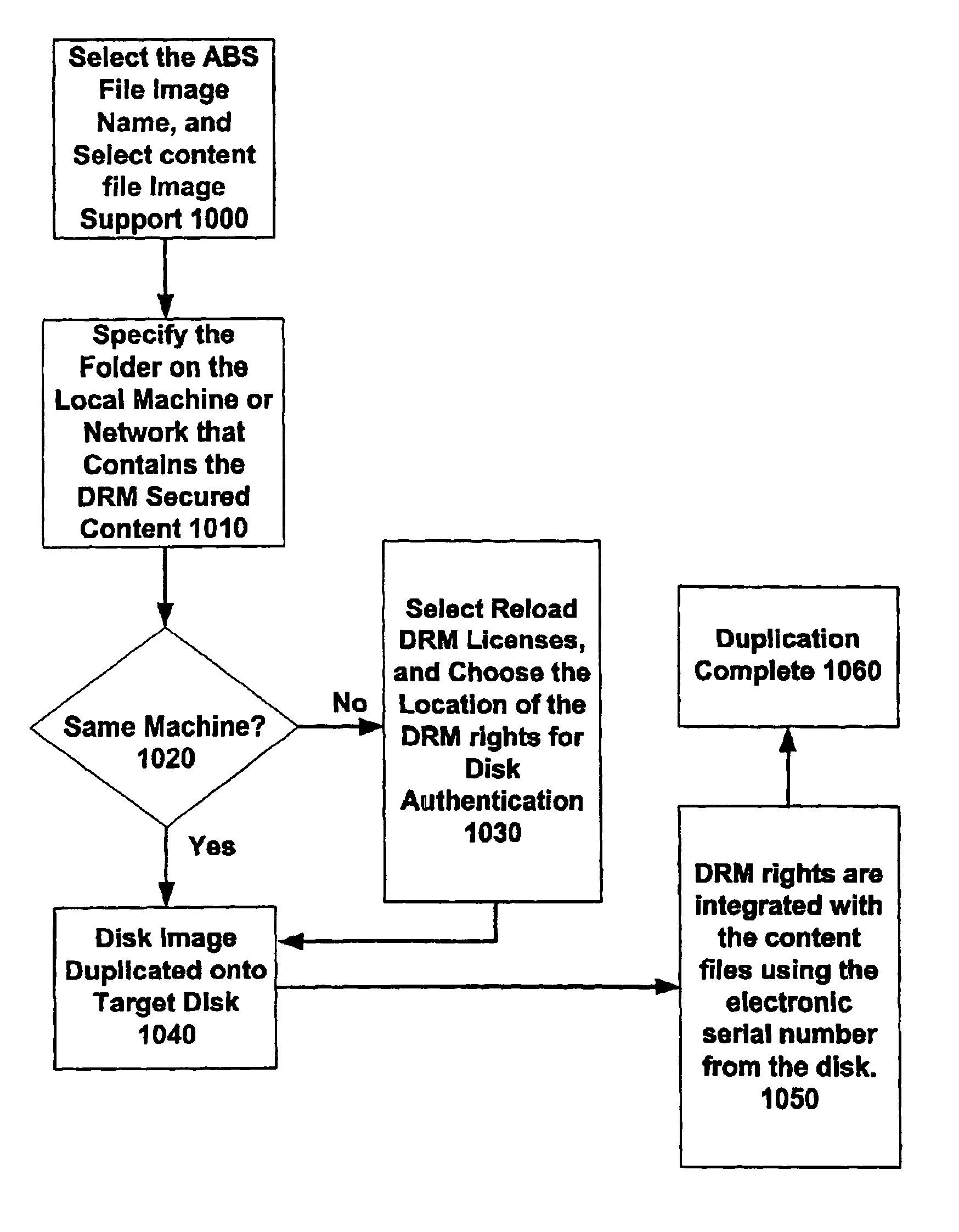
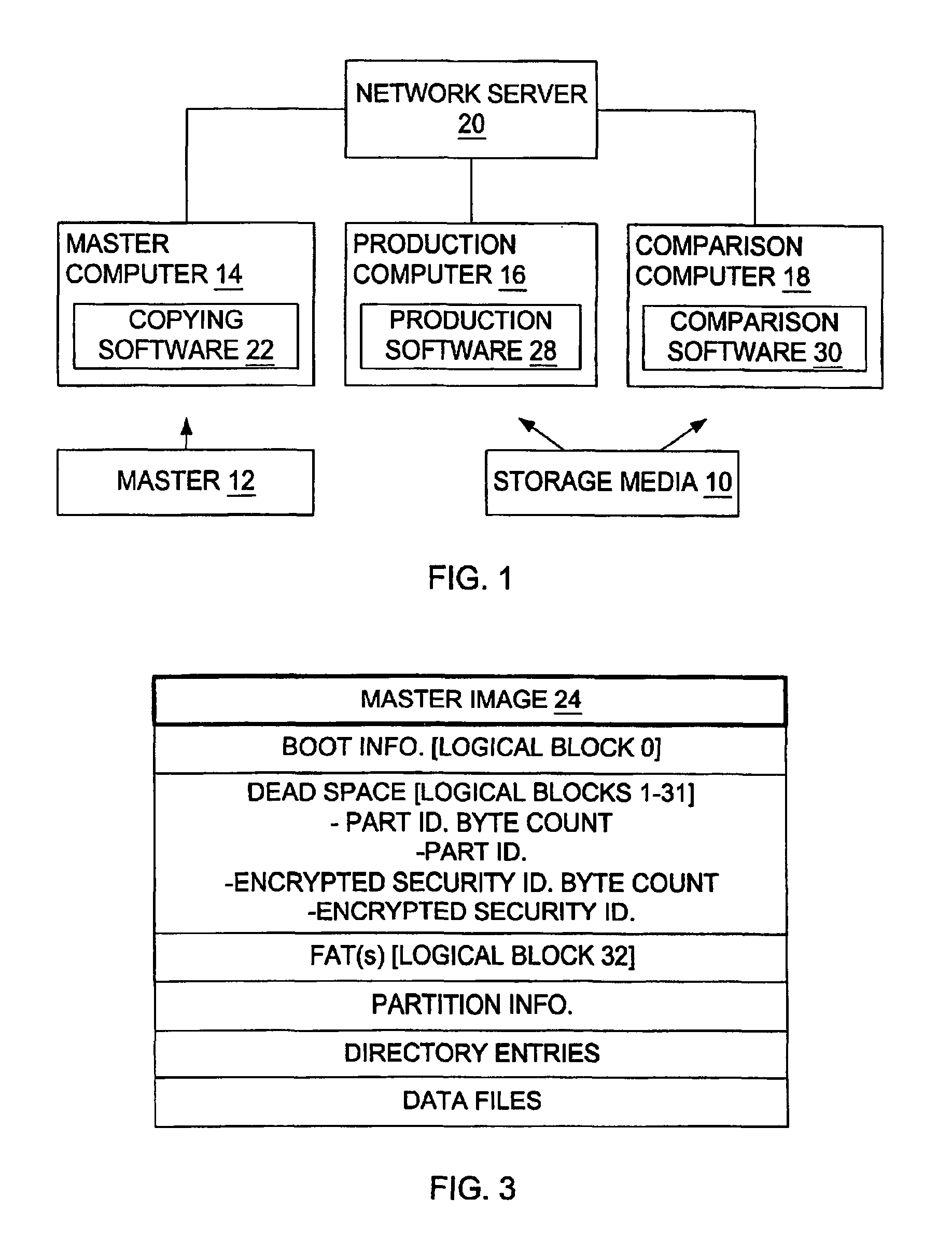
Method and system for providing secure digital music duplication
InactiveUS6920565B2Eliminate needCircuits to prevent unauthorised copying/reproductionUnauthorized memory use protectionDigital dataDigital content
A system and method are provided wherein digital data representing content and associated license rights may copied to a storage medium, such as a removable storage medium, whereby the serial number of the copied-to storage medium is integrated into the licensing scheme utilized to secure the digital content. As a result, the digital content is pre-authenticated and bound to the copied-to storage medium, obviating the need to access a network or other location for access to the protected content.
Owner:BOZAK INVESTMENTS
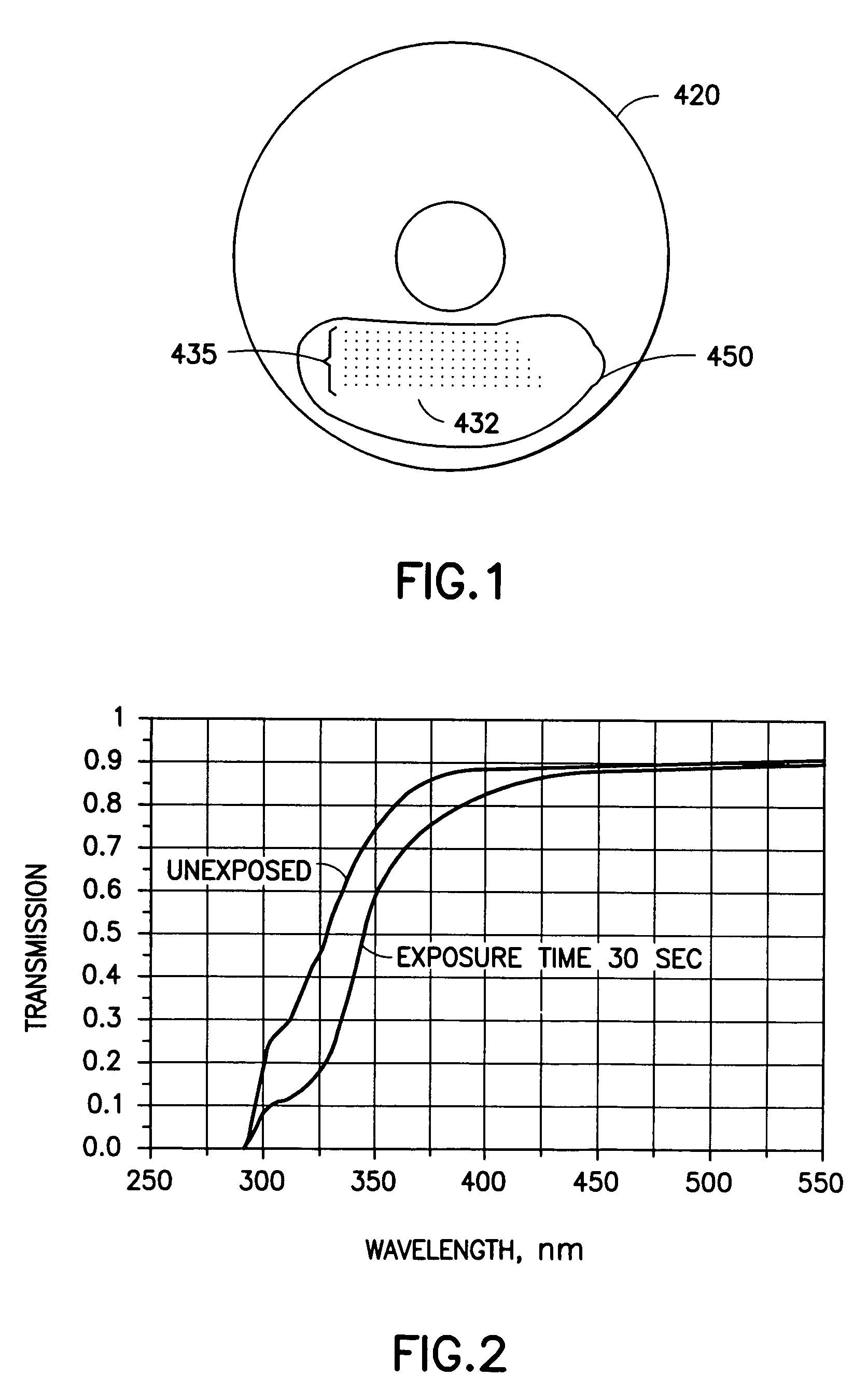
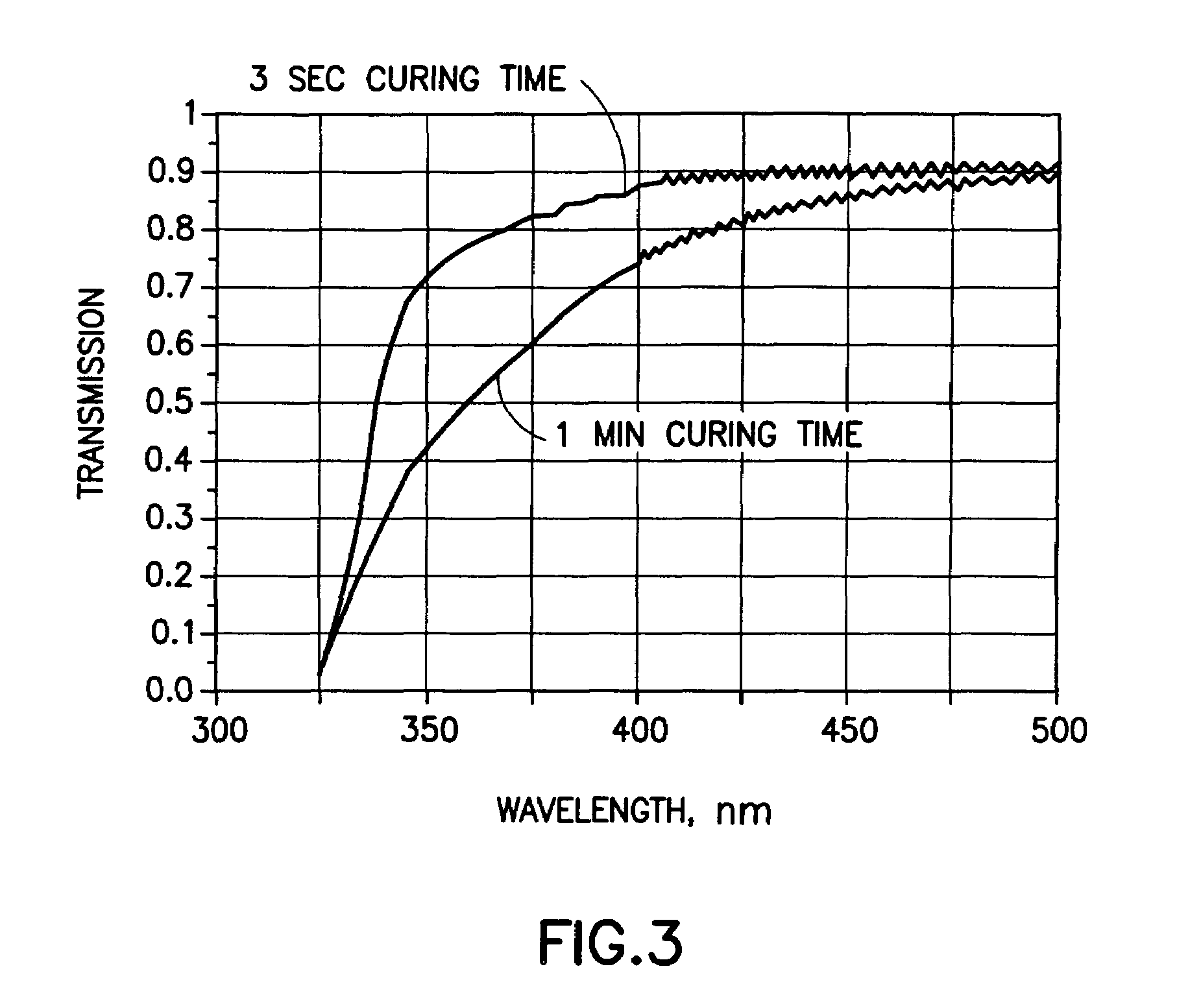
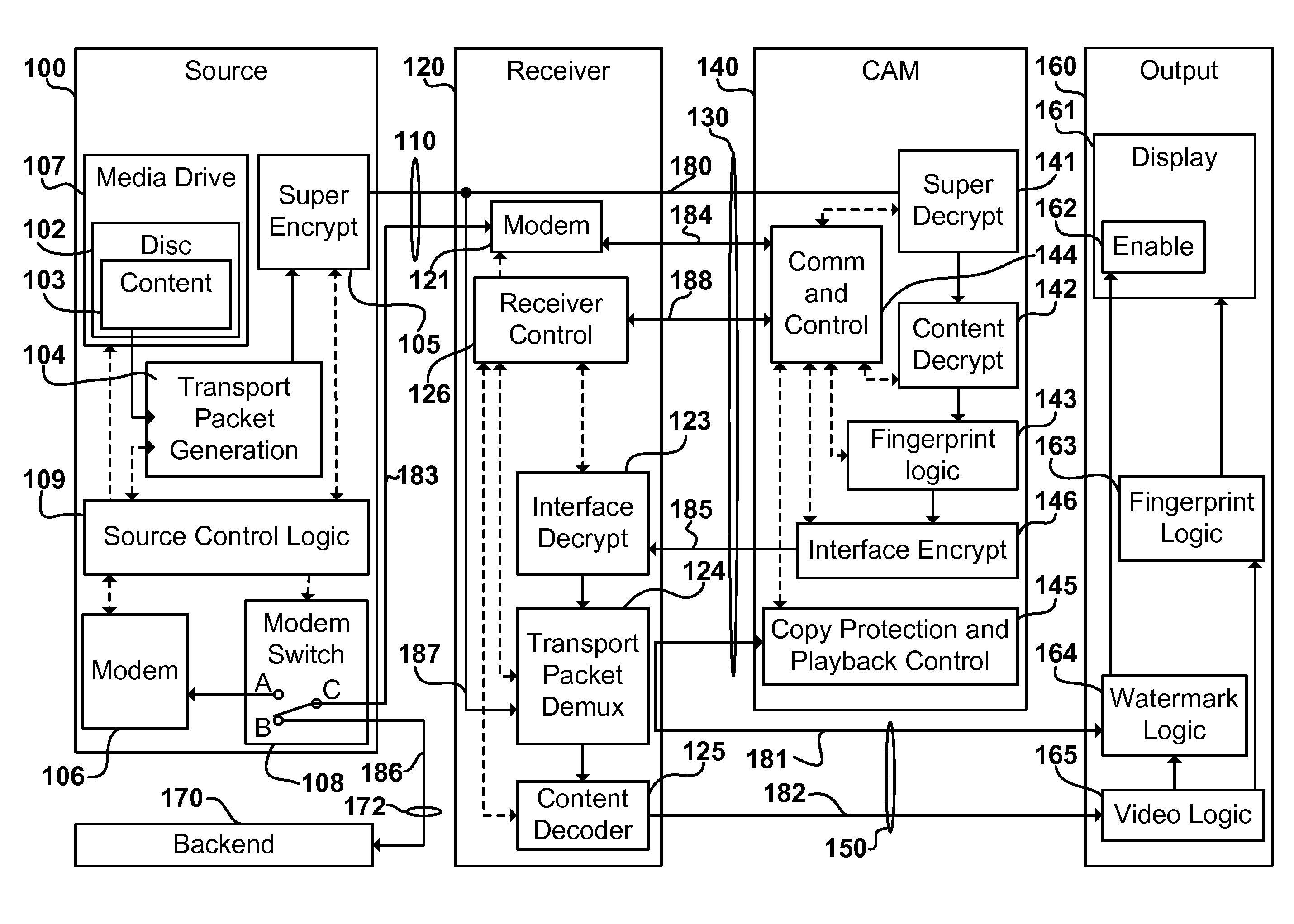
System for applying markings to optical media
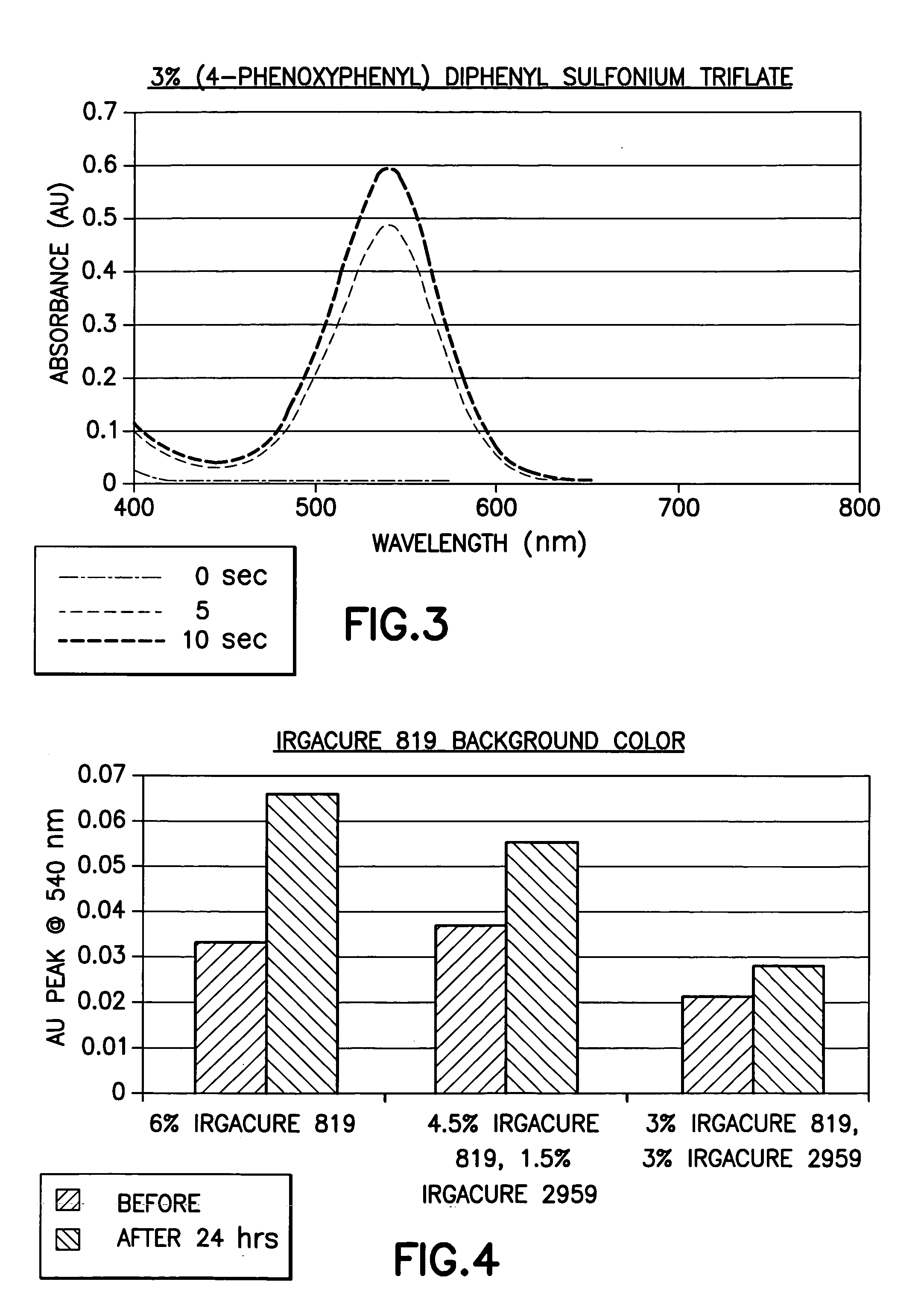
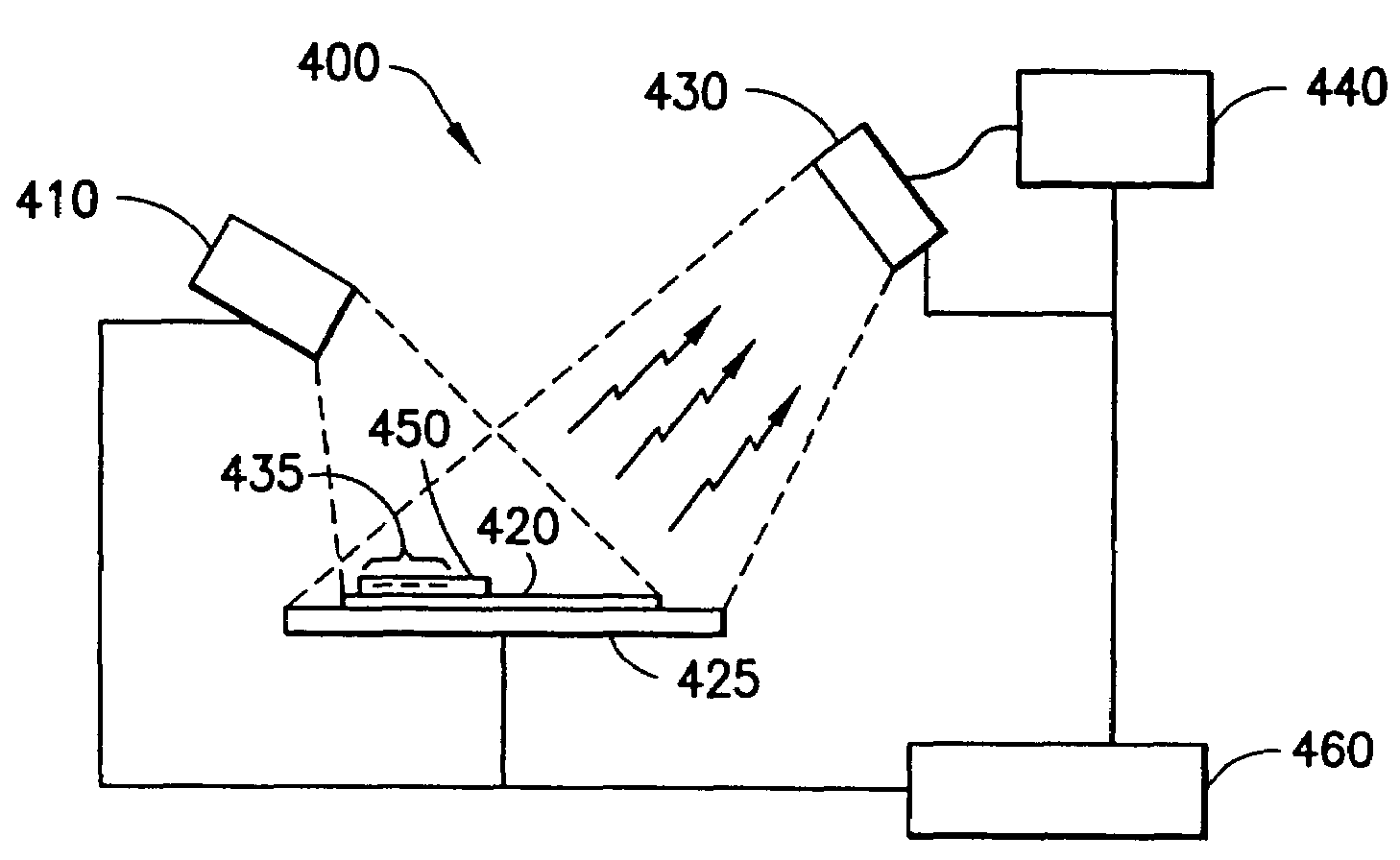
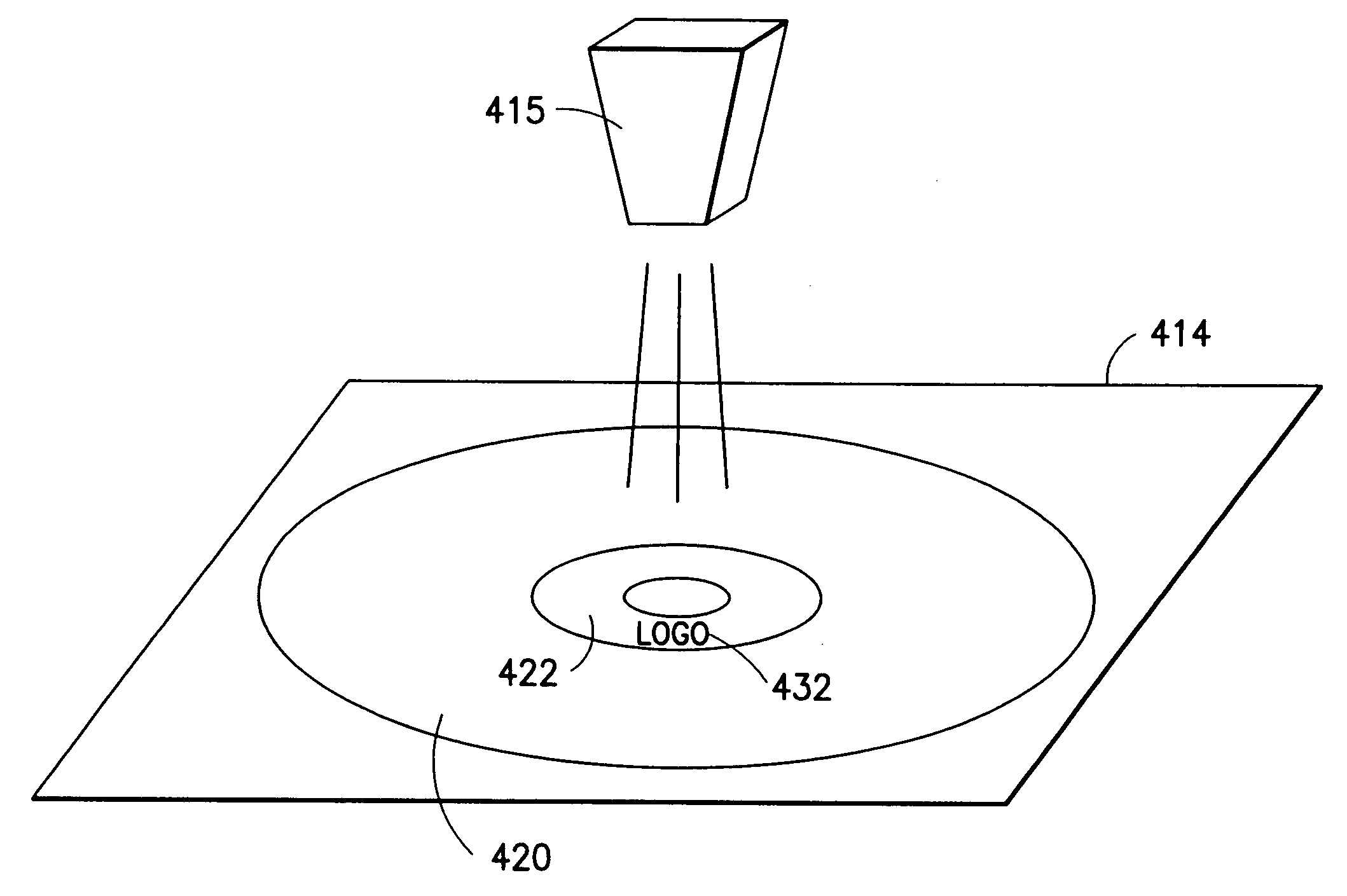
Disclosed herein is a system for recording a marking in the readout area of an optical media, wherein the marking does not interfere, or substantially interfere, with the readout of data from the optical media. The system disclosed herein is supportive of commercial production requirements. Markings may contain content as desired by the user of the system, including text, graphics, or other items. The marking is formed in a photosensitive coating that is applied to the optical media, and then cured with a first light. A second light, having a substantially separate band of wavelengths from the first light, is used to image a marking into the coating. The coating is robust to many external influences, such as ambient environmental conditions, and physical wear.
Owner:SPECTRA SYST CORP
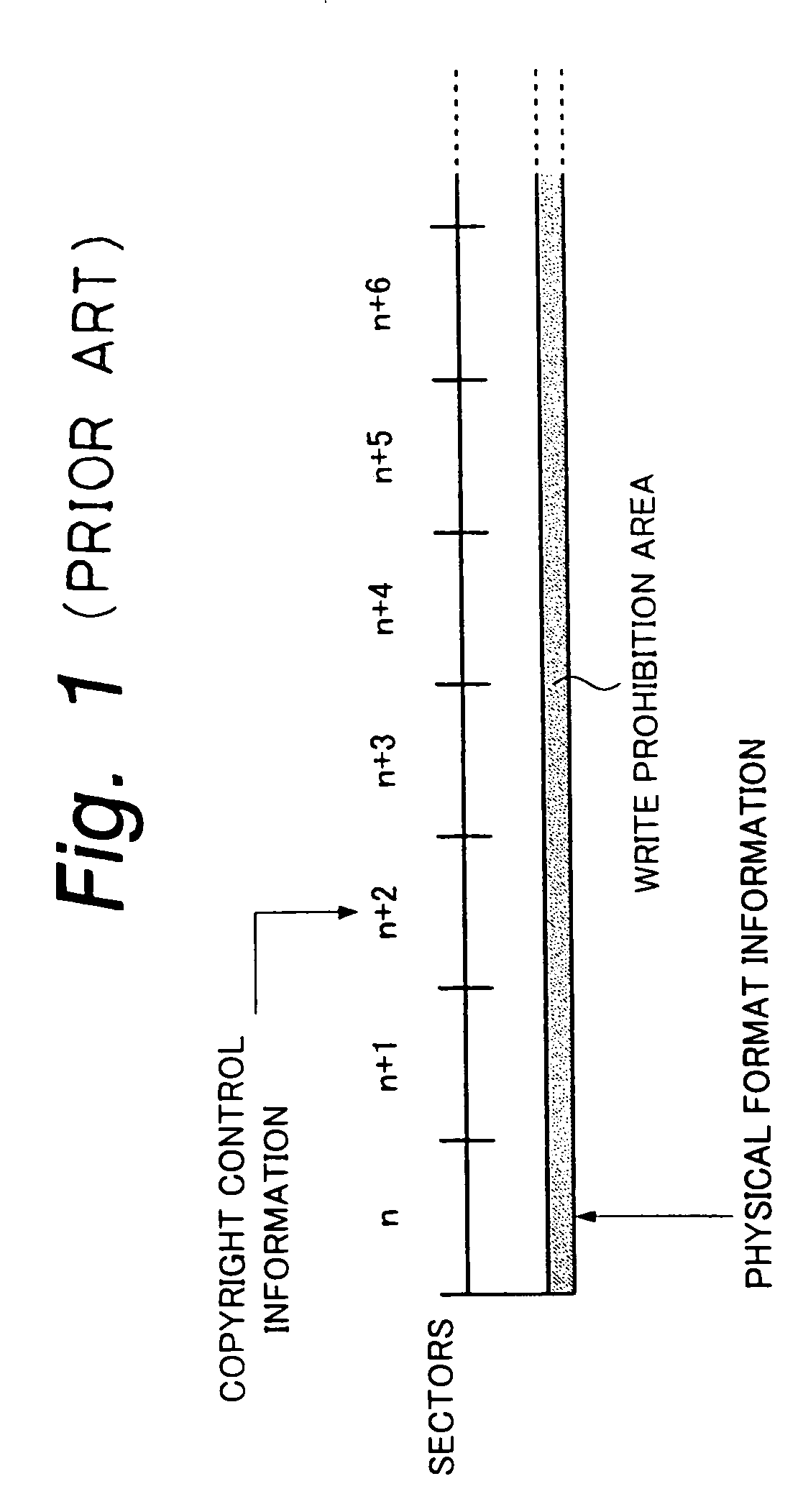
Copyright control of encrypted data using uncorrected errors in an error correcting code
A data storing medium has a digital data area in which encrypted digital data or non-encrypted digital data is written, a control data area in which control data necessary for reproducing recorded digital data is written, and a copyright control information area in which copyright control information necessary for decrypting encrypted digital data is written, wherein the copyright control information area is write-prohibited, and wherein the control data area is write-permitted.
Owner:SONY CORP
Marking articles using a covert digitally watermarked image
ActiveUS7184569B2Accessories for auxillary signalsUser identity/authority verificationFluorescenceUltraviolet lights
A marking system that includes forming at least one marking in or on an article, wherein the image formed is not visible to the unaided human observer, and further contains at least one digital watermark. The digitally watermarked image comprises emissive and photoabsorptive portions. The digitally watermarked image is applied using a substance reactive to a predetermined excitation source, and exposure to ultraviolet light. Other traditional techniques, such as printing with fluorescent inks may be used in combination. The digitally watermarked image is subsequently observable upon exposure to the predetermined excitation source. The digitally watermarked image may be observed and decoded by appropriately configured detection systems, wherein the information obtained may be used for purposes including, but not limited to, authentication and security of the article or information contained within the article.
Owner:SPECTRA SYST CORP
Digital content distribution system and method
InactiveUS7698570B2Obtaining unauthorized accessPrevent unauthorized accessDigital data processing detailsUser identity/authority verificationContent distributionDigital content
A content distribution system and method which prevents unauthorized access to secured content such as movies and music. The system includes a source, a receiver, an authorized security device such as a conditional access module (CAM) for decrypting authorized content and an output device for outputting content. The system can also include a backend for managing accounts and system operations. One aspect of this invention is that the content data is derived from the Internet. The system allows for the verification of authorization to play secured content, the addition of watermarks to the secured content, the conversion of the secured content to a displayable form and the means for preventing output of the secured content.
Owner:GOOGLE LLC
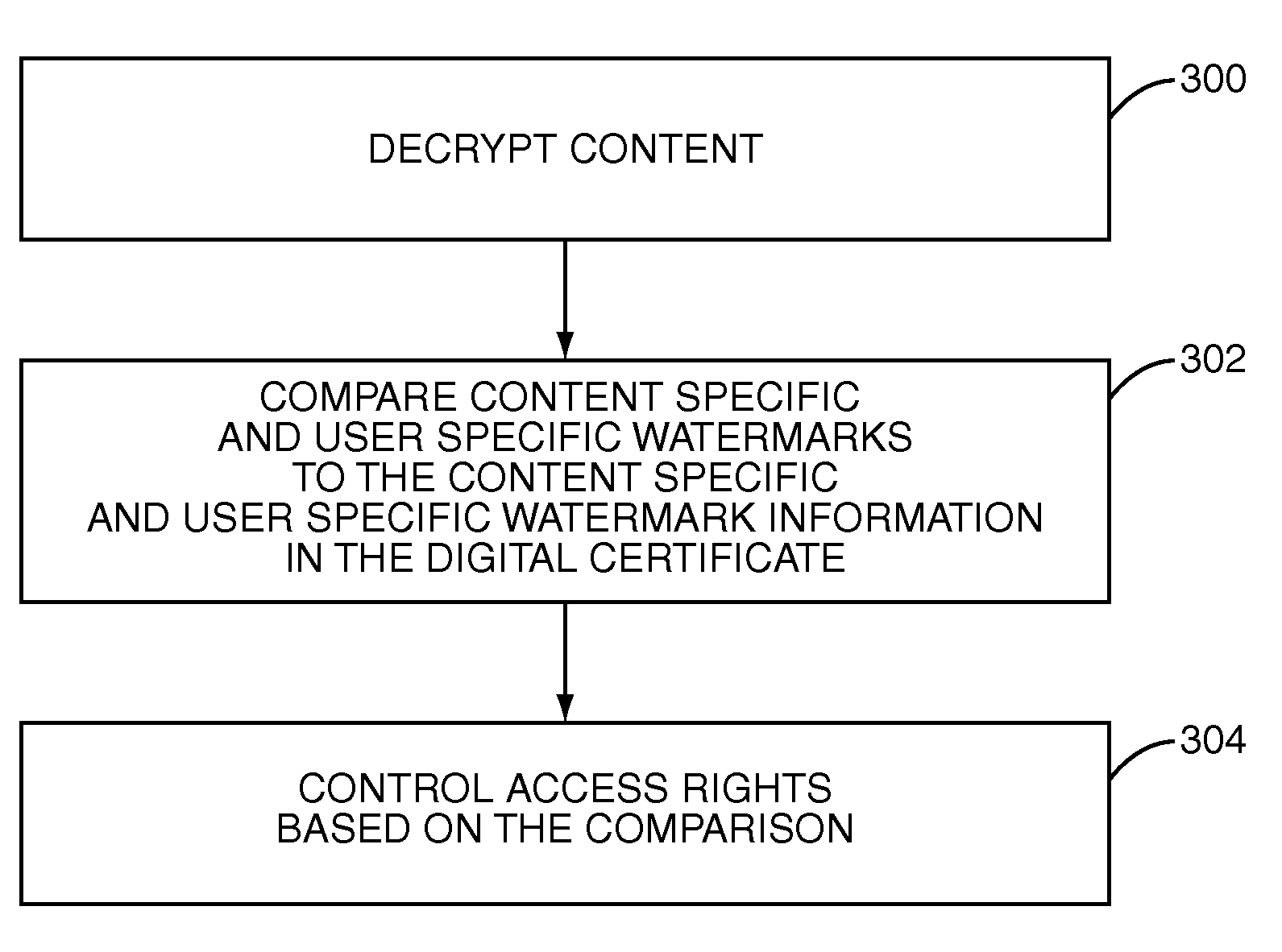
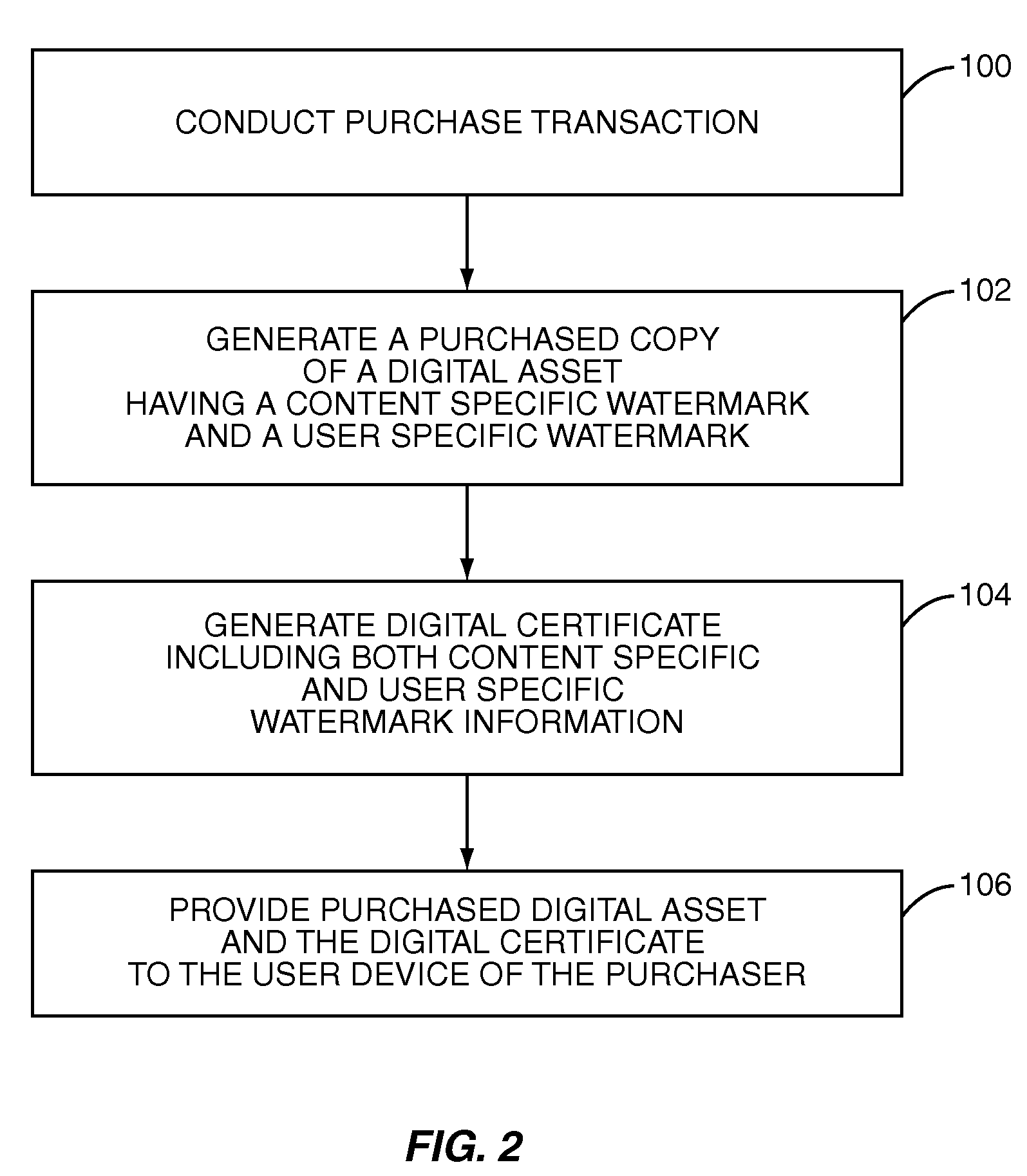
Multiple watermarks for digital rights management (DRM) and content tracking
InactiveUS7802306B1Digital data processing detailsUser identity/authority verificationDigital rights managementDigital asset
A system and method for providing Digital Rights Management (DRM) using multiple watermarks are disclosed. In one embodiment, upon purchase of a digital asset, a copy of the digital asset that is watermarked with a content specific watermark and a user, or purchaser, specific watermark and a digital certificate including content specific watermark information and user specific watermark information corresponding to the watermarks in the copy of the digital asset are generated. The copy of the digital asset and the digital certificate are provided to the user. Thereafter, access to the copy of the digital asset is controlled based on a comparison of the watermarks in the copy of the digital asset and the watermark information in the digital certificate.
Owner:QURIO HLDG
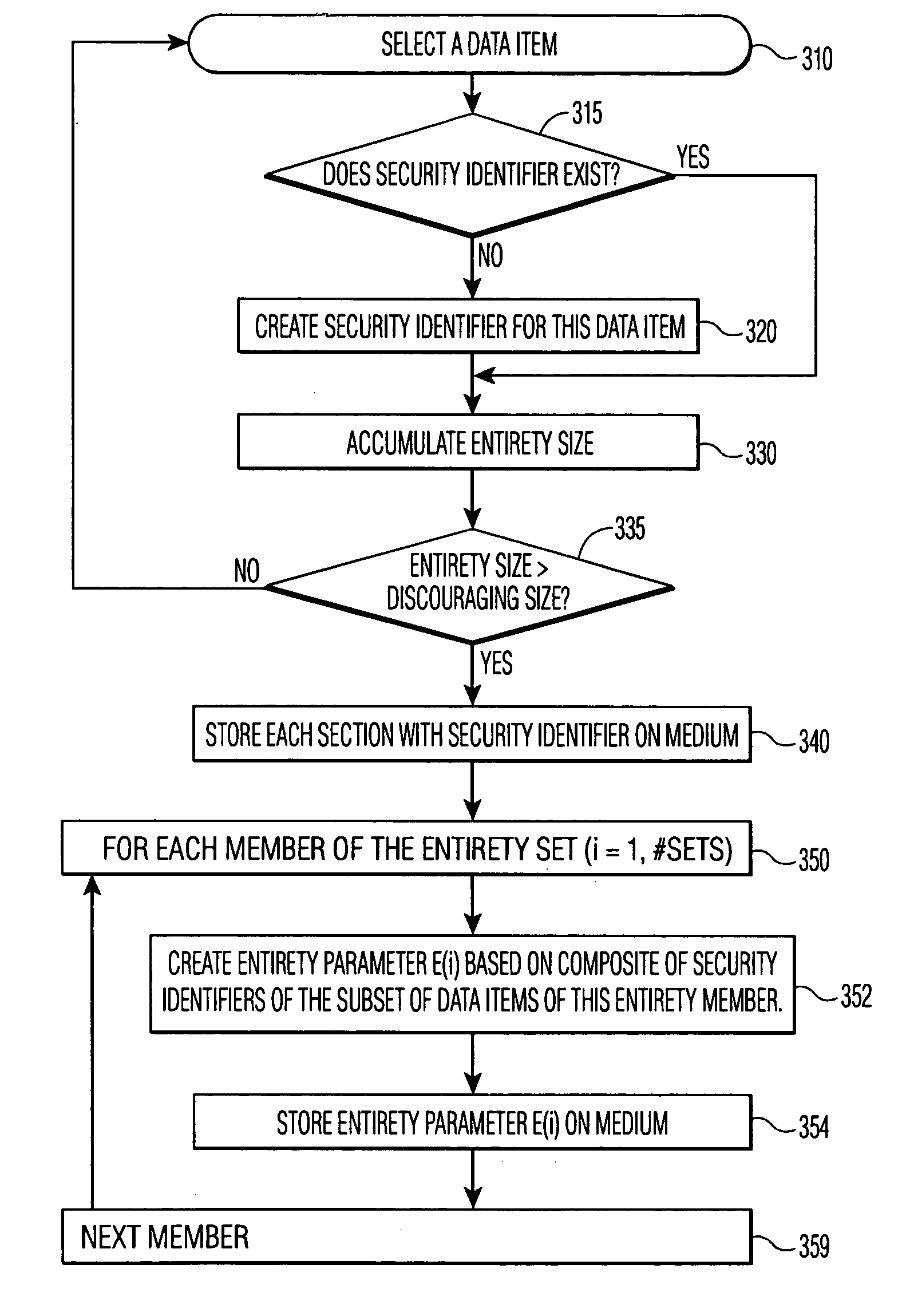
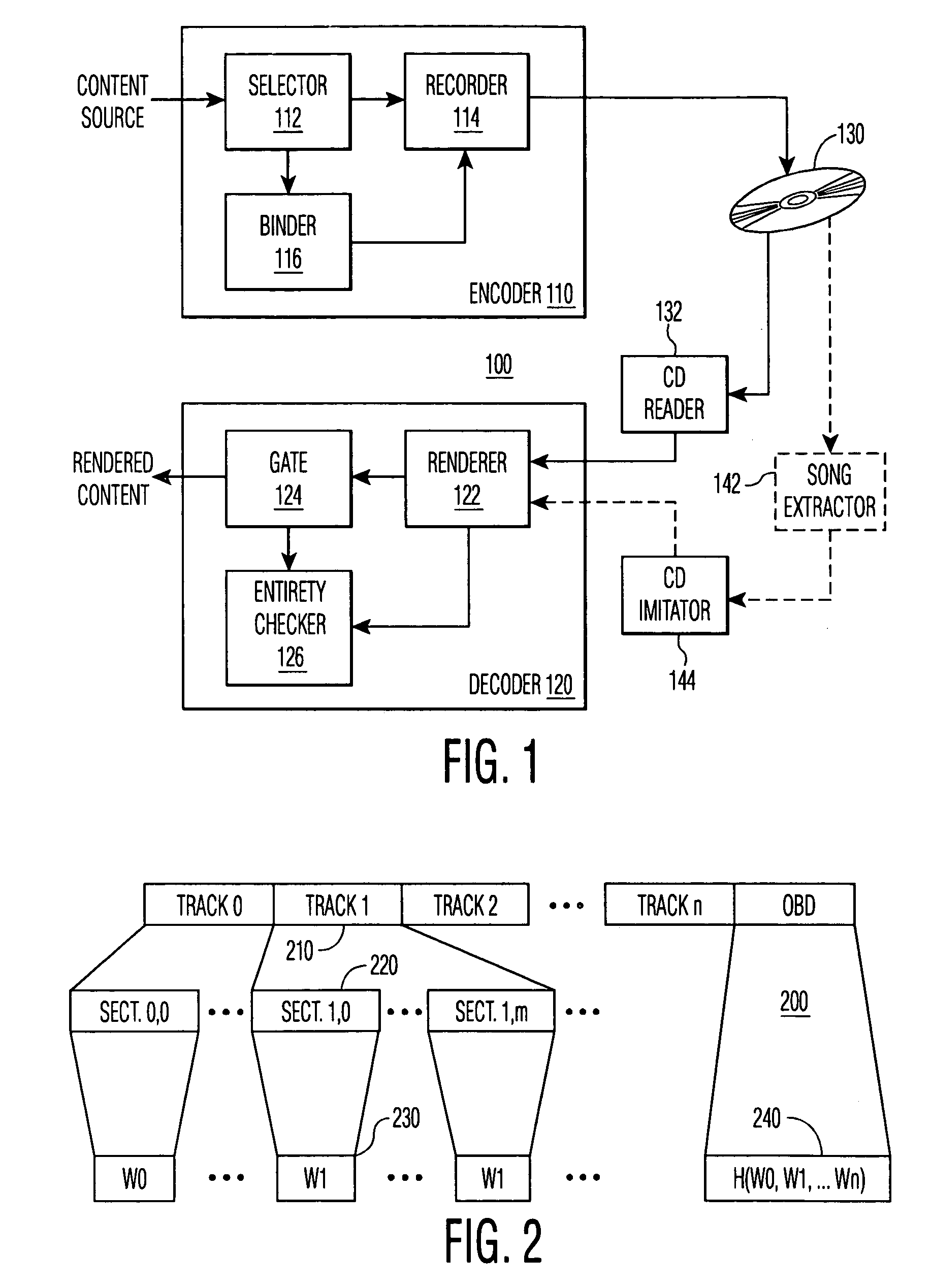
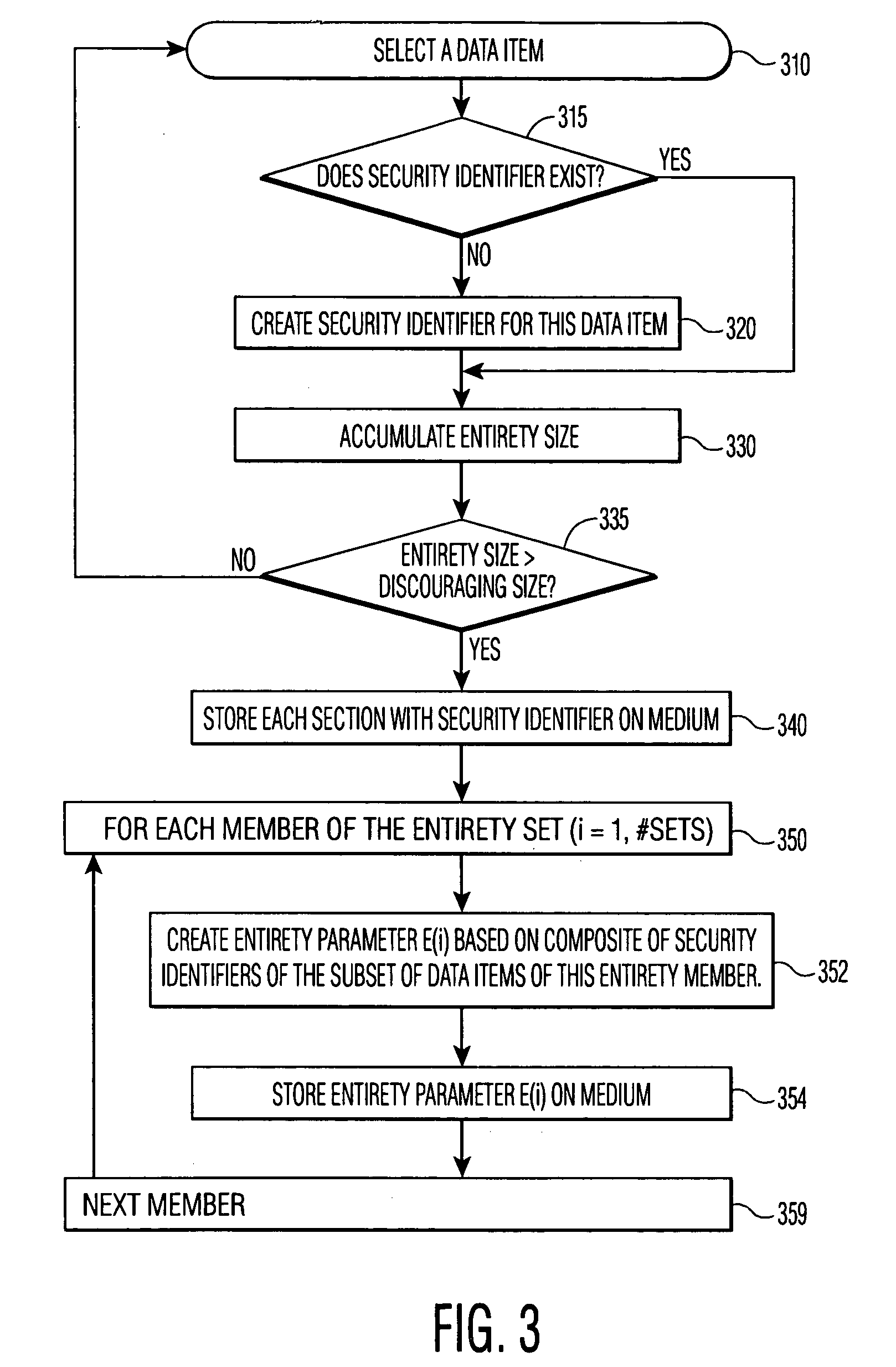
Protecting content from illicit reproduction by proof of existence of a complete data set using security identifiers
InactiveUS6986048B1Avoid spreadingIncrease the number ofVolume/mass flow measurementUser identity/authority verificationComplete dataData set
A number of data items are selected for inclusion in a data set so as to discourage a transmission of the entire set over a limited bandwidth communications path, such as the Internet. The data set includes an entirety parameter that is used to determine whether the entirety of the data set is present. In a preferred embodiment, the entirety parameter is a hash value that is based on watermarks of each data item. When presented for rendering, the watermarks of the data items in the presented material are read and a hash value based on the presented watermarks is computed. A mis-match between the computed hash value and the entirety hash value contained in the data set indicates that less than the entirety of the data set is being presented, and the rendering is prohibited.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Management Server Device, Content Repoduction Device, and Recording Medium
InactiveUS20080049934A1Easy to specifyEasy to findTelevision system detailsPulse modulation television signal transmissionCapacity limitAuthorization
When a technique for specifying an unauthorized terminal based on a combination of watermarks embedded in content distributed without authorization is applied to content distributed on recording media, recording capacity limits of the recording media lead to a limit on the number of combinations of watermarks that can be embedded in the content, and only a limited number of terminals can be specified. In the present invention, all terminals are sorted into the same number of groups as there are combinations of watermarks, and a group that includes an unauthorized terminal can be specified based on the combination of watermarks embedded in the content. When the group including the unauthorized terminal is specified, this group is divided into groups, and a plurality of groups that do not include the unauthorized terminal are integrated. This enables the unauthorized terminal to be specified while keeping within the capacity of the recording medium.
Owner:PANASONIC CORP
Marking and authenticating articles
InactiveUS7220535B2Accessories for auxillary signalsPhotosensitive materialsComputer scienceAccess to information
Disclosed herein are methods and apparatus for providing markings upon objects, including the read side of an optical information media, where the markings do not substantially interfere with object, including the use of the optical information media. This invention discloses use of a coating, marking schemes, printing of markings with UV light, as well as methods and apparatus for reading and deciphering said marking. Included is an authentication scheme, where the marking may be used as a lock to limit access to information contained in an optical information media.
Owner:SPECTRA SYST CORP
Error Correction Scheme for a Disc-Playing System
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
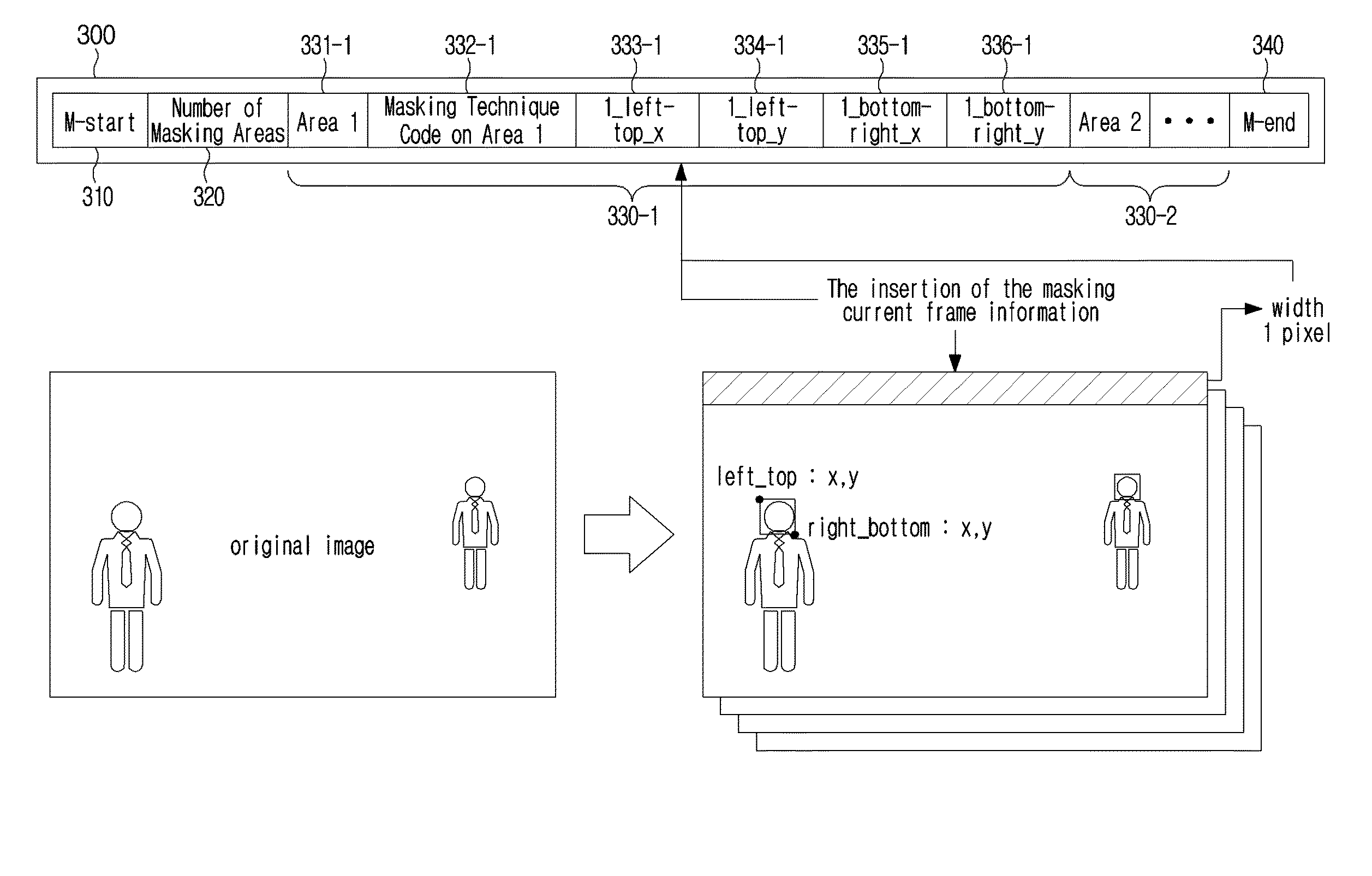
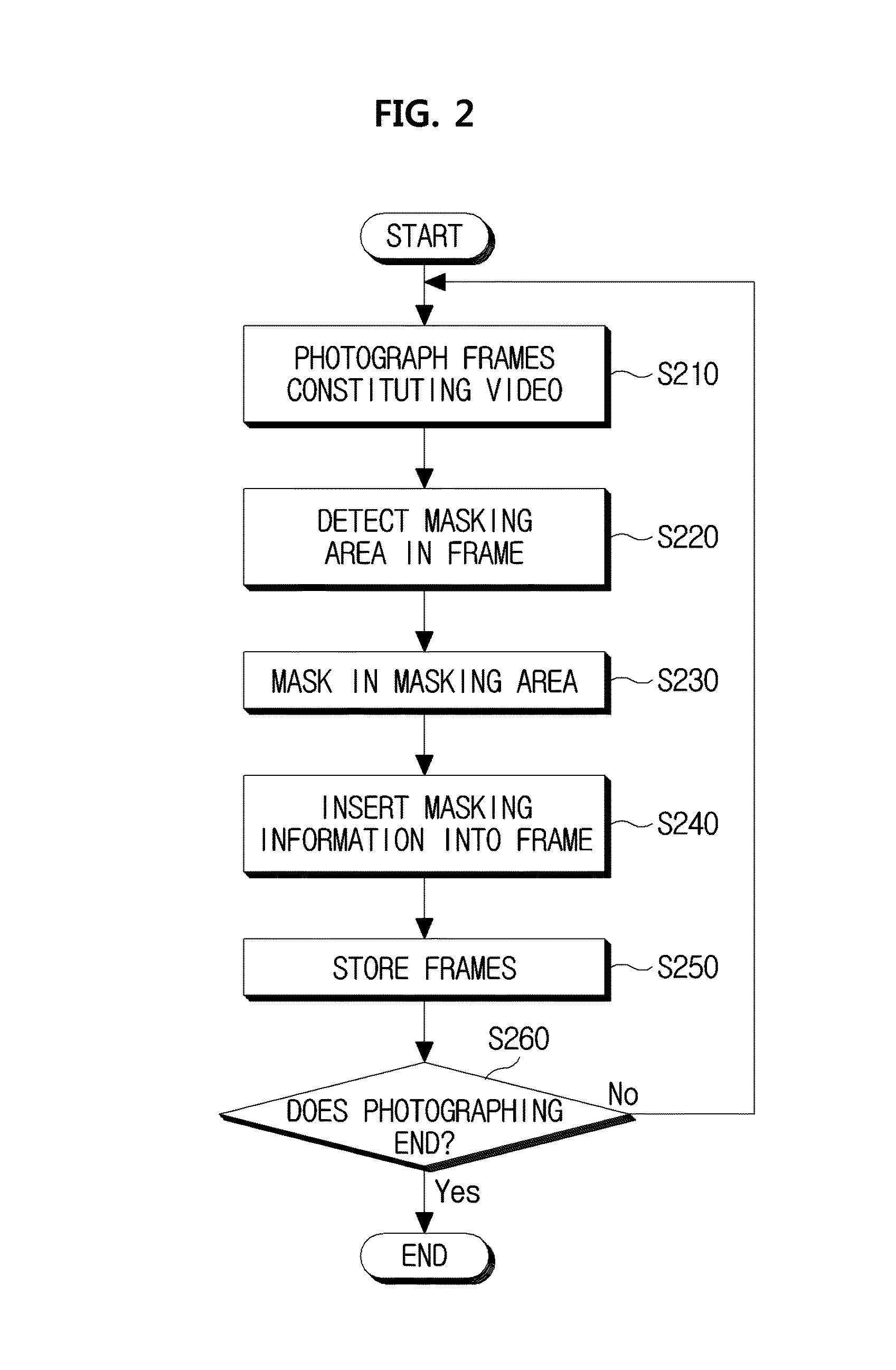
Video masking processing method and apparatus
ActiveUS20160155465A1Not infringe others' privacyTelevision system detailsElectronic editing digitised analogue information signalsComputer graphics (images)Device Sensor
A video masking processing method and a video masking processing apparatus using the same are provided. The video masking processing method photographs frames constituting a video, detects at least one masking area to be masked in the photographed frames, masks an image in the detected at least one masking area, inserts masking information including information on the masking into the photographed frame, and stores the frame which has undergone the masking and has the masking information inserted thereinto. Therefore, since images related to personal information in a photographed video are masked, a user does not infringe others' privacy in a video normally photographed by a CCTV or a dashboard camera.
Owner:KOREA ELECTRONICS TECH INST
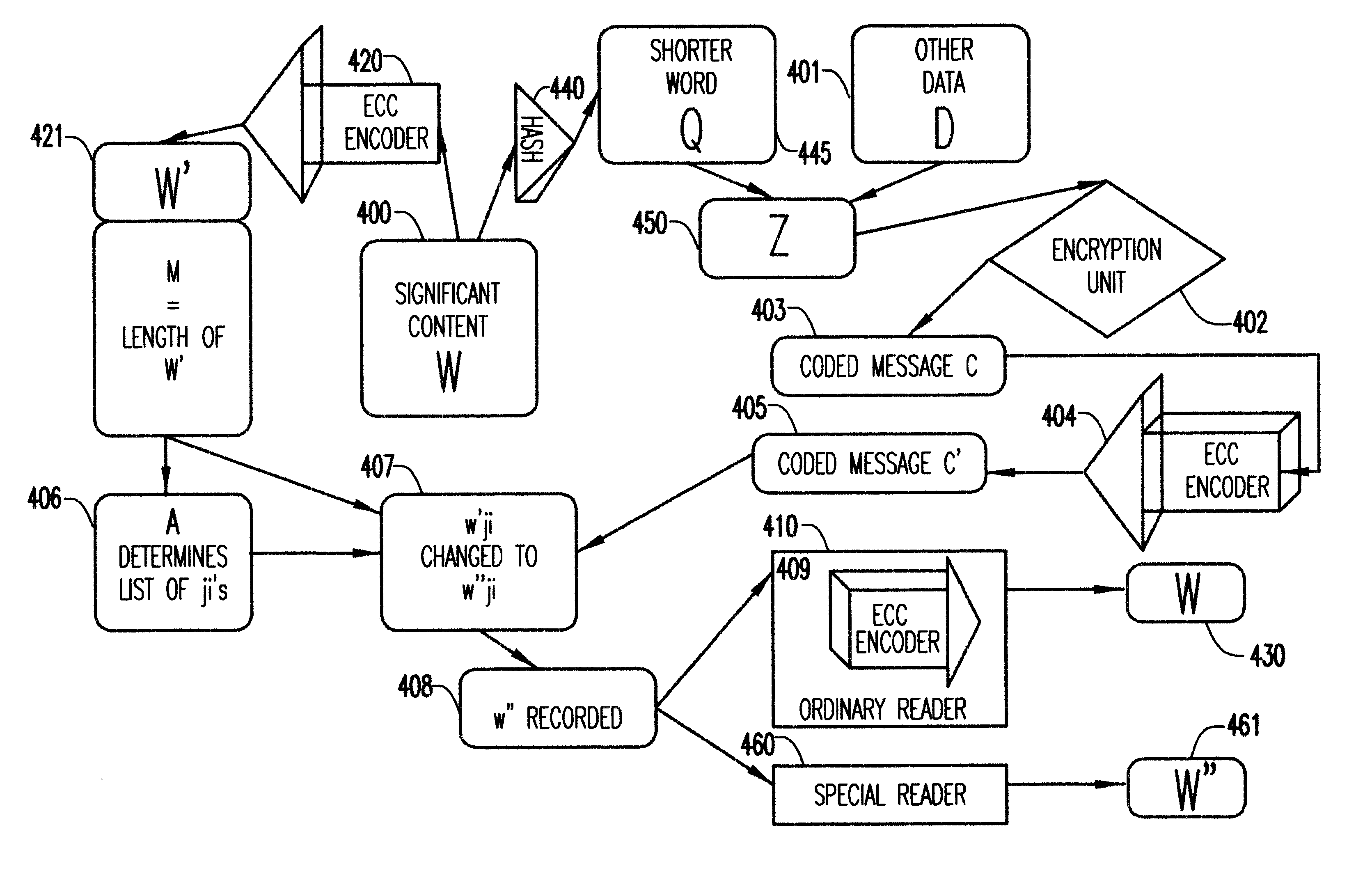
Method and apparatus for watermarking with no perceptible trace
InactiveUS6564322B1Public key for secure communicationDigital data processing detailsDigital recordingDigital records
A watermark in the form of an added message is attached to a digital recording so that a significant content of the recording is completely unchanged by the process in the sense that any reader commonly used for such recording will extract from the recording exactly what would have been extracted in the case the added message had not been attached. This is done by hiding the added message in the error correcting code (ECC) for the significant content of the recording.
Owner:IBM CORP
Collusion-robust watermarking
InactiveUS20050108535A1Prevent removalTelevision system detailsUser identity/authority verificationWatermark embeddingMultiple copy
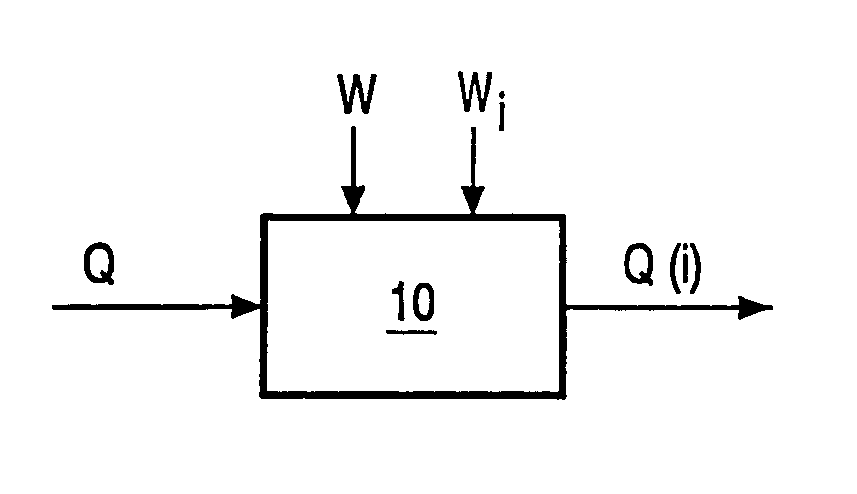
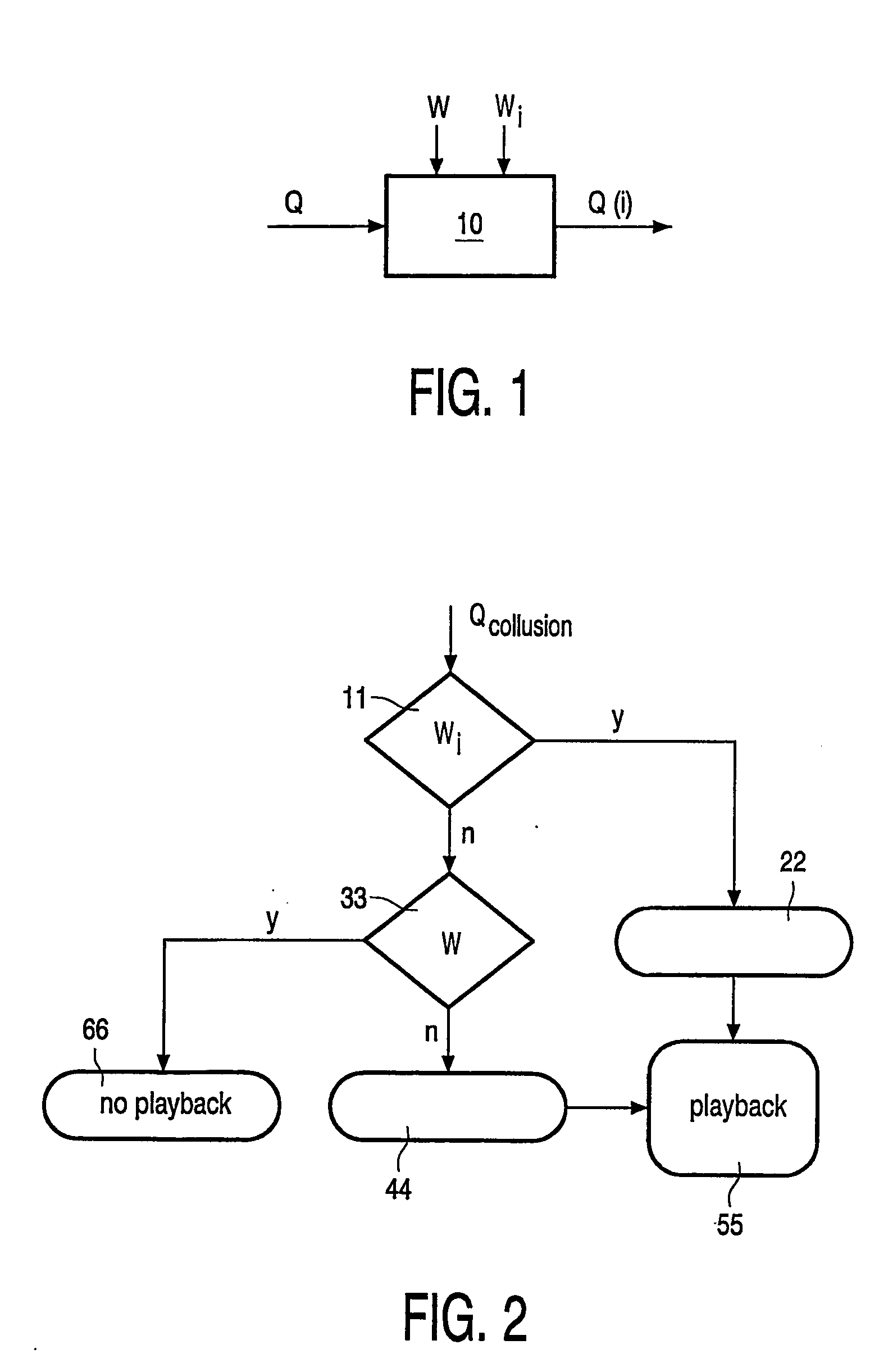
Watermark embedding is often used to identify multiple copies (Qi) of the same content (Q). Each copy (Qi) is provided with a different private watermark (Wi) which, for example, identifies the player on which that copy may be reproduced. Private watermarks can be hacked. Averaging two or more watermarked copies may cause any of the private watermarks to become undetectable. The watermark embedder (10) in accordance with the invention embeds a global (fixed) watermark (W) in addition to the private watermark (Wi). The global watermark is the same in each copy and therefore remains detectable. Its presence indicates that a private watermark shall be present as well. It can be used in a protocol like: no playback allowed if the global watermark is present and a private watermark is not found.
Owner:CIVOLUTION BV
High spread highly randomized generatable interleavers
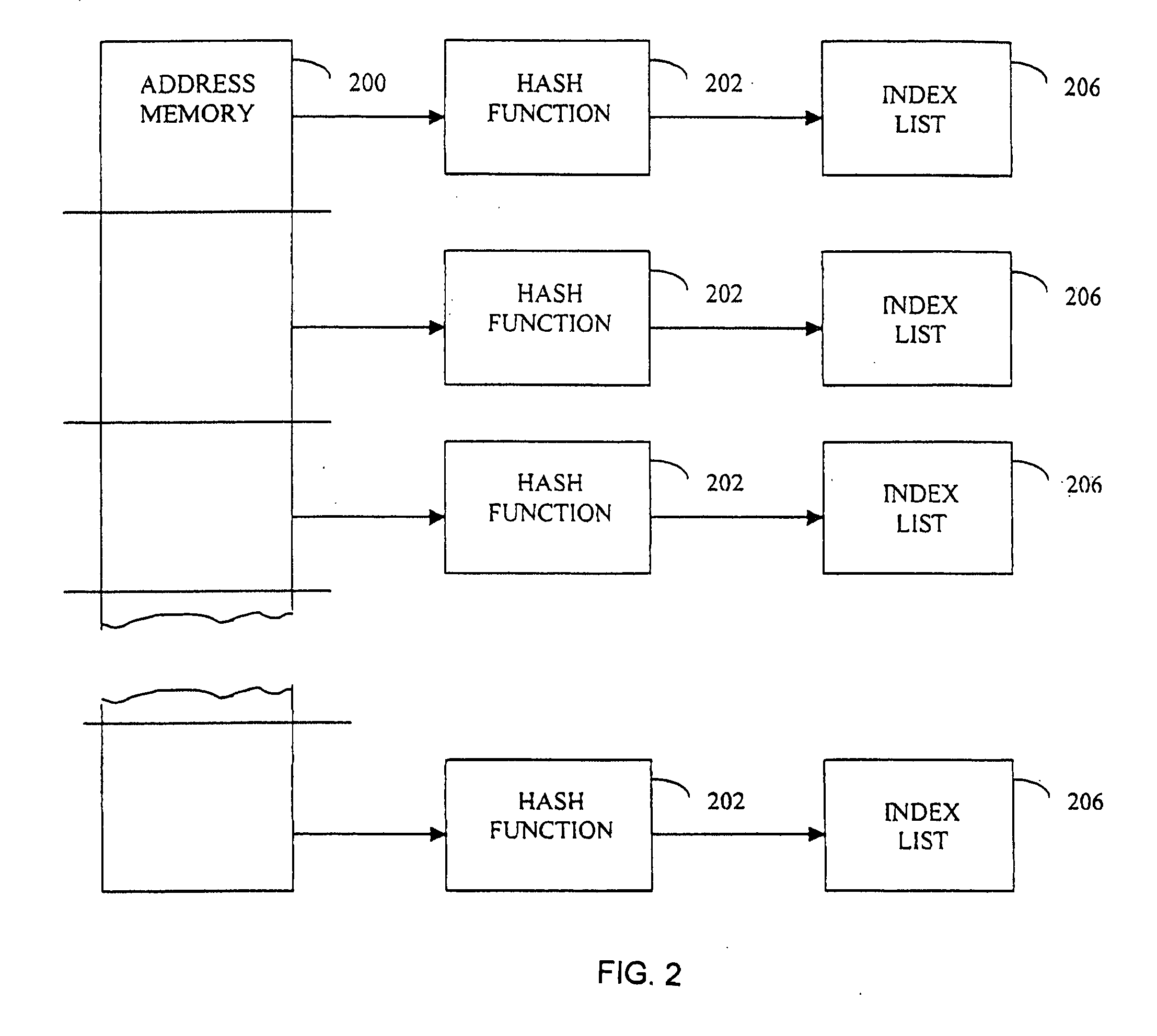
InactiveUS20070234180A1Minimize negative impactIncrease the number ofOther decoding techniquesCode conversionCommunications systemTheoretical computer science
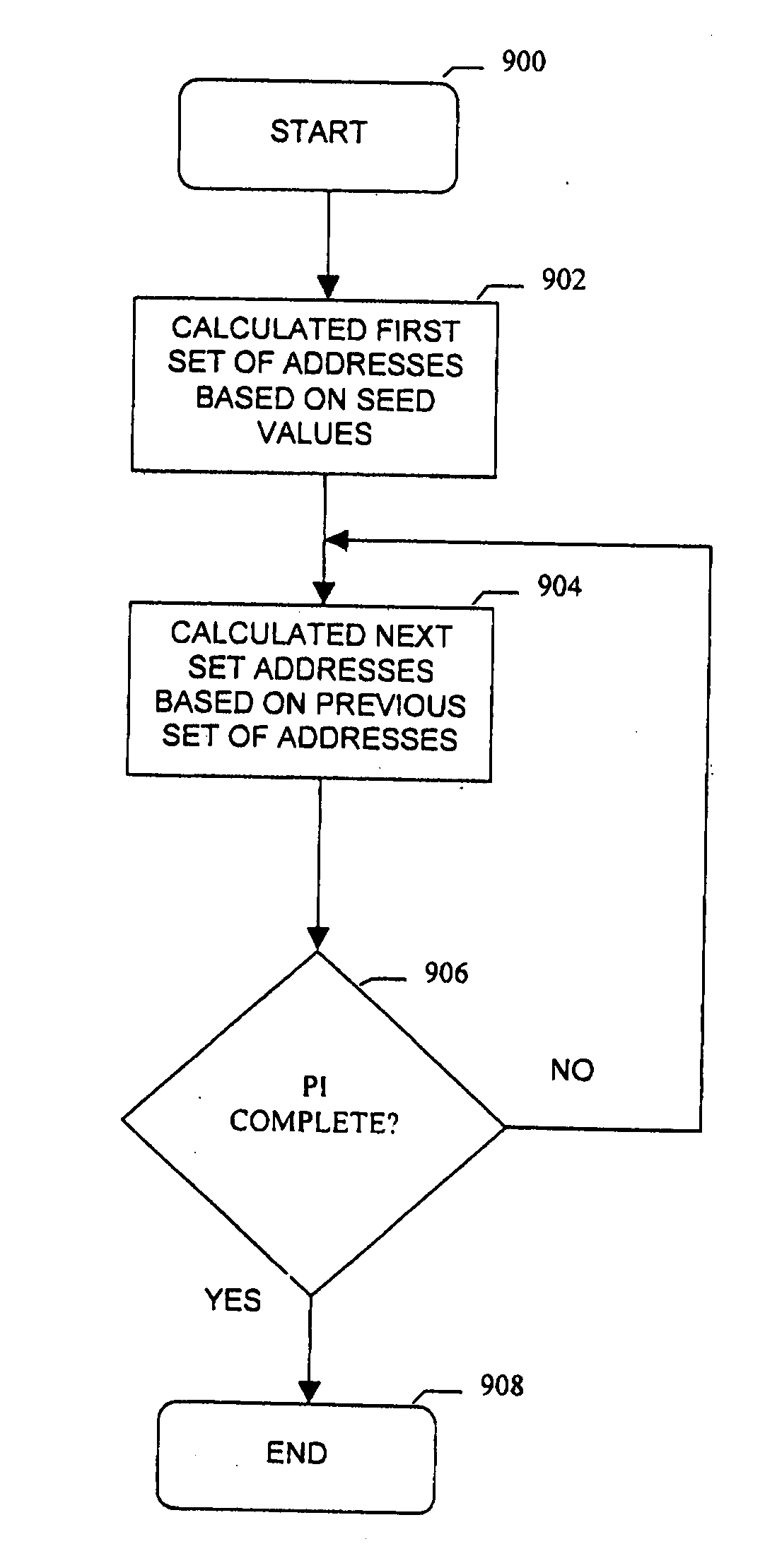
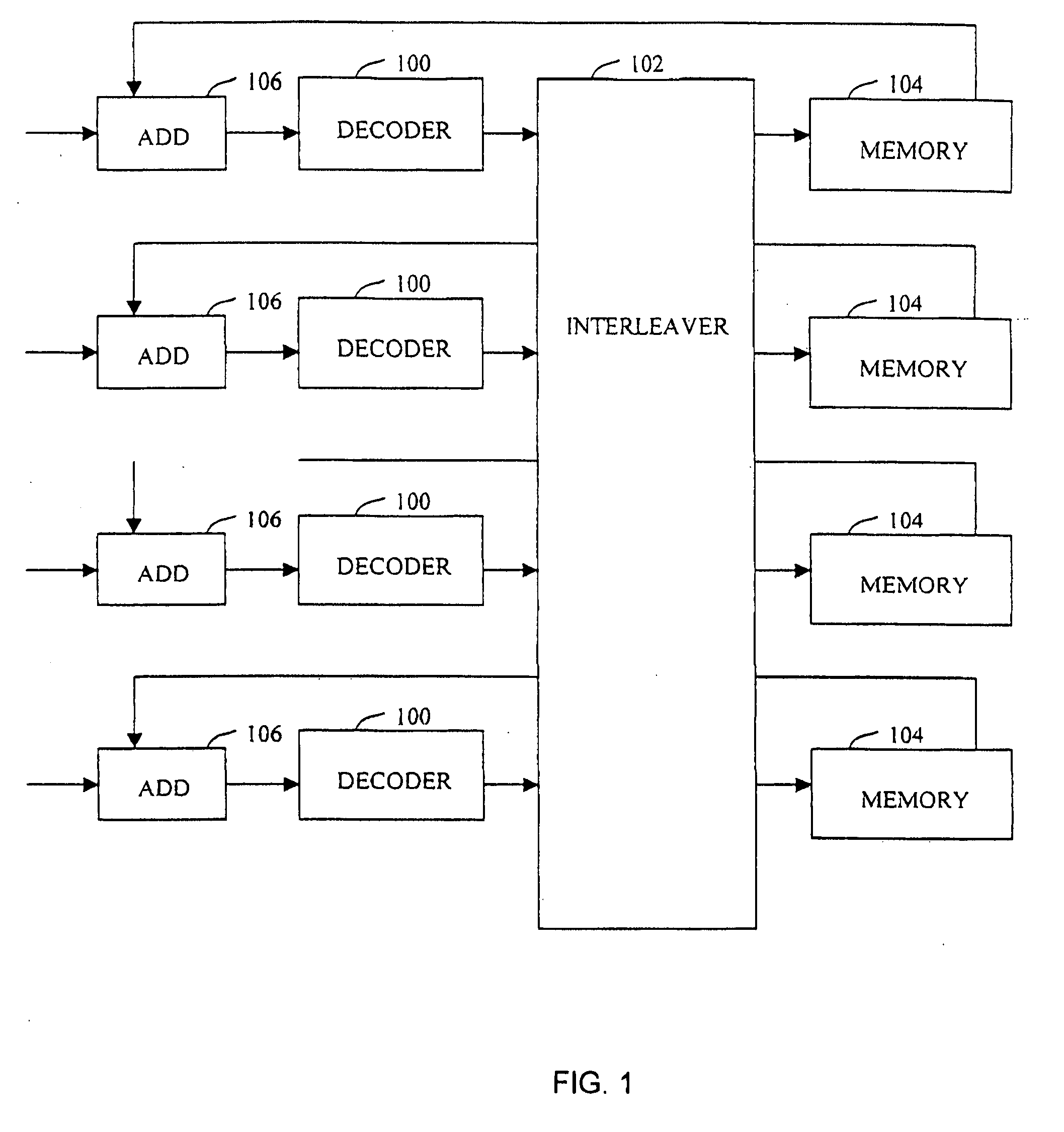
Methods and apparatus for generating and performing digital communications using a randomized generatable interleaver. In accordance with one exemplary embodiment of the invention, a pseudo random interleaver of size n*m with excellent randomness and spread properties may be generated from a set of seed values. The interleaver of size N=n*m is defined by dividing the N possible address in the interleaver (0-N−1) into n subsets. The subsets are preferably generatable from a single value within the subset either using an algorithm or a memory based lookup table. The set of n seeds comprises one value selected from each subset. An improved communication system incorporating the aforementioned interleaver and using turbo codes or other concatenated coding systems is also disclosed.
Owner:AVAGO TECH INT SALES PTE LTD
Lossless data embedding
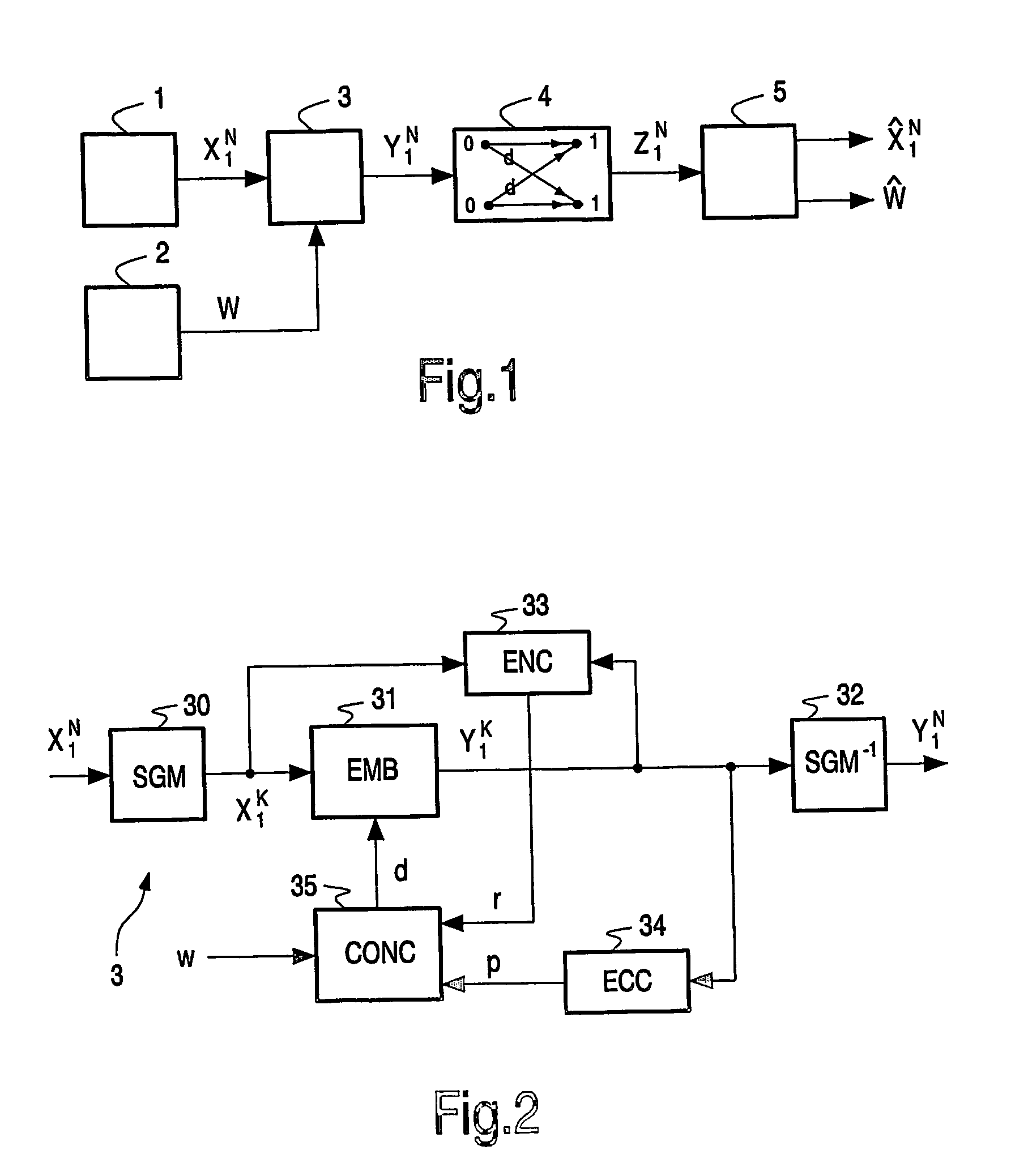
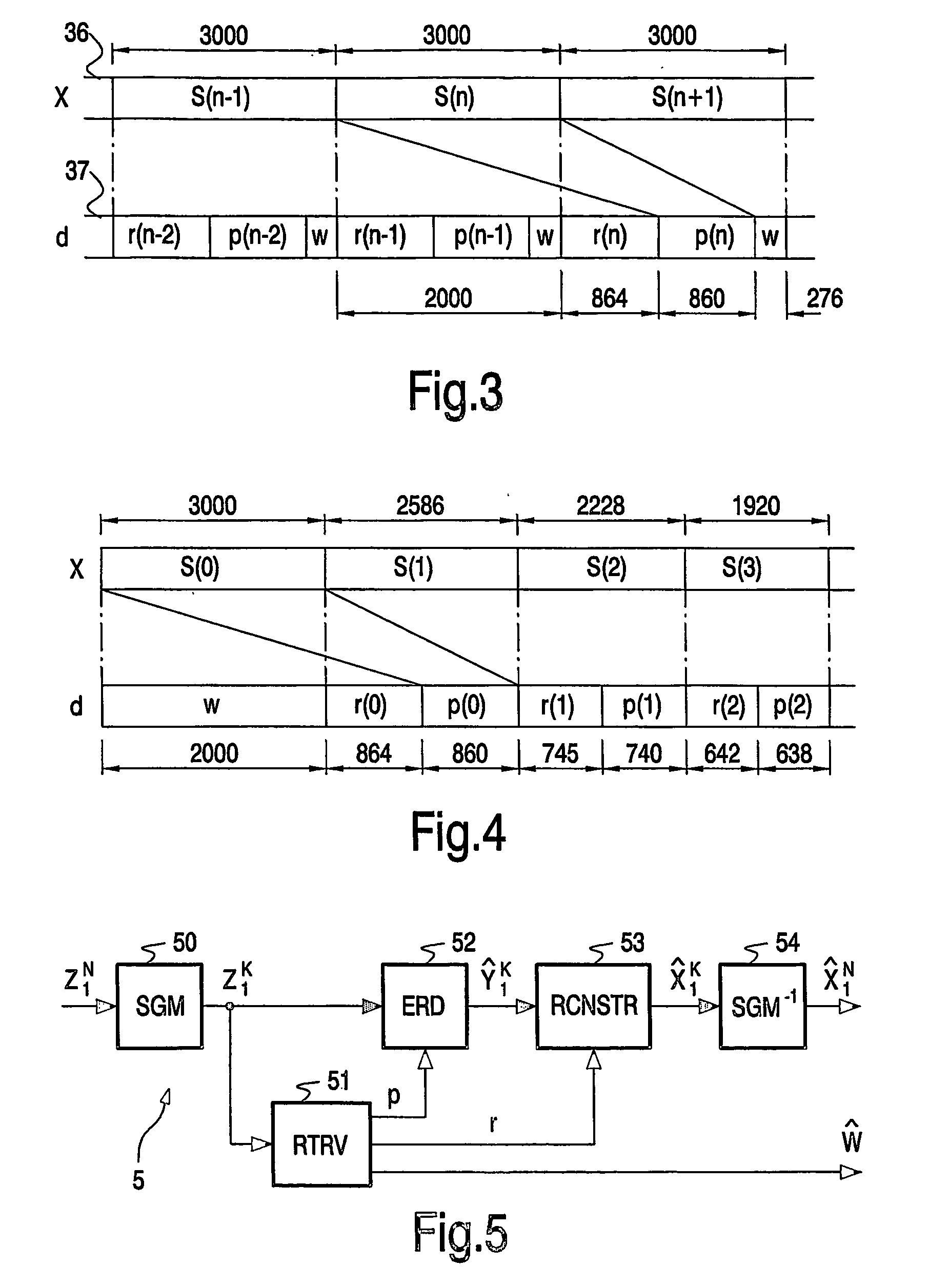
InactiveUS20060075240A1High embedding rateProcess compatibleUser identity/authority verificationCode conversionComputer scienceAncillary data
Many methods for reversible watermarking (embedding schemes that allow perfect reconstruction of the original host signal) are highly fragile in the sense that the slightest modification of watermarked content prohibits the recovery of both the original signal as well as the embedded auxiliary data. In order to obtain robustness against transmission or channel errors, the embedding method according to the invention accommodates error correction data in a portion of the data embedding capacity. In an advantageous embodiment, the host signal (36) is segmented in segments, and error correction data (p(n)) for a segment (S(n)) is accommodated in data (37) being embedded in a subsequent segment (S(n+1)) along with restoration data (r(n)) for reconstructing the host signal. The remaining portion of the embedding capacity is used for payload (w).
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
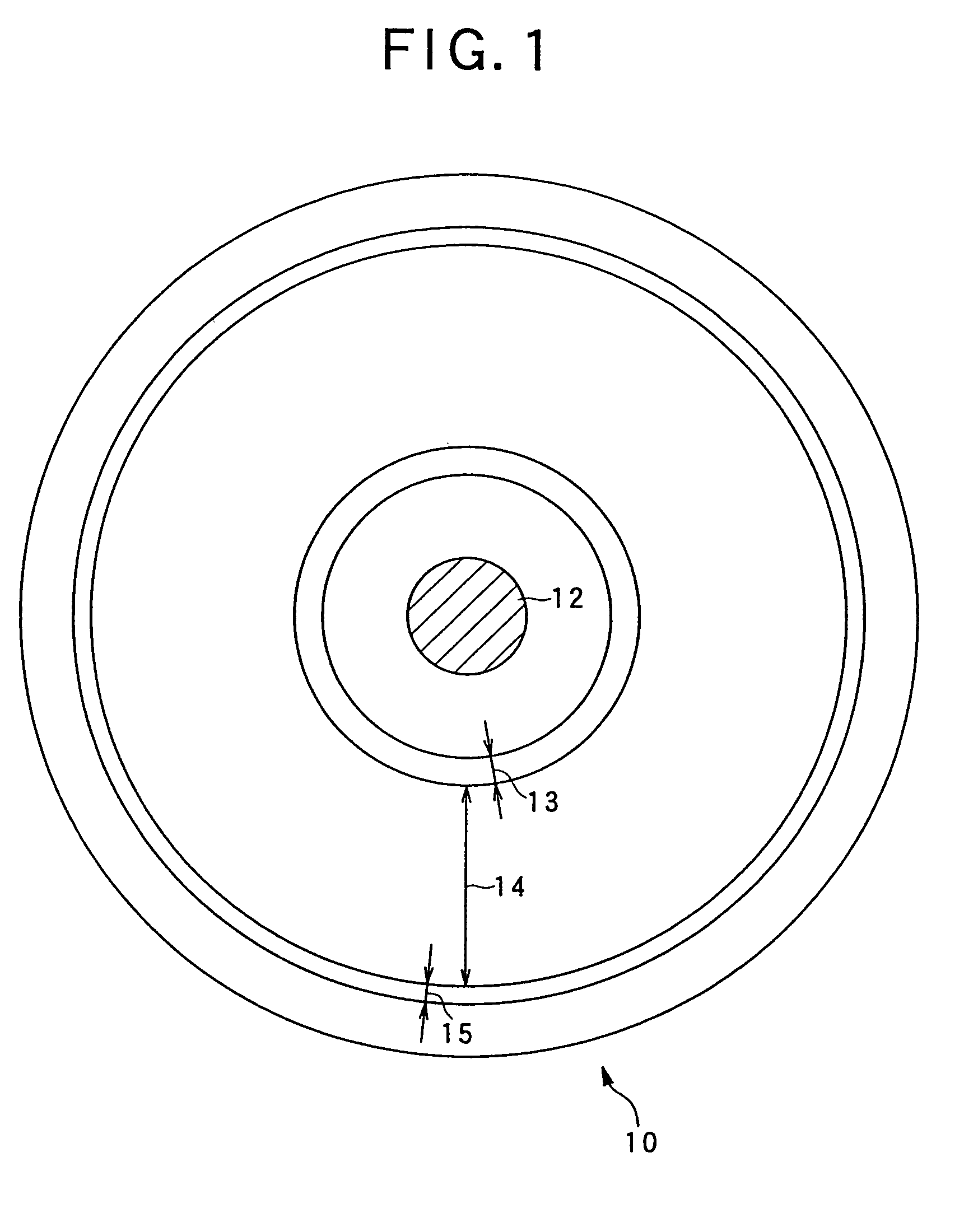
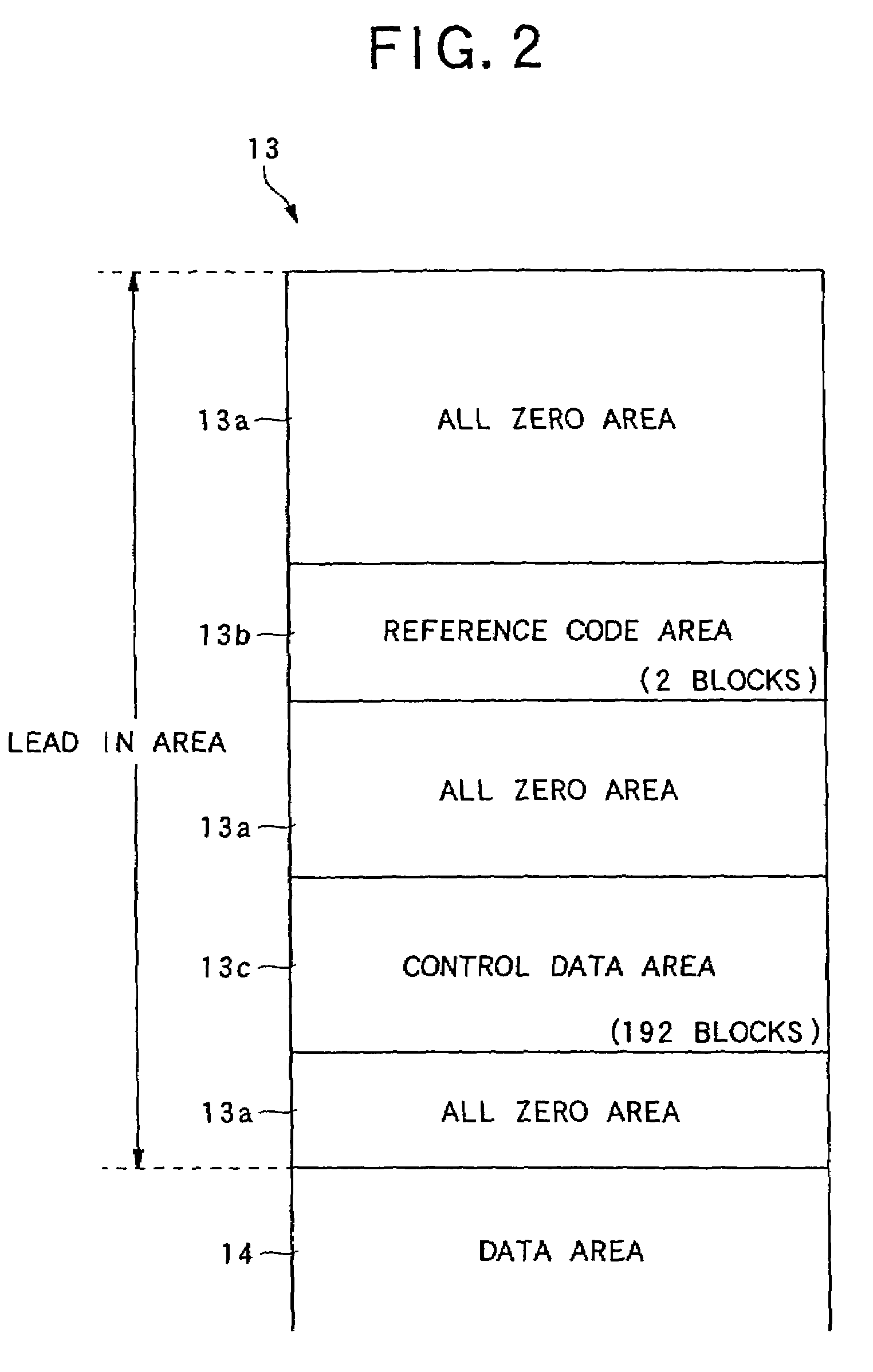
Apparatus for manufacturing information record medium, information record medium, information recording apparatus and information recording method
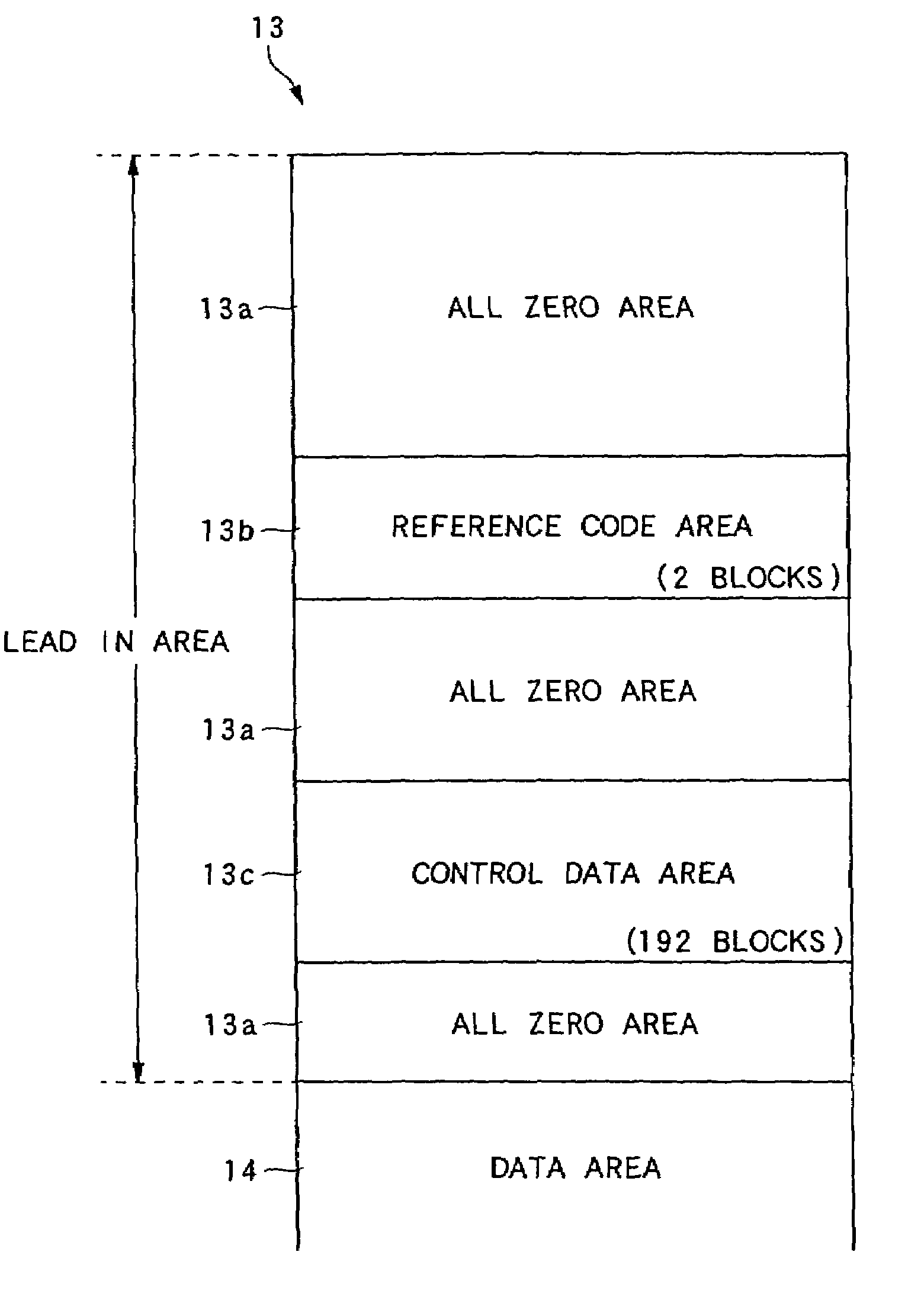
InactiveUS7206270B2Effective protectionTelevision system detailsOptical beam sourcesDatabaseRecording media
On an information record medium (10, 11), record information can be recorded one time or a plurality of times by a predetermined record format. An apparatus for manufacturing the information record medium by using a stamper (27, 28) is provided with an embossed pit array forming device (20 to 26, 50) for forming on the stamper as an embossed pit array, pre-record data (SFi) which is a predetermined data row to disable overwriting on the record information in a pre-record area, which is set in advance in a range including an area (13c) assigned to information required to control a reproduction of the record information, which is recorded by the predetermined record format.
Owner:PIONEER CORP
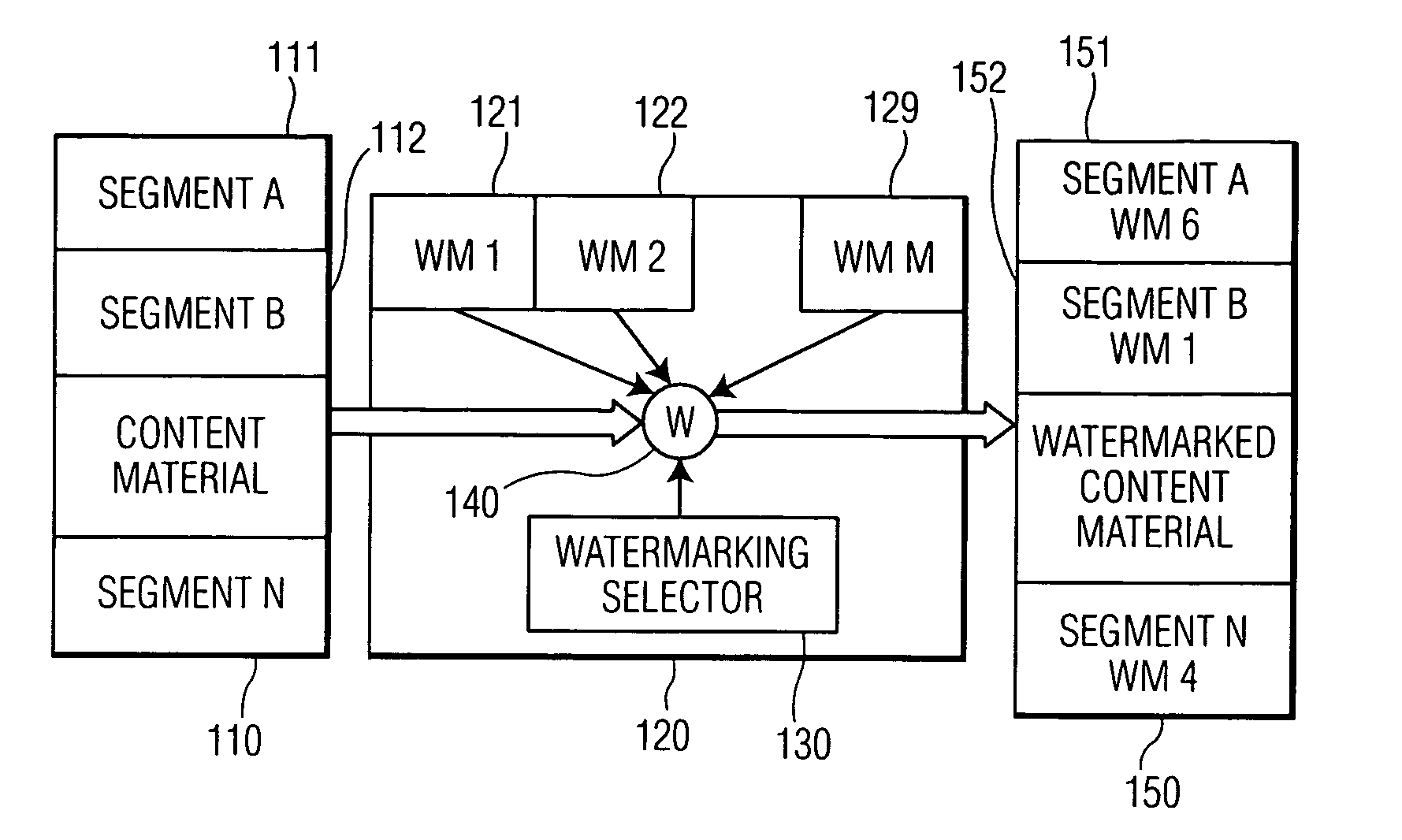
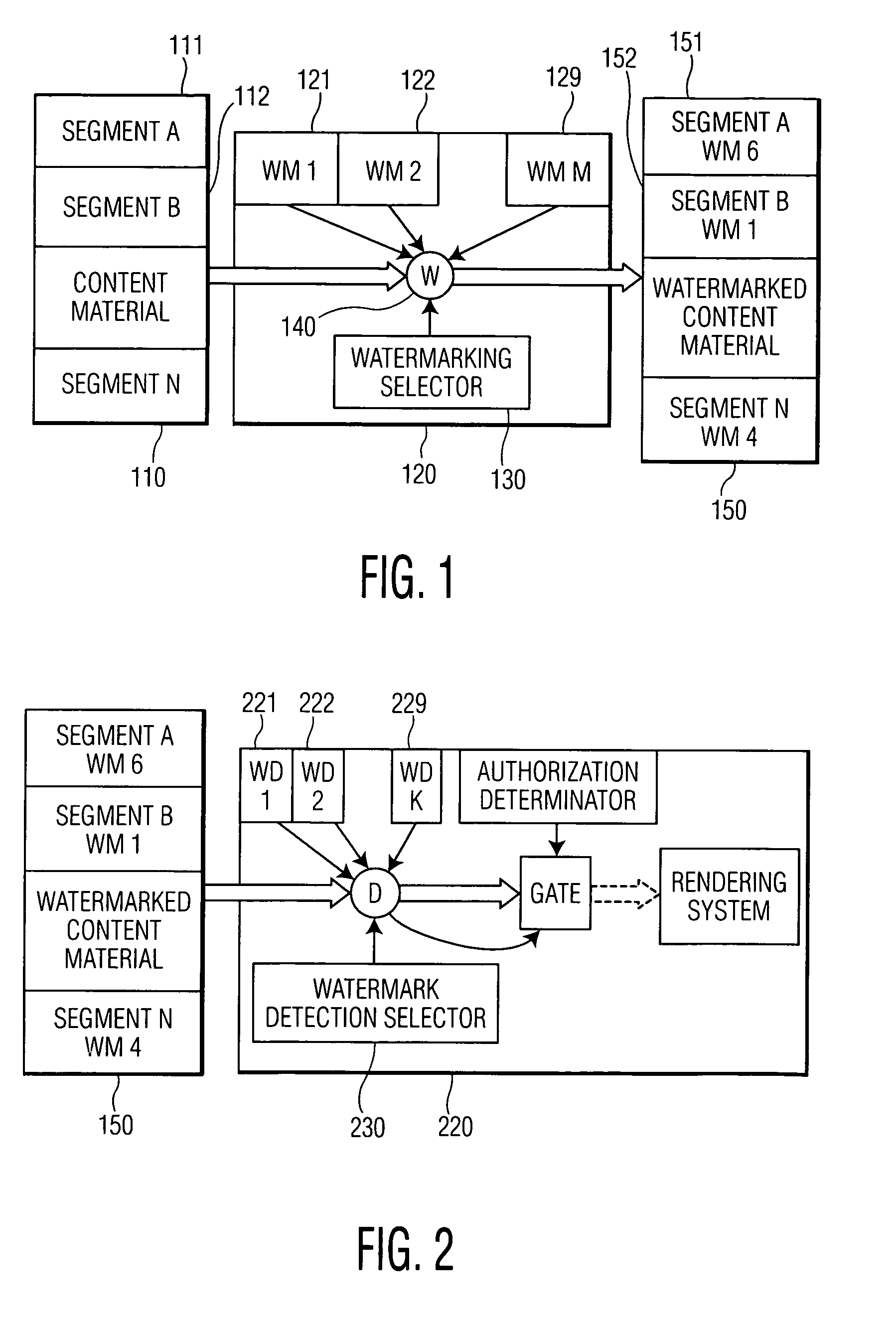
Using multiple watermarks to protect content material
InactiveUS7398395B2Watermarking processUser identity/authority verificationSpeech analysisComputer security
Content material is protected with a variety of watermarking processes. Different subsets of the protected content material are submitted to different watermarking processes. At the rendering device, a watermark detector is configured to detect one or more different watermarks. Only if the particular watermark(s) that the rendering device is configured to detect is removed from the protected content material will the rendering device permit the rendering of the protected material. If the particular watermark(s) that the rendering device is configured to detect is unpredictable, or if the particular segment that is protected by a particular watermark is undetectable, a wholesale removal of specific watermarks from the watermarked material will neither be efficient nor economically viable.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
Method and system for protecting digital media from illegal copying
InactiveUS20060259975A1Access to content can be preventedAvoid accessDigital data processing detailsCircuits to prevent unauthorised copying/reproductionDigital signatureCopying
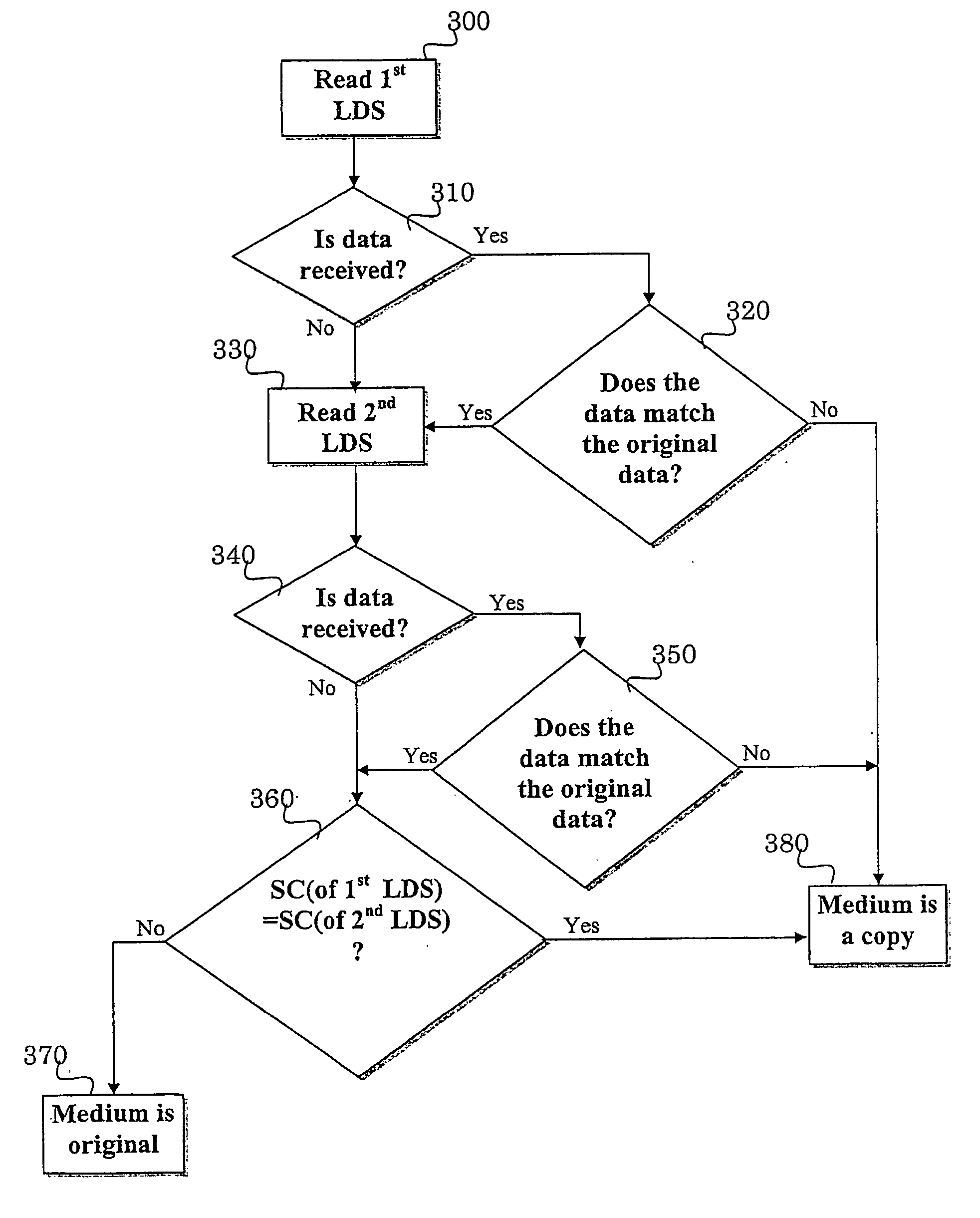
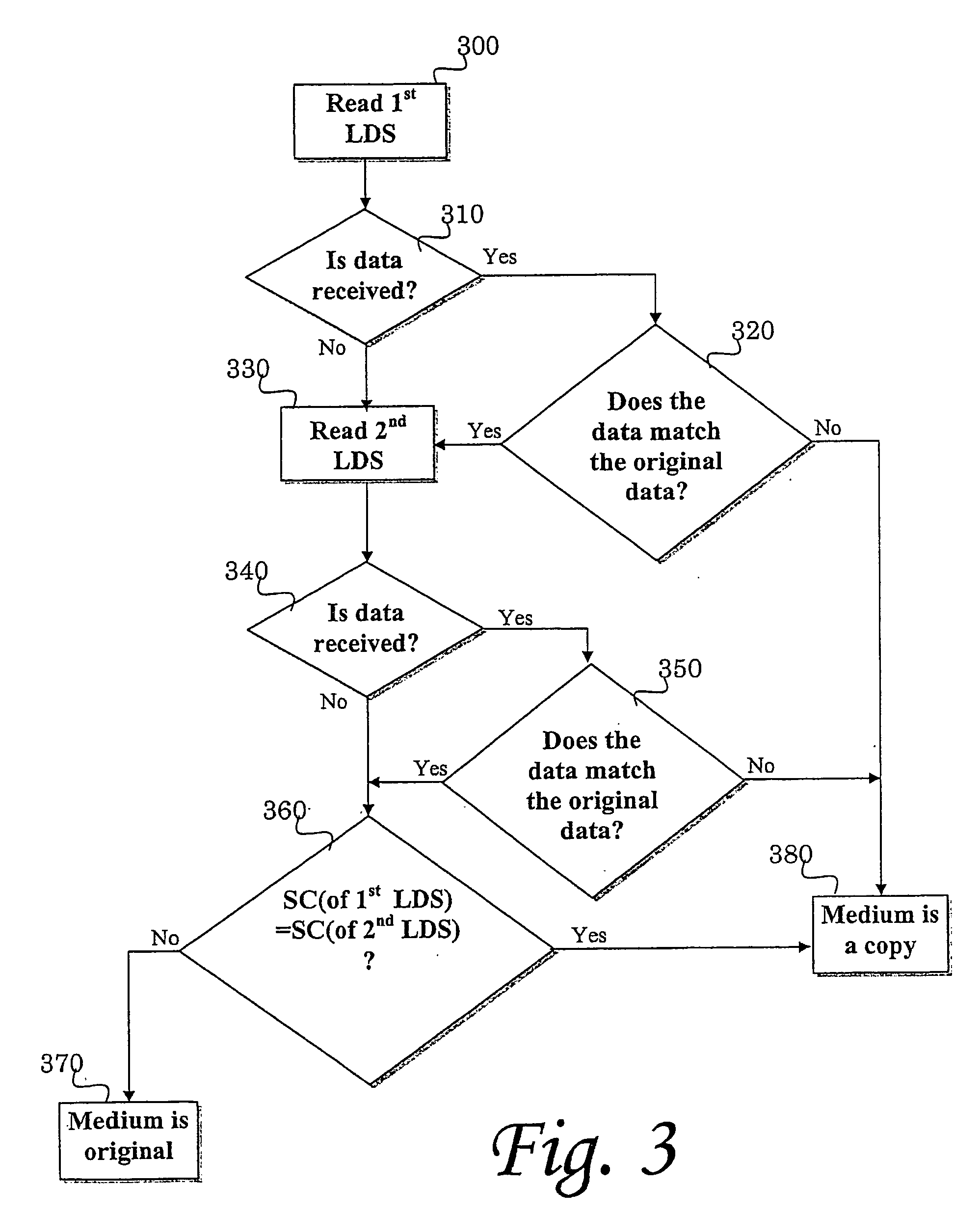
A method for protecting digital media from illegal copying by placing in predetermined locations of the digital media a set of Logical Digital Signatures (LDS), each of which causes retrieval of a different Sense Code (SC) and comprise a different signature, and utilizing an authentication module, which contains, or has access, to the signatures, for detecting the presence of the logical errors. The method comprises activating the authentication module whenever the content of the storage media is accessed, performing read operation of the locations wherein the LDSs are located, storing the Sense Code (SC) obtained from each read operation in a memory, and allowing access to the content of said storage media if information was retrieved following the LDS read operation and it matches the information that was originally stored, as accessible by the authentication module, and if different SCs were obtained from the reading operation of the different LDSs, otherwise preventing the access to the content of the storage media.
Owner:HEXALOCK
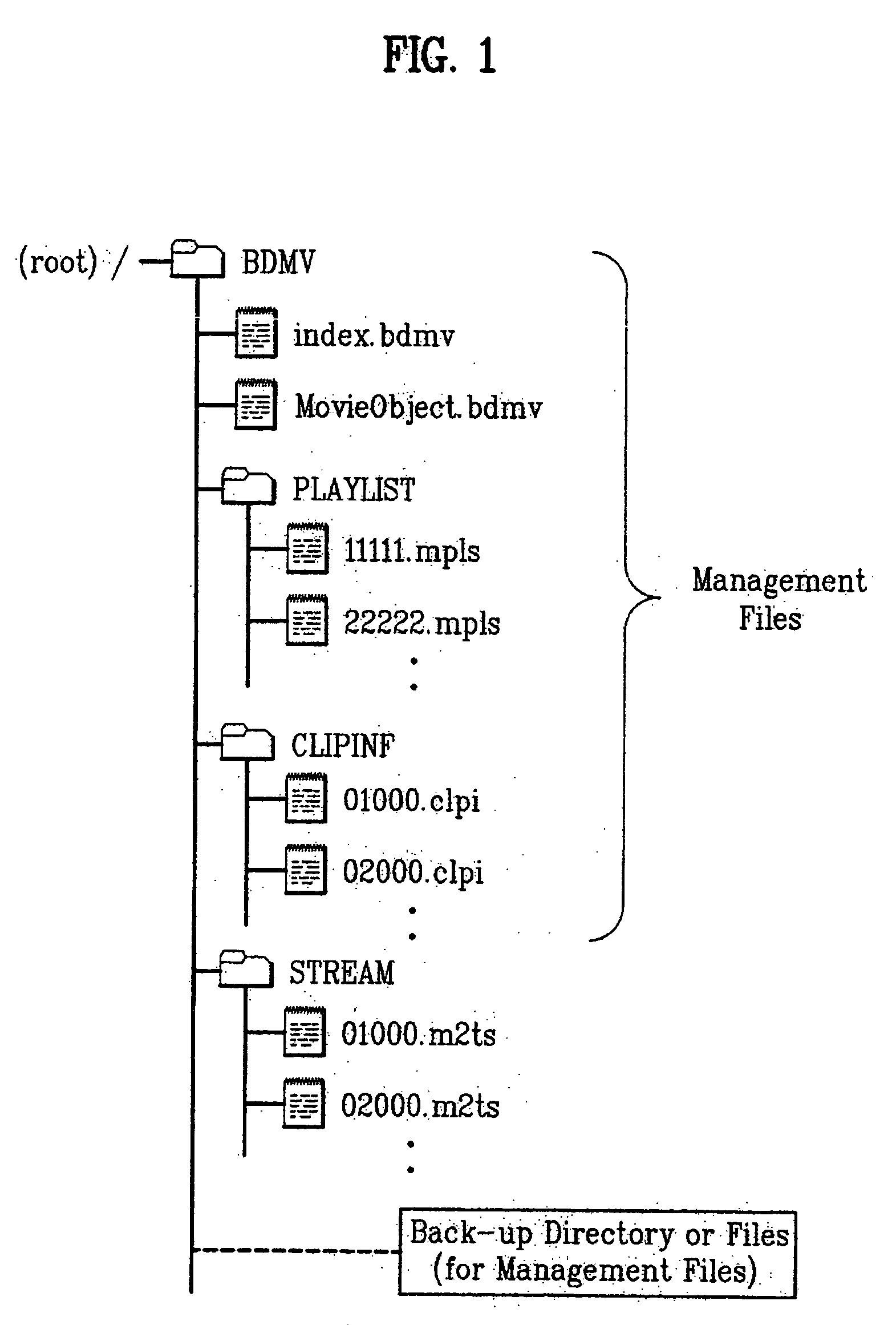
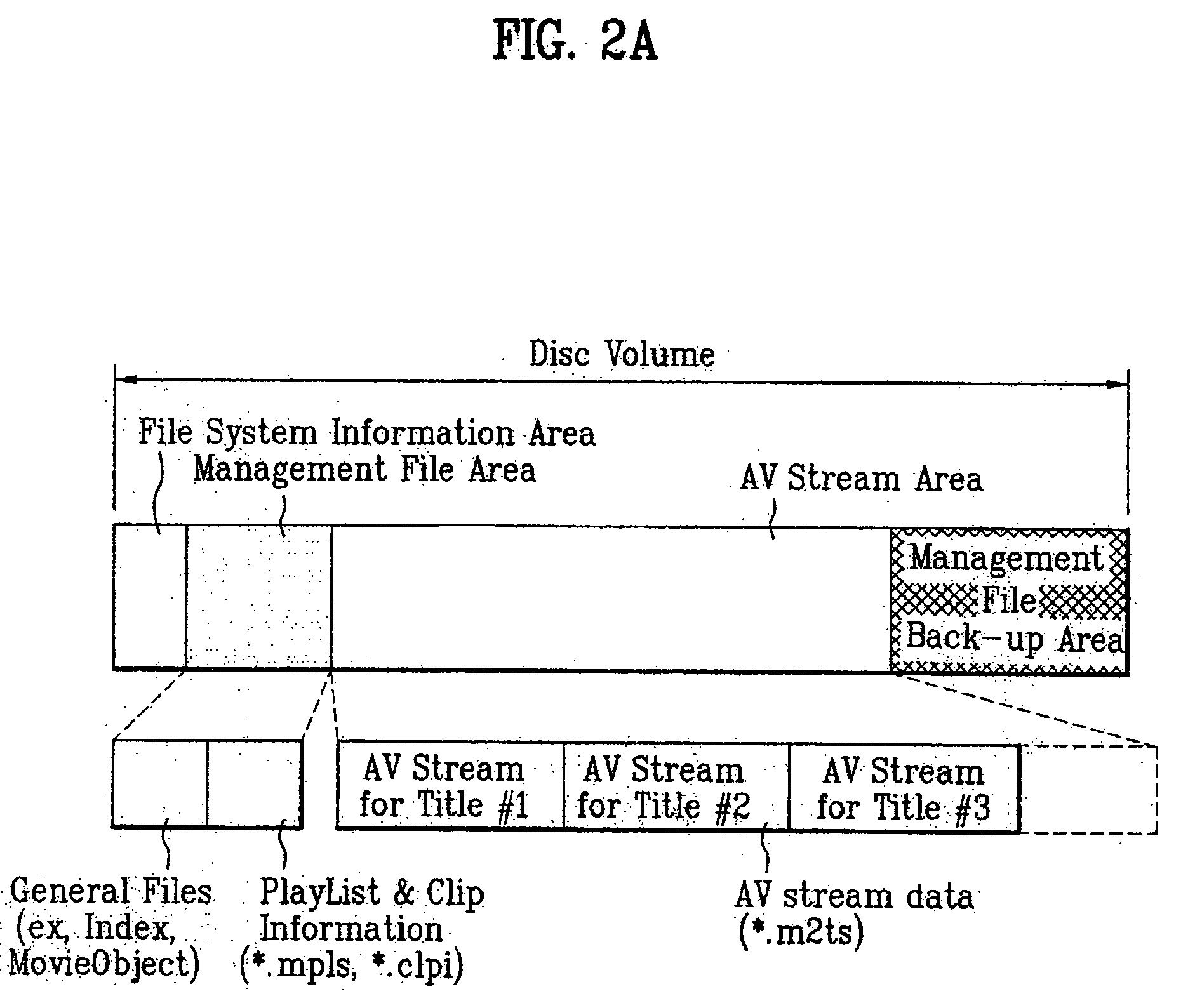
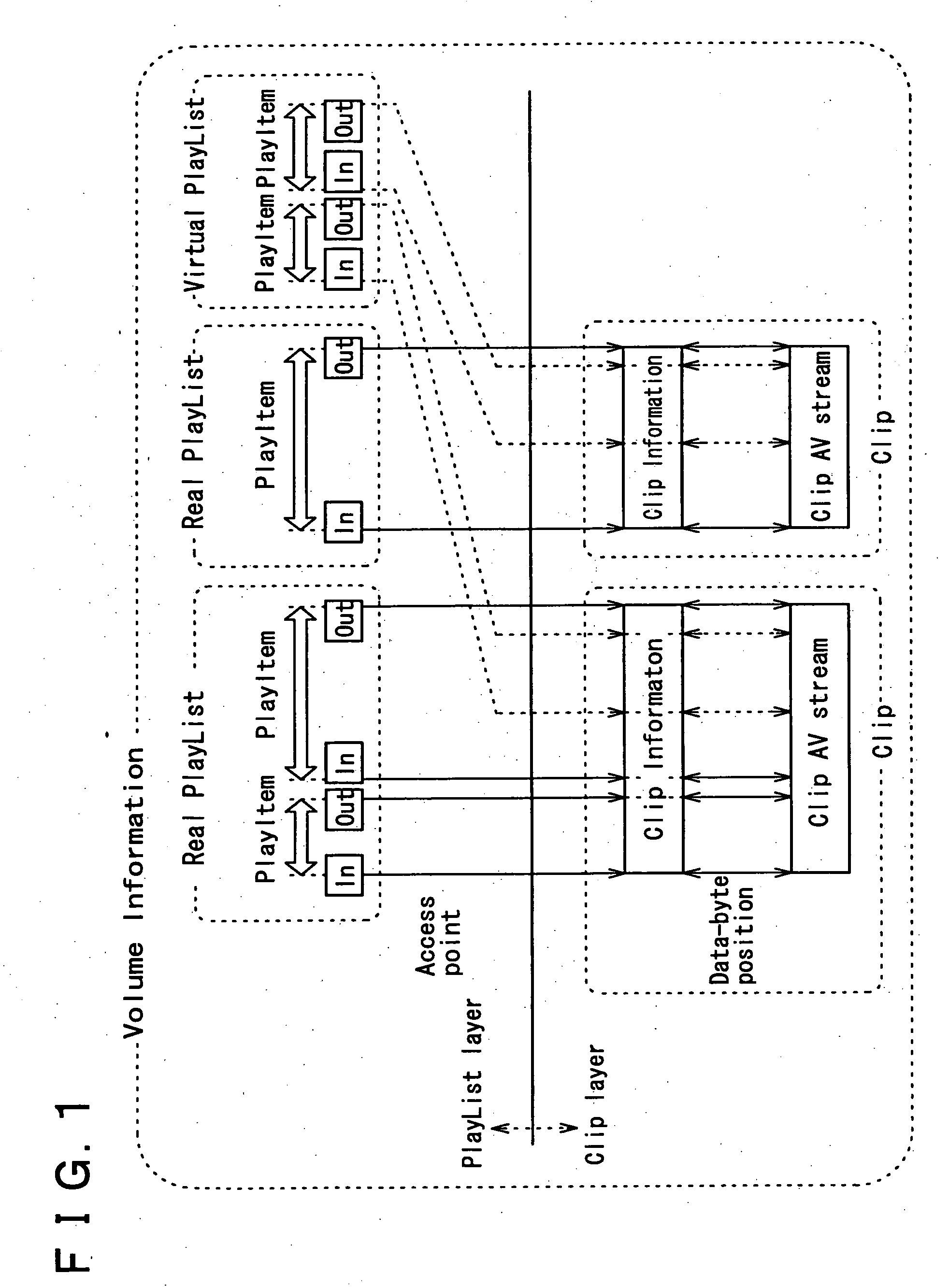
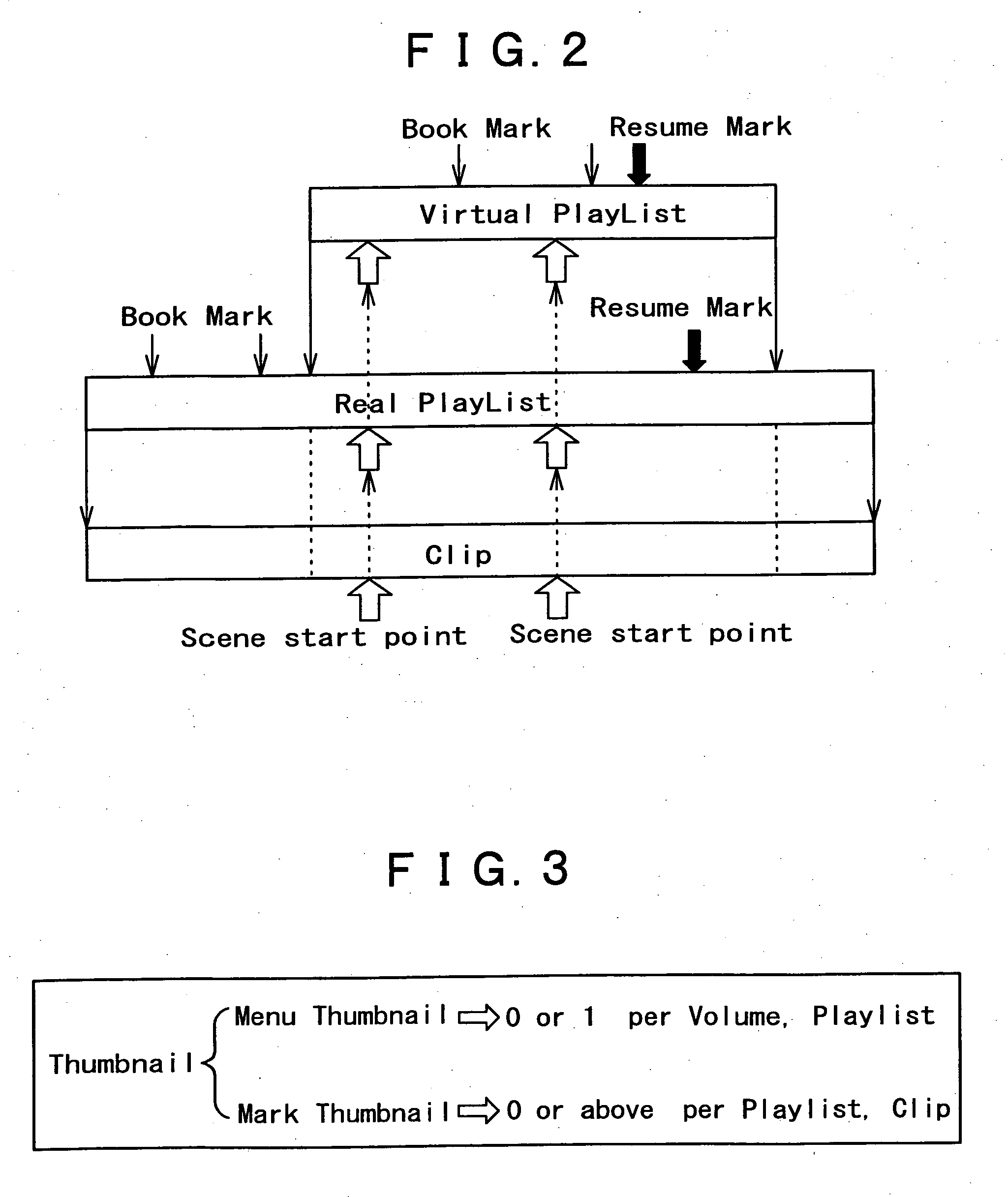
Recording medium having a data structure for backing up management files and recording and reproducing methods and apparatuses
InactiveUS20050175326A1Television system detailsStationary drilling machinesComputer hardwareRecording media
In the data structure for backing up management files, management files that manage reproduction of data from the recording medium are stored in a recording area as is a back-up directory. The back-up directory includes a copy of each management file as a respective back-up file.
Owner:LG ELECTRONICS INC
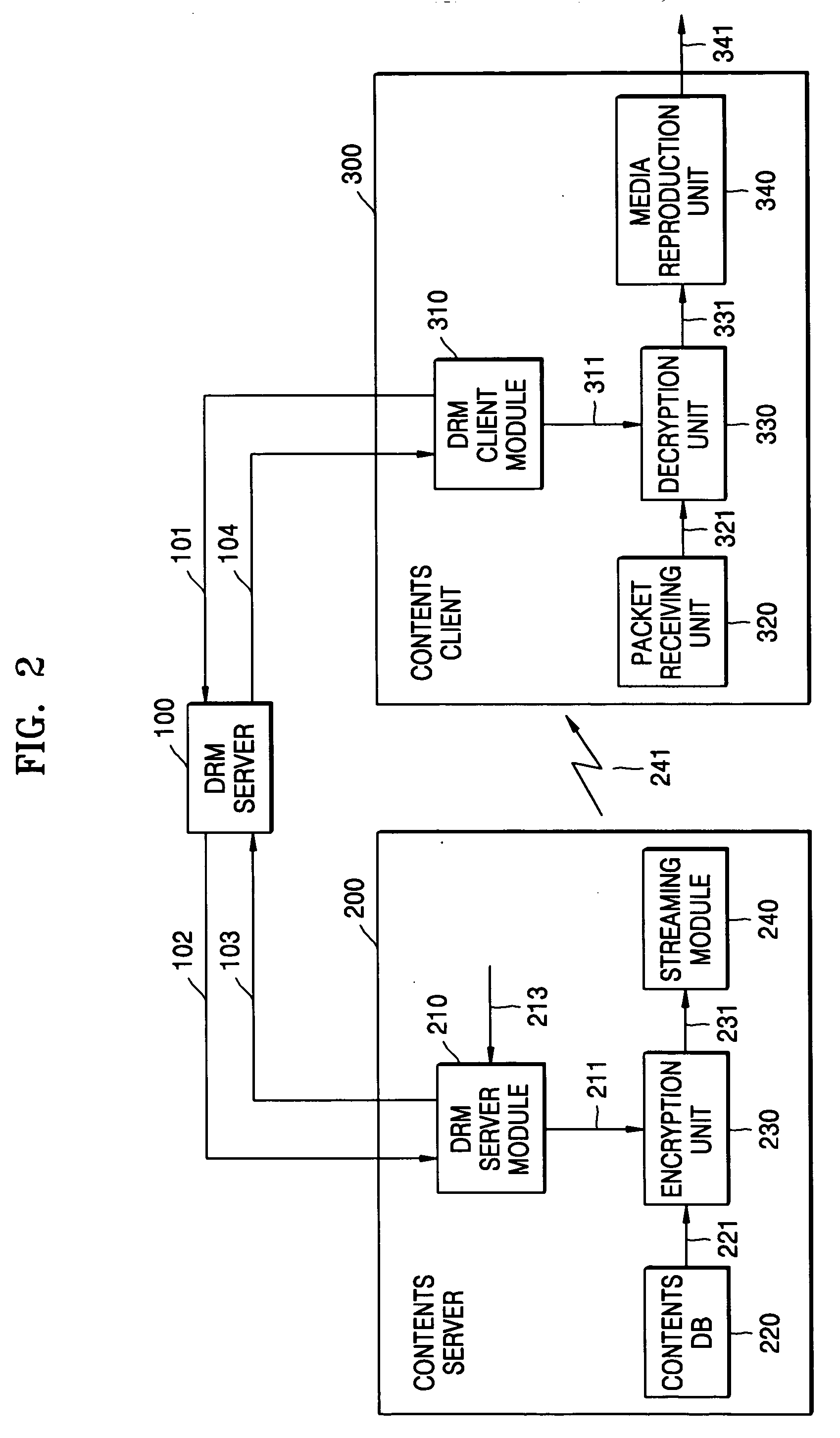
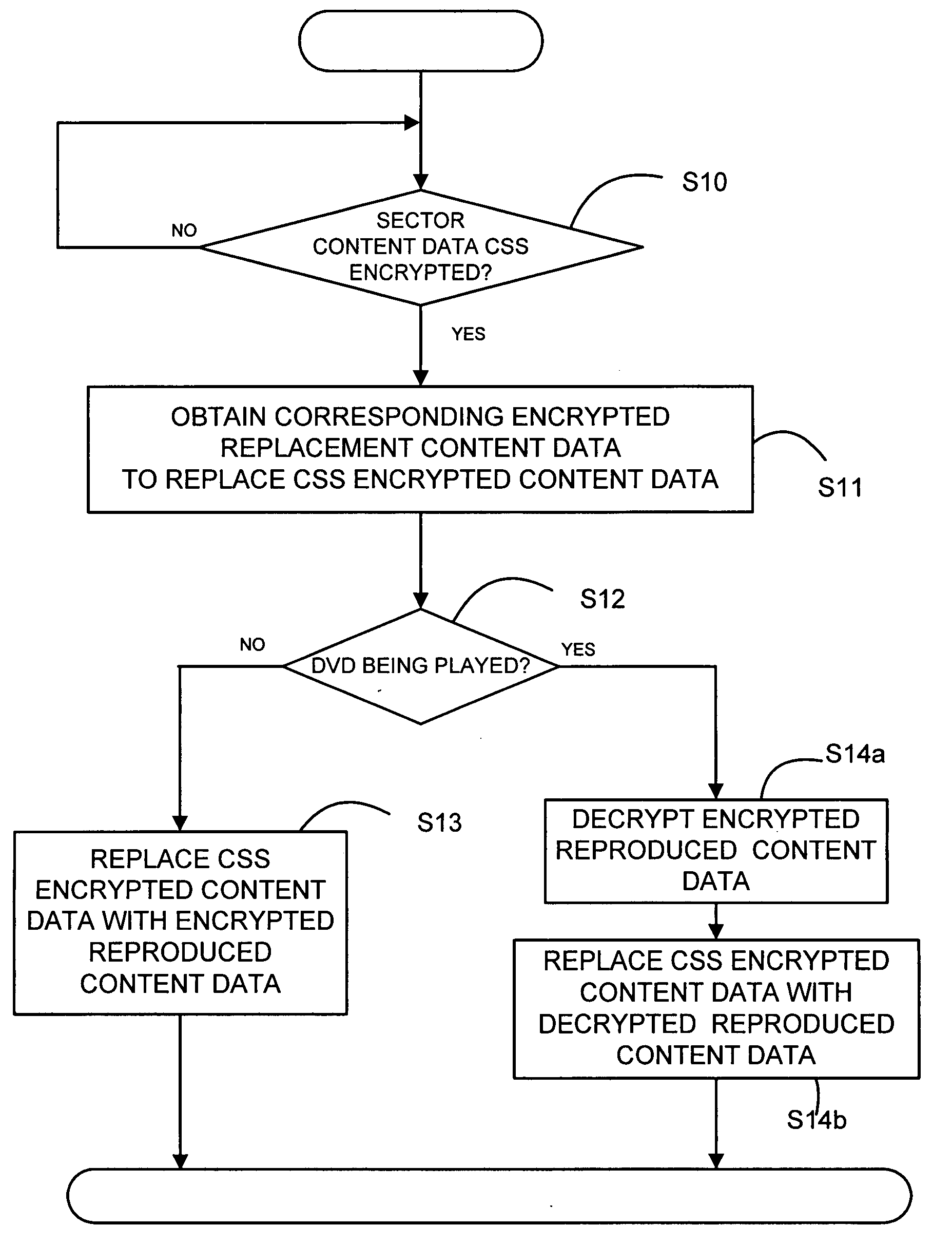
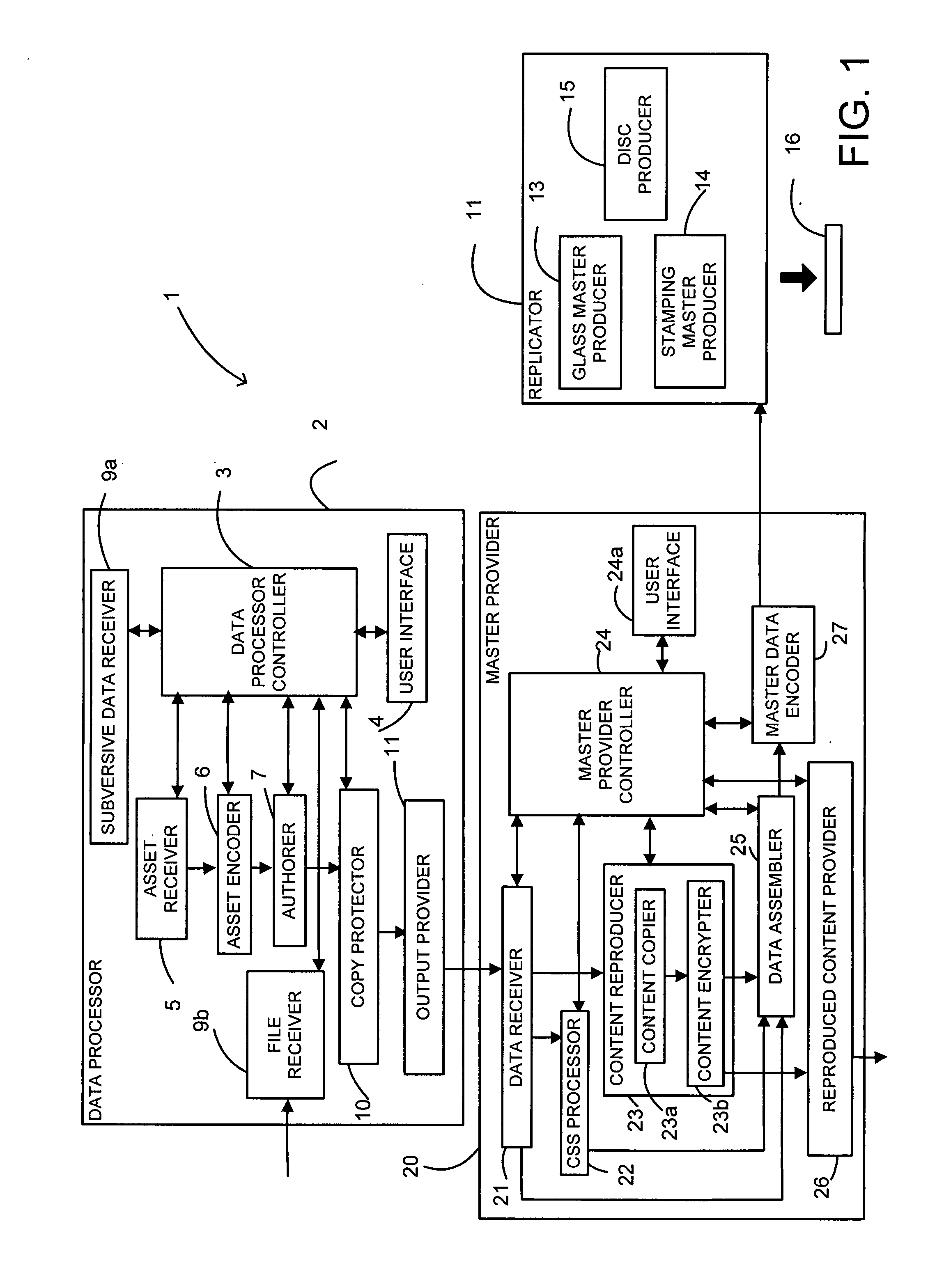
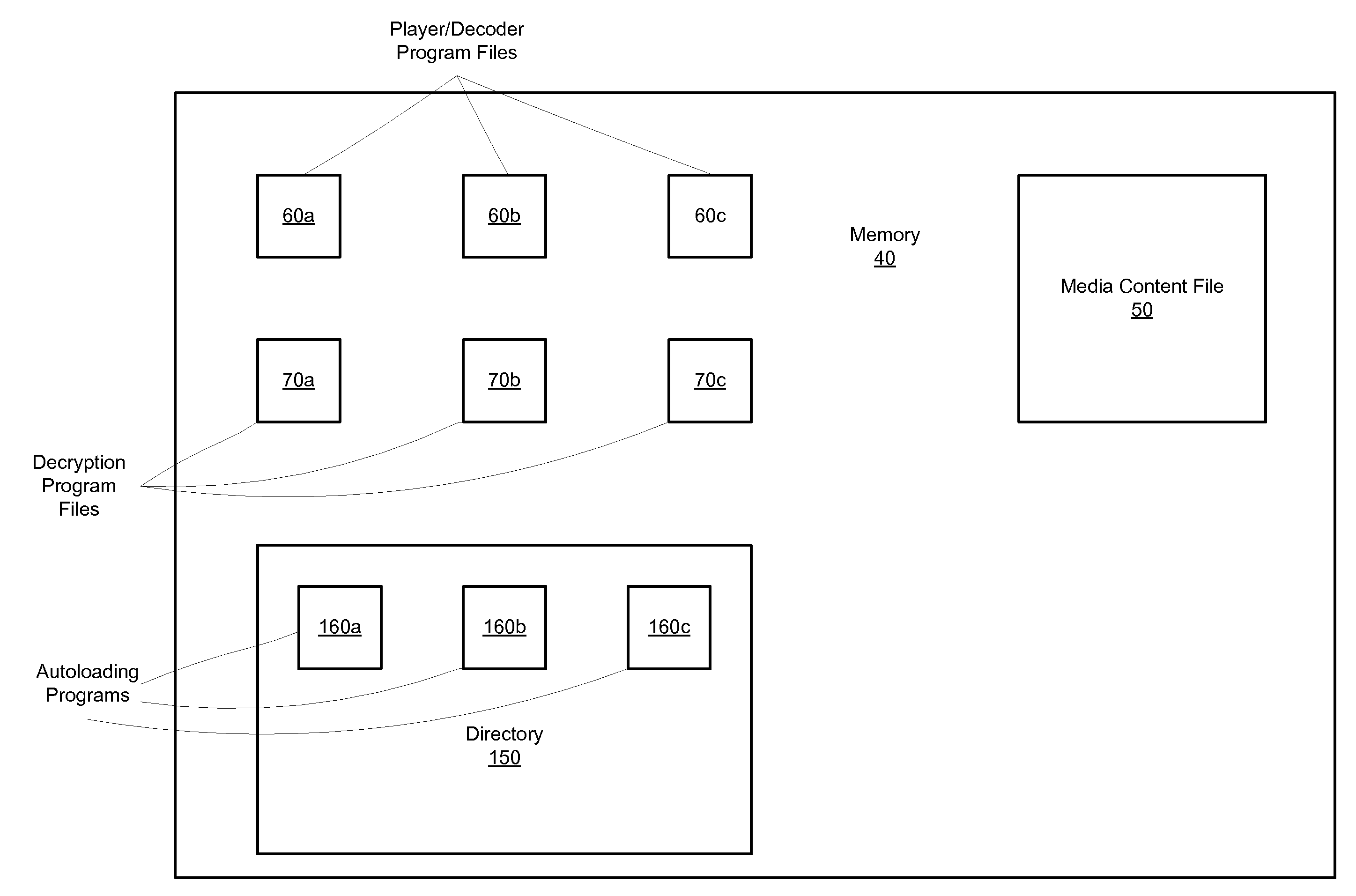
Apparatus for and a method of providing content data
ActiveUS20080247542A1Electronic editing digitised analogue information signalsUsing non-detectable carrier informationComputer hardwareEncryption
Apparatus and a method are described to enable reading apparatus to access content data of an optical disc such as a DVD where the content data carried by the DVD is encrypted by an encryption technique that requires a decryption key or keys. Reproduced content data corresponding to the encrypted content data is provided and this reproduced content data, at least some of which may be encrypted using a different technique, is made available for access by a reading apparatus. The reproduced content data may be stored on the same optical disc as the encrypted content data or at a different location, for example on a storage medium which may be coupled to the reading apparatus or at a location on a network that can be accessed by the reading apparatus.
Owner:ROVI SOLUTIONS CORP
Video information recording apparatus and method, video information reproducing apparatus and method, recording medium, and program
Owner:SONY CORP
Digital Content Distribution System and Method
InactiveUS20070286421A1Obtaining unauthorized accessPrevent unauthorized accessDigital data processing detailsCircuits to prevent unauthorised copying/reproductionContent distributionDigital content
A content distribution system and method which prevents unauthorized access to secured content such as movies and music. The system includes a source, a receiver, an authorized security device such as a conditional access module (CAM) for decrypting authorized content and an output device for outputting content. The system can also include a backend for managing accounts and system operations. One aspect of this invention is that the content data is derived from the Internet. The system allows for the verification of authorization to play secured content, the addition of watermarks to the secured content, the conversion of the secured content to a displayable form and the means for preventing output of the secured content.
Owner:GOOGLE LLC
Multimedia Storage Systems and Methods
ActiveUS20090169004A1Circuits to prevent unauthorised copying/reproductionRecord information storageElectronic systemsOperational system
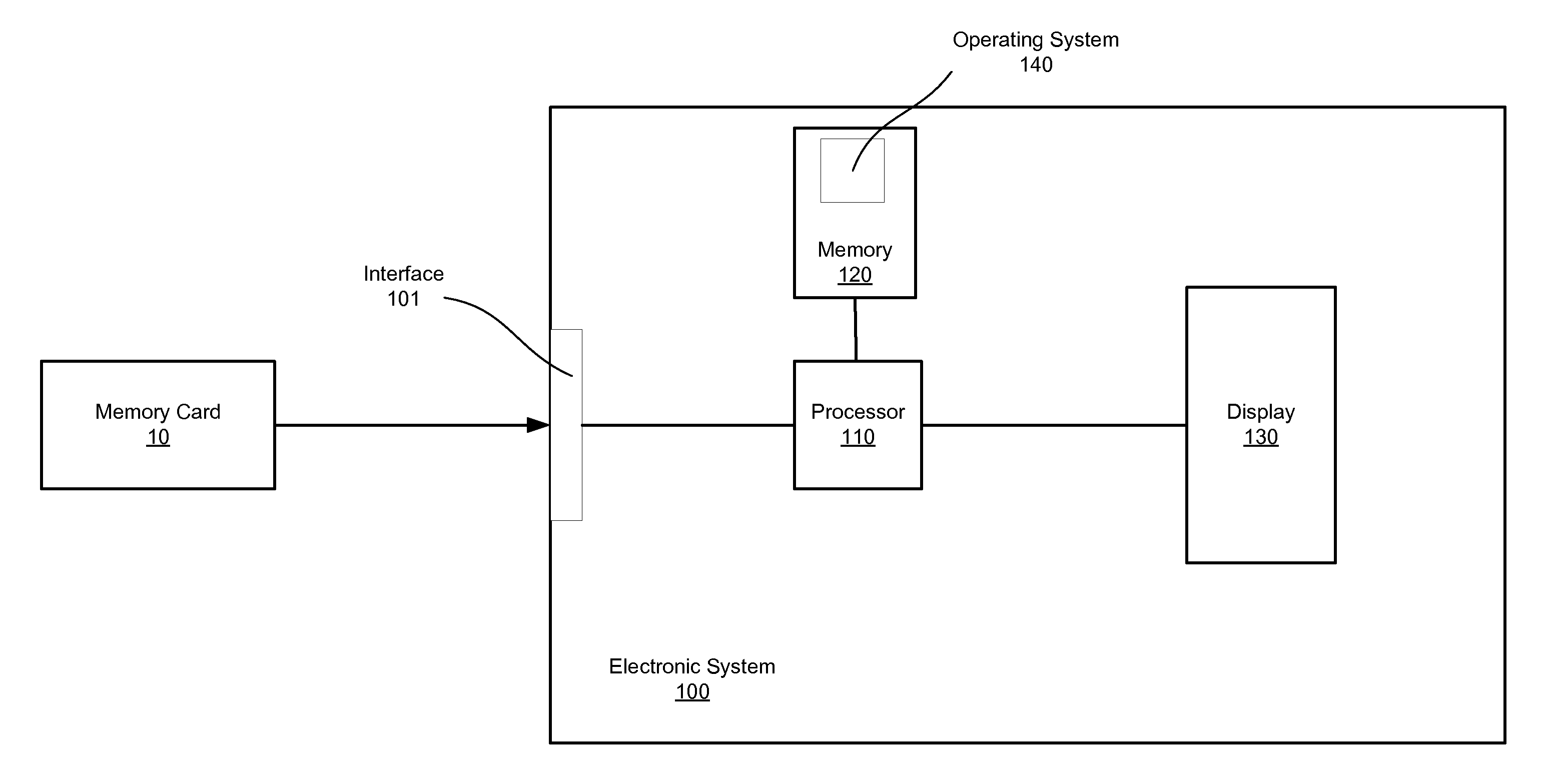
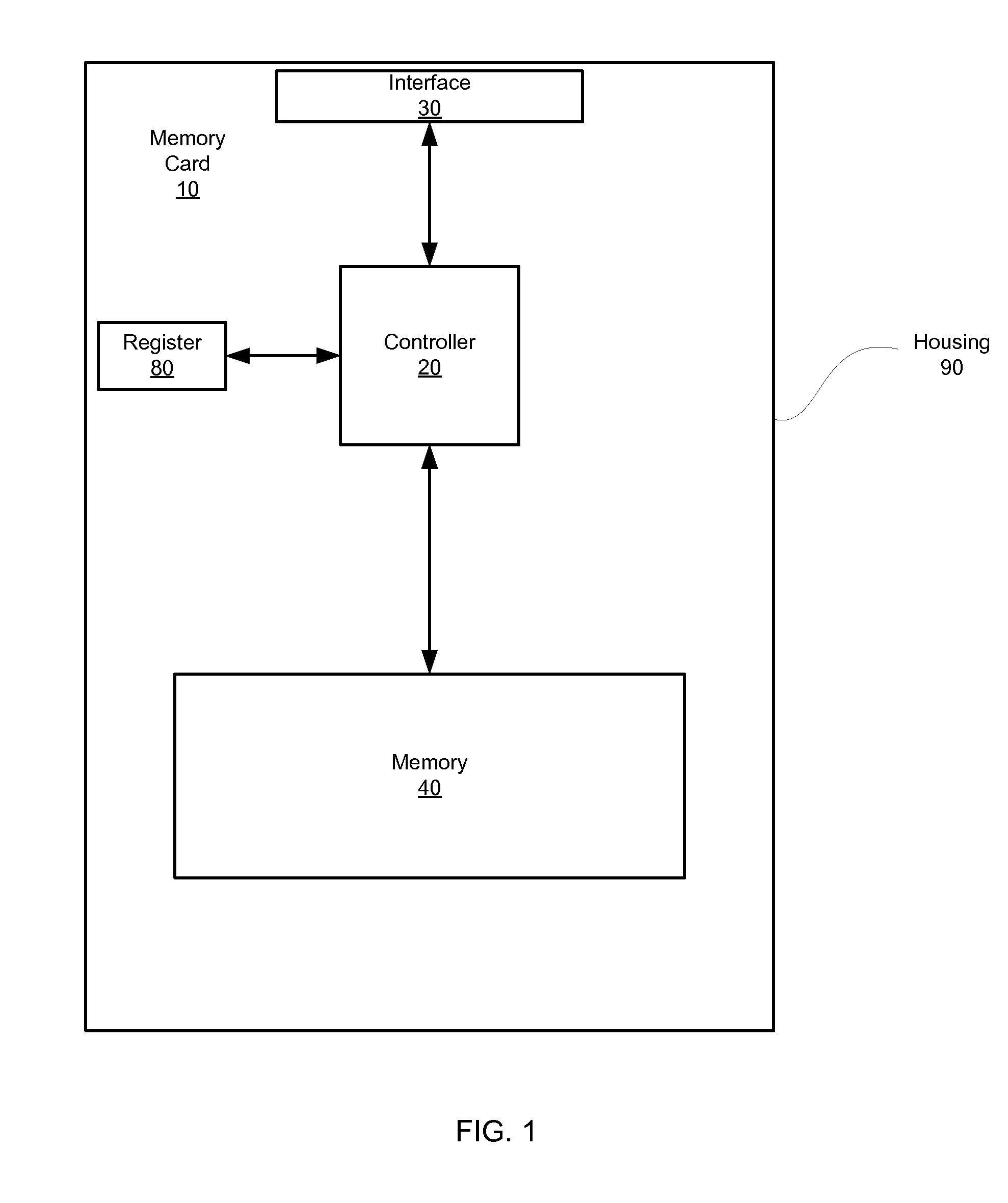
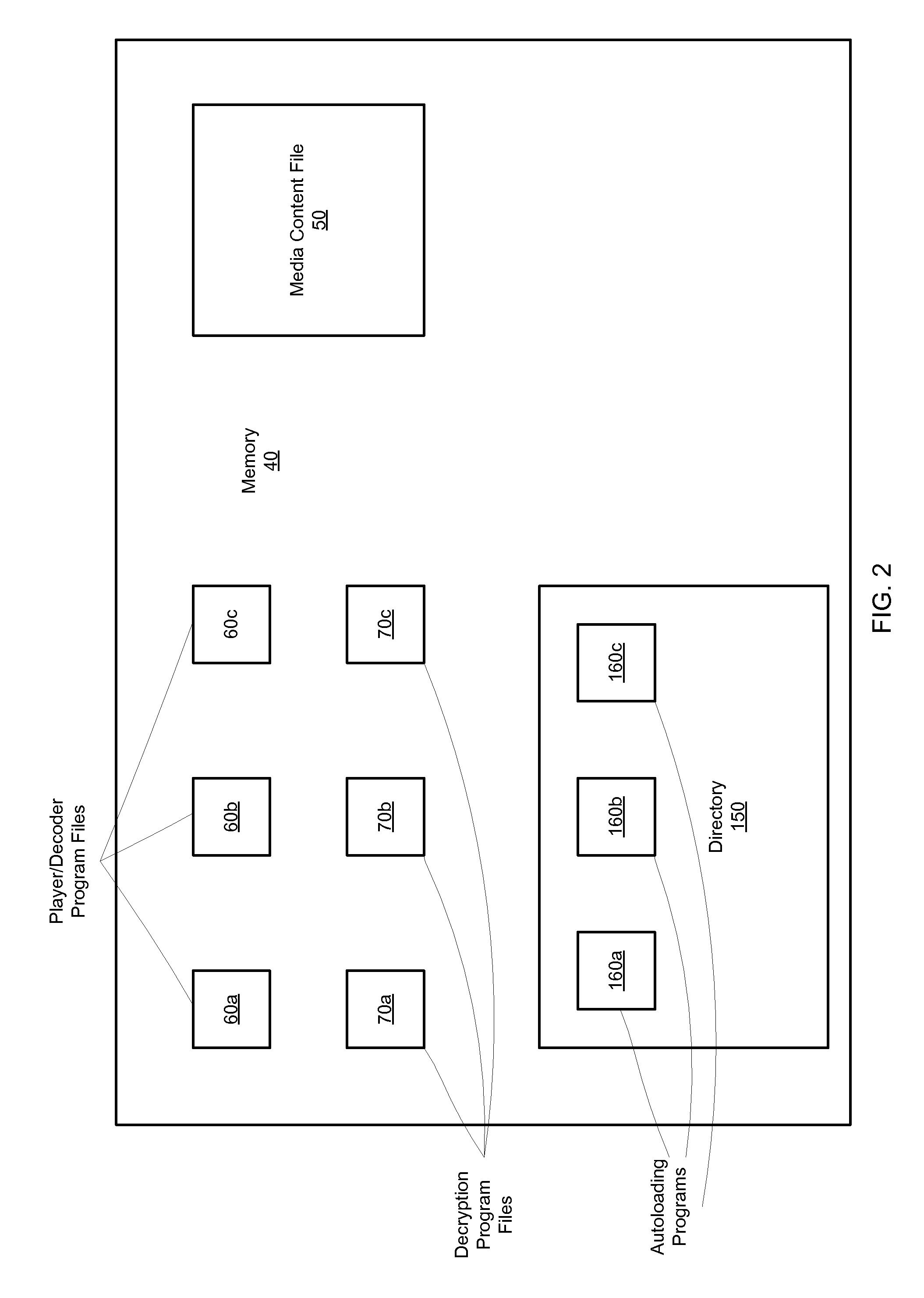
An article of manufacture includes a machine-readable medium that stores a multimedia content file in a first format and multiple program sets. Each program set is a version of software that, when executed by a respective electronic system, produces the multimedia content file in a second format for use in the respective electronic system. A first program set is compatible with a first operating system executed by a first electronic system and a second program set is compatible with a second operating system executed by a second electronic system. The second operating system is distinct from the first operating system.
Owner:MO DV INC
Video information recording apparatus and method, video information reproducing apparatus and method, recording medium, and program
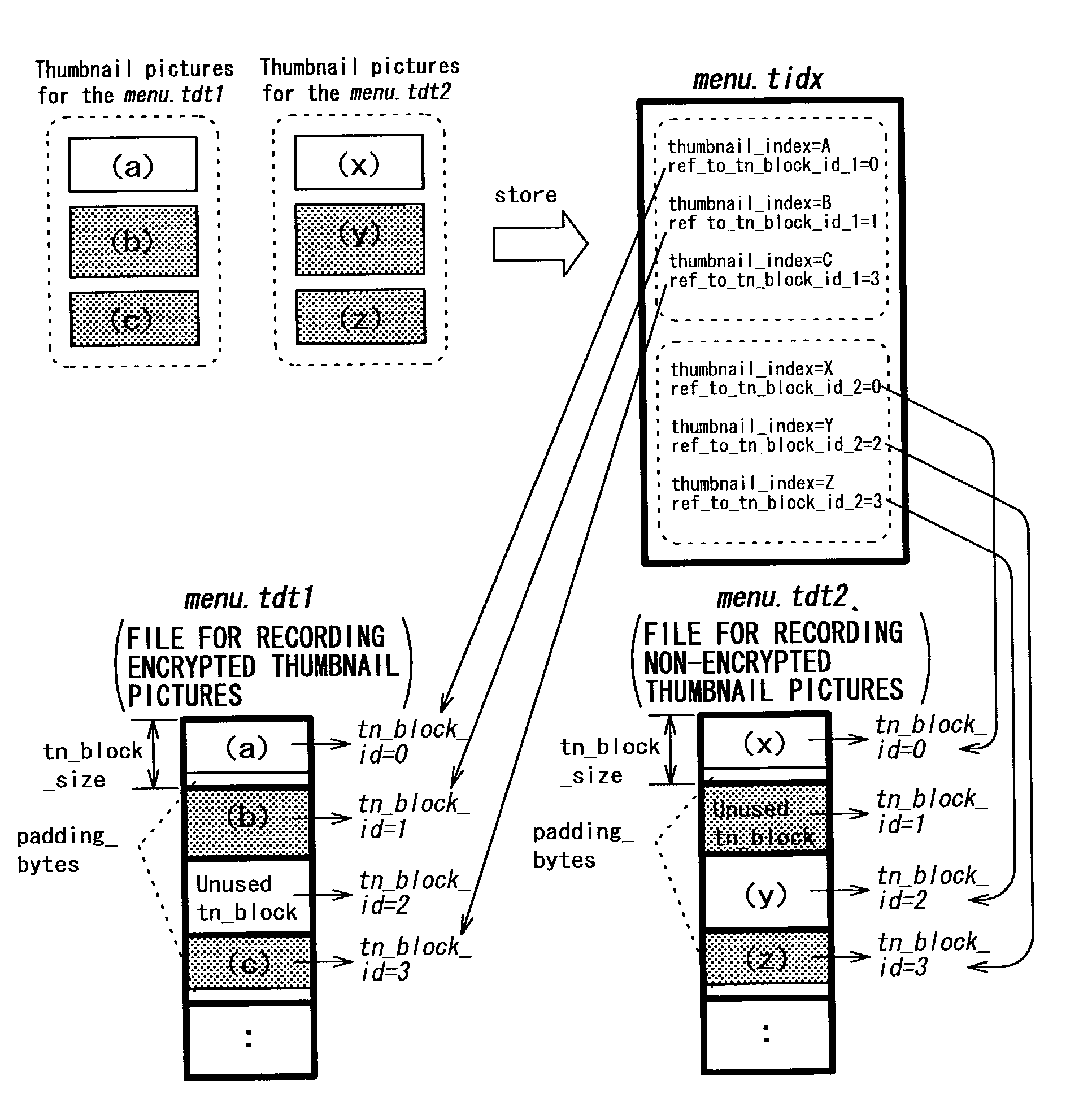
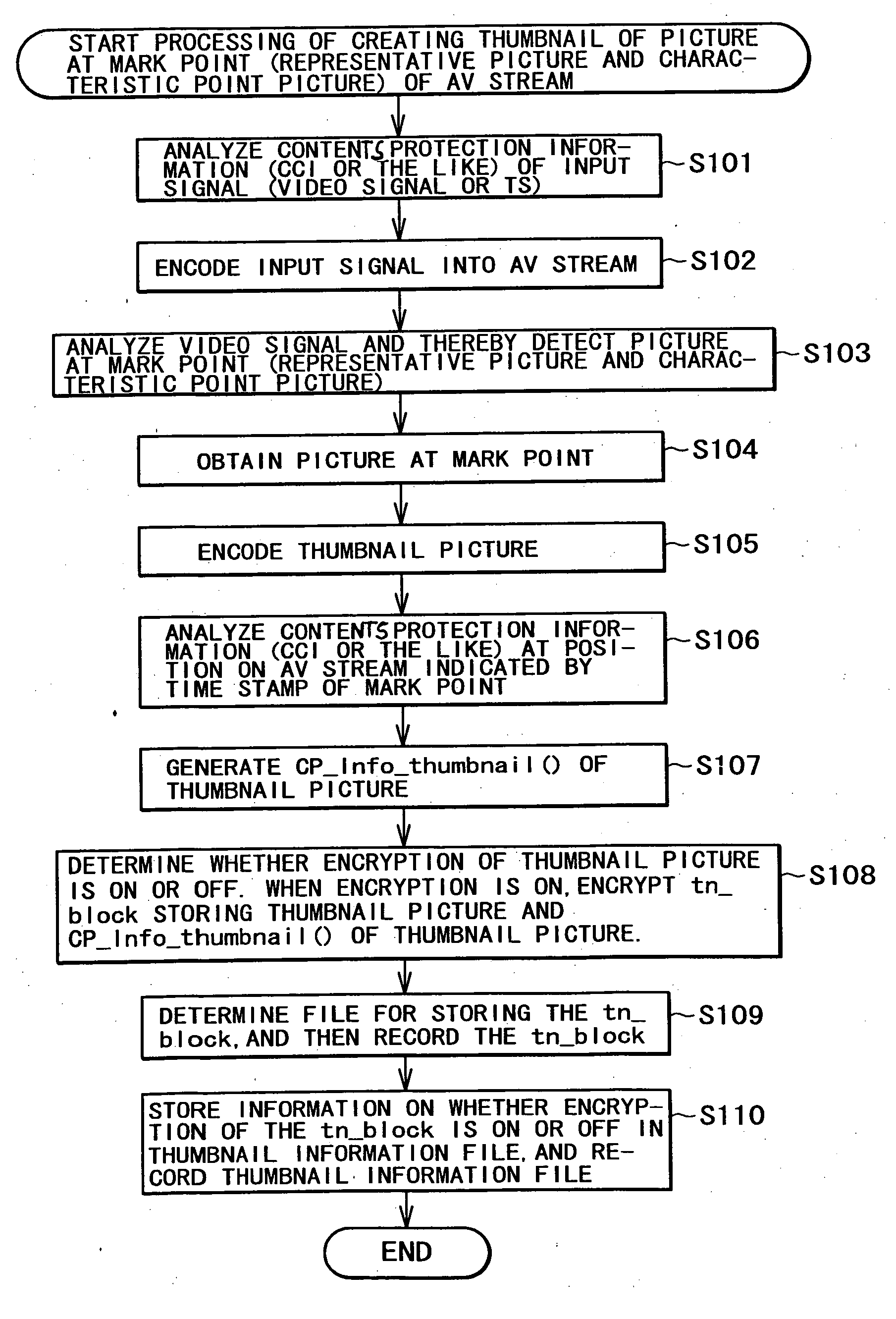
InactiveUS20070154013A1Television system detailsElectronic editing digitised analogue information signalsComputer hardwareThumbnail
A video information recording apparatus includes a first obtaining unit operable to obtain video information to be recorded; a second obtaining unit operable to obtain thumbnail picture information to be recorded in correspondence with the video information; an encrypting unit operable to encrypt the thumbnail picture information; and a recording unit operable to record the video information and the encrypted thumbnail picture information onto a recording medium.
Owner:SONY CORP
Multimedia storage systems and methods
ActiveUS7508943B2Circuits to prevent unauthorised copying/reproductionRecord information storageElectronic systemsOperational system
An article of manufacture includes a machine-readable medium that stores a multimedia content file in a first format and multiple program sets. Each program set is a version of software that, when executed by a respective electronic system, produces the multimedia content file in a second format for use in the respective electronic system. A first program set is compatible with a first operating system executed by a first electronic system and a second program set is compatible with a second operating system executed by a second electronic system. The second operating system is distinct from the first operating system.
Owner:MO DV INC
Method and system for providing secure digital music duplication
InactiveUSRE43936E1Digital data processing detailsCircuits to prevent unauthorised copying/reproductionDigital dataDigital content
A system and method are provided wherein digital data representing content and associated license rights may copied to a storage medium, such as a removable storage medium, whereby the serial number of the copied-to storage medium is integrated into the licensing scheme utilized to secure the digital content. As a result, the digital content is pre-authenticated and bound to the copied-to storage medium, obviating the need to access a network or other location for access to the protected content.
Owner:XYLON LLC
Recording medium, recording medium method and apparatus , information signal output control method, recording medium reproducing apparatus, signal transmission method, and content data
InactiveUS7284128B2Easy to detectEasy to rewriteTelevision system detailsUser identity/authority verificationComputer hardwareAnalog signal
A record medium for recording an information signal in which a first watermark and a second watermark have been embedded, the first watermark being embedded when the information signal is transmitted as an analog signal, the second watermark being embedded when the information signal is further transmitted.
Owner:SONY CORP
Popular searches
Analogue secracy/subscription systems Hardware monitoring Selective content distribution Program/content distribution protection Special data processing applications Coding/ciphering apparatus Simultaneous/sequential multiple television signal transmission Digital recording/reproducing Color television details Data resetting
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com