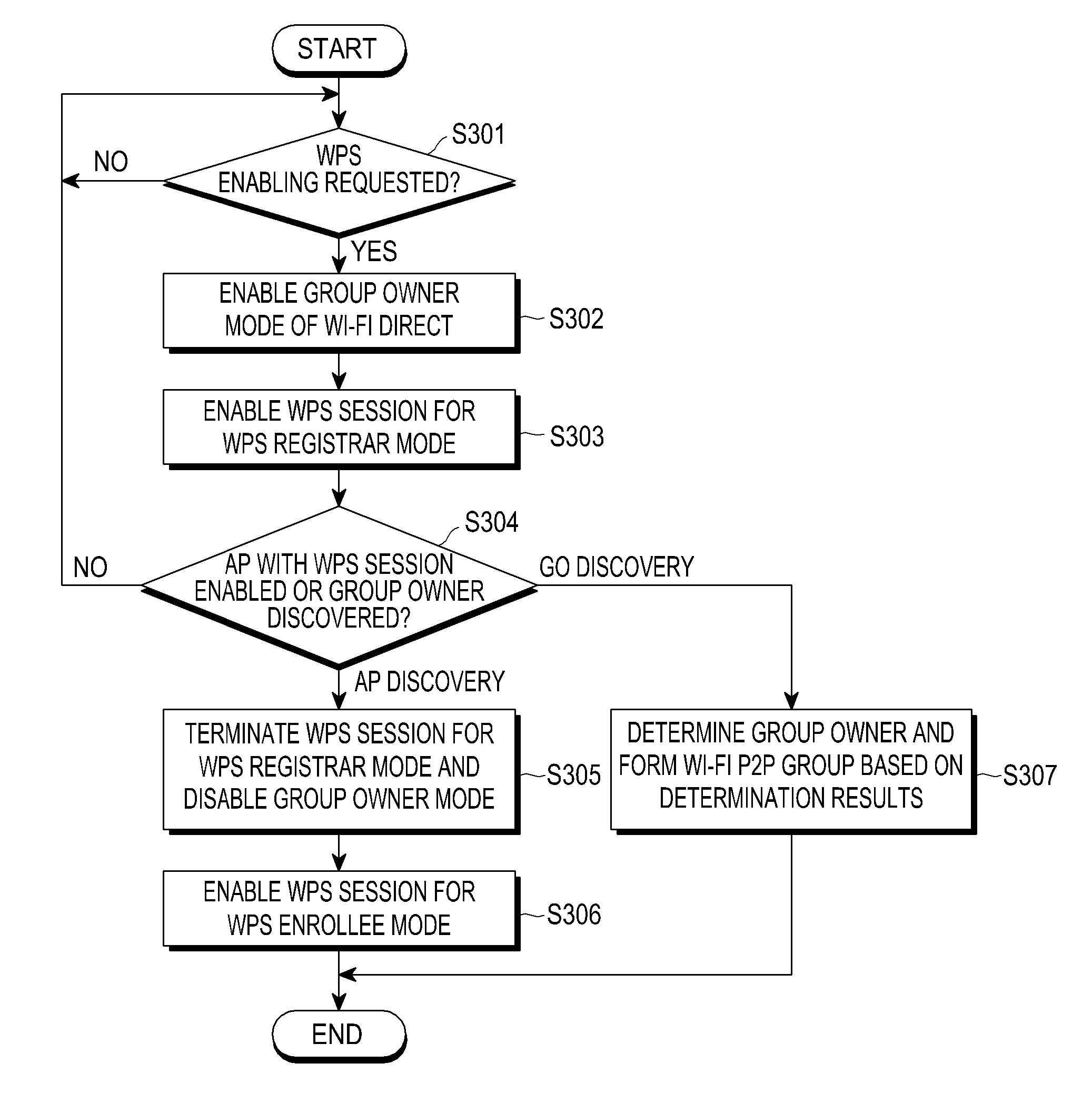
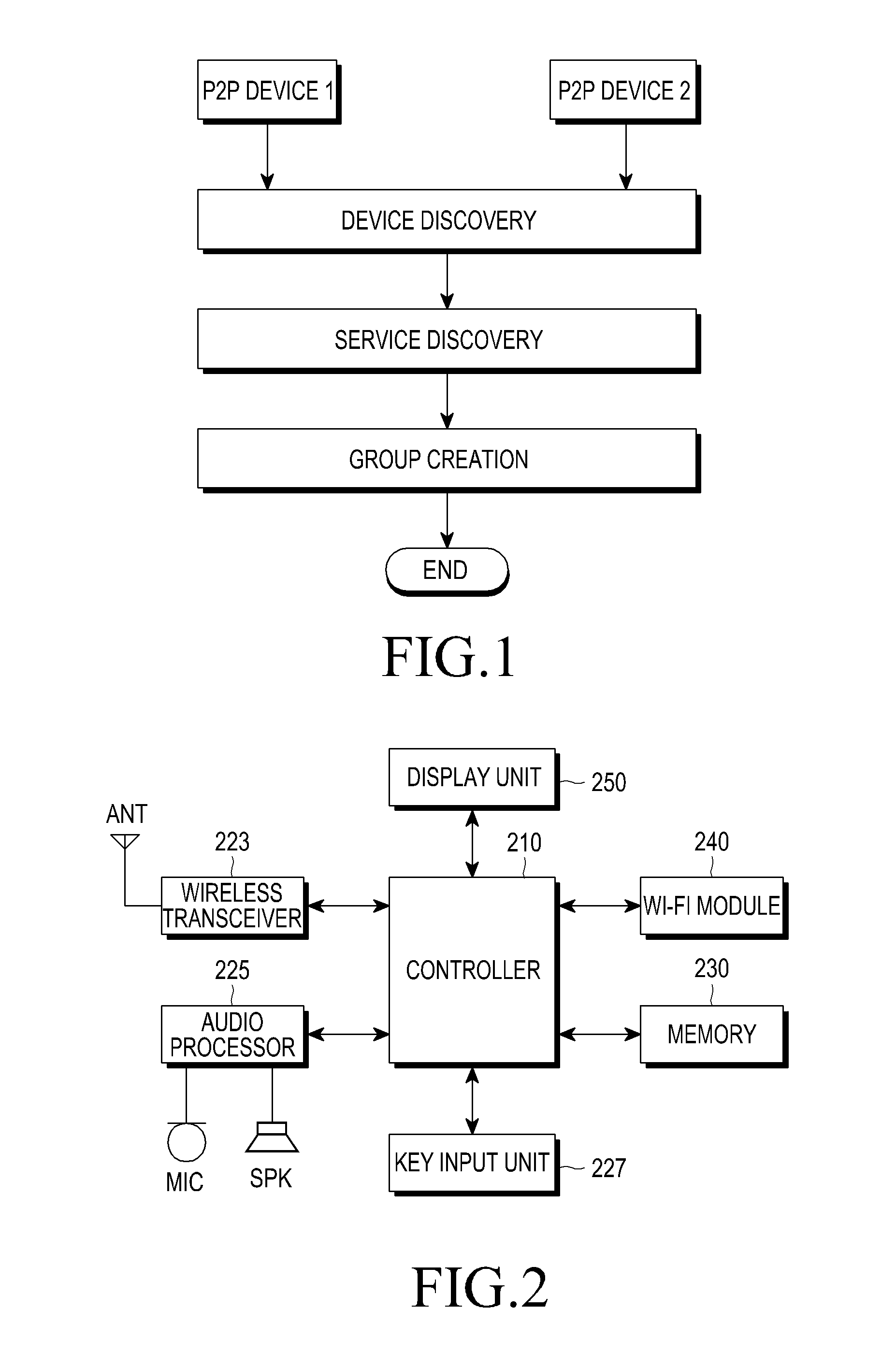
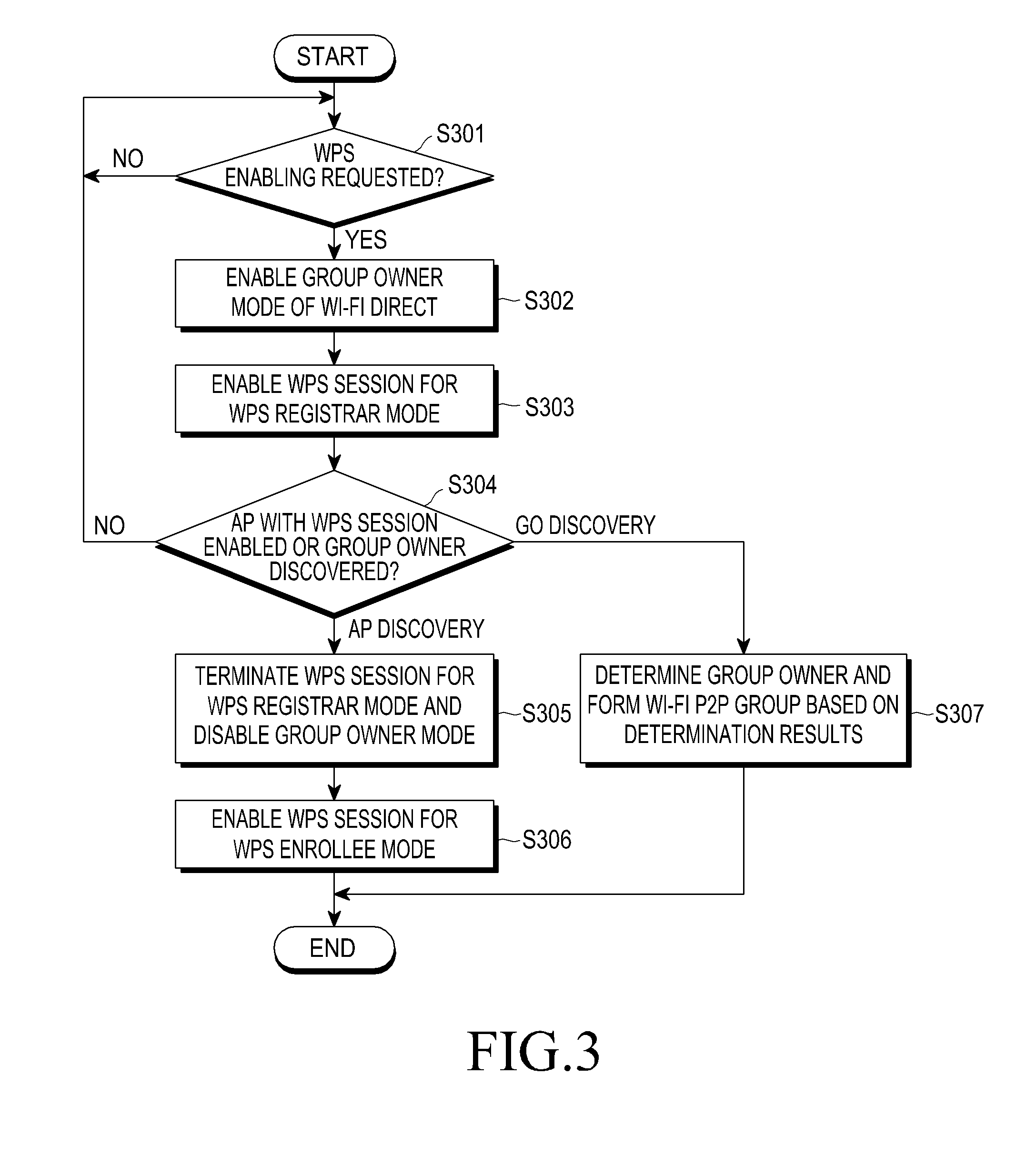
Patents
Literature
Hiro is an intelligent assistant for R&D personnel, combined with Patent DNA, to facilitate innovative research.
34 results about "Wi-Fi Protected Setup" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
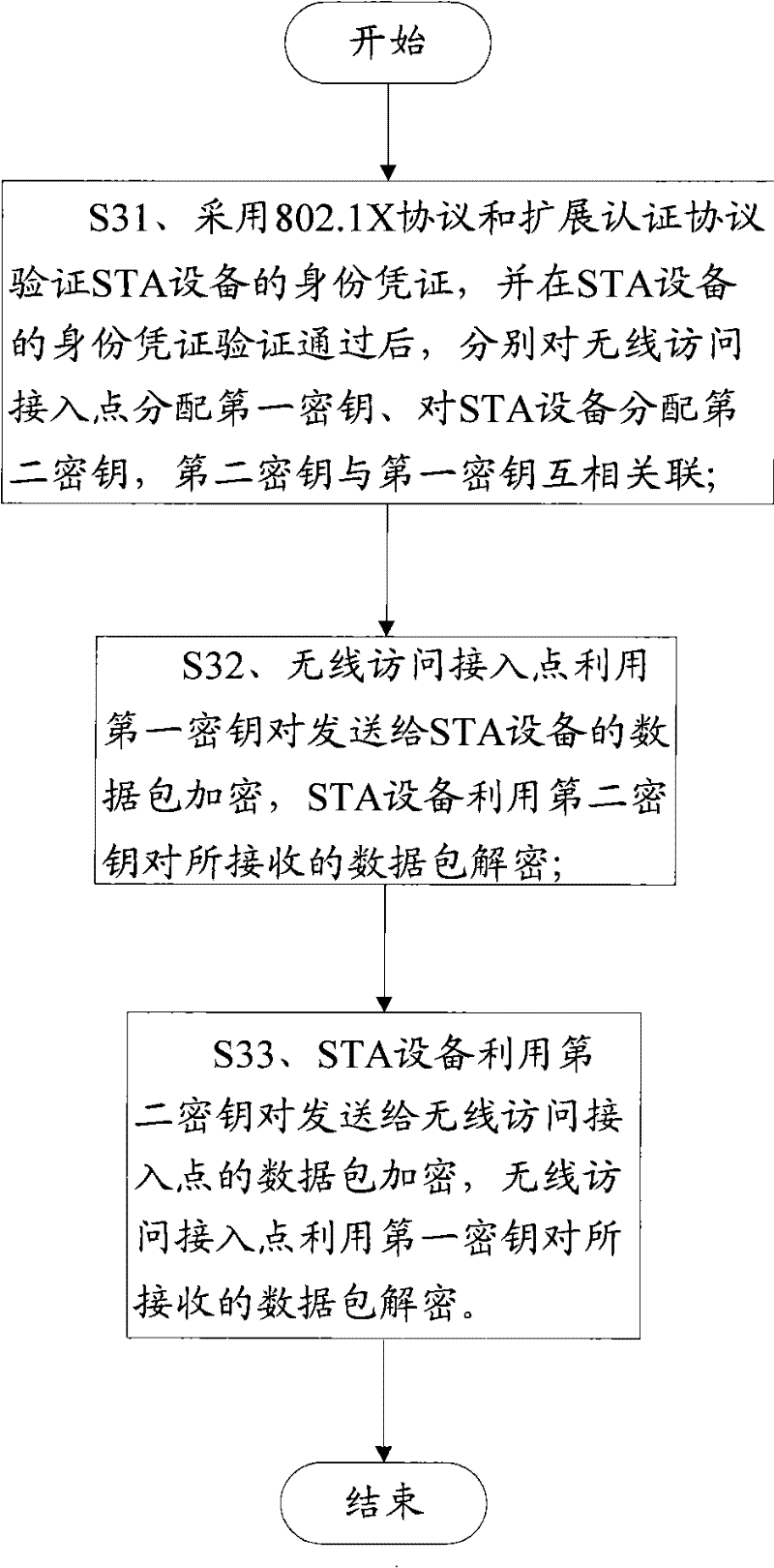
Wi-Fi Protected Setup (wps; originally, Wi-Fi Simple Config) is a network security standard to create a secure wireless home network. Created by the Wi-Fi Alliance and introduced in 2006, the goal of the protocol is to allow home users who know little of wireless security and may be intimidated by the available security options to set up Wi-Fi Protected Access, as well as making it easy to add new devices to an existing network without entering long passphrases. Prior to the standard, several competing solutions were developed by different vendors to address the same need.
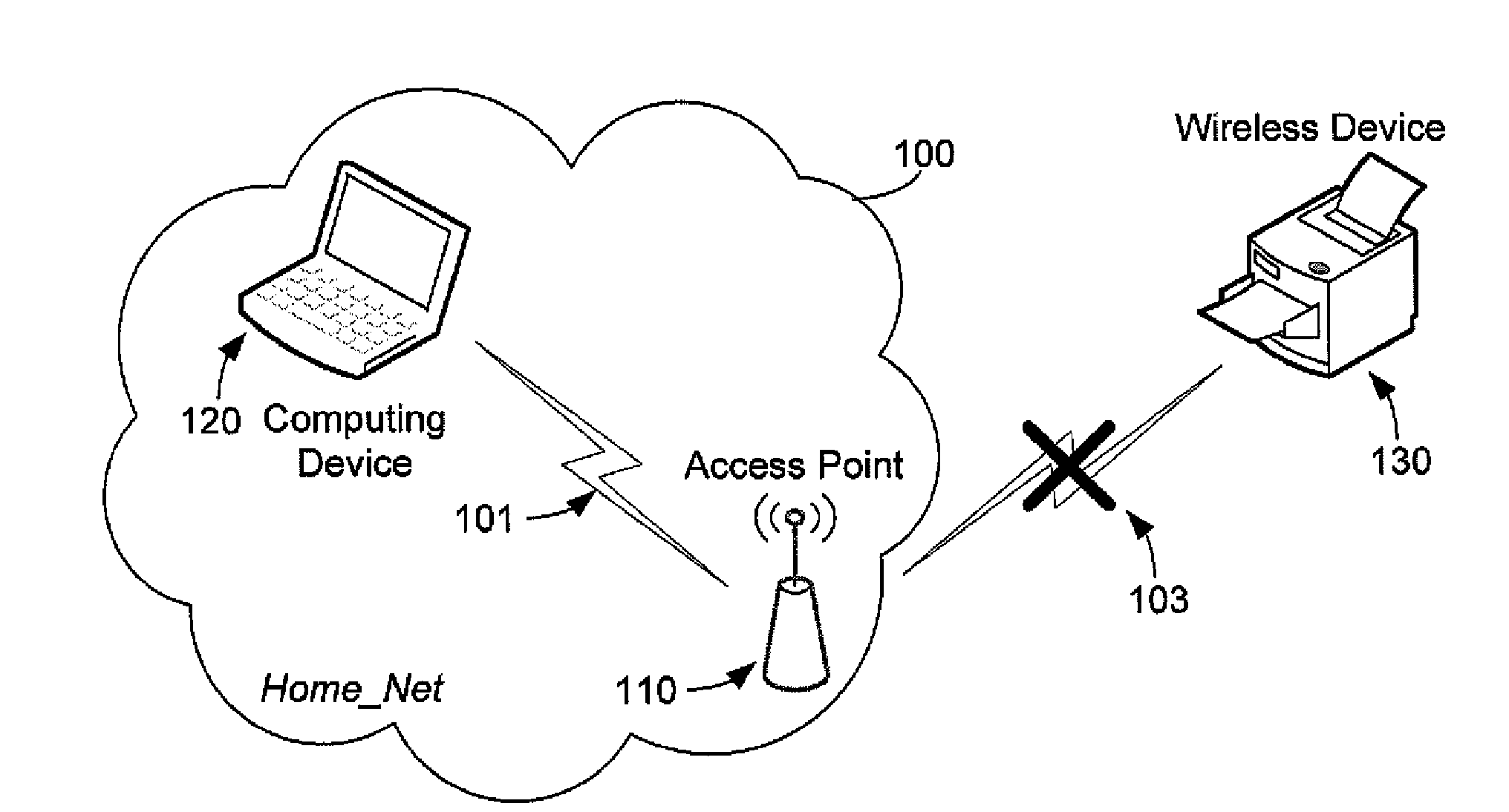
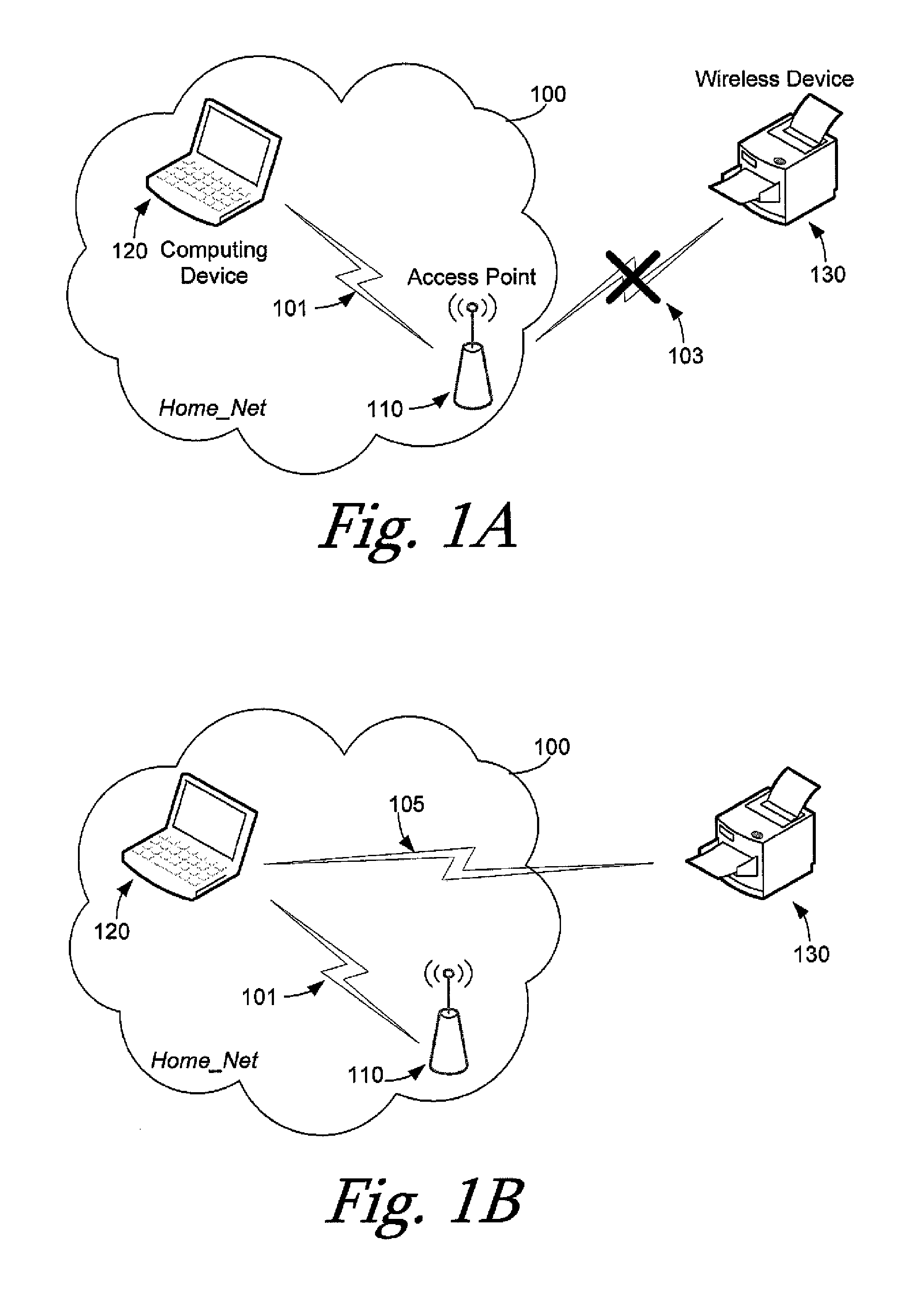
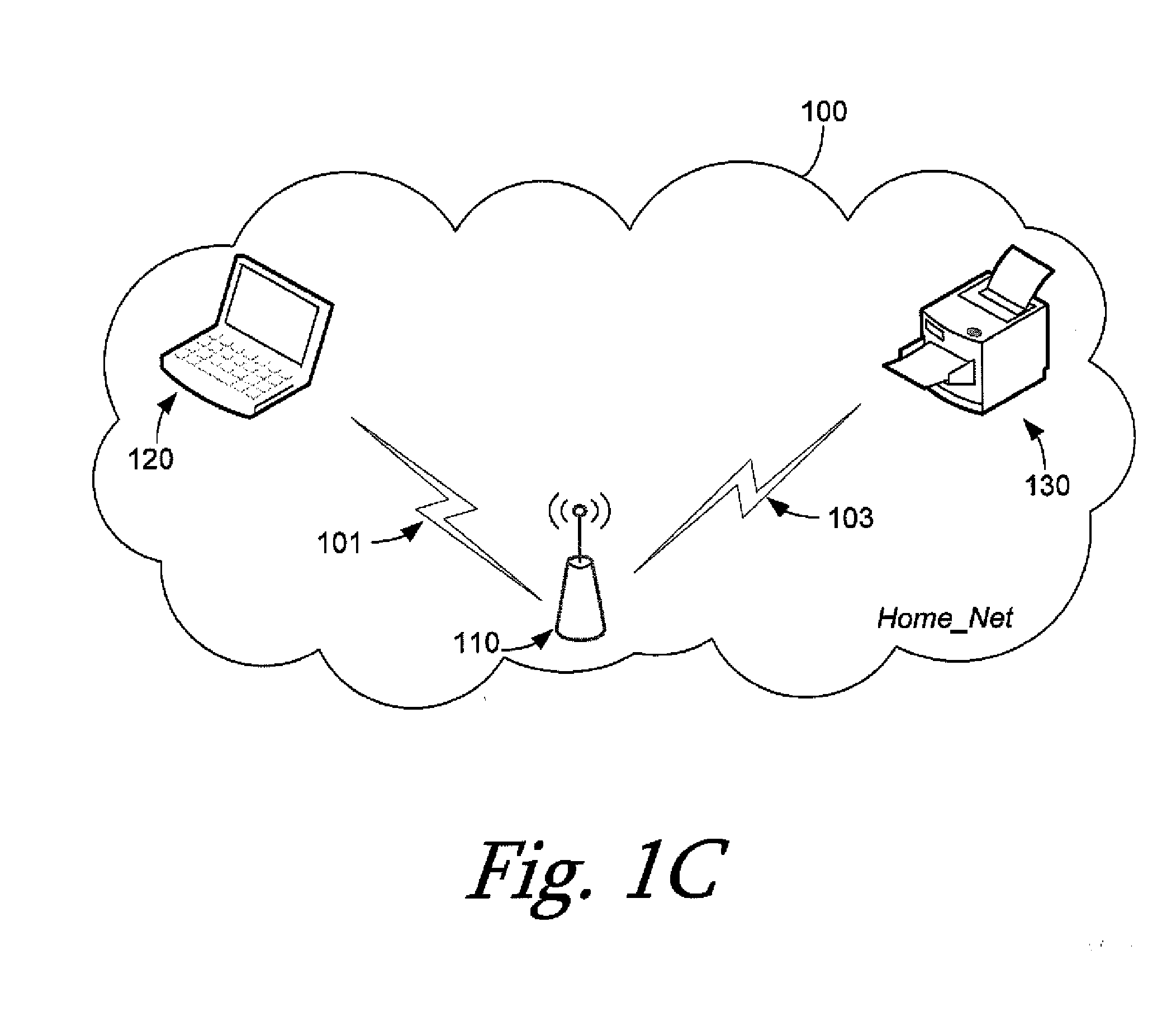
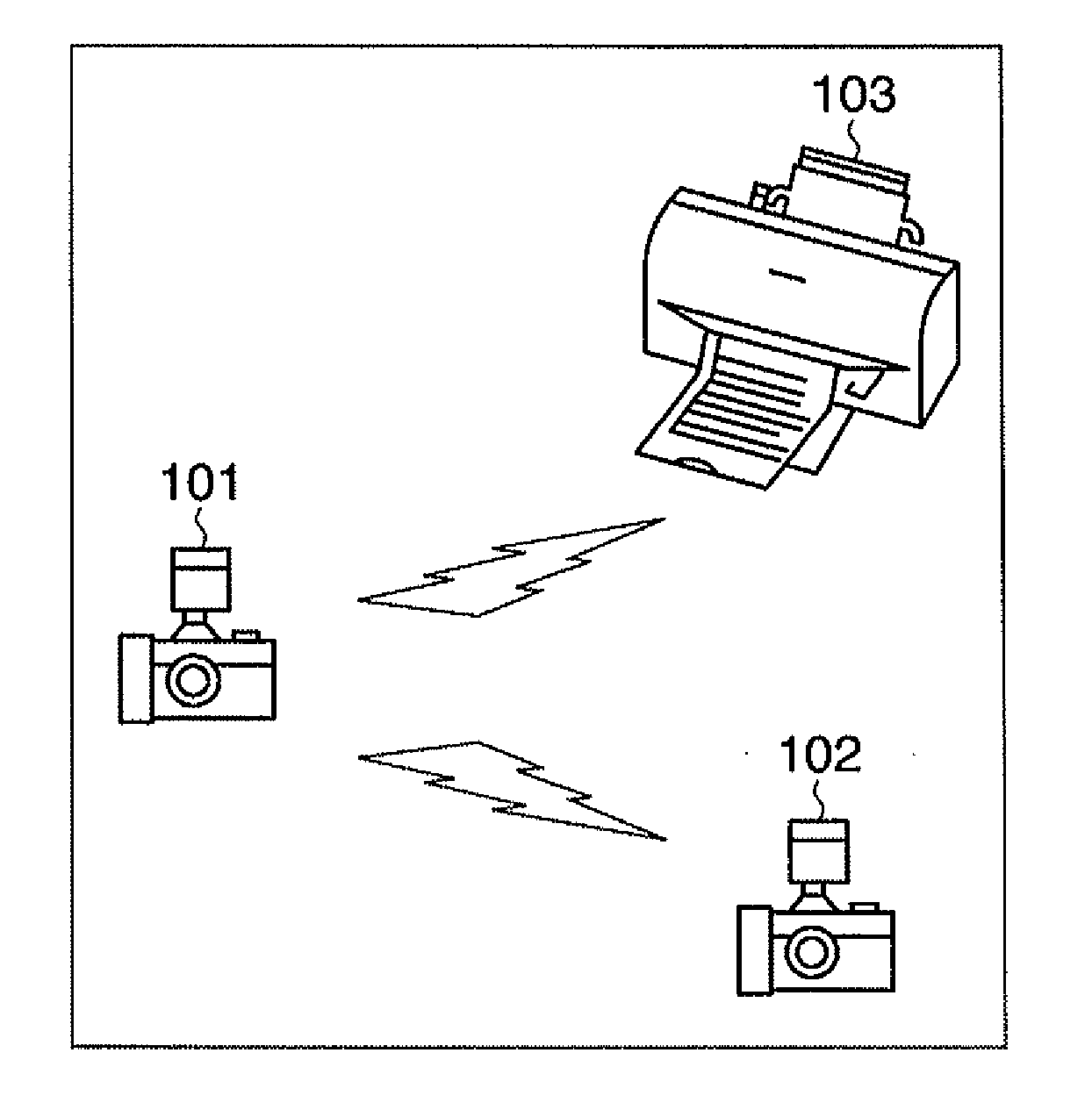
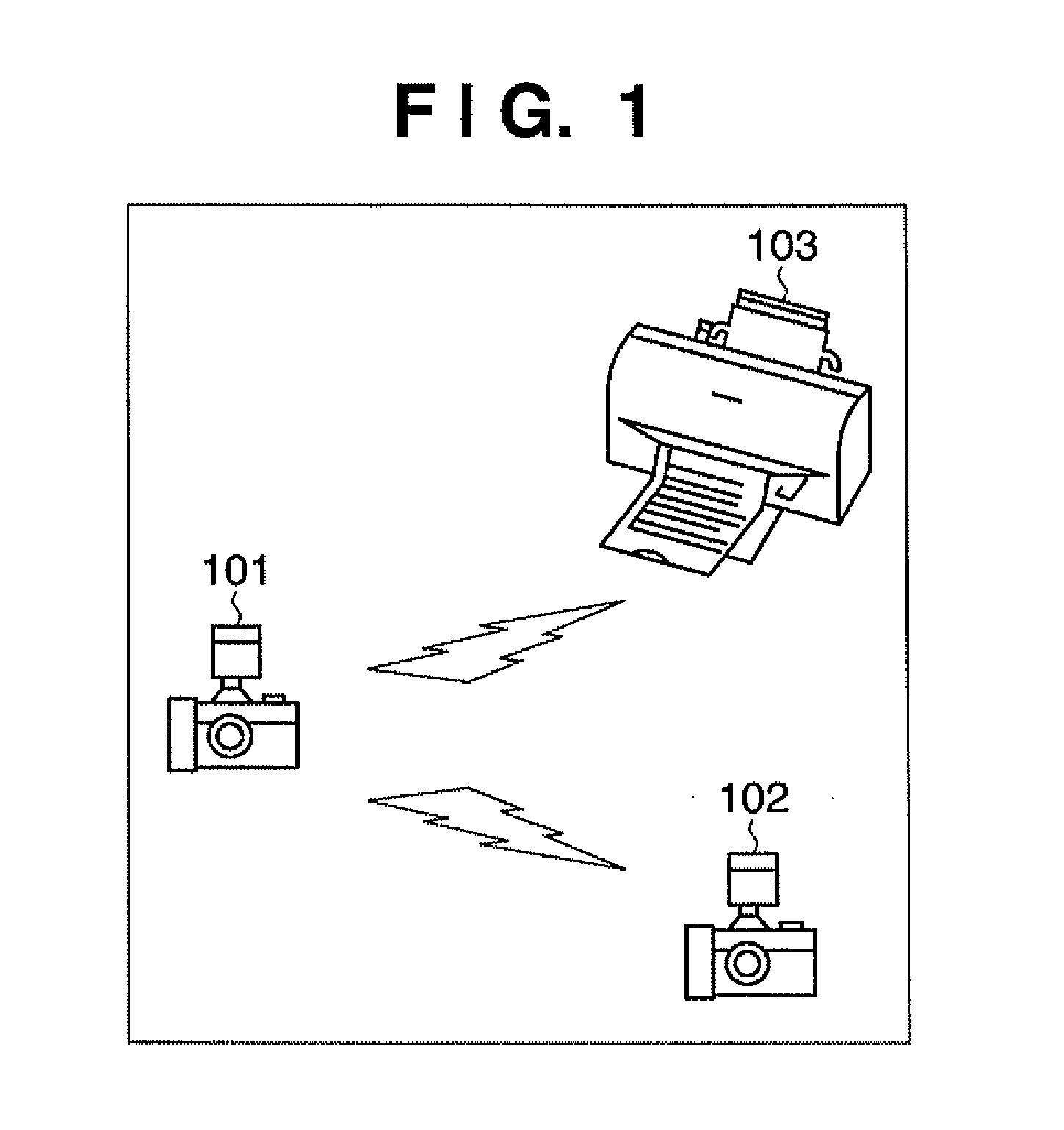
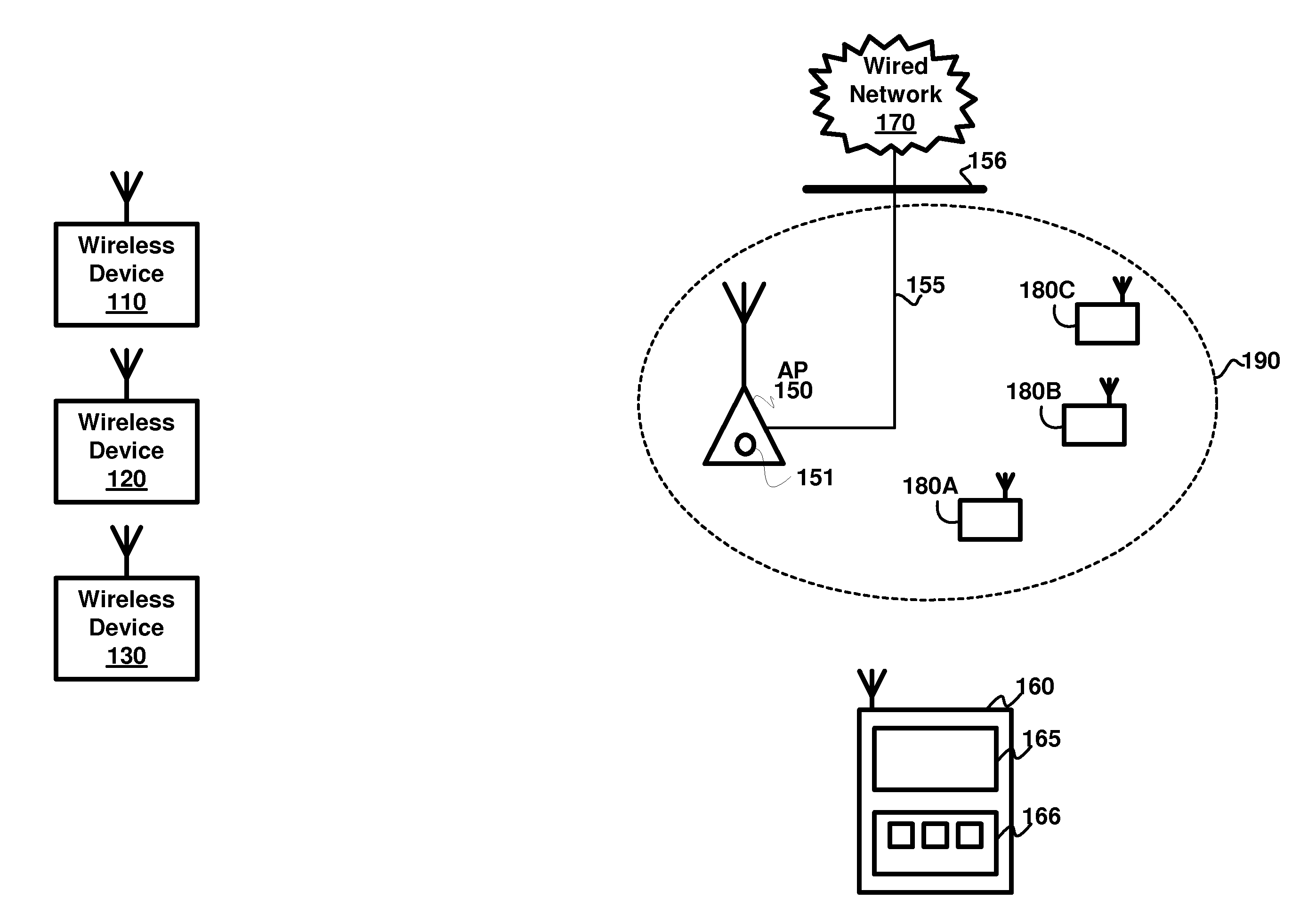
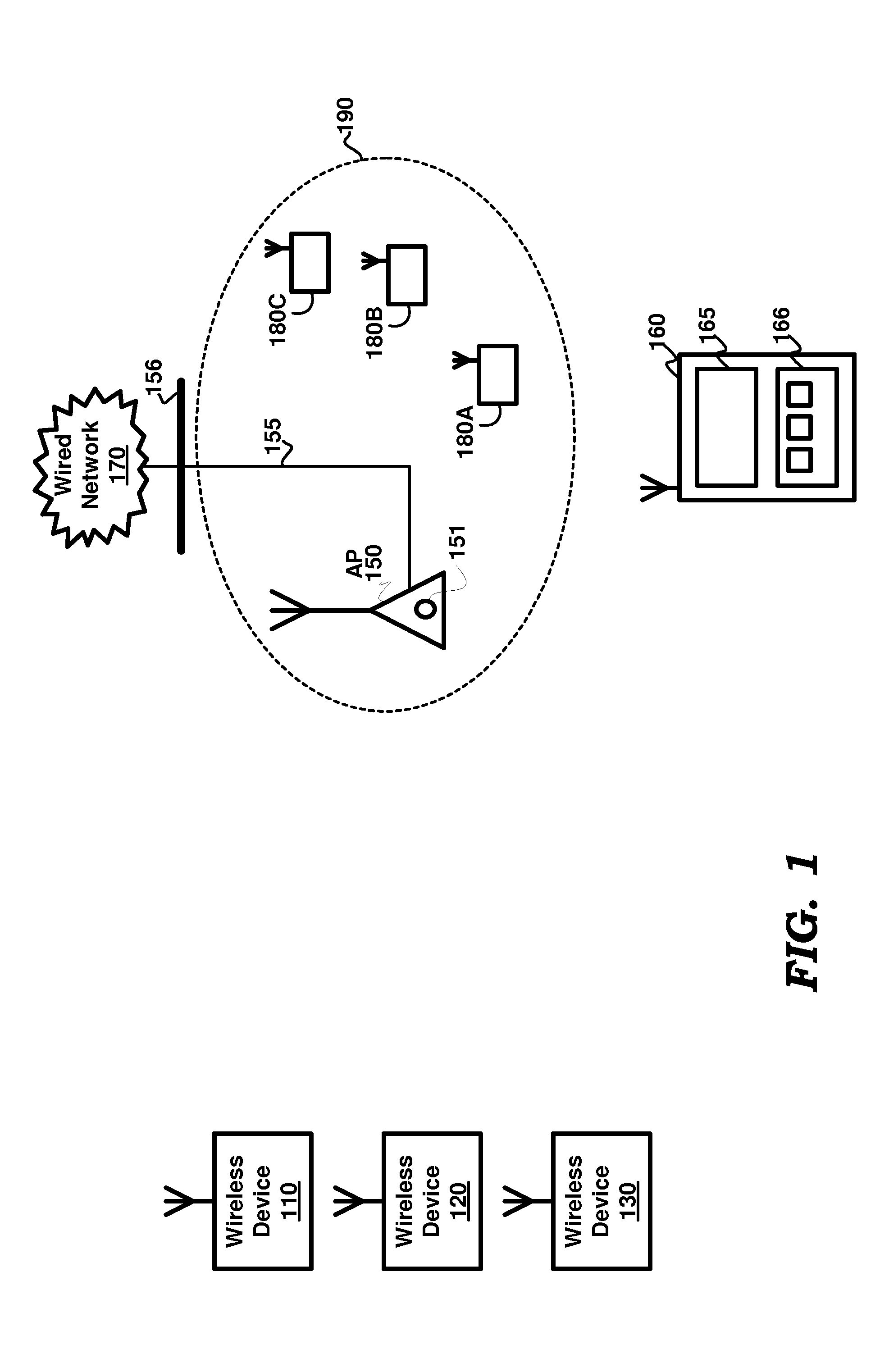
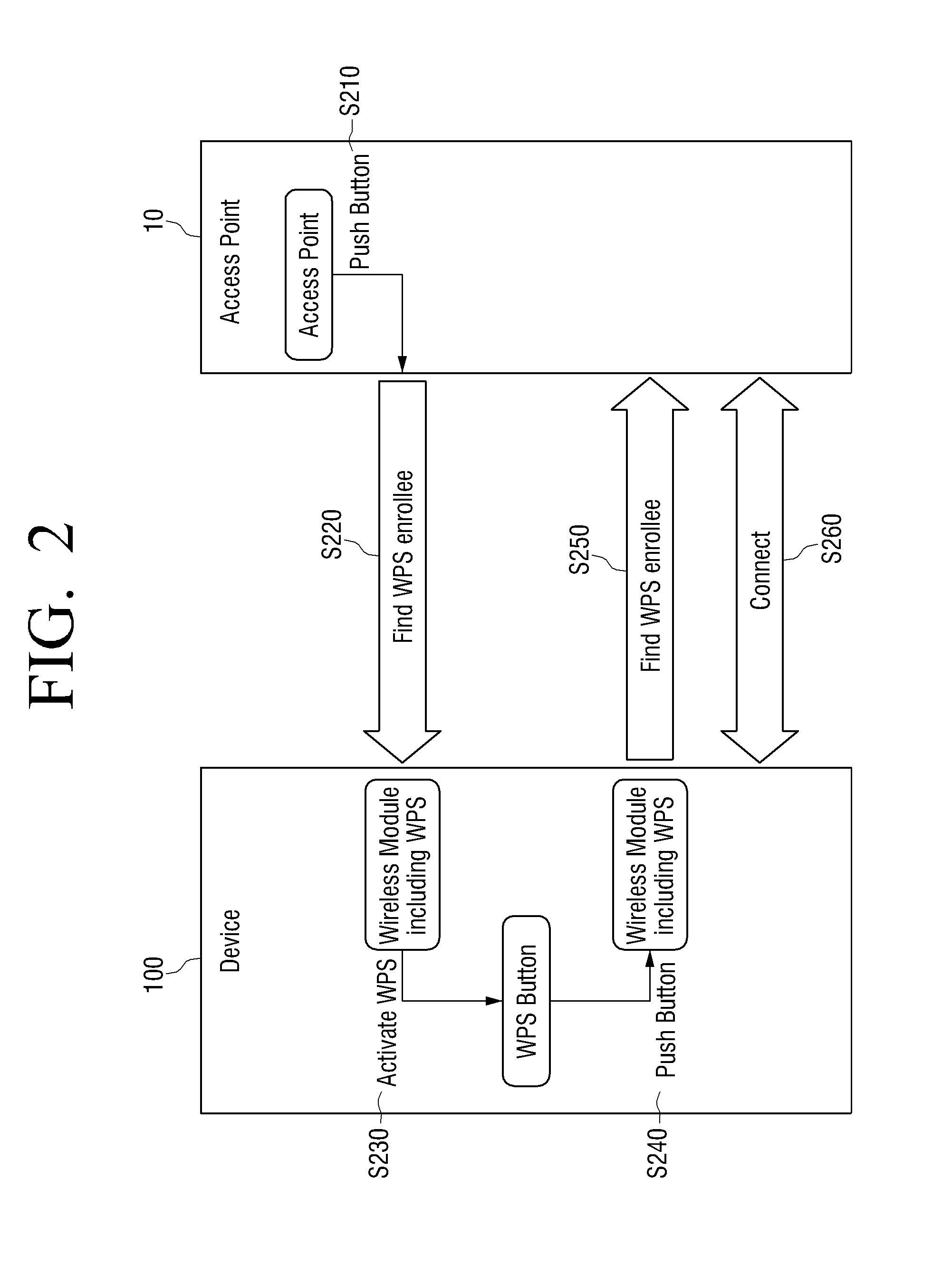
Wireless provisioning a device for a network using a soft access point
ActiveUS20100165879A1Improve usabilityImprove user experienceAssess restrictionNetwork topologiesUser inputWi-Fi Protected Setup
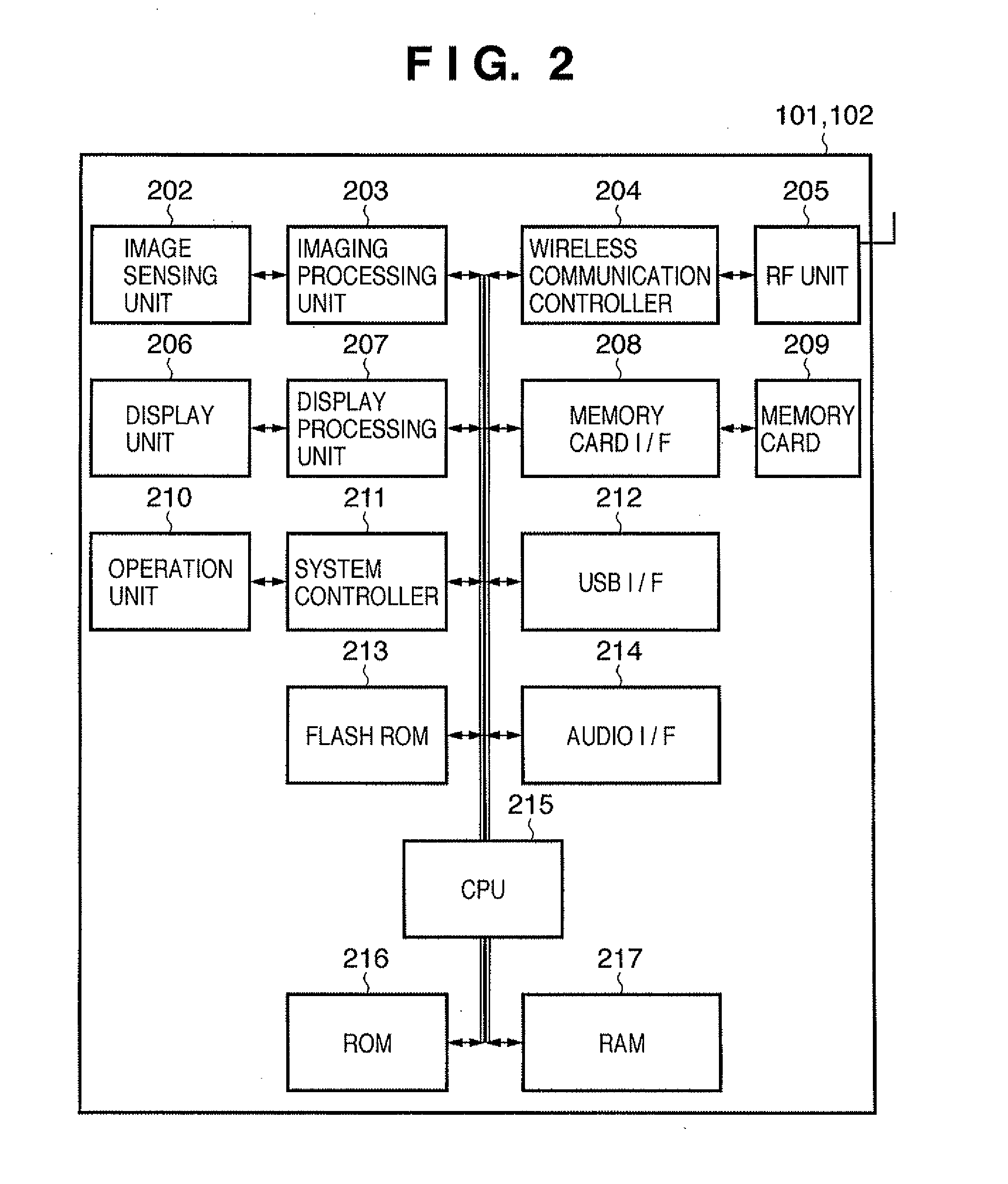
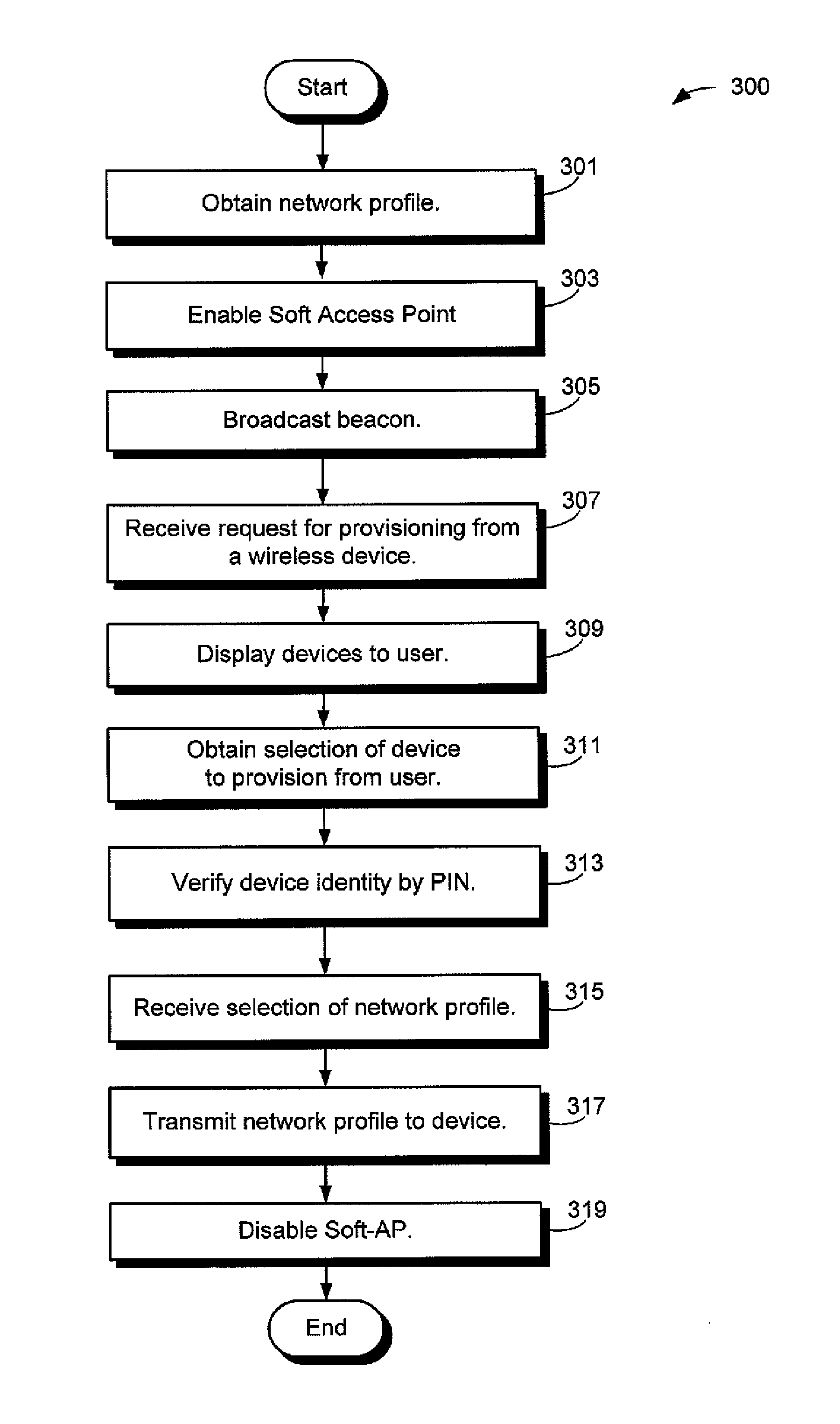
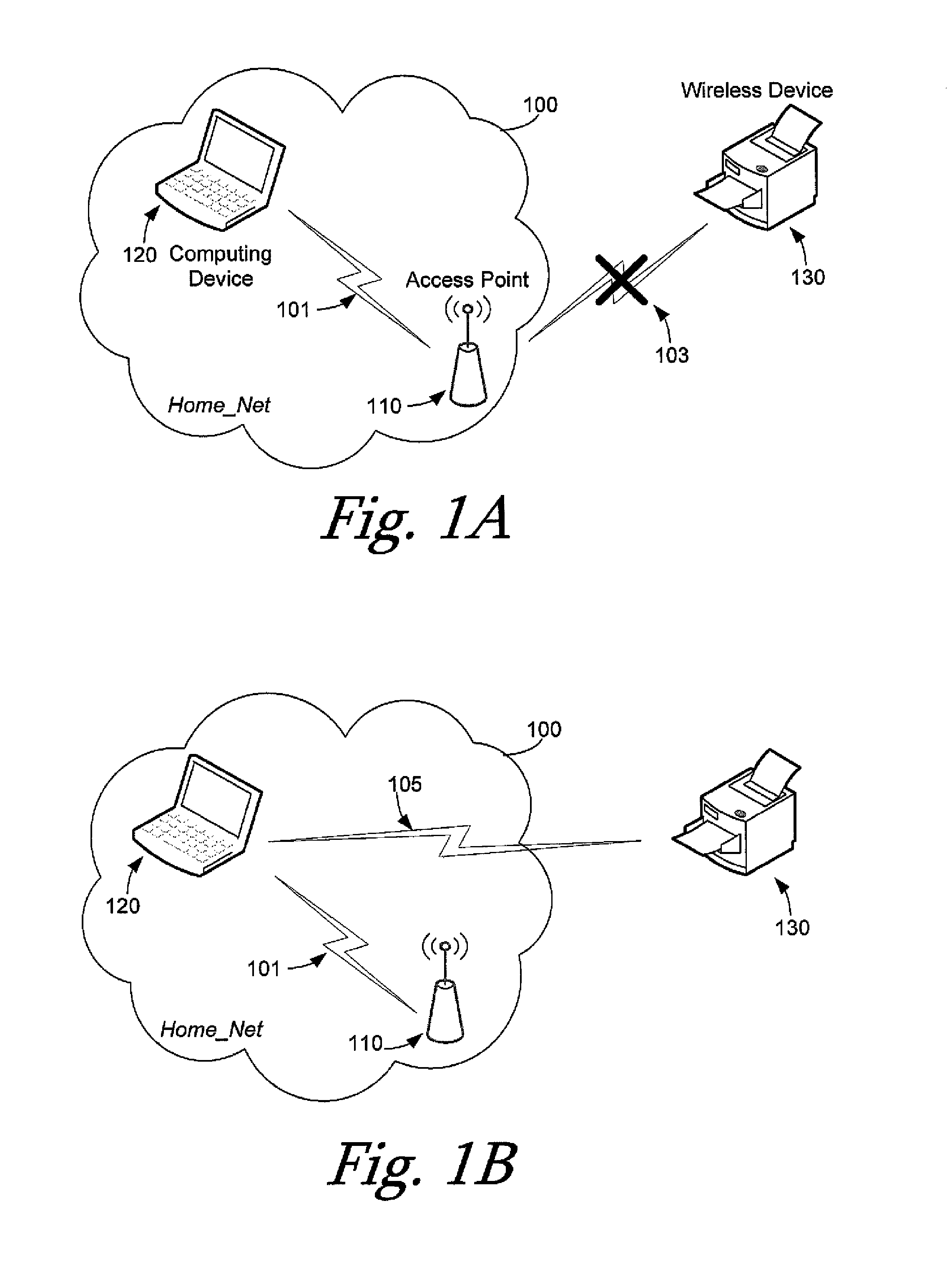
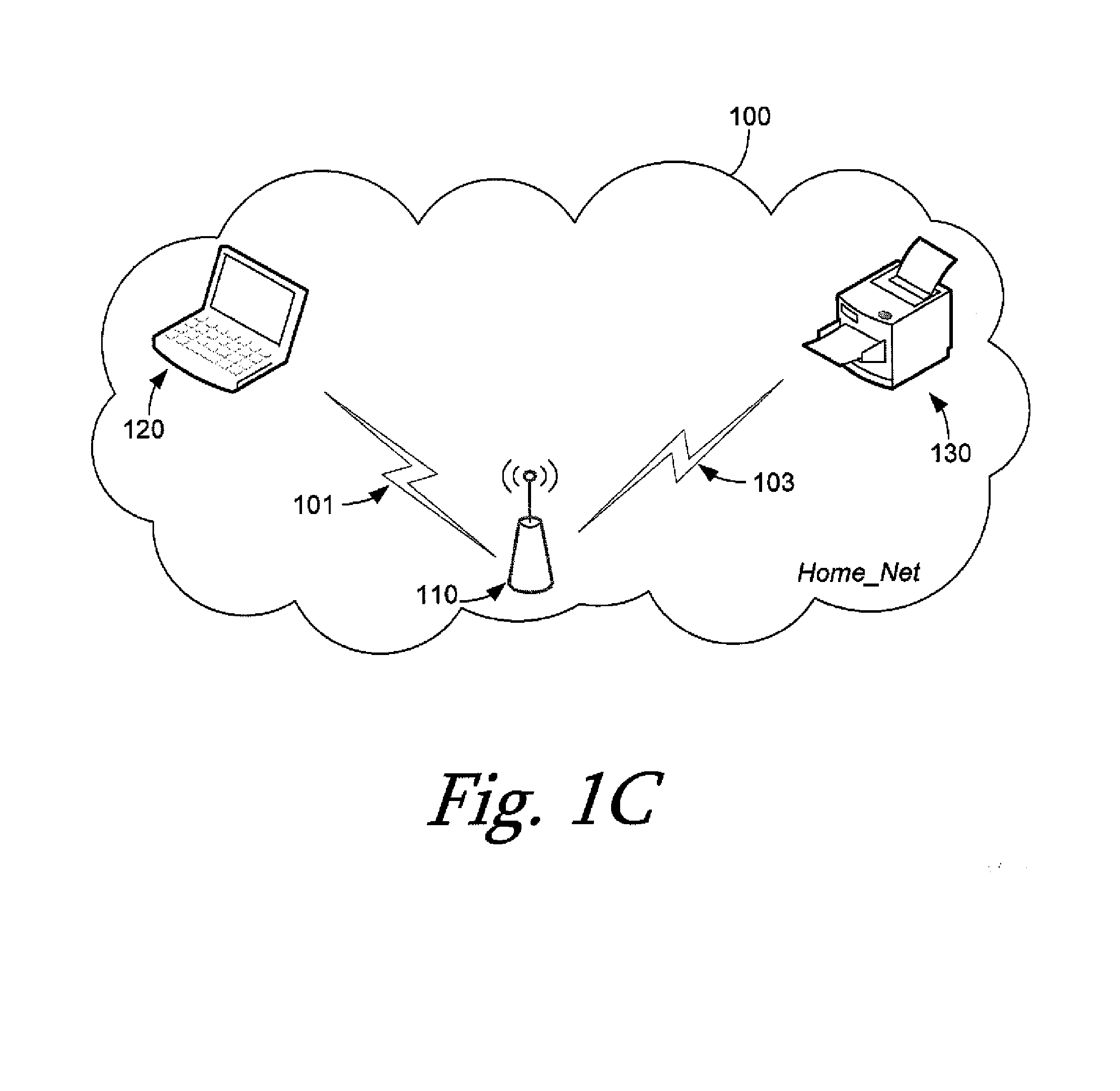
A computing device for provisioning a wireless device for connection to a wireless network via a legacy access point. The wireless device supports a wireless protected setup protocol for obtaining the network profile of the network. A user requests the computing device discover wireless devices for provisioning. In response to the user input, the computing device is configured as a soft access point and broadcasts a beacon signal indicating that the access point supports a wireless protected setup protocol, such as Wi-Fi Protected Setup. A request for provisioning is then received by the computing device from the wireless device. A network profile is transmitted from the computing device to the wireless device in accordance with the wireless protected setup protocol. The wireless device may use the profile to connect to the network via the legacy access point using the network profile.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for wi-fi connection using wi-fi protected setup in portable terminal
Owner:SAMSUNG ELECTRONICS CO LTD
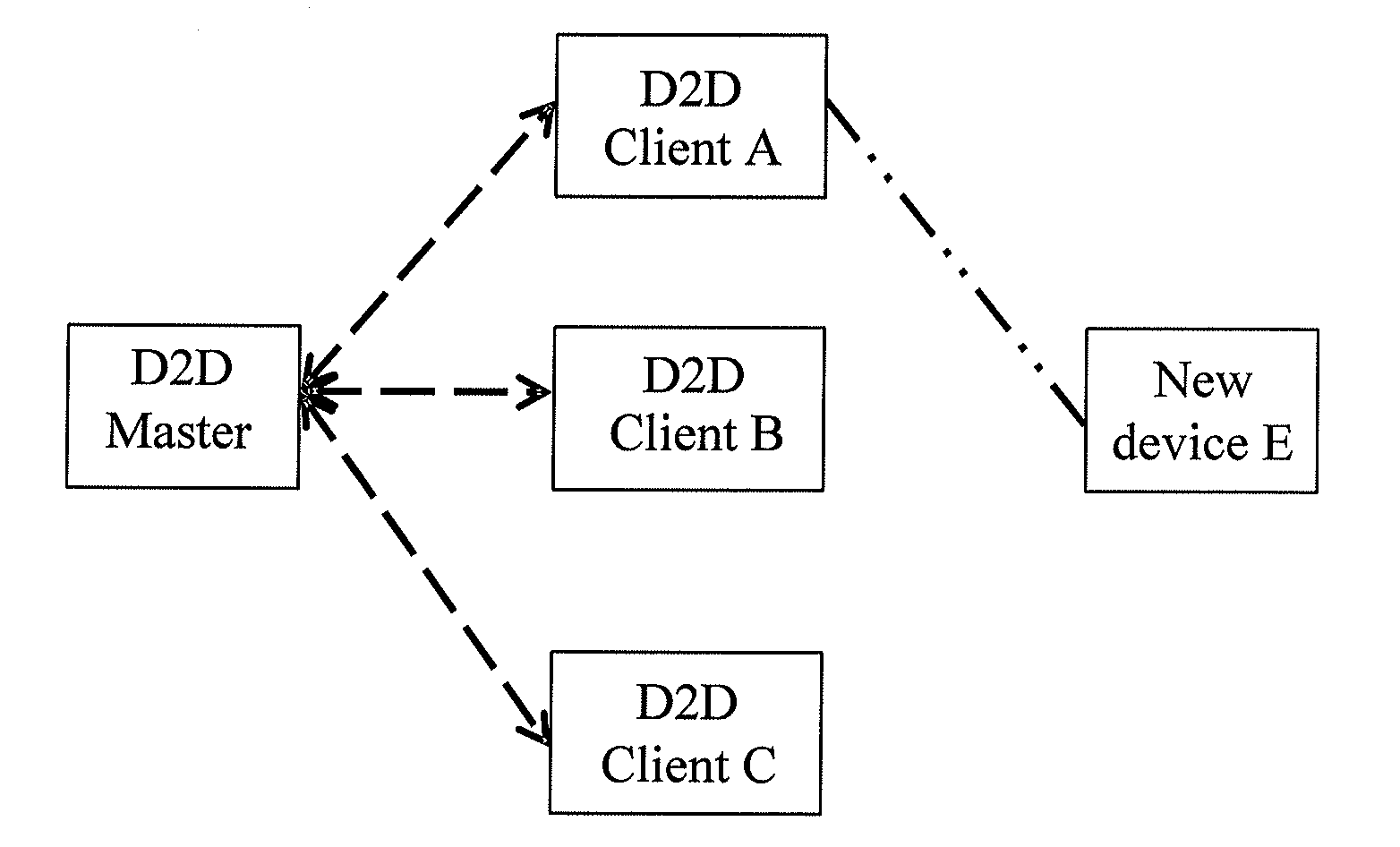
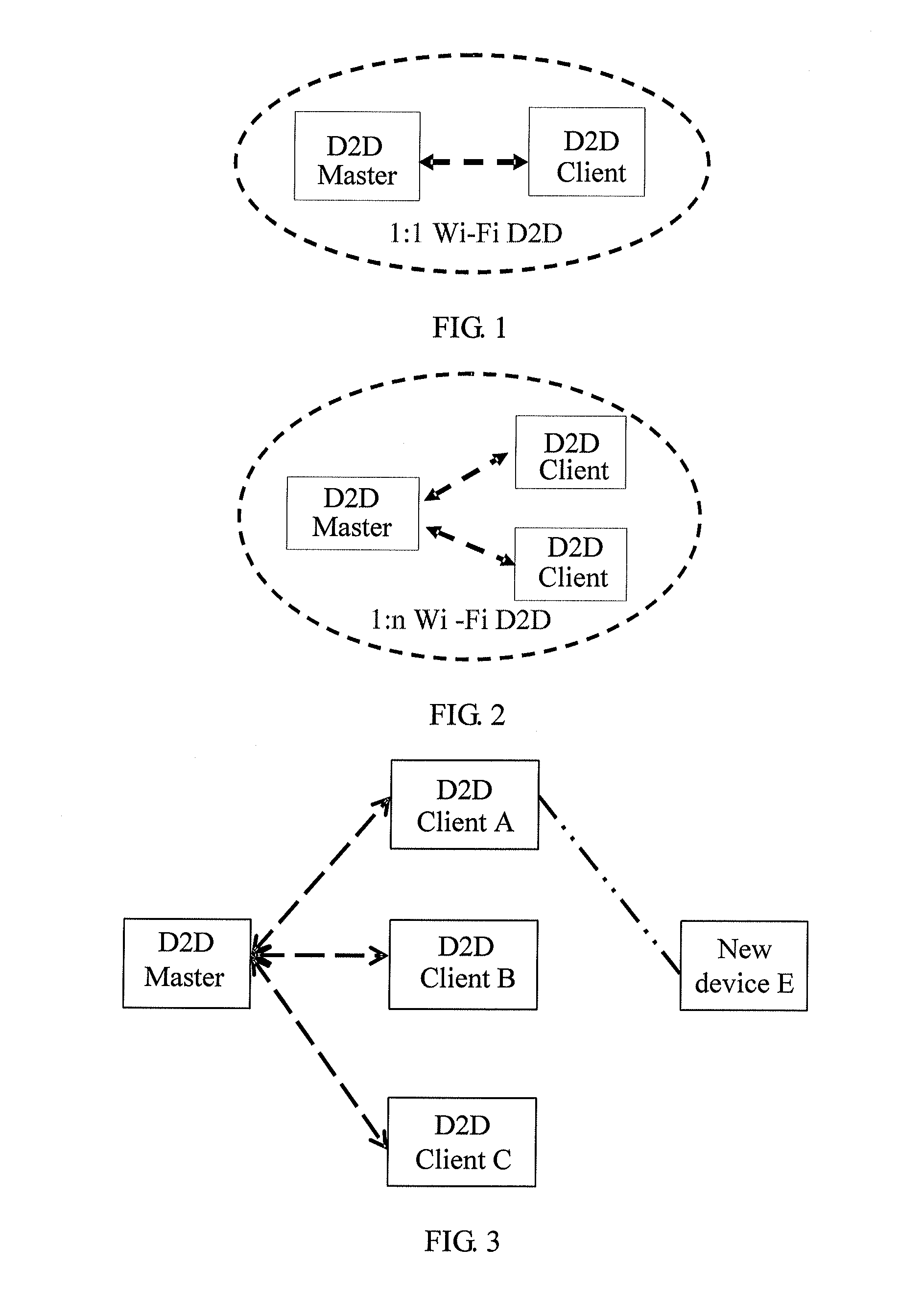
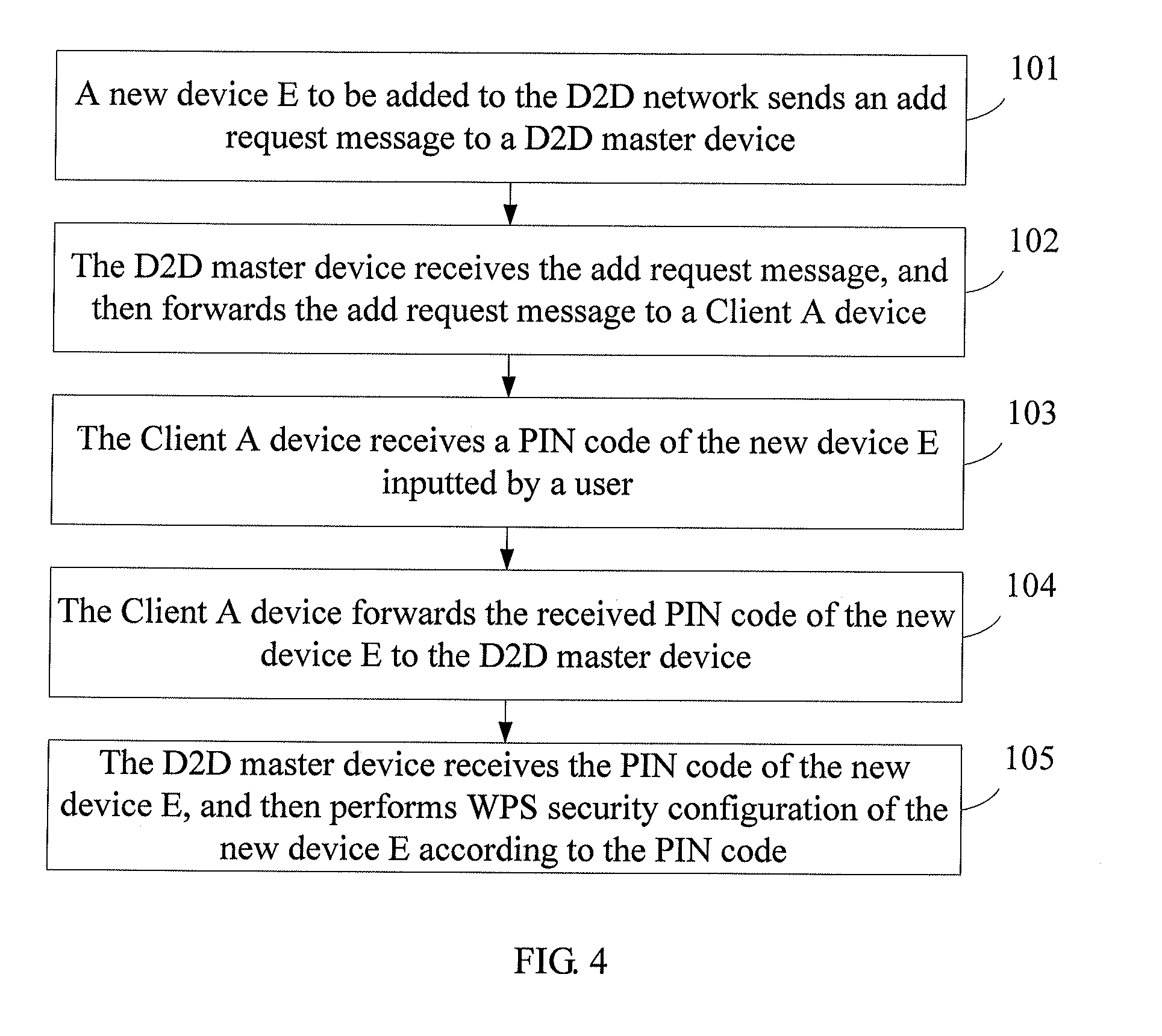
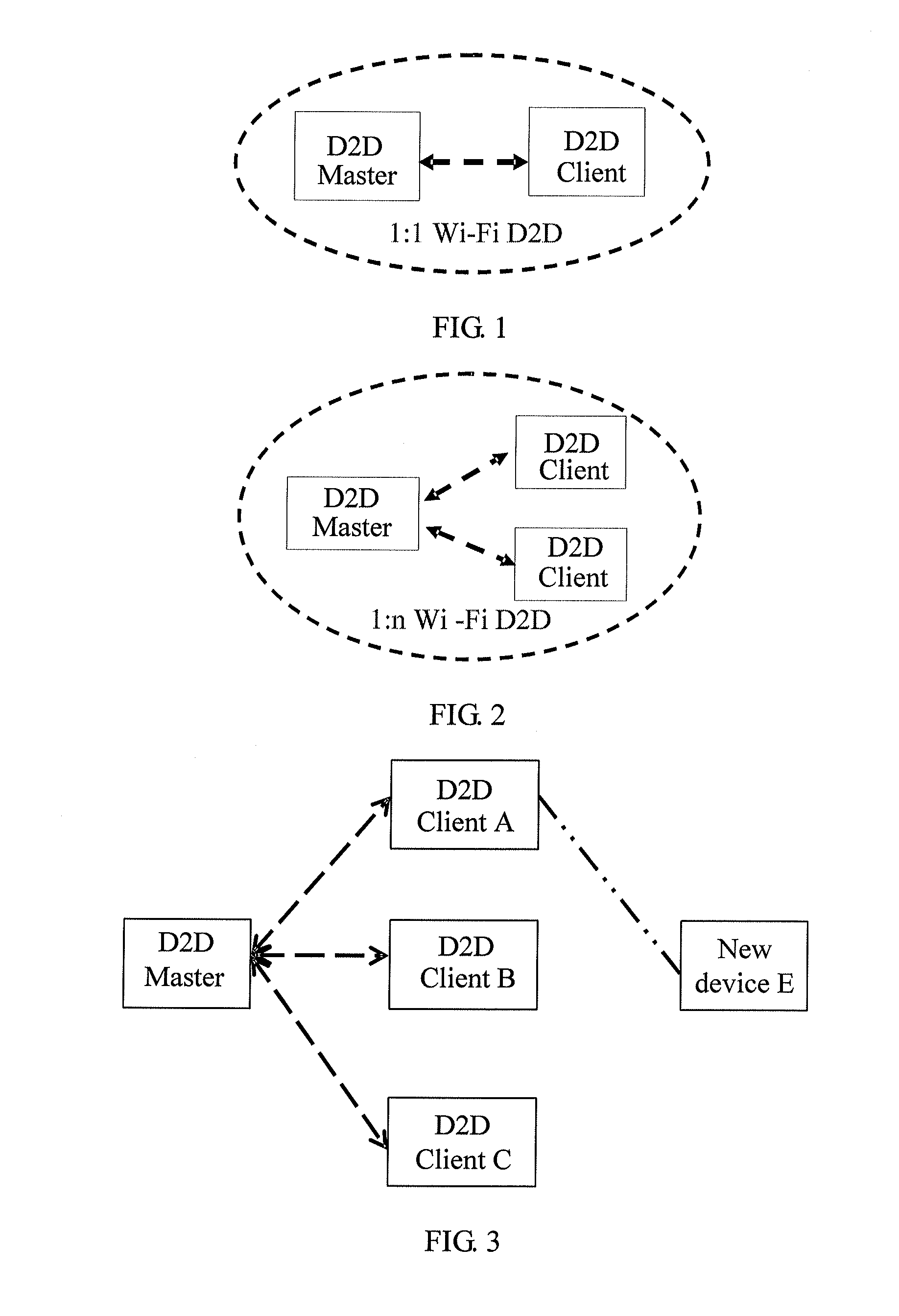
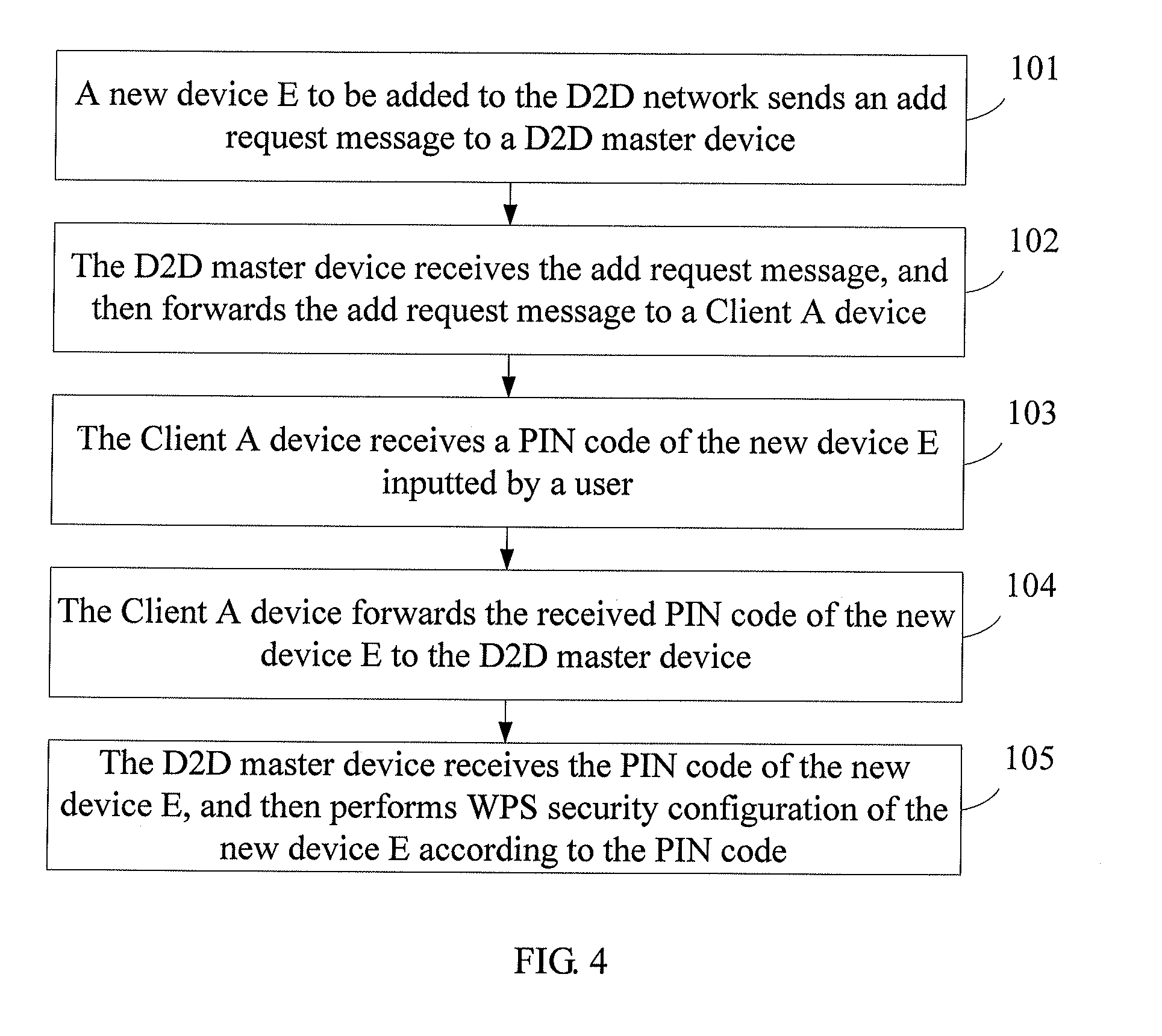
Method, system, and device for implementing device addition in wi-fi device to device network
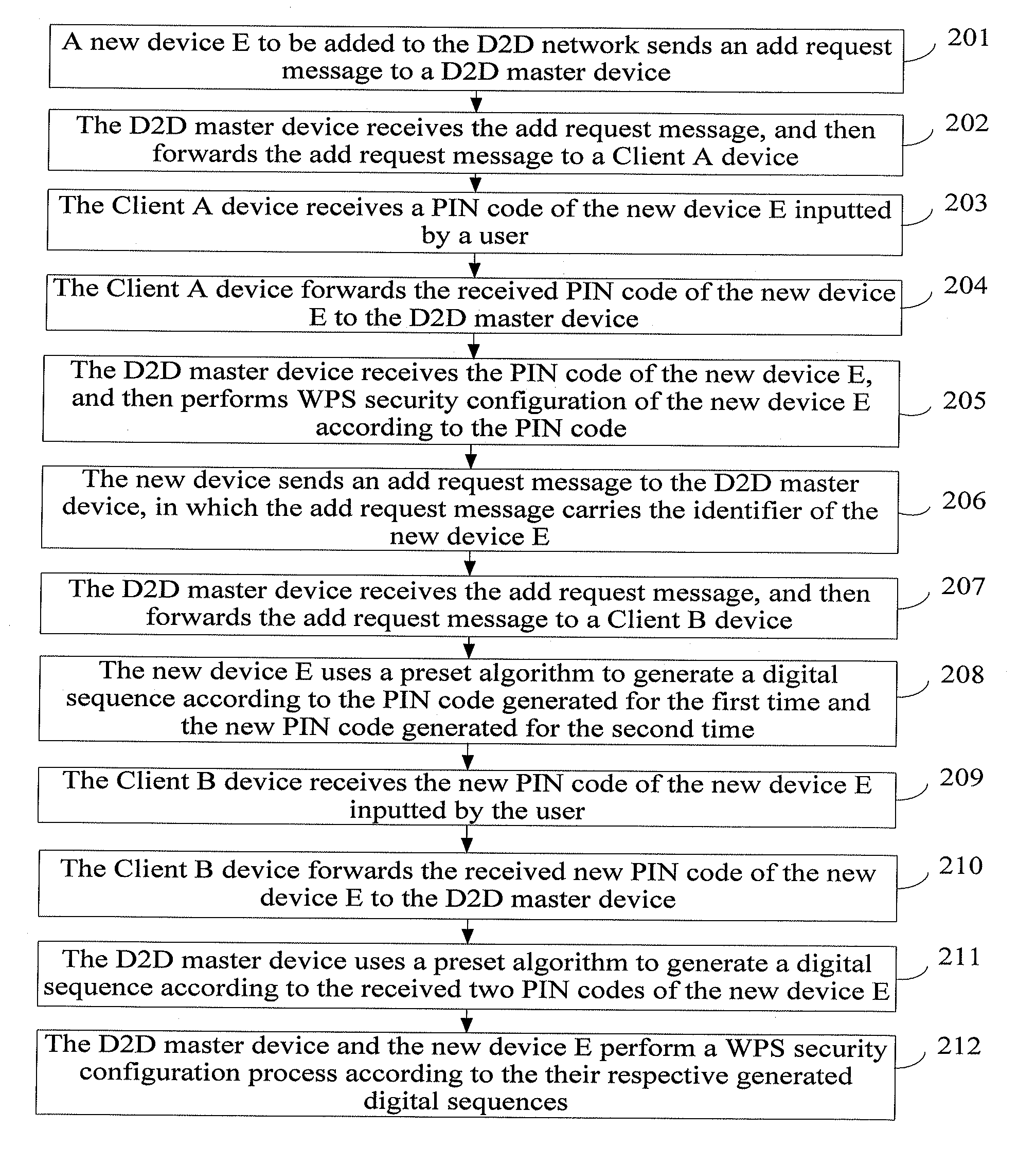
ActiveUS20110271334A1Avoid normal workEnsure work continuityDigital data processing detailsUser identity/authority verificationComputer hardwareWi-Fi
A method, a system, and a device for implementing device addition in a Wireless Fidelity (Wi-Fi) Device to Device (D2D) network are provided, which belong to the field of communication. The method includes: receiving, by a first D2D client device, a first add request message forwarded by a D2D master device, in which the first add request message carries an identifier of a new device to be added to the D2D network; receiving a first Personal Identification Number (PIN) code of the new device; and forwarding the received first PIN code to the D2D master device, in which the first PIN code of the new device is used for implementing that the D2D master device performs Wi-Fi Protected Setup (WPS) security configuration of the new device according to the first PIN code. Therefore, in the Wi-Fi D2D network, when a new device is to be added, a PIN code of the new device inputted by a user is received by the D2D client device, and the PIN code is forwarded to the D2D master device, so that the addition of the new device through the recommendation of the D2D client device is implemented, and the work continuity of the user using the D2D master device is ensured.
Owner:HUAWEI DEVICE CO LTD
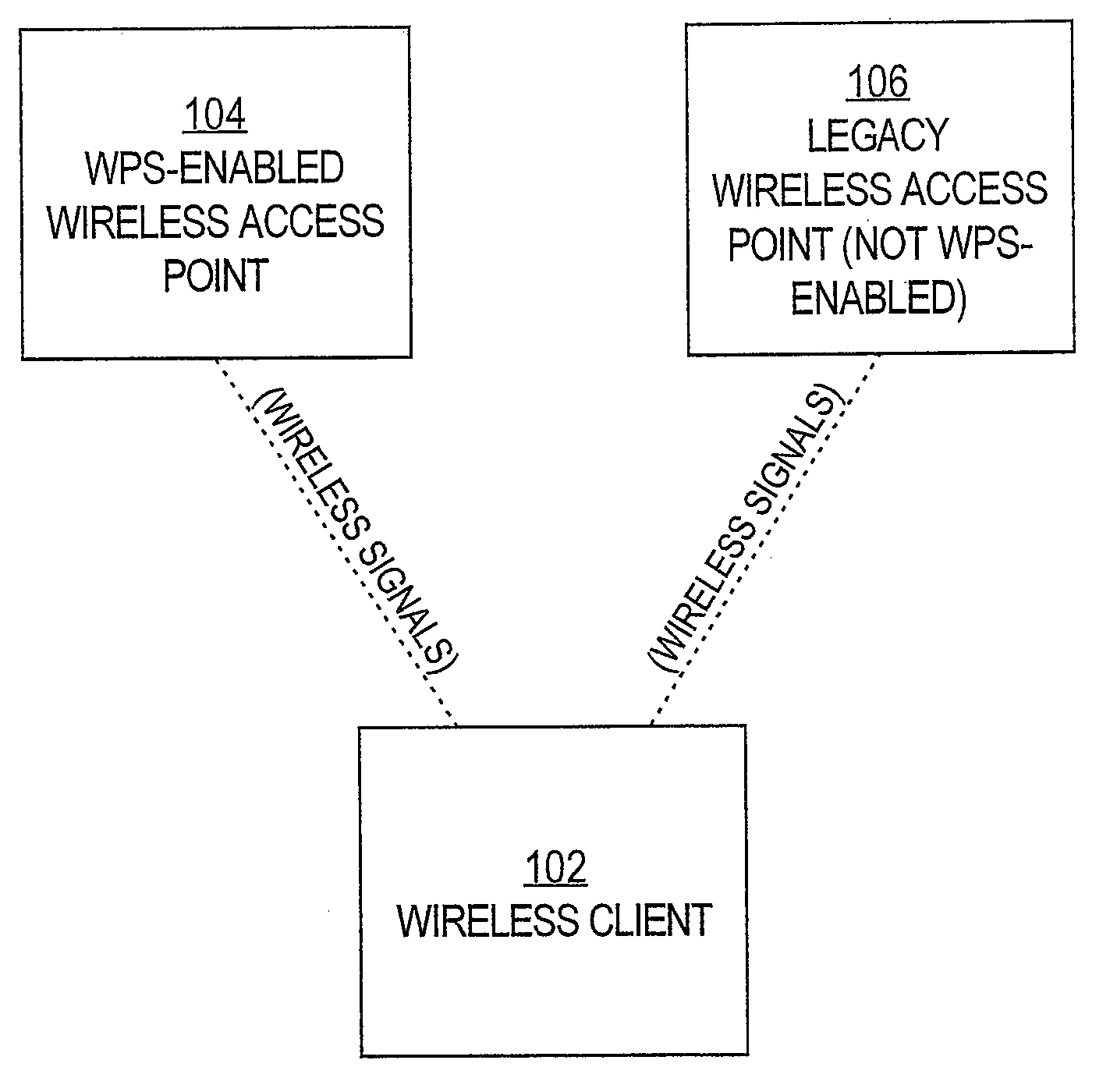
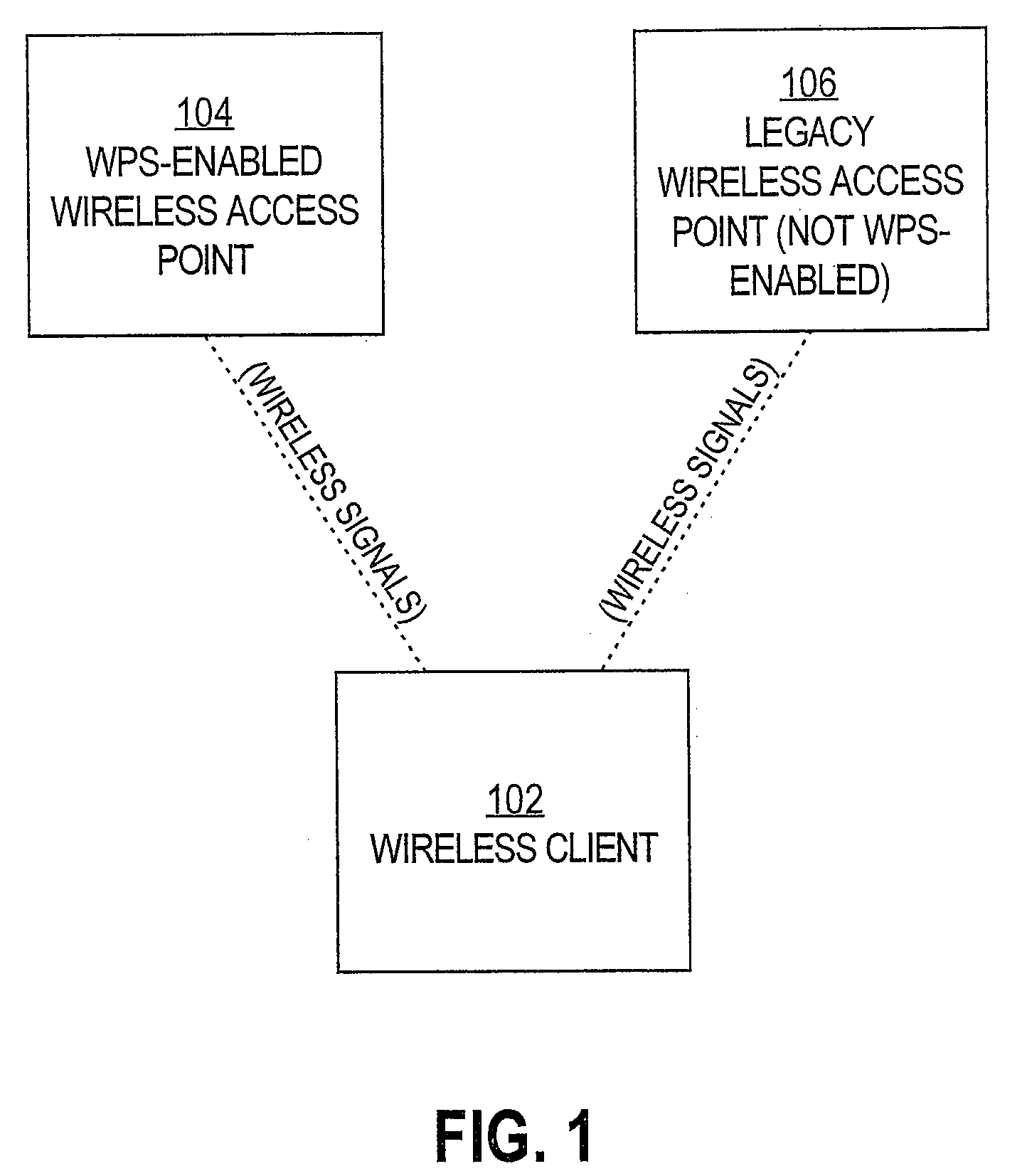
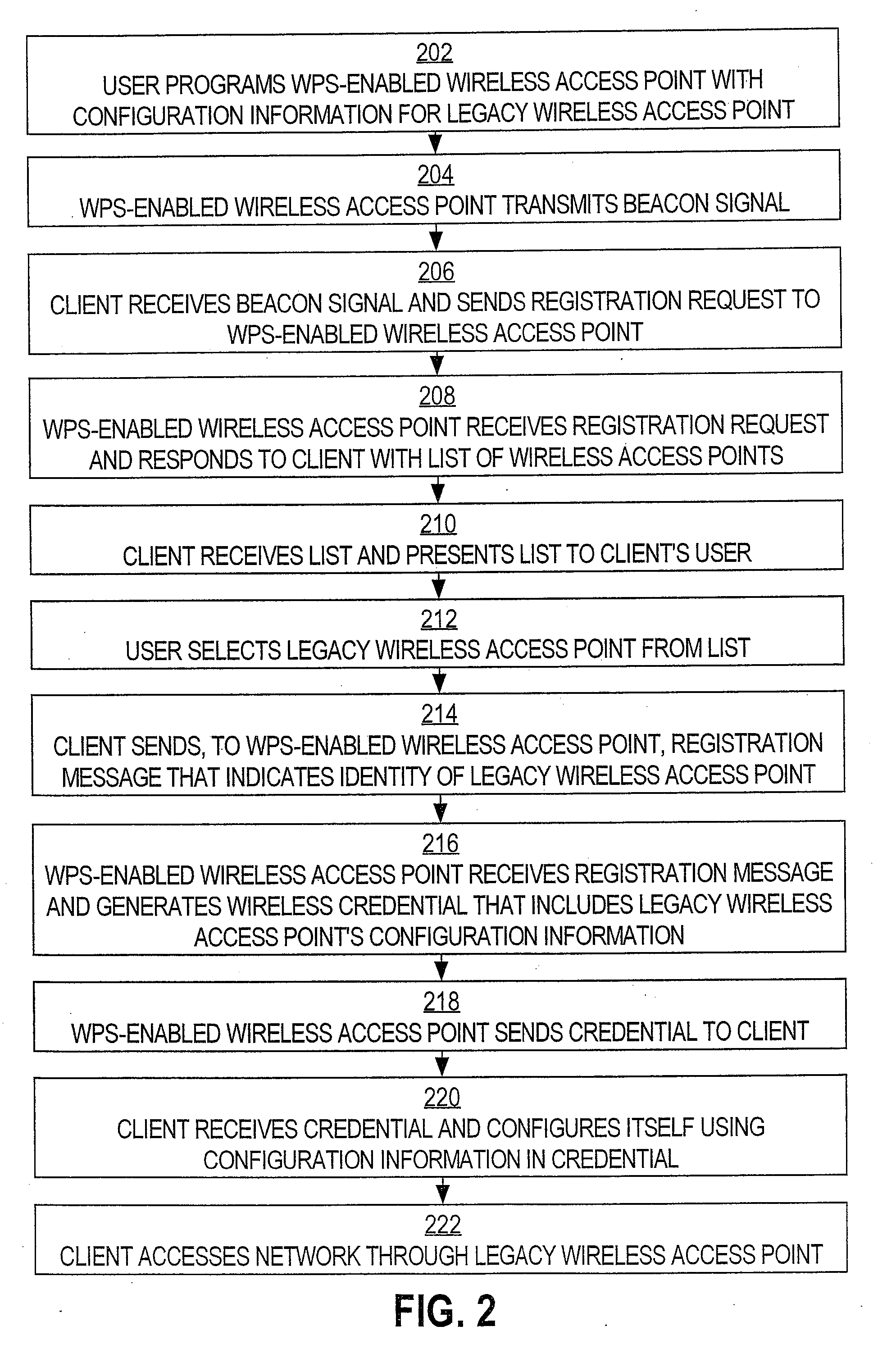
Legacy support for wi-fi protected setup
ActiveUS20090109897A1Assess restrictionData switching by path configurationAuto-configurationComputer science
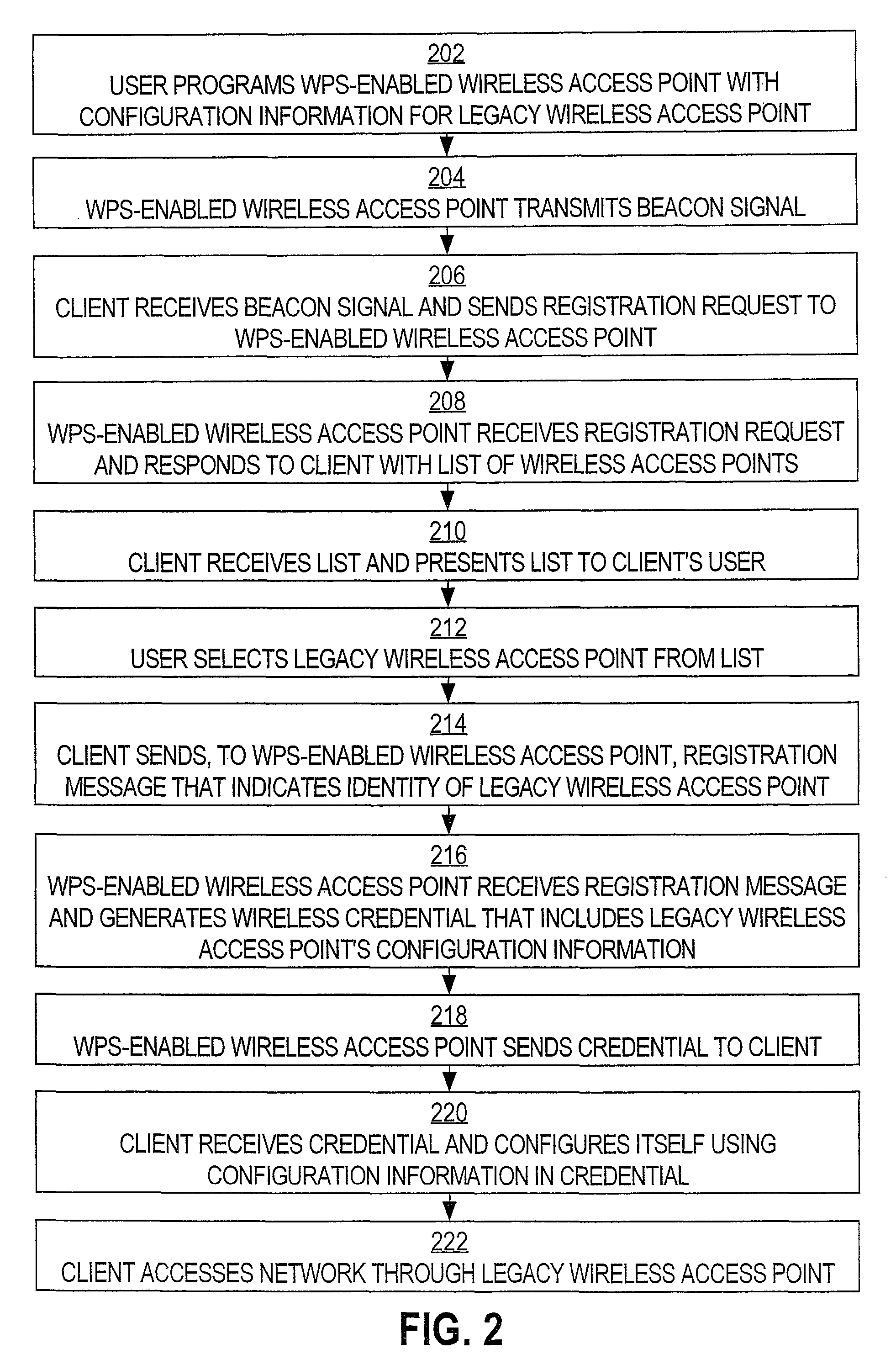
Techniques and systems for automatically configuring devices to interact with “legacy” wireless access points (“WAPs”) are disclosed. According to one technique, a user programs a WPS-enabled WAP with the configuration information of a “legacy” WAP. This makes the WPS-enabled WAP “aware” of the “legacy” WAP. When any other user brings his device within discovery range of the WPS-enabled WAP, the WPS-enabled WAP sends, to that device, a list of the WAPs of which the WPS-enabled WAP is aware. The device's user selects one of the WAPs (e.g., a “legacy” WAP) from the list. The WPS-enabled WAP receives the user's selection and sends, to the device, the configuration information for the selected WAP. The user's device configures itself, using the configuration information, to interact with the selected WAP. Thereafter, the user's device can access a network through the selected WAP, even if the selected WAP is a “legacy” WAP.
Owner:RICOH KK
Wi-fi service method and system for wi-fi devices
ActiveUS20110280233A1Satisfactory Wi-Fi service environmentThe method is simple and convenientNetwork topologiesServices signallingWi-FiAuto-configuration
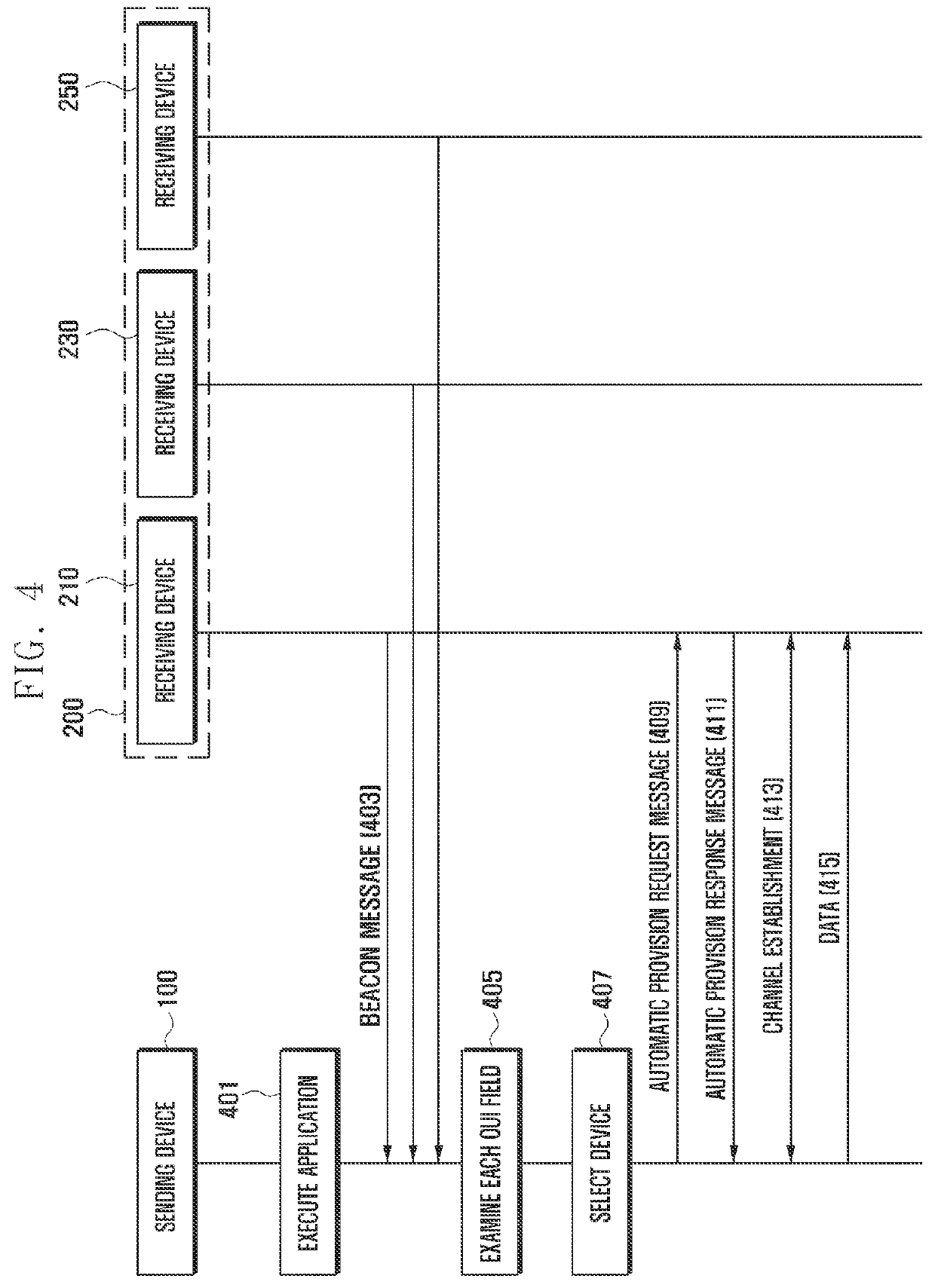
A Wireless-Fidelity (Wi-Fi) service method and system are provided. A beacon message and probe response message may contain a service information field storing device information. Wi-Fi devices can exchange information on supported functions with each other and one Wi-Fi device may identify functions supported by another Wi-Fi device. Hence, a Wi-Fi connection can be set up through automatic provisioning. The method includes receiving, by a first Wi-Fi device in non-Access Point (AP) mode, messages from nearby Wi-Fi devices operating in AP mode, analyzing a service information field of each received message, determining a second Wi-Fi device that is manufactured by the same manufacturer as the first Wi-Fi device and is capable of supporting a requested service, establishing a connection with the second Wi-Fi device through Wi-Fi Protected Setup (WPS) based on automatic provision, and sending data associated with the requested service to the second Wi-Fi device for a Wi-Fi service.
Owner:SAMSUNG ELECTRONICS CO LTD
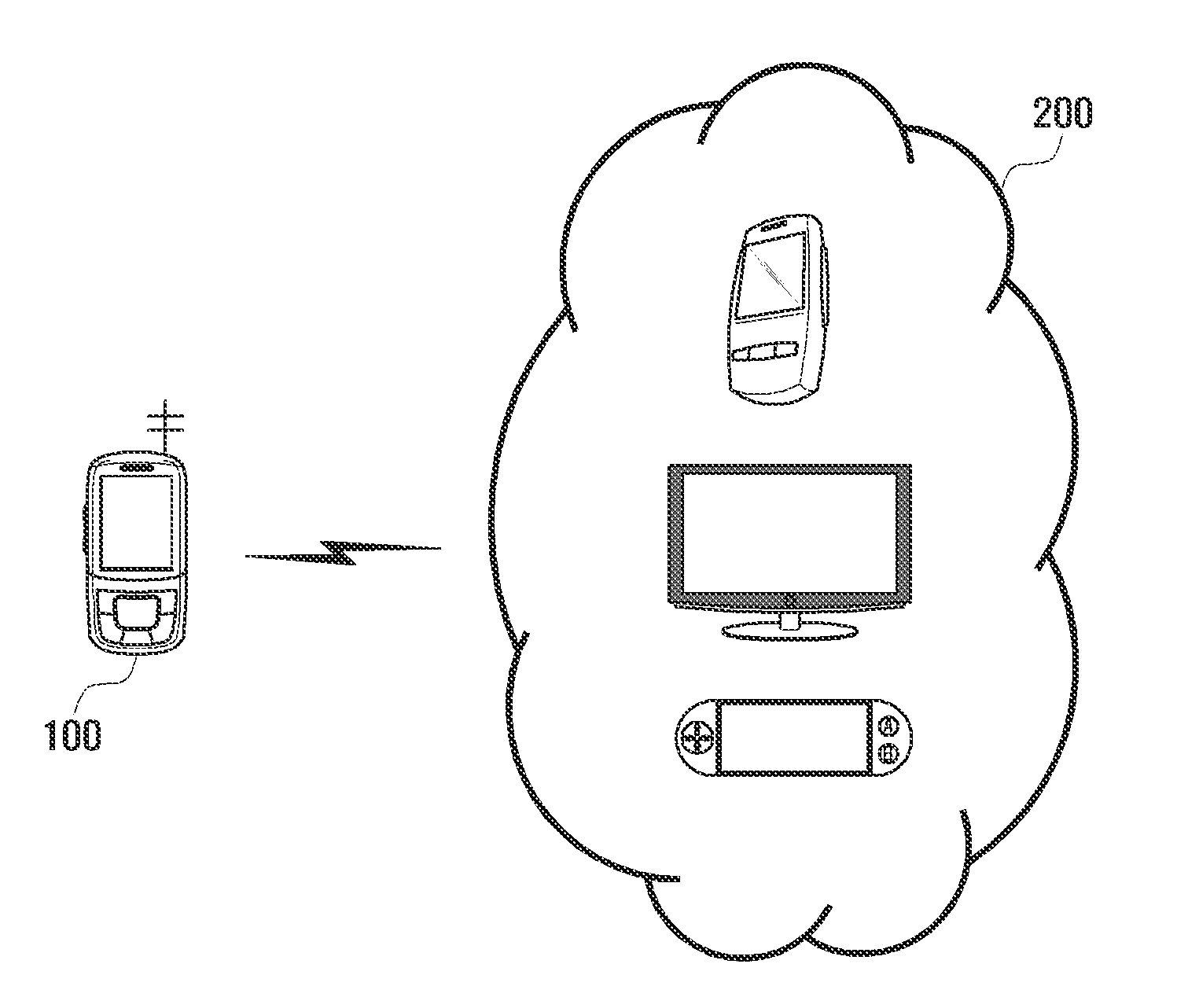
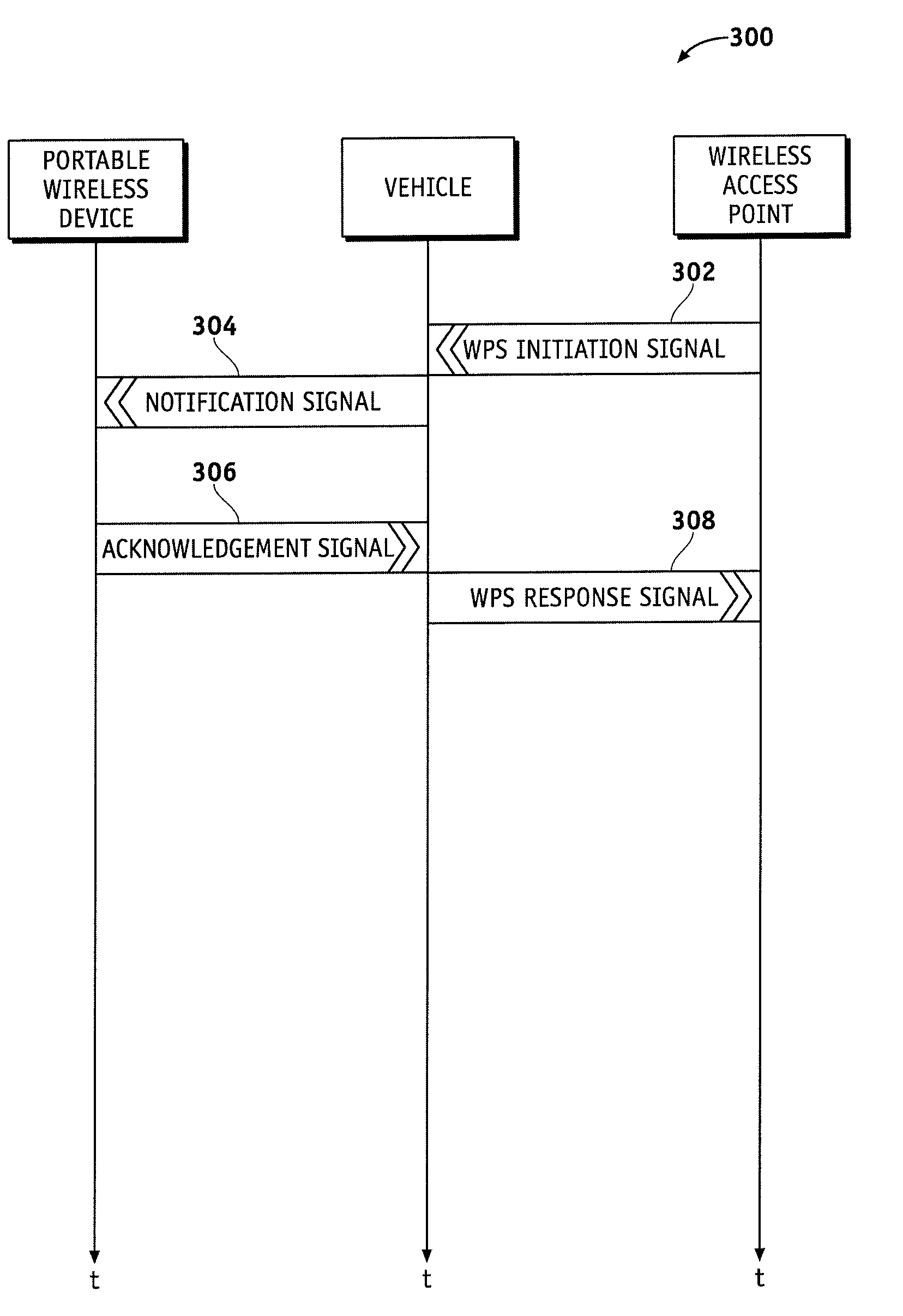
Secure wireless communication initialization system and method
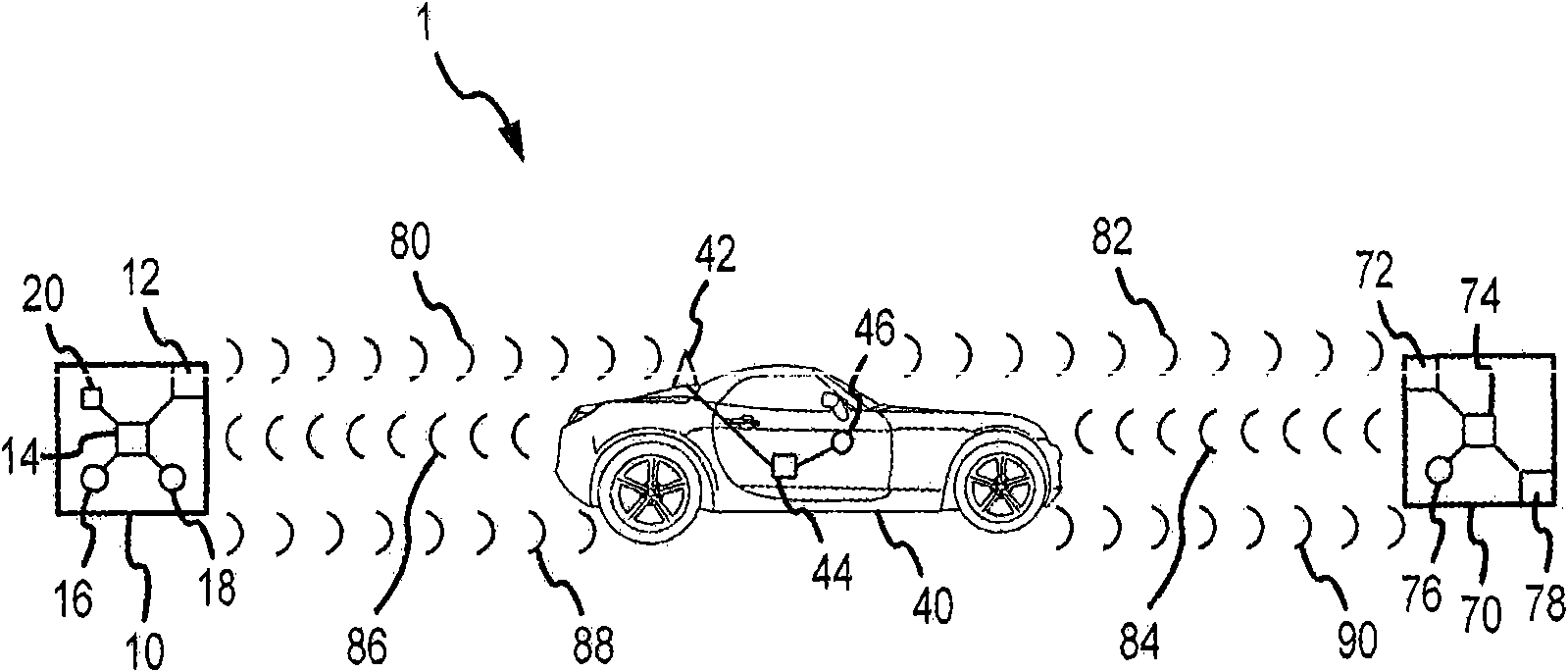
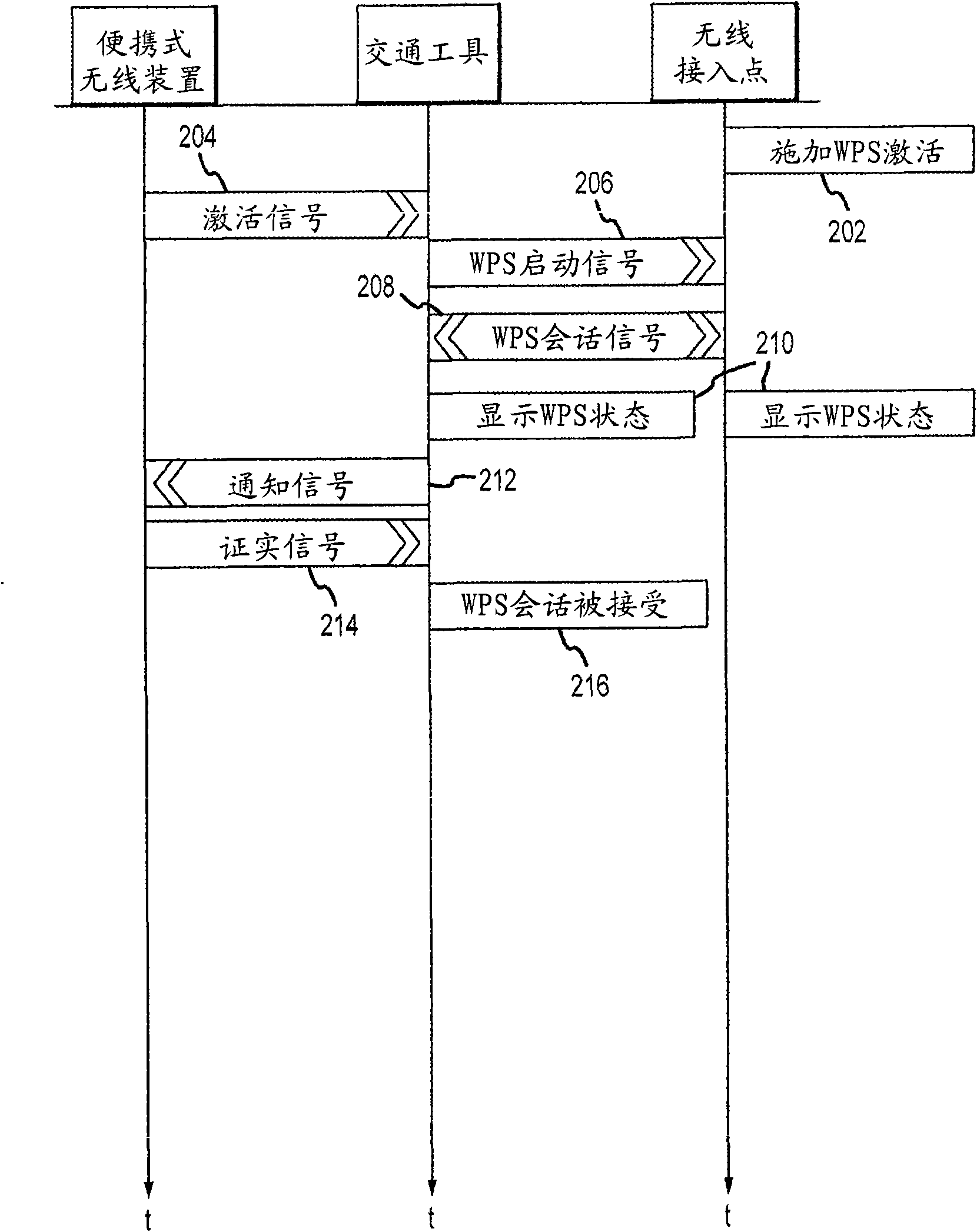
InactiveUS20090328189A1Registering/indicating working of vehiclesUser identity/authority verificationCommunications systemIn vehicle
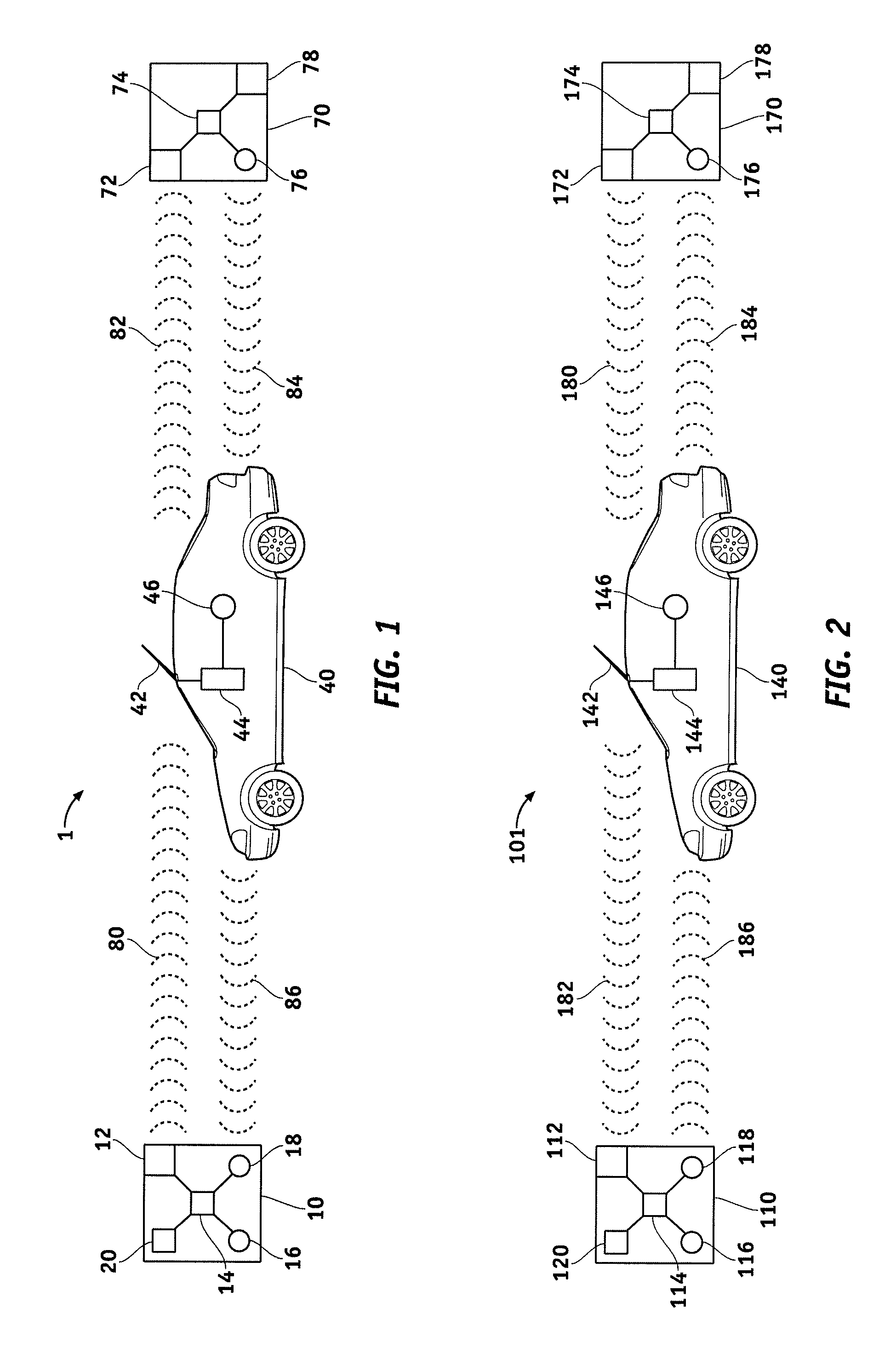
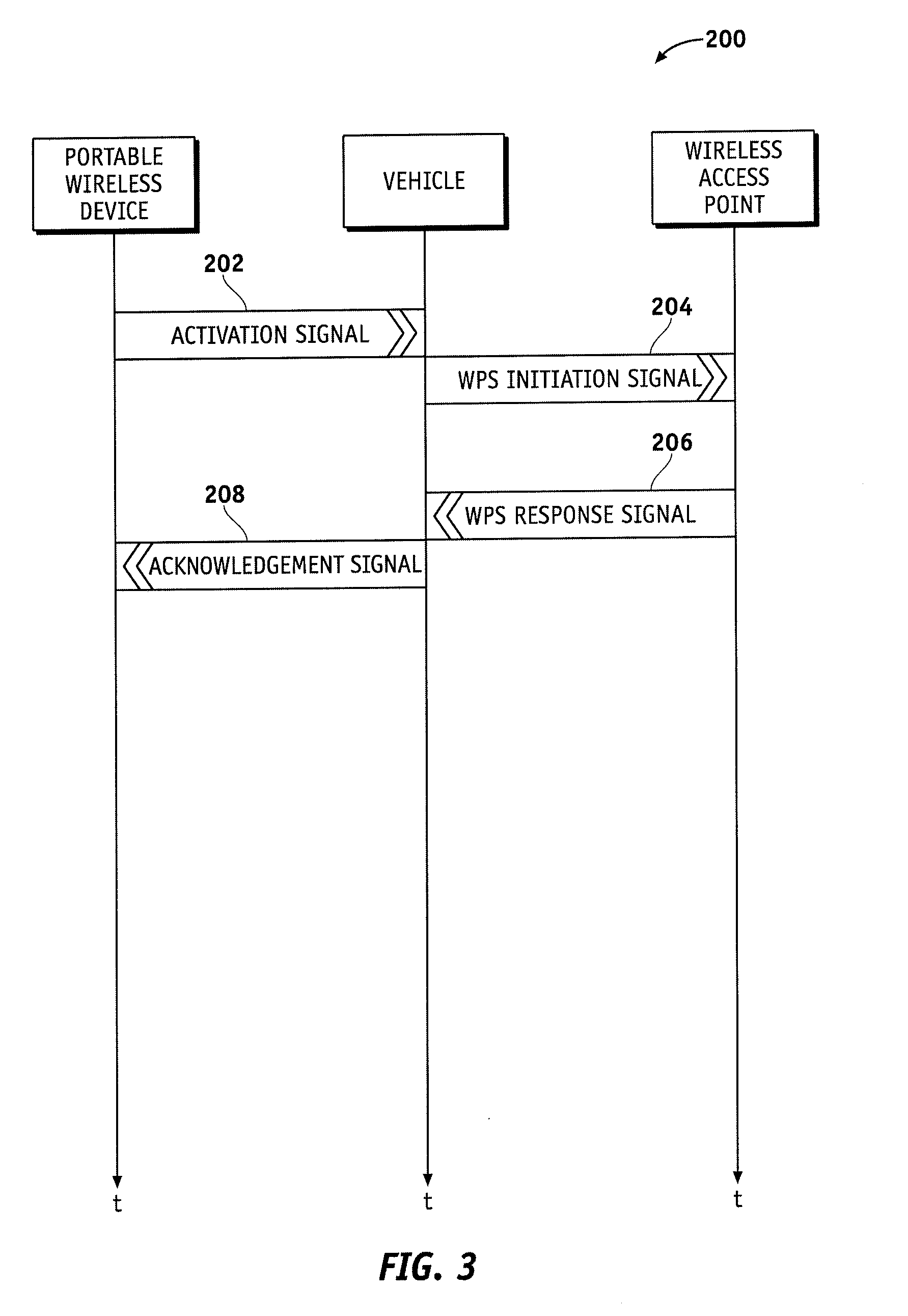
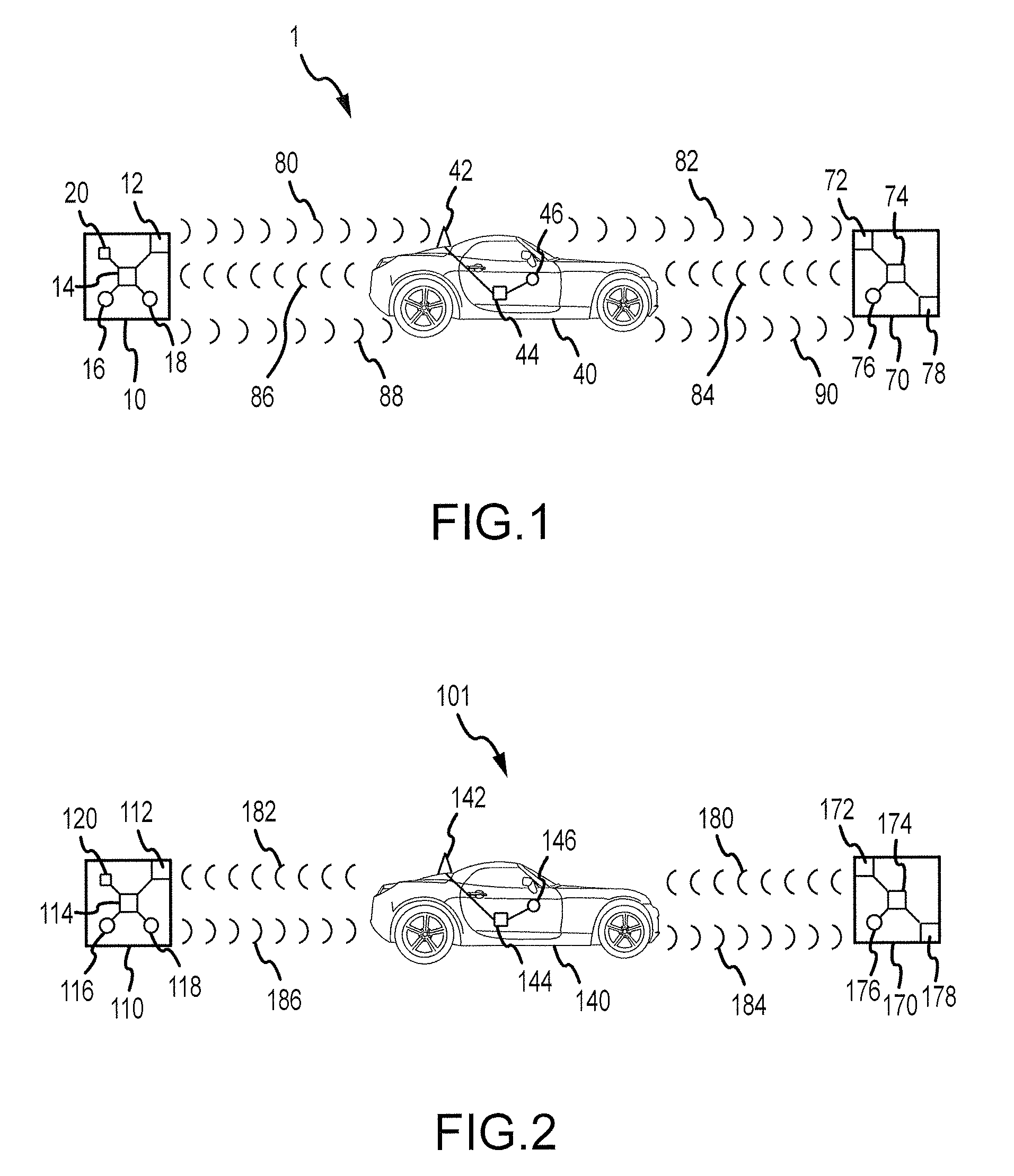
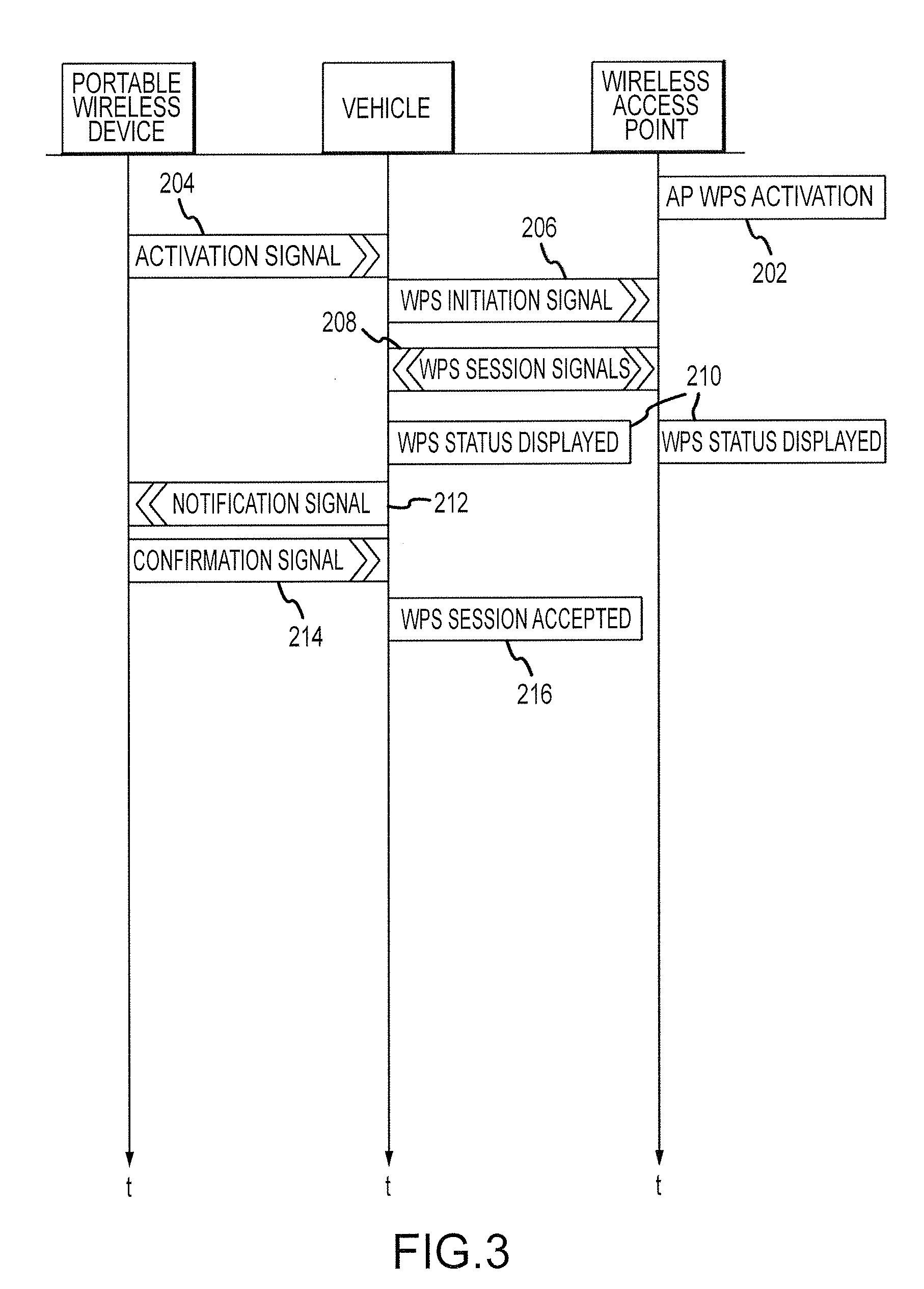
A wireless communication system for use with a vehicle is disclosed. The communication system comprises a portable wireless device comprising a first manual interface device, the portable wireless device adapted to transmit an activation signal in response to manipulation of the first manual interface device, and an onboard wireless communication device for a vehicle. The onboard wireless communication device can be adapted to transmit Wi-Fi Protected Setup initiation signals in response to receiving the activation signal.
Owner:GM GLOBAL TECH OPERATIONS LLC
Secure wireless communication initialization system and method
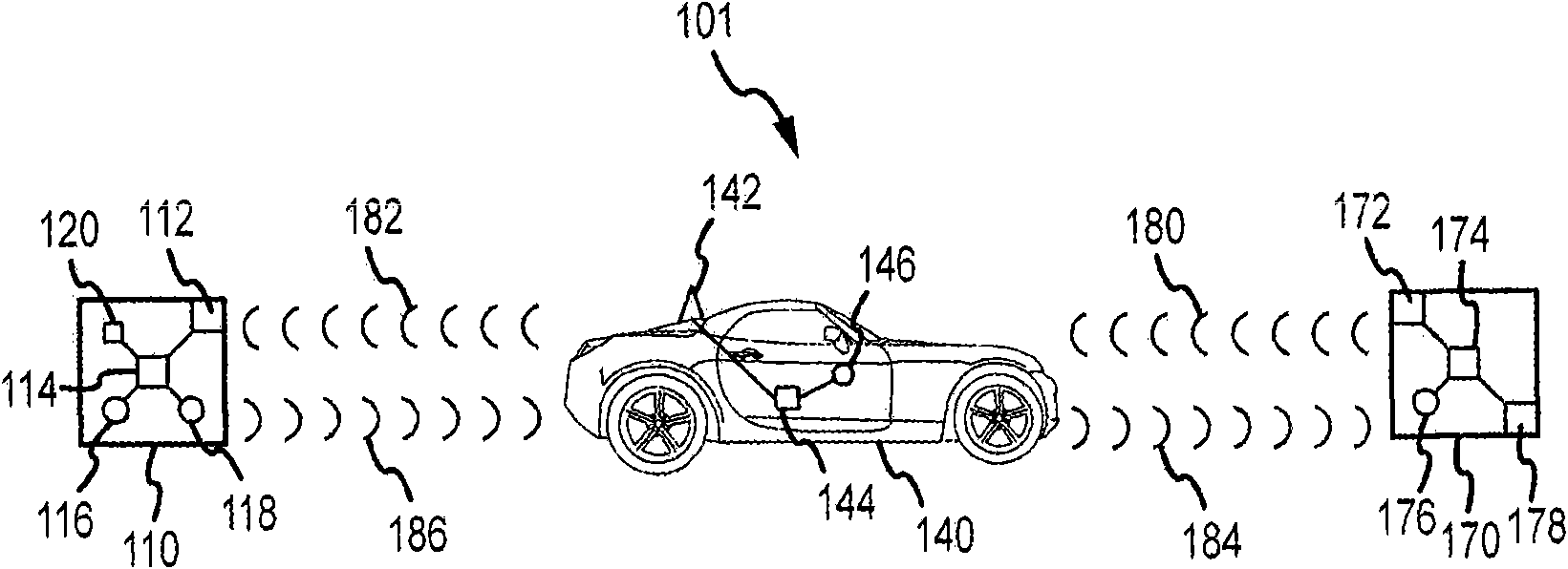
InactiveUS20090291637A1Secure wireless communicationWell formedRadio transmissionSecurity arrangementCommunications systemCommunication device
A wireless communication system for a vehicle is provided. The system comprises a portable wireless device comprising first and second manual interface devices and adapted to transmit a wireless network security protocol confirmation signal in response to manipulation of the first and second manual interface devices, and an onboard wireless communication device for the vehicle, adapted to accept a Wi-Fi Protected Setup (WPS) session outcome in response to receiving the wireless network security protocol confirmation signal.
Owner:GM GLOBAL TECH OPERATIONS LLC
Wireless ad-hoc network configuration method and apparatus
InactiveUS20110044208A1Provide flexibilityDigital data processing detailsUser identity/authority verificationWireless ad hoc networkSelf-organizing network
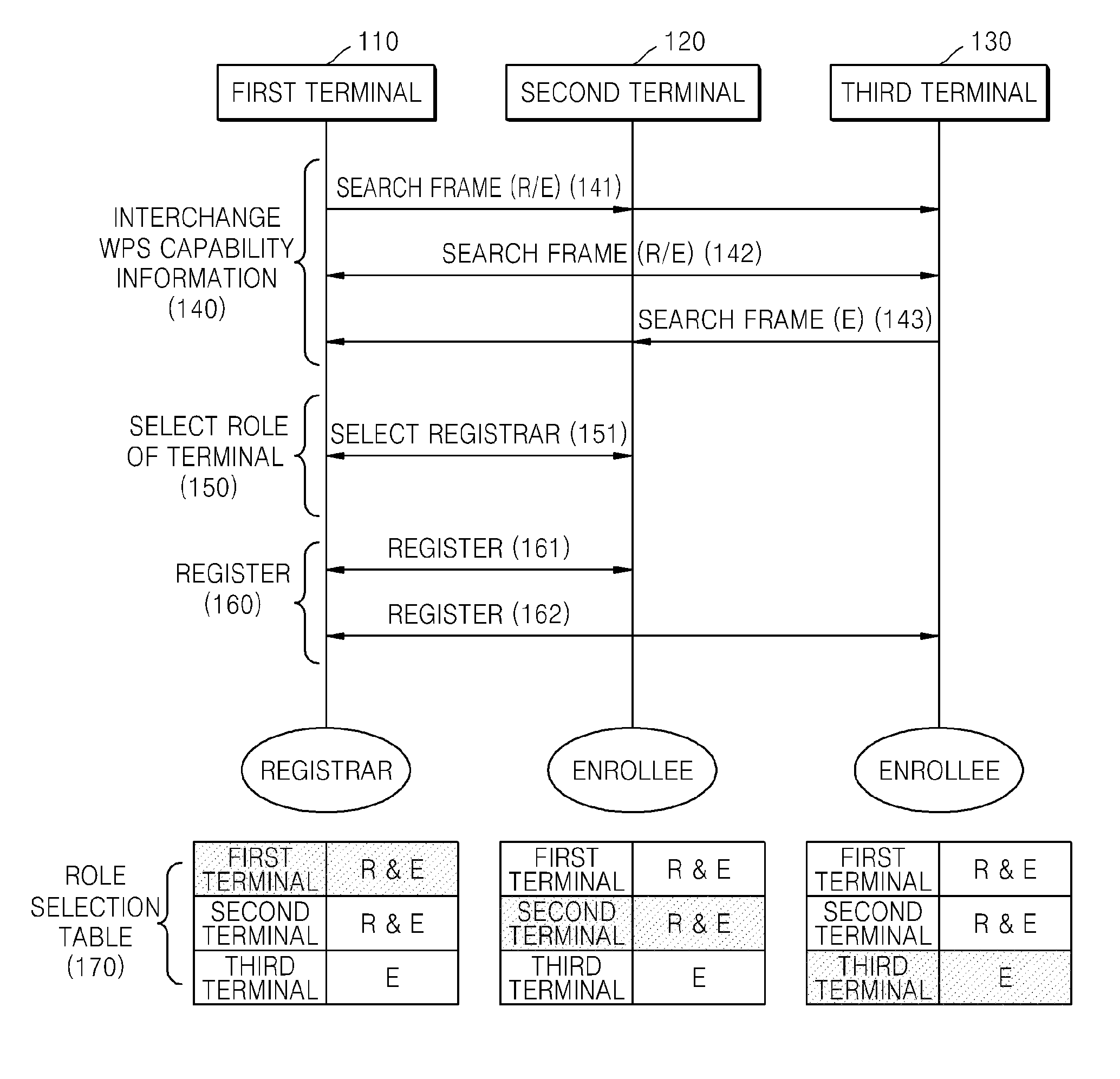
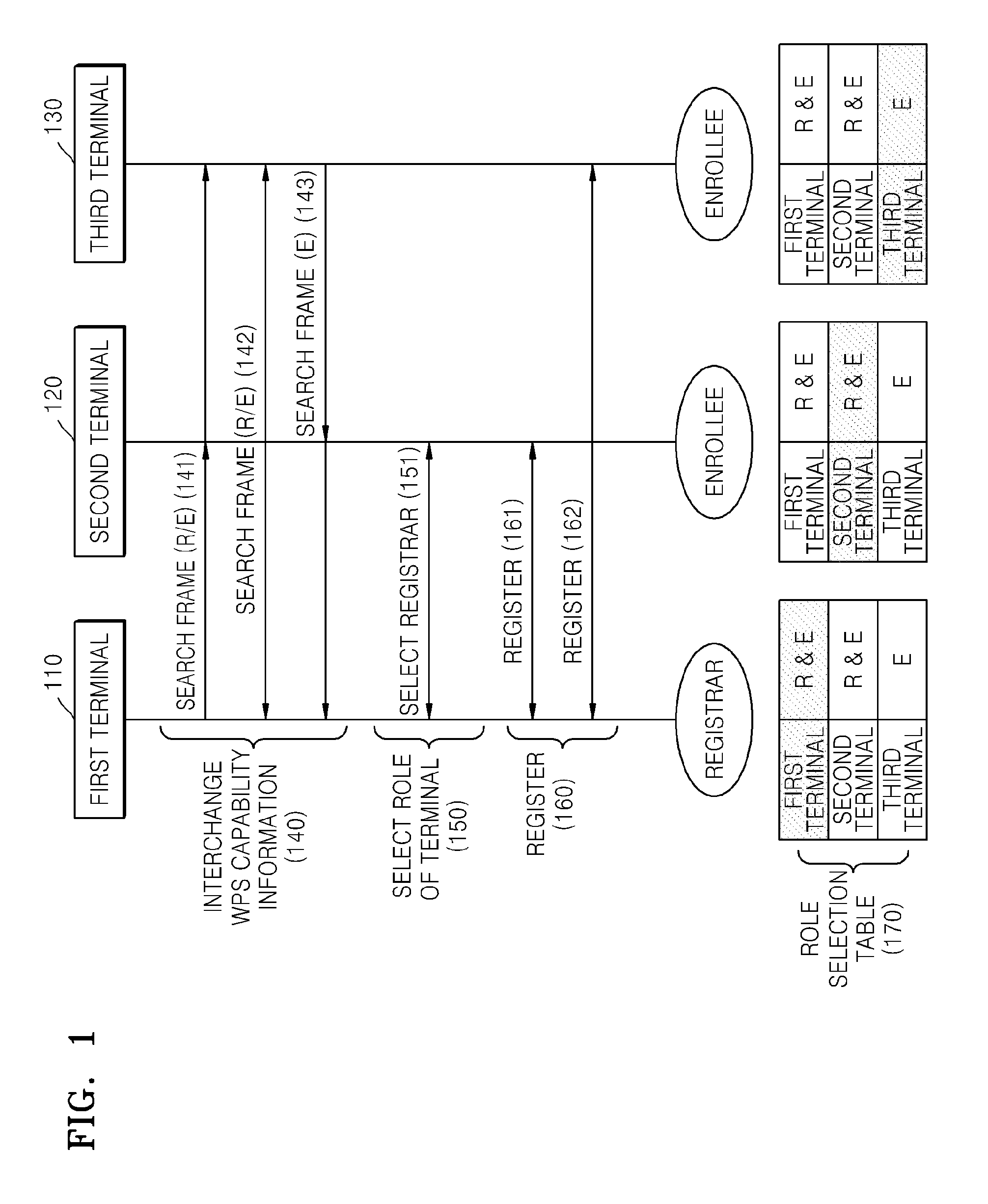
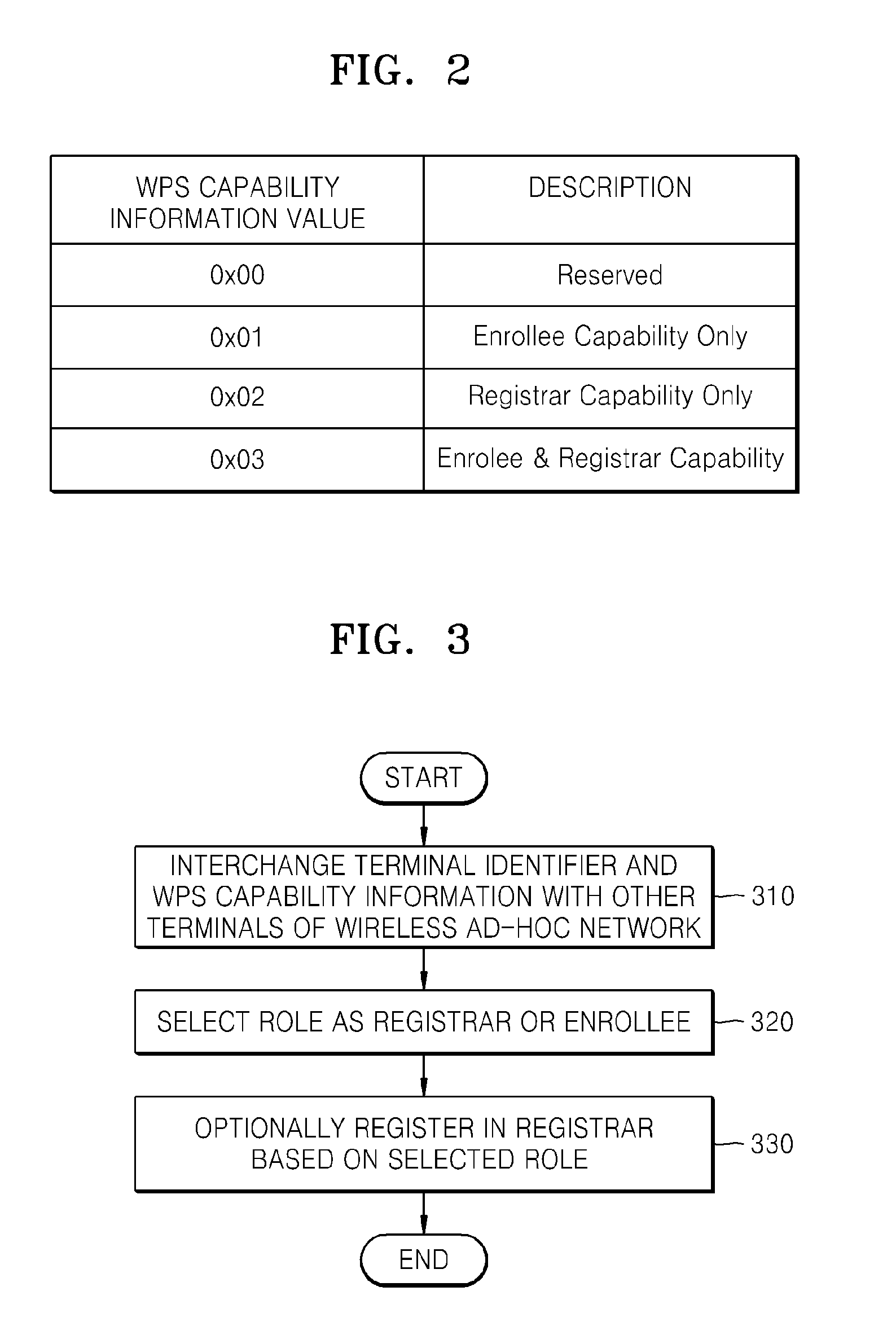
A method and apparatus for setting up a wireless ad-hoc network, the method including: interchanging a terminal identifier and Wi-Fi protected setup (WPS) capability information with other terminals of the wireless ad-hoc network; selecting a role as a registrar or an enrollee based on the interchanged terminal identifier and the interchanged WPS capability information of the wireless ad-hoc network; and optionally registering in the registrar based on the selected role.
Owner:SAMSUNG ELECTRONICS CO LTD
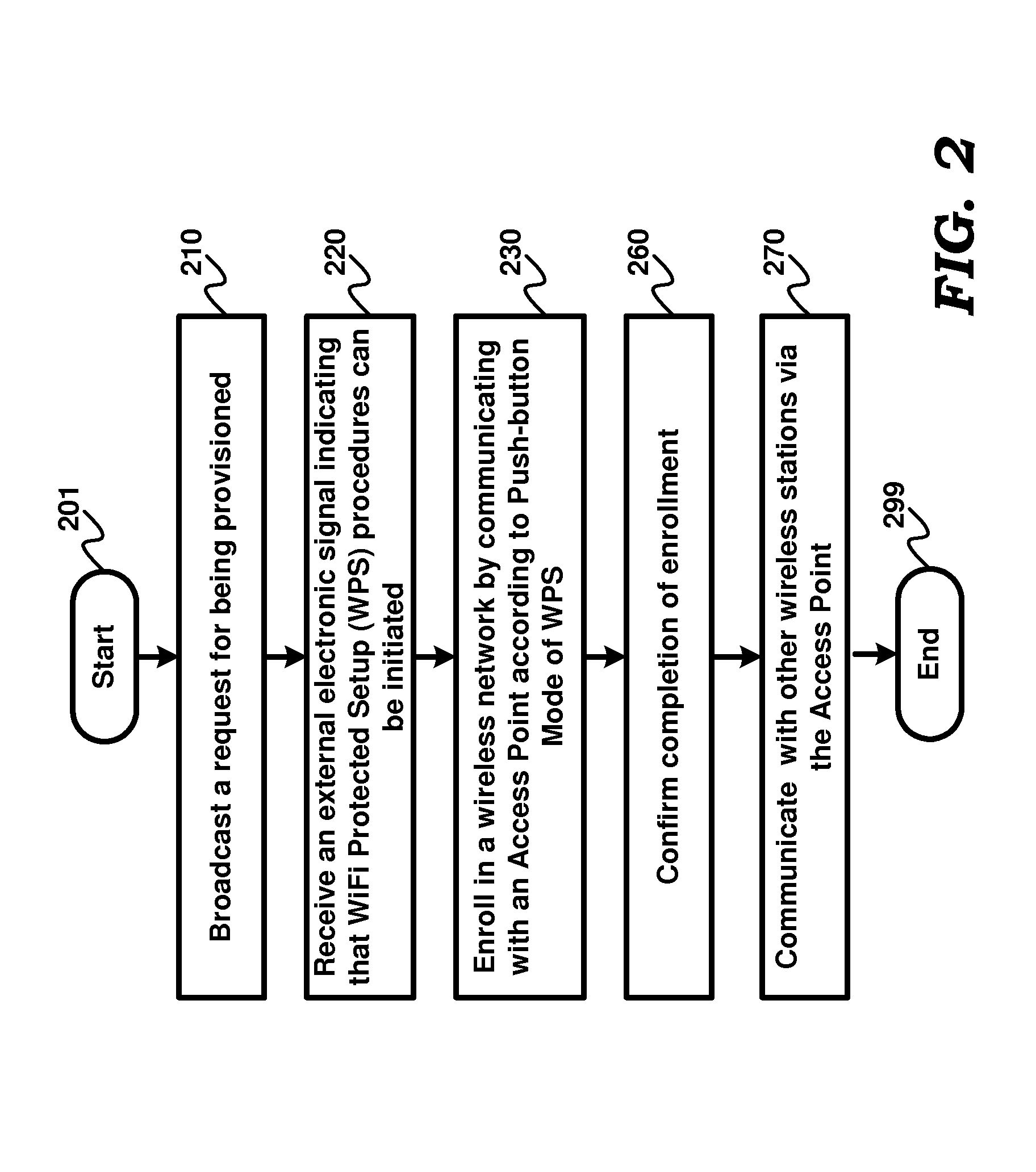
Provisioning a wireless device for secure communication using an access point designed with push-button mode of wps (wi-fi protected setup)
InactiveUS20140328334A1Network topologiesConnection managementSecure communicationRadio access point
A wireless device is provisioned according to WPS (WiFi Protected Setup) push button mode. The wireless device receives an electronic signal from a provisioning agent external to the wireless device, the electronic signal indicating to the wireless device that the wireless device is to start WPS provisioning procedures. A user presses a push button on an AP to which the wireless device is to be connected. On receipt of the electronic signal, the wireless device enrolls in a wireless network, of which the AP is a part, by communicating with the access point in accordance with push button mode of WPS. The technique enables a wireless device to be provisioned without a user requiring to press any button on the wireless device.
Owner:GAINSPAN
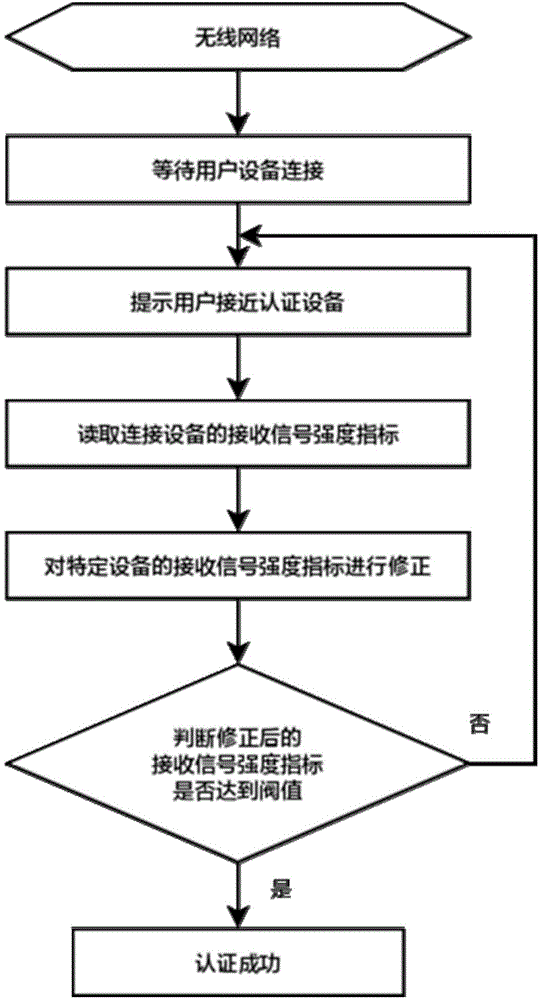
Authentication method based on wireless signal intensity
ActiveCN104540131AImprove convenienceImprove securitySecurity arrangementComputer hardwareWired Equivalent Privacy
The invention discloses an authentication method based on wireless signal intensity. The wireless signal intensity of wireless network equipment is read, whether the wireless signal intensity reaches a set threshold value or not is judged, the equipment is authenticated when the wireless signal intensity reaches the threshold value, and the wireless signal intensity continues being read and judged if the wireless signal intensity does not reach the threshold value; in addition, the threshold value can be corrected according to the network equipment of different kinds, and the method is more flexible and more convenient to implement. By the adoption of the technical scheme, the method can be combined with a secret-key-free open network mechanism, cooperation of the secret-key-free open network mechanism and a mobile communication equipment short message authentication mechanism, a WEP encryption authentication mechanism, a WPA encryption authentication mechanism, a WPA2 encryption authentication mechanism and a WPS encryption authentication mechanism, and is an effective measure for further enhancing safety.
Owner:深圳市鑫博创科技有限公司
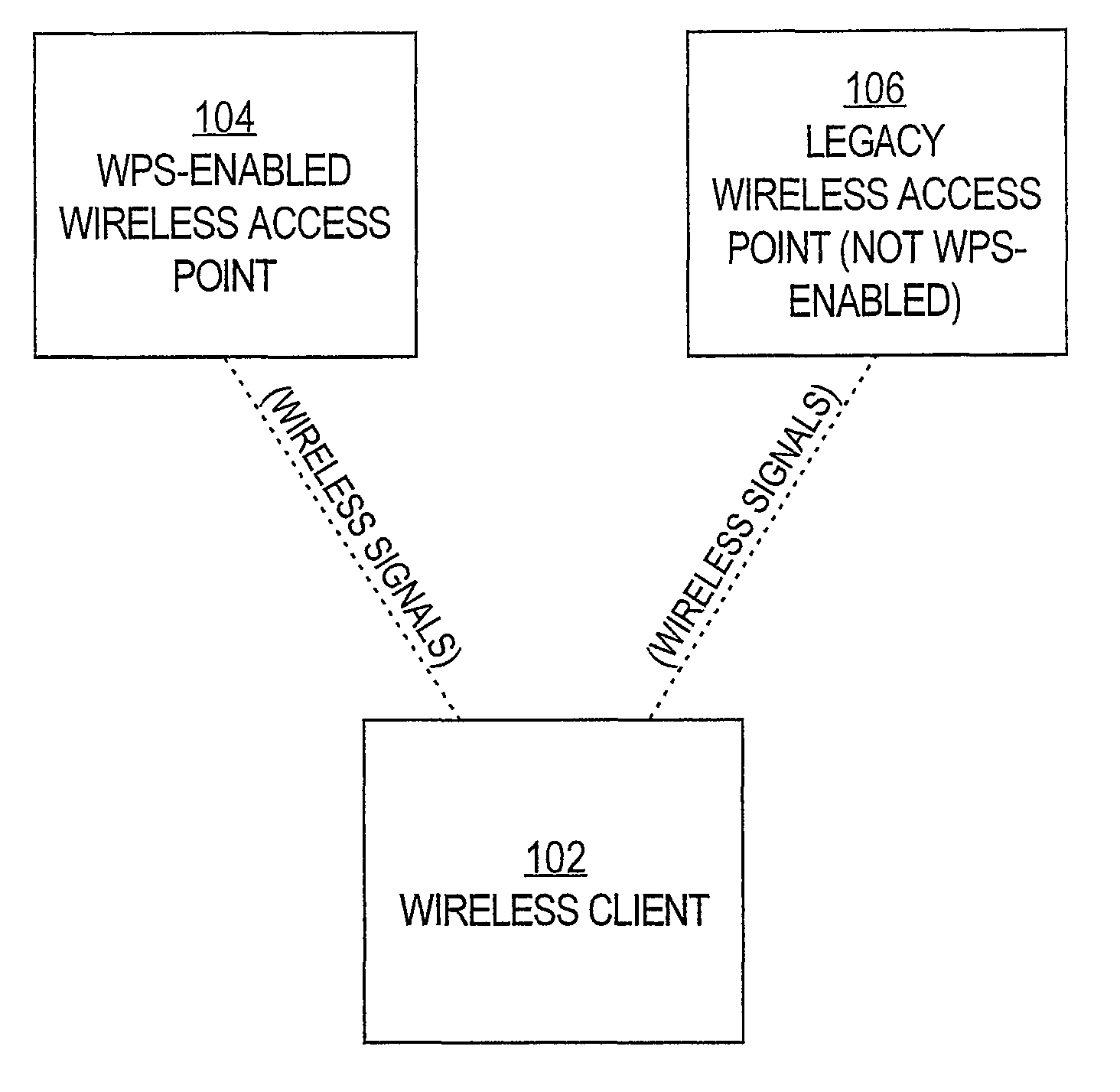
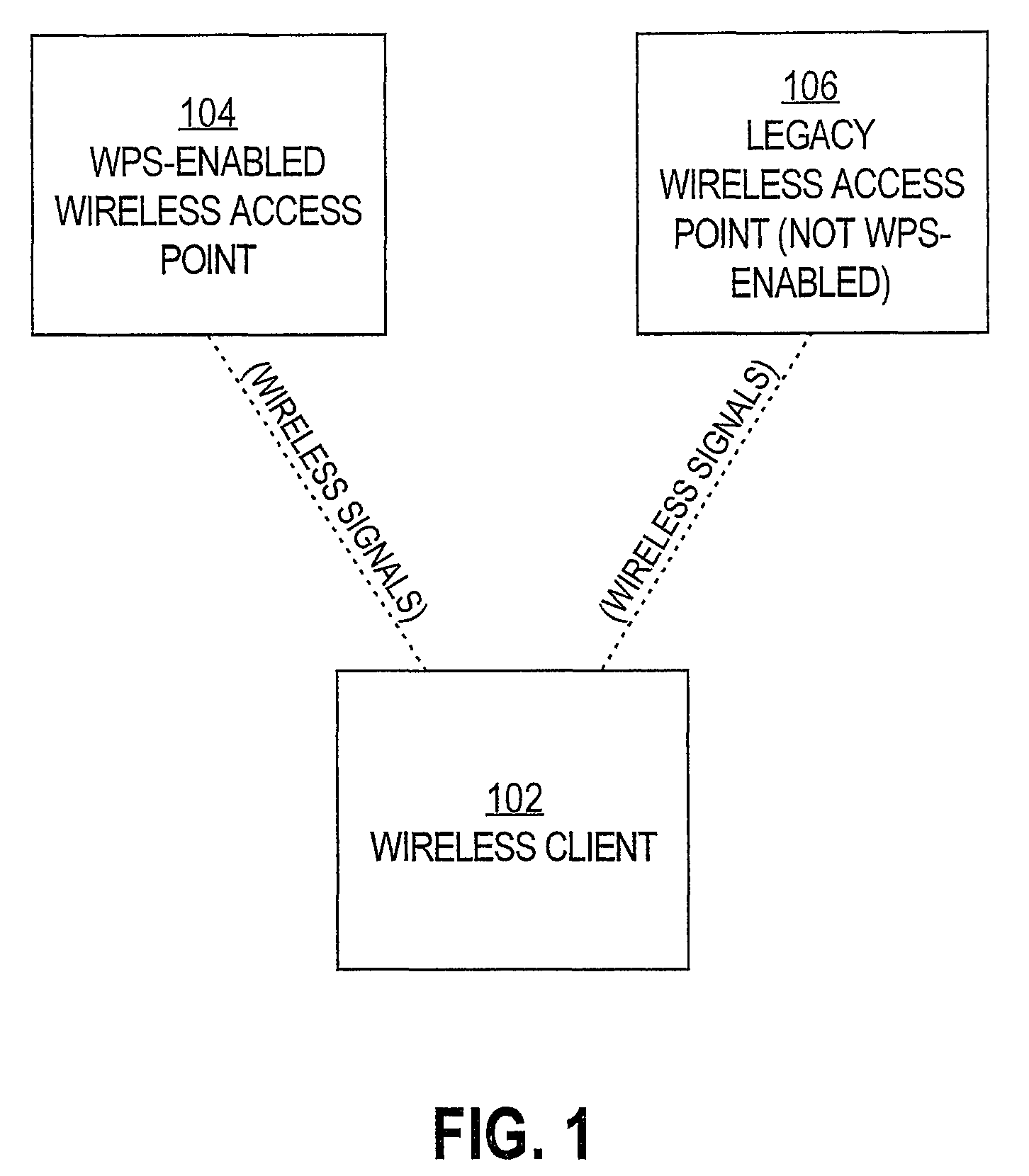
Wireless provisioning a device for a network using a soft access point
ActiveUS8625552B2Improve usabilityImprove user experienceAssess restrictionNetwork topologiesUser inputRogue access point
A computing device for provisioning a wireless device for connection to a wireless network via a legacy access point. The wireless device supports a wireless protected setup protocol for obtaining the network profile of the network. A user requests the computing device discover wireless devices for provisioning. In response to the user input, the computing device is configured as a soft access point and broadcasts a beacon signal indicating that the access point supports a wireless protected setup protocol, such as Wi-Fi Protected Setup. A request for provisioning is then received by the computing device from the wireless device. A network profile is transmitted from the computing device to the wireless device in accordance with the wireless protected setup protocol. The wireless device may use the profile to connect to the network via the legacy access point using the network profile.
Owner:MICROSOFT TECH LICENSING LLC
Security protection method for PIN (Personal Identification Number) code access mode
ActiveCN102624725AImprove securityAchieve lockingTransmissionSecurity arrangementPersonal identification numberWi-Fi Protected Setup
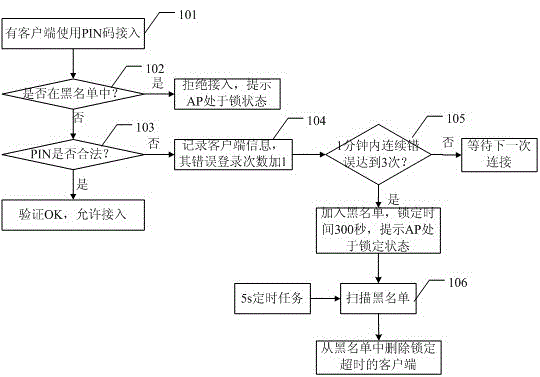
The invention provides a security protection method for a PIN (Personal Identification Number) code access mode. The security protection method includes the following steps: a blacklist is established and initialized to be empty; when a client end is detected to use a PIN code for access, whether the client end is in the blacklist is judged; if the client end is in the blacklist, then the access is denied; if the client end is not in the blacklist, then the next step is executed; whether the PIN code provided by the client end is valid is judged; if the PIN code is valid, then the access of the client end is allowed; if the PIN code is invalid, the access is denied, and the next step is executed; the information of the client end is recorded, and whether the client end meets preset blacklisting conditions is judged; if the client end meets the preset blacklisting conditions, then the client end is added into the blacklist; and if the client end does not meet the preset blacklisting conditions, the client end waits for the next connection. Since the blacklist mechanism is introduced into the security protection method, a certain client end can be added into the blacklist when the failure of the PIN code access of the client end meets the preset conditions, and thereby is locked, consequently, while the security protection method can ensure that the accesses of normal client ends can be normal, all malicious attackers can be locked, and thereby the security of WPS (Wi-Fi Protected Setup) is further enhanced.
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
Method and apparatus for Wi-Fi connection using Wi-Fi protected setup in portable terminal
Owner:SAMSUNG ELECTRONICS CO LTD
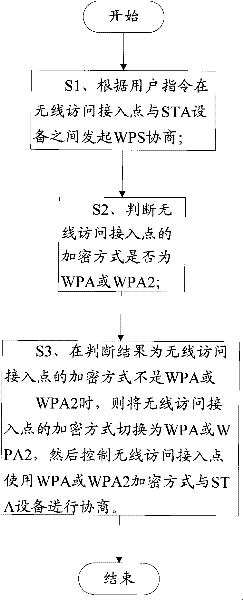
Method and device for performing negotiation according to Wi-Fi protected setup (WPS) protocol
InactiveCN102215483AHigh degree of automationSolve technical problems that are difficult to operateNetwork traffic/resource managementWireless network protocolsWi-Fi Protected AccessWireless access point
The embodiment of the invention discloses a method and a device for performing negotiation according to a Wi-Fi protected setup (WPS) protocol, which belong to the technical field of communication and solve the technical problems of troubles in operation in the prior art. The method for performing the negotiation according to the WPS protocol comprises the following steps of: initiating WPS negotiation between a wireless access point and station (STA) equipment according to a user instruction; judging whether the encryption way of the wireless access point is Wi-Fi protected access (WPA) or WPA2; and if a judgment result indicates that the encryption way of the wireless access point is not the WPA or the WPA2, switching the encryption way of the wireless access point into the WPA or the WPA2, and controlling the wireless access point to negotiate with the STA equipment by using the WPA or WPA2 encryption way. The device for performing the negotiation according to the WPS protocol comprises a negotiation initiation unit, a way judgment unit and a way switching unit. The method and the device are applied to the negotiation according to the WPS protocol.
Owner:HUAWEI DEVICE CO LTD
Legacy support for Wi-Fi protected setup
ActiveUS8199699B2Unauthorised/fraudulent call preventionAssess restrictionAuto-configurationComputer science
Techniques and systems for automatically configuring devices to interact with “legacy” wireless access points (“WAPs”) are disclosed. According to one technique, a user programs a WPS-enabled WAP with the configuration information of a “legacy” WAP. This makes the WPS-enabled WAP “aware” of the “legacy” WAP. When any other user brings his device within discovery range of the WPS-enabled WAP, the WPS-enabled WAP sends, to that device, a list of the WAPs of which the WPS-enabled WAP is aware. The device's user selects one of the WAPs (e.g., a “legacy” WAP) from the list. The WPS-enabled WAP receives the user's selection and sends, to the device, the configuration information for the selected WAP. The user's device configures itself, using the configuration information, to interact with the selected WAP. Thereafter, the user's device can access a network through the selected WAP, even if the selected WAP is a “legacy” WAP.
Owner:RICOH KK
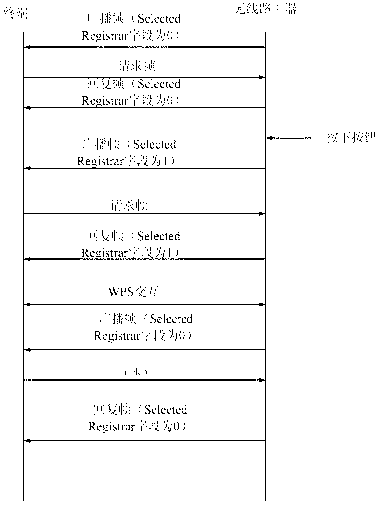
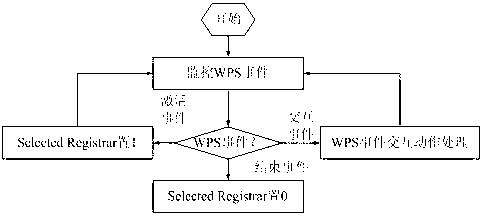
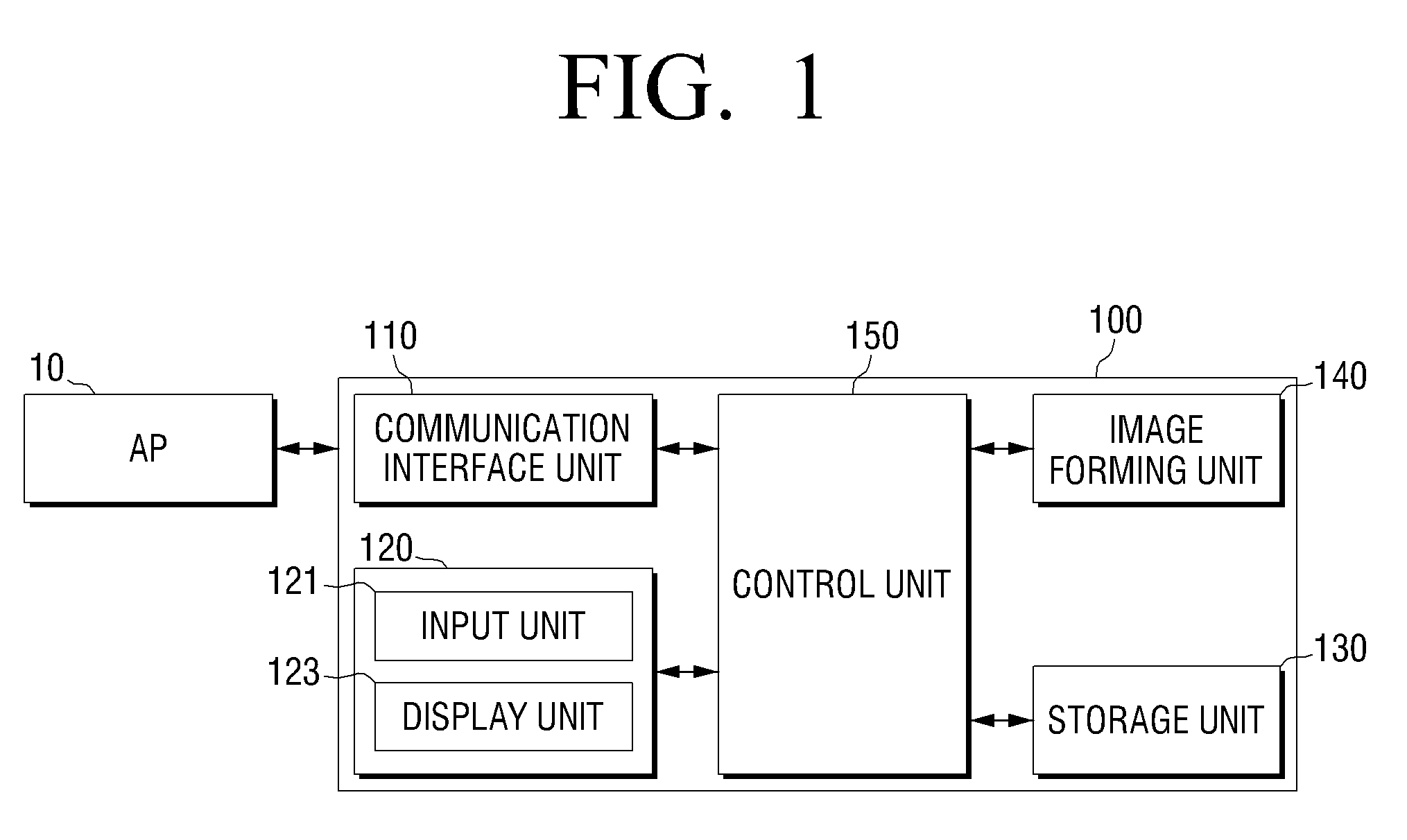
Image forming apparatus and method for setting wireless LAN thereof
A method and apparatus for setting up a wireless LAN. The method includes receiving a packet, which informs a user that a WPS (Wi-Fi Protected Setup) button of an access point is operated, from the access point; activating a button provided in an image forming apparatus as a WPS button; selecting a button activated as the WPS button; and if the button activated as the WPS button is selected, establishing a wireless network with the access point.
Owner:HEWLETT PACKARD DEV CO LP
Image forming apparatus and method for setting wireless lan thereof
A method for setting a wireless LAN is provided, which includes receiving a packet, which informs a user that a WPS (Wi-Fi Protected Setup) button of an access point is operated, from the access point; activating a button provided in an image forming apparatus as a WPS button; selecting a button activated as the WPS button; and if the button activated as the WPS button is selected, constructing a wireless network with the access point.
Owner:HEWLETT PACKARD DEV CO LP
Apparatus and method for improving capability of wi-fi in wireless communication system
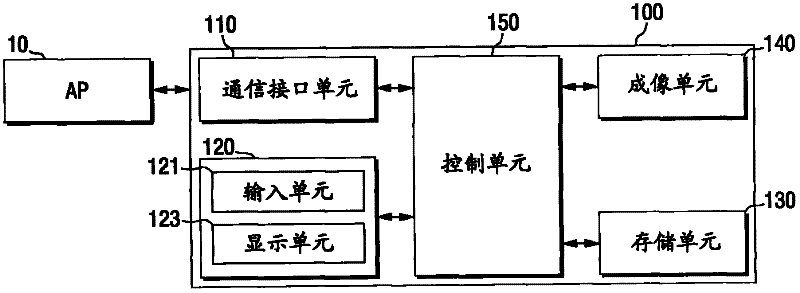
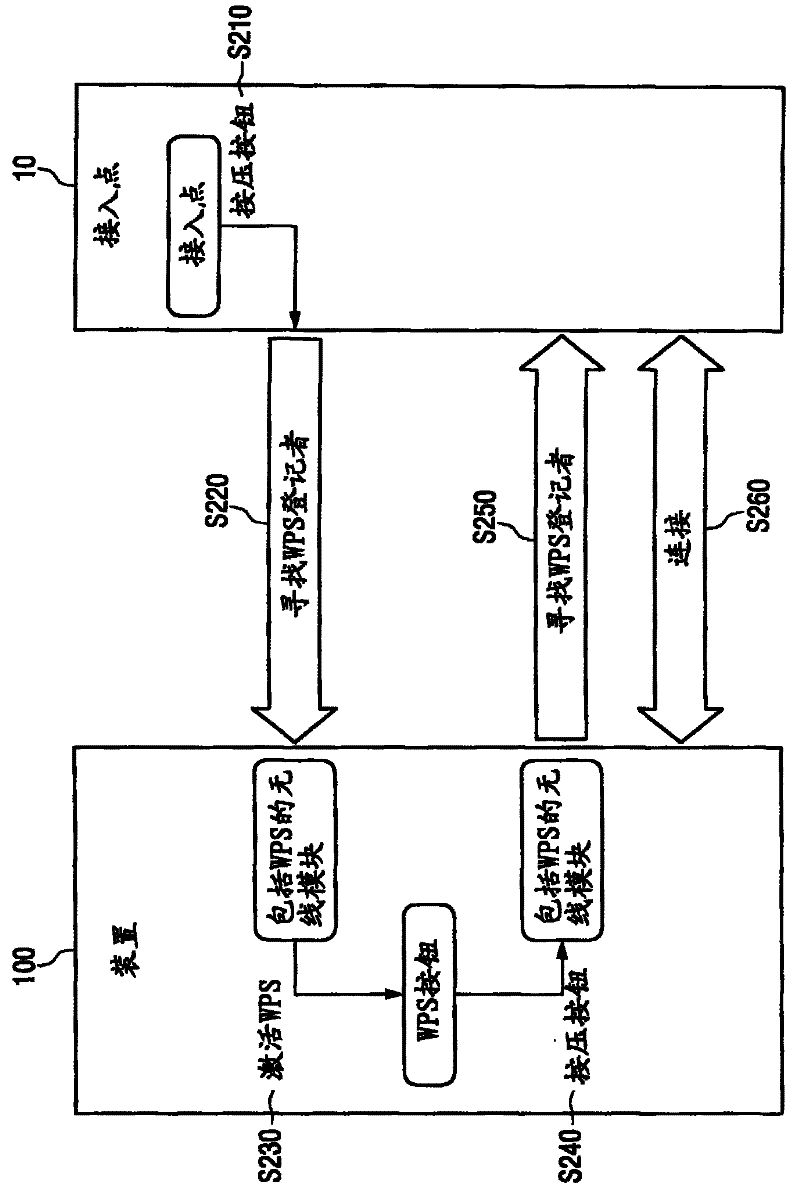
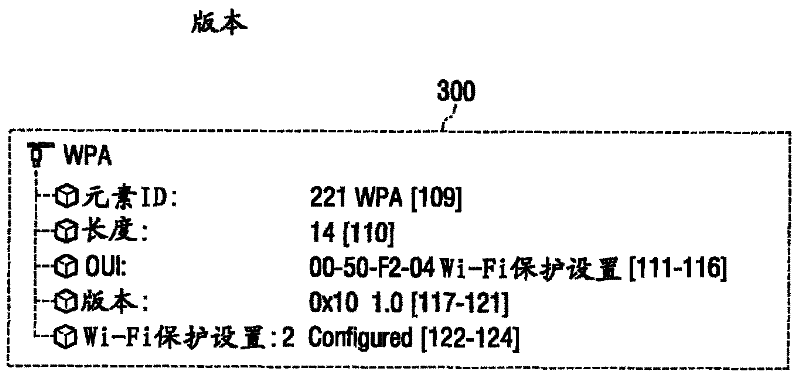
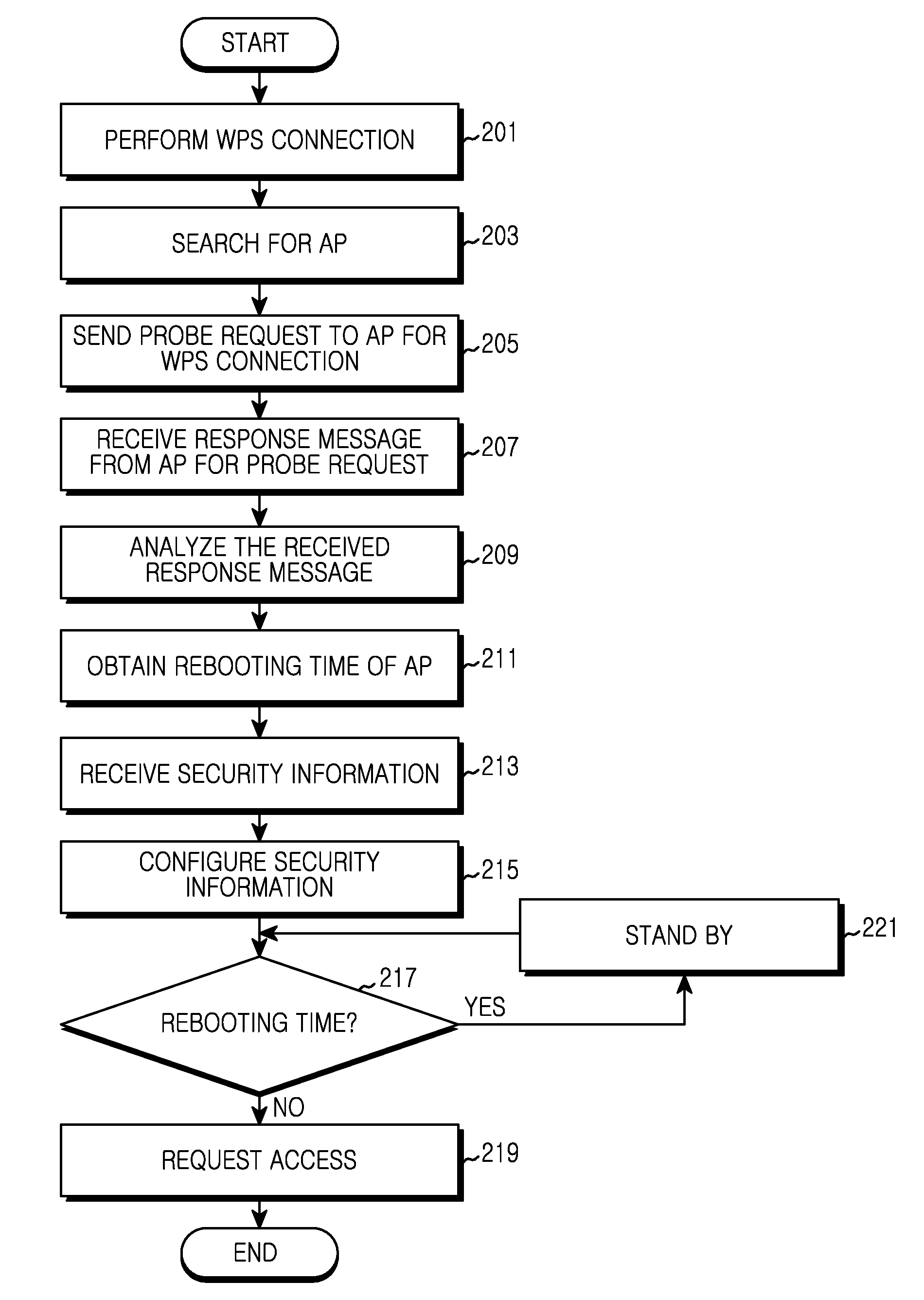
ActiveUS20120042158A1Firmly connectedNetwork traffic/resource managementDigital computer detailsWi-FiCommunications system
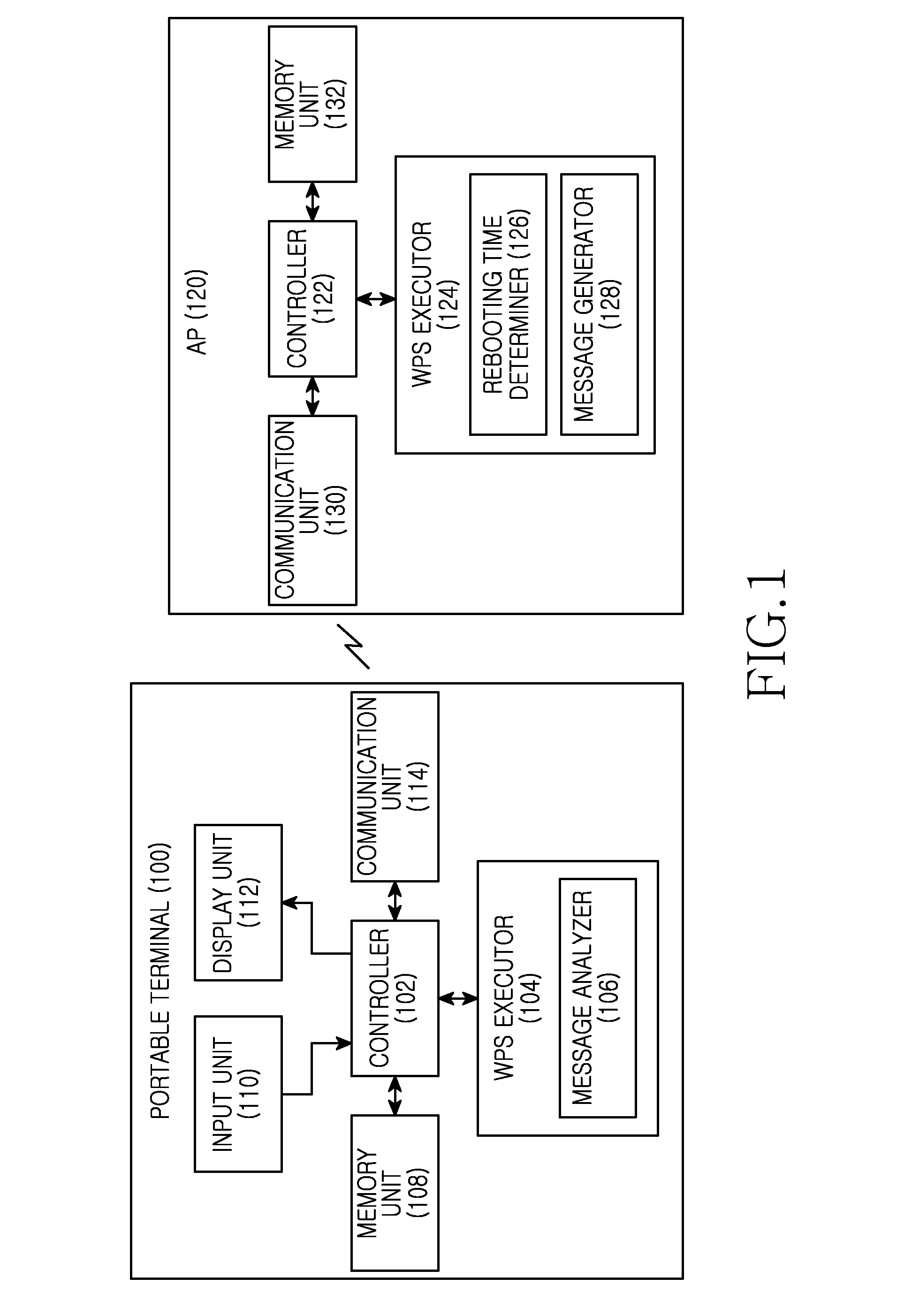
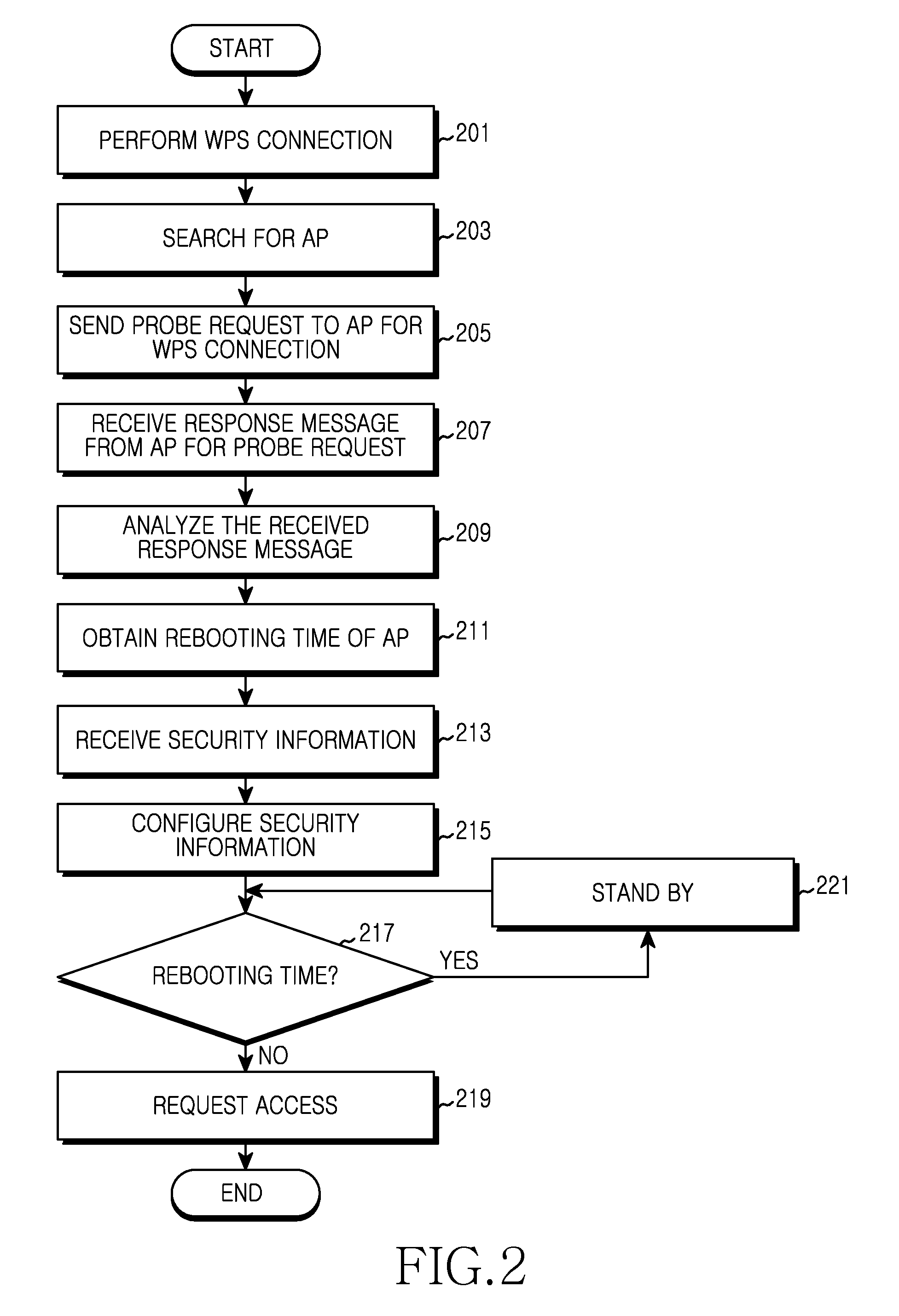
An apparatus and a method for configuring security for connection between a portable terminal supporting a Wireless-Fidelity (Wi-Fi) function and an Access Point (AP) are provided. More particularly, an apparatus and a method are provided for preventing access failure caused by an access request of a portable terminal while an AP of an un-configured mode, which is completing security setup using a Wi-Fi Protected Setup (WPS) function, is rebooted. The apparatus includes an AP for providing a terminal with a time taken to reboot after configuring security information based on a WPS function in an un-configured mode, wherein the terminal sends a request to access the AP after the rebooting has completed by determining the time taken to reboot received from the AP of the un-configured mode.
Owner:HUAWEI TECH CO LTD
Wi-Fi service method and system for Wi-Fi devices
ActiveUS9338633B2Satisfactory Wi-Fi service environmentThe method is simple and convenientNetwork topologiesServices signallingWi-FiAuto-configuration
A Wireless-Fidelity (Wi-Fi) service method and system are provided. A beacon message and probe response message may contain a service information field storing device information. Wi-Fi devices can exchange information on supported functions with each other and one Wi-Fi device may identify functions supported by another Wi-Fi device. Hence, a Wi-Fi connection can be set up through automatic provisioning. The method includes receiving, by a first Wi-Fi device in non-Access Point (AP) mode, messages from nearby Wi-Fi devices operating in AP mode, analyzing a service information field of each received message, determining a second Wi-Fi device that is manufactured by the same manufacturer as the first Wi-Fi device and is capable of supporting a requested service, establishing a connection with the second Wi-Fi device through Wi-Fi Protected Setup (WPS) based on automatic provision, and sending data associated with the requested service to the second Wi-Fi device for a Wi-Fi service.
Owner:SAMSUNG ELECTRONICS CO LTD
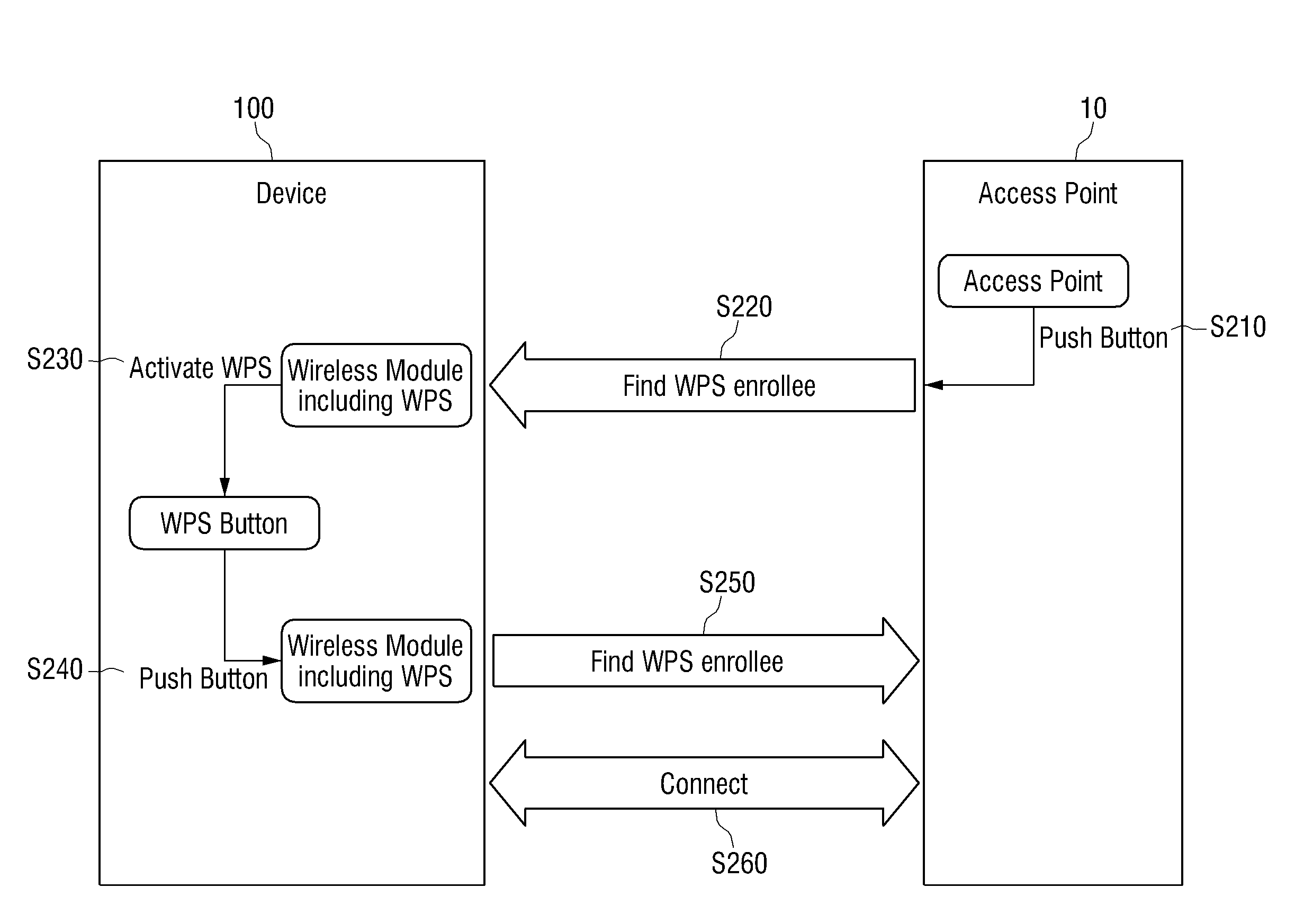
Apparatus and method for automatic access in a wireless communication system
Owner:SAMSUNG ELECTRONICS CO LTD
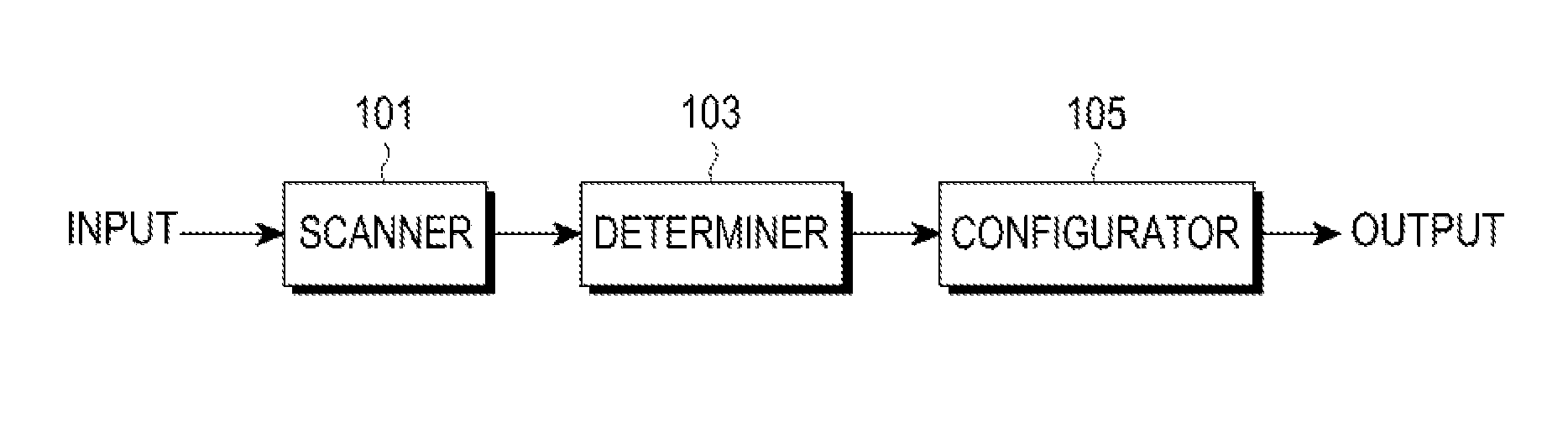
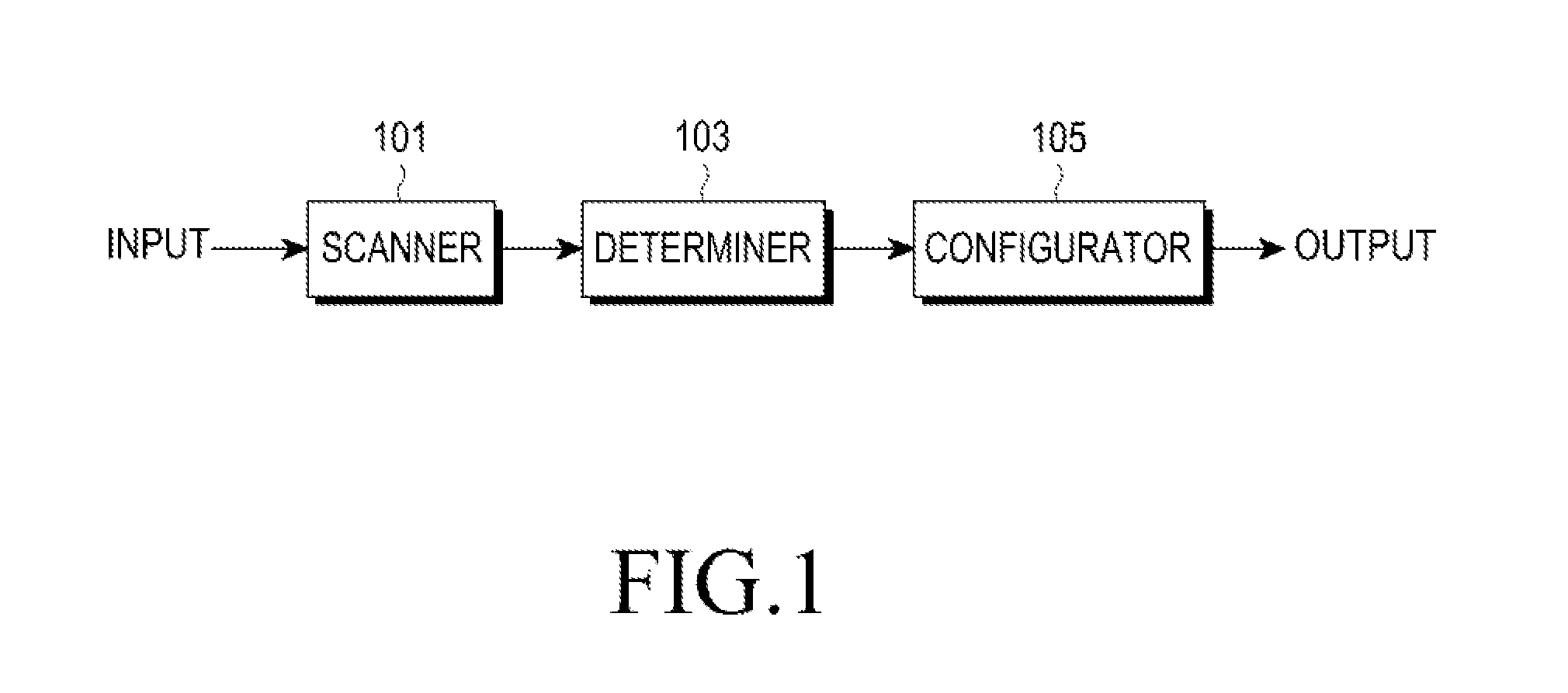
Apparatus and method for automatic access in a wireless communication system
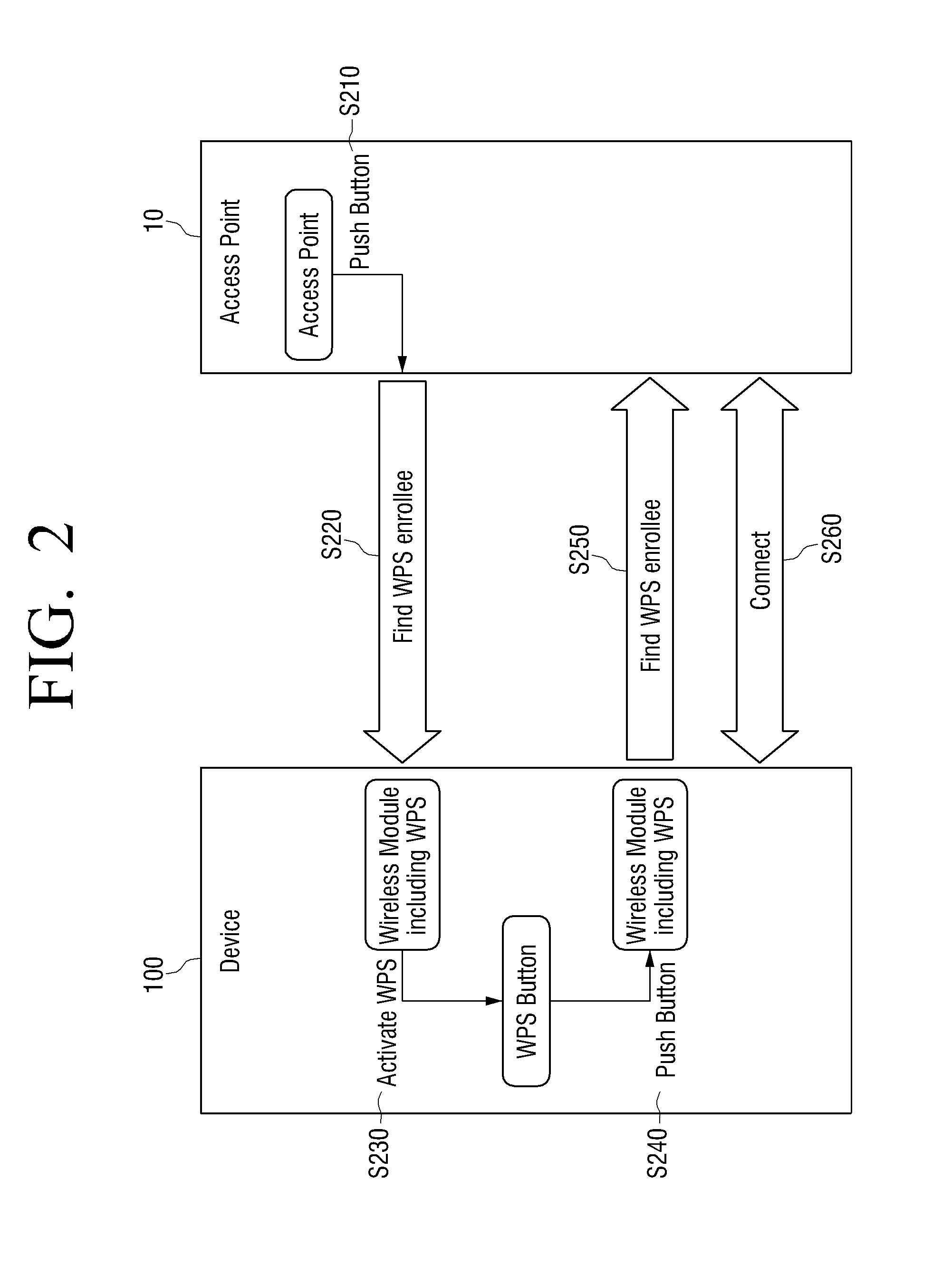
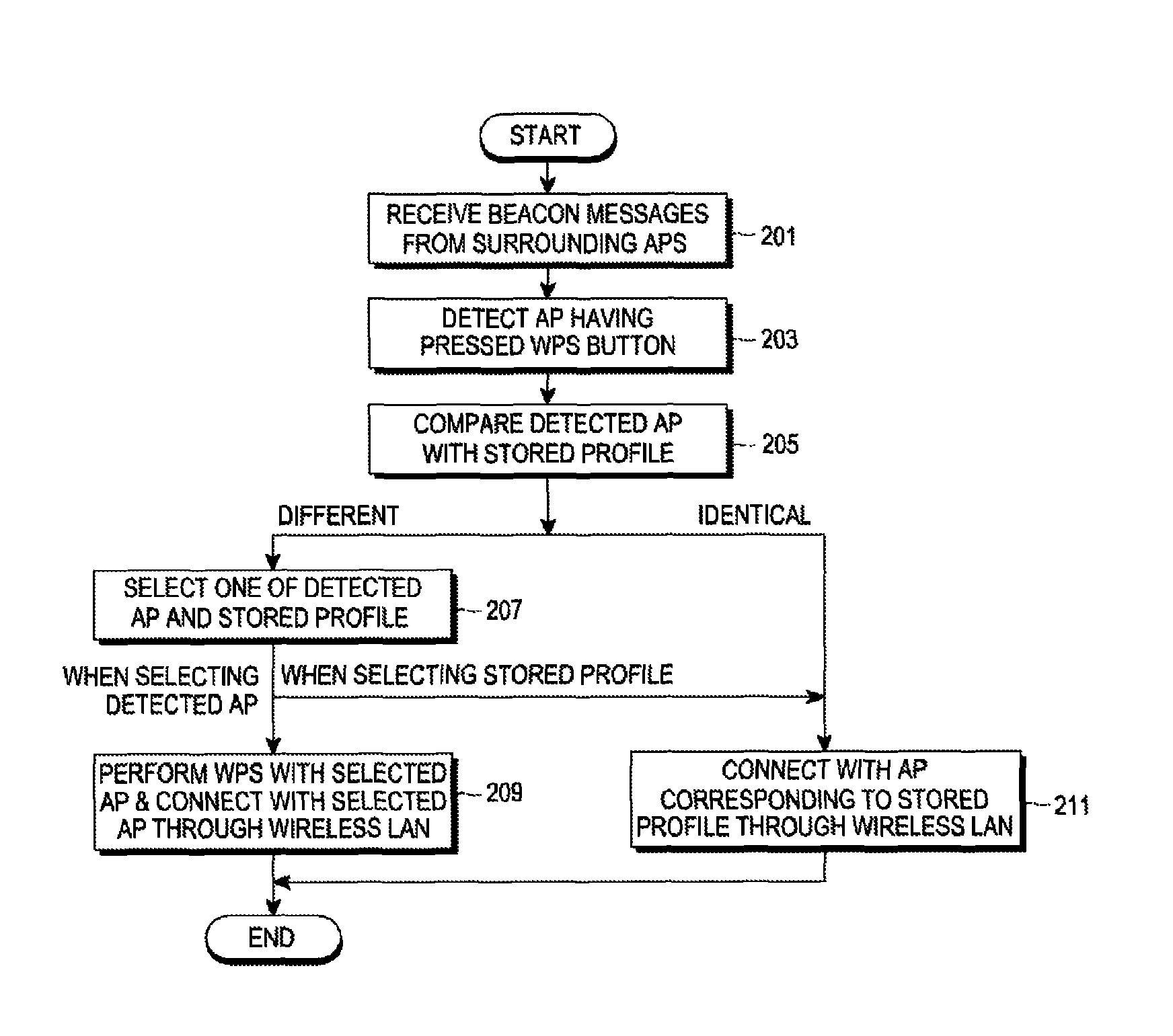
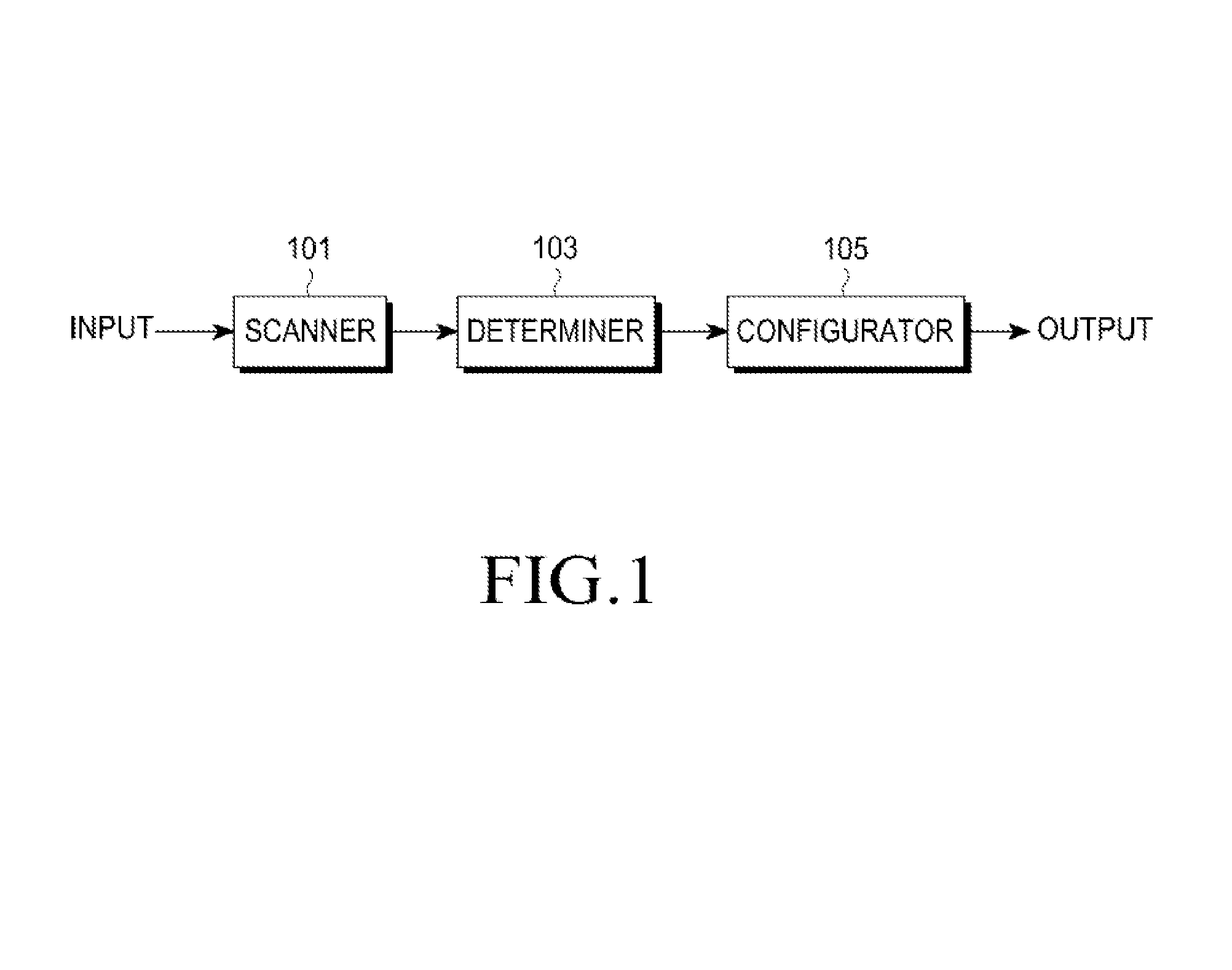
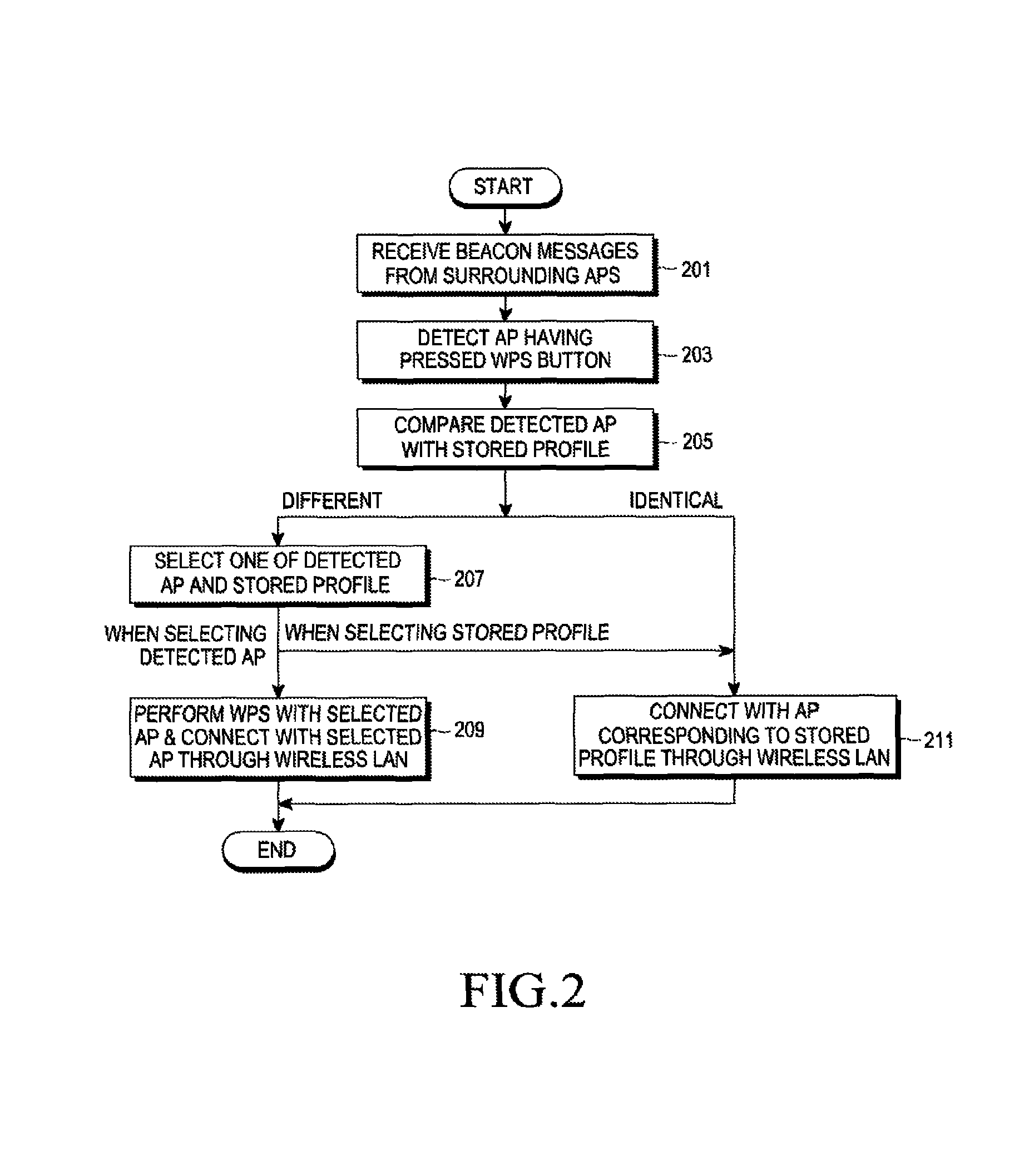
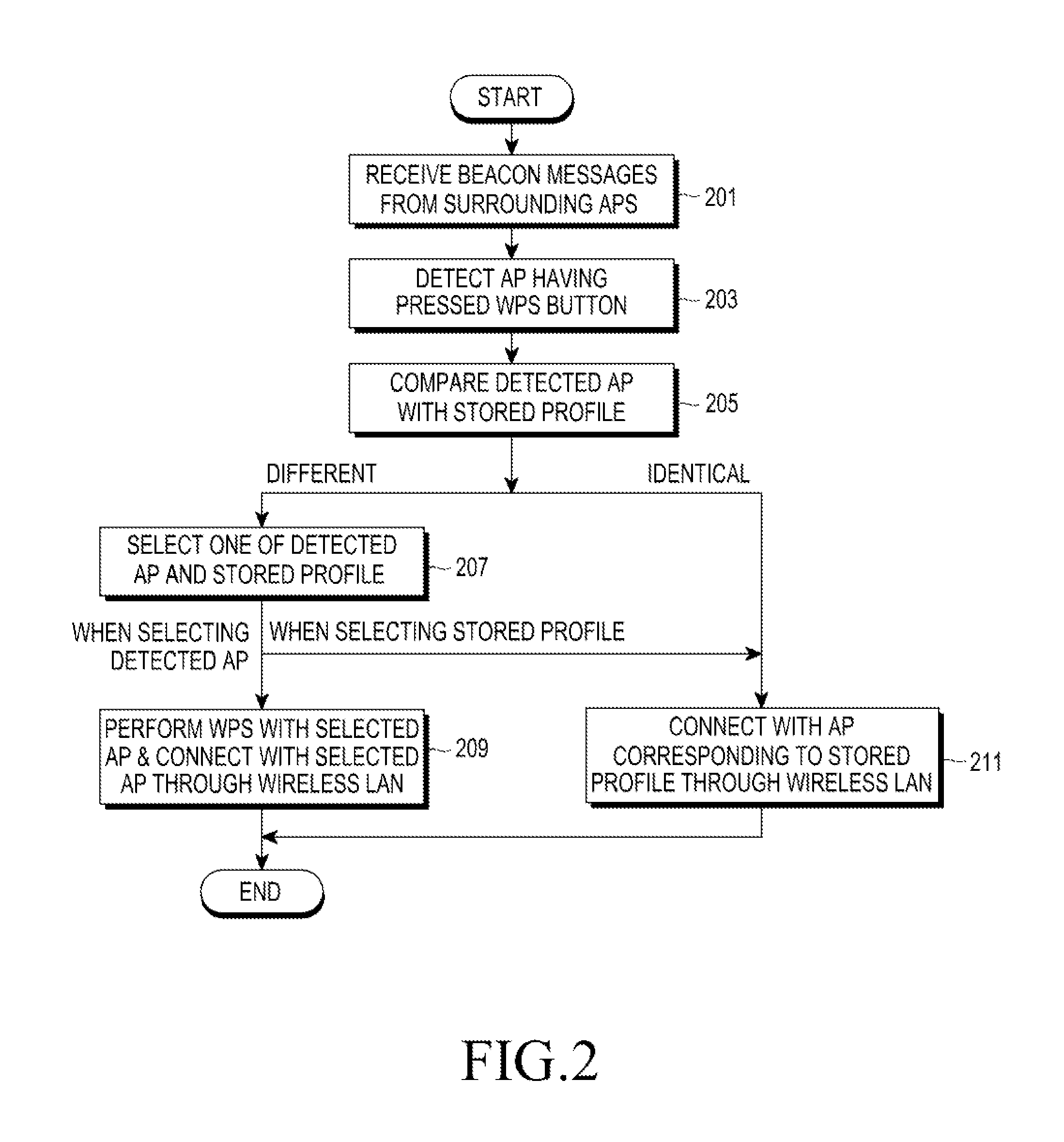
An apparatus and a method for automatic access in a wireless communication system are provided. The apparatus includes a scanner for scanning surrounding Access Points (APs) by receiving beacon messages from the APs, a determiner for detecting an AP, a WPS button of which has been pressed, from one or more scanned APs and for determining if there are two or more detected APs, and a configurator for, when there are two or more detected APs, transmitting a message including a Medium Access Control (MAC) address of an AP, which has been selected among the detected APs by an input of a user, to the AP and for performing a Wi-Fi Protected Setup (WPS) with the selected AP, thereby accessing a wireless Local Area Network (LAN).
Owner:SAMSUNG ELECTRONICS CO LTD
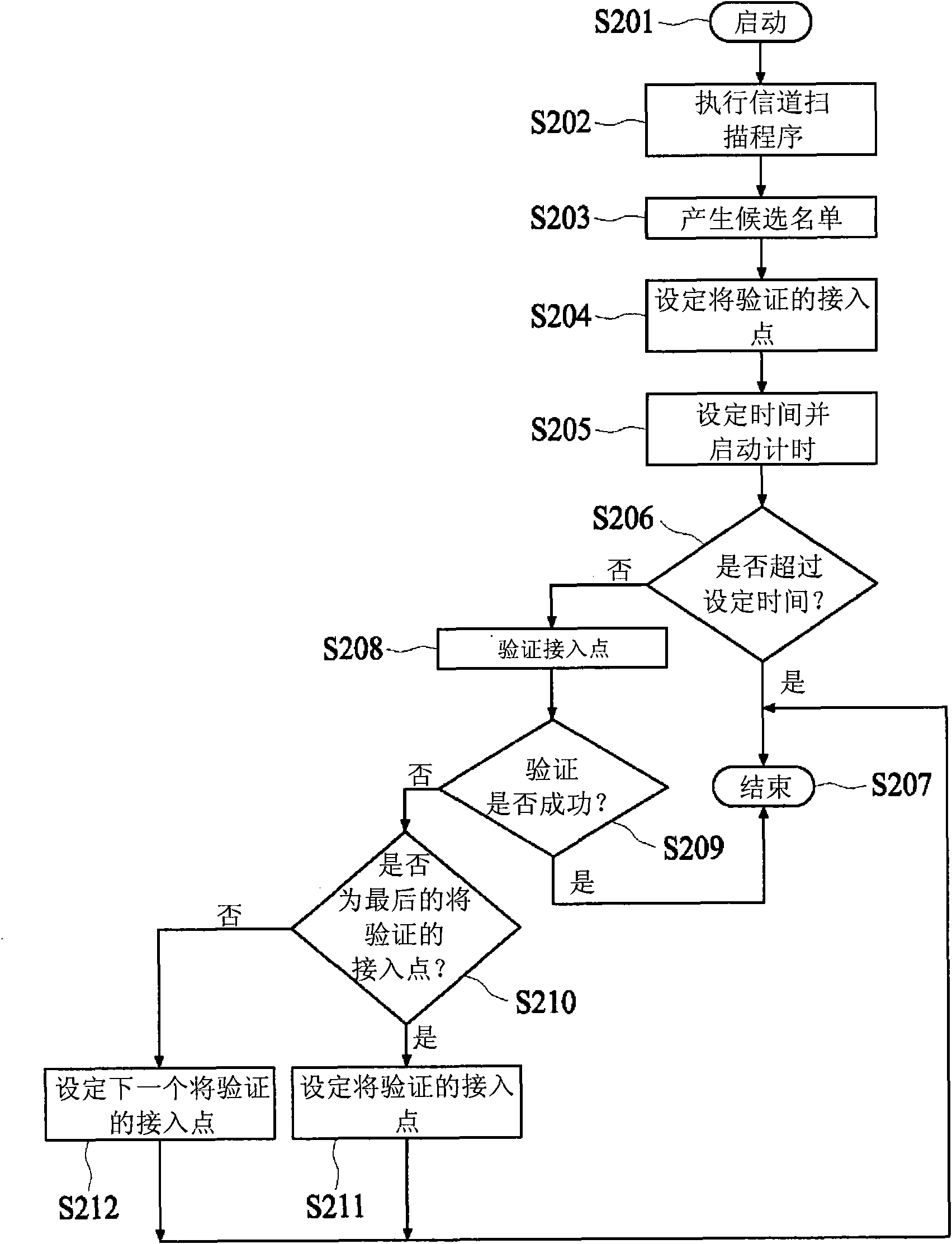
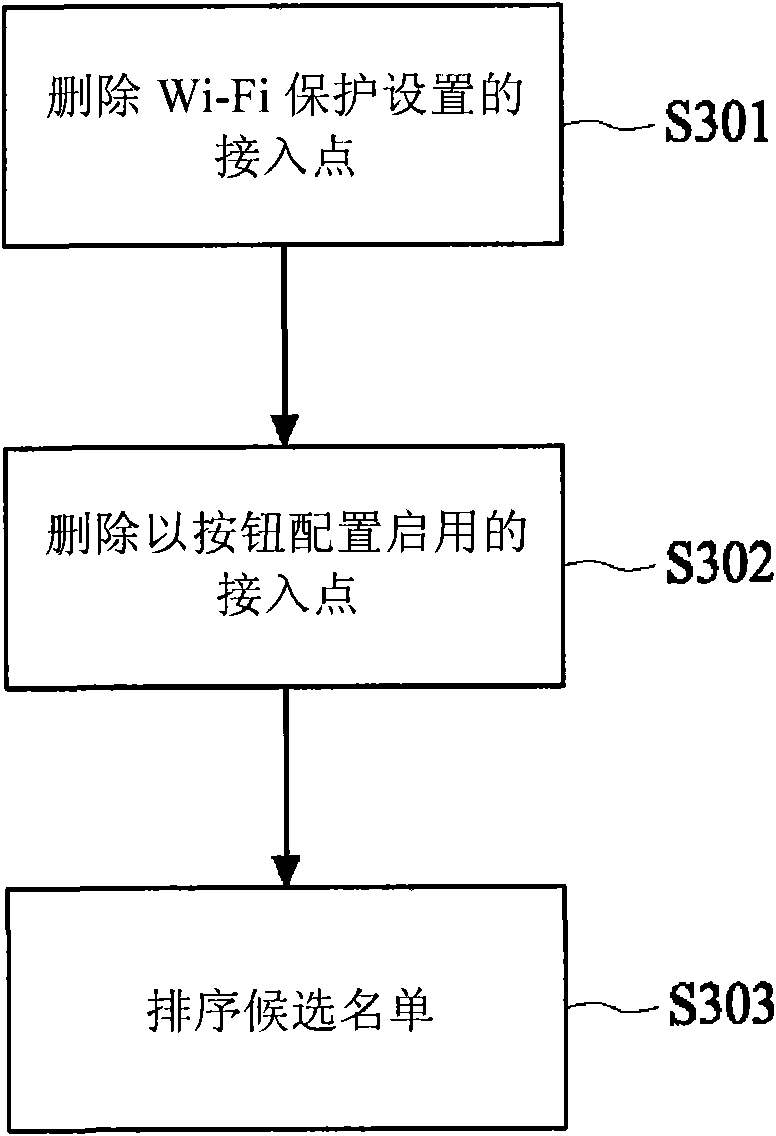
Method for selecting access point and device
The invention relates to a method for selecting an access point and a device. The method produces a candidate list according to a frame content transmitted by the access point, and verifies the access points in the candidate list one by one according to the candidate list to select the access point for starting a person identification number. During producing the candidate list, the access point for starting the person identification number is sequenced to a high priority level position so as to remove the access points of non-Wi-Fi protecting device and the access points for starting button allocation.
Owner:LINK TECH INC
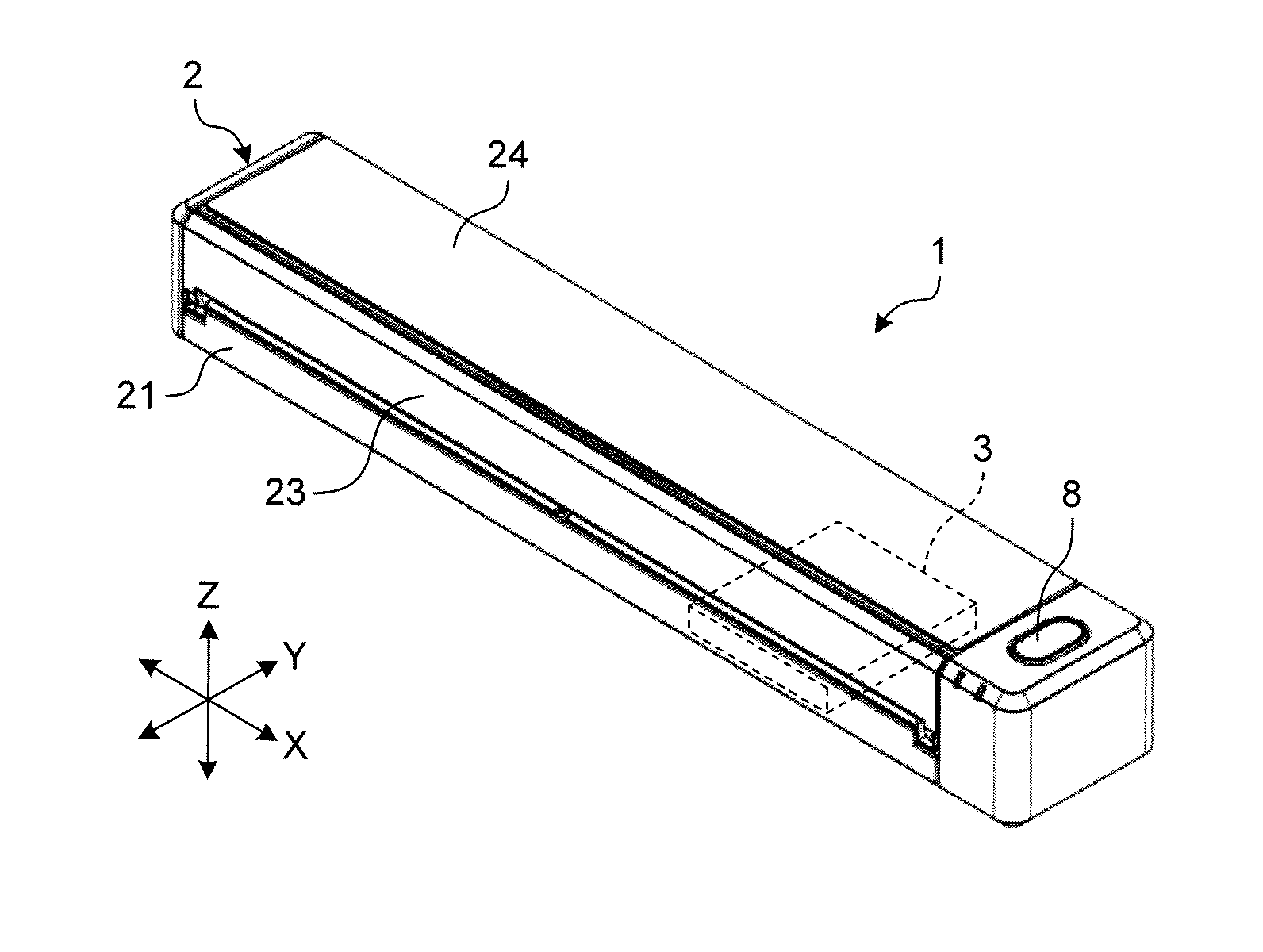
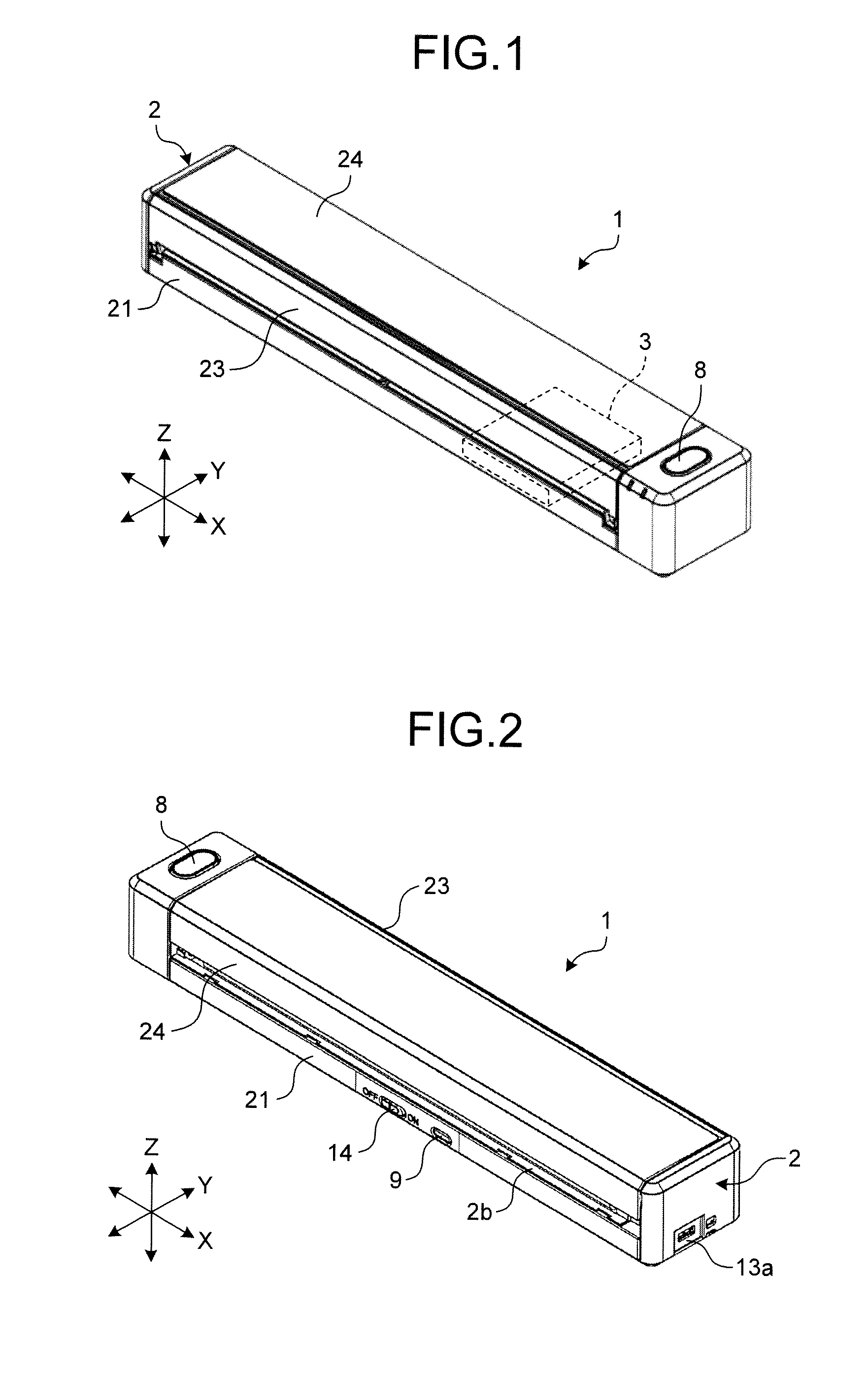
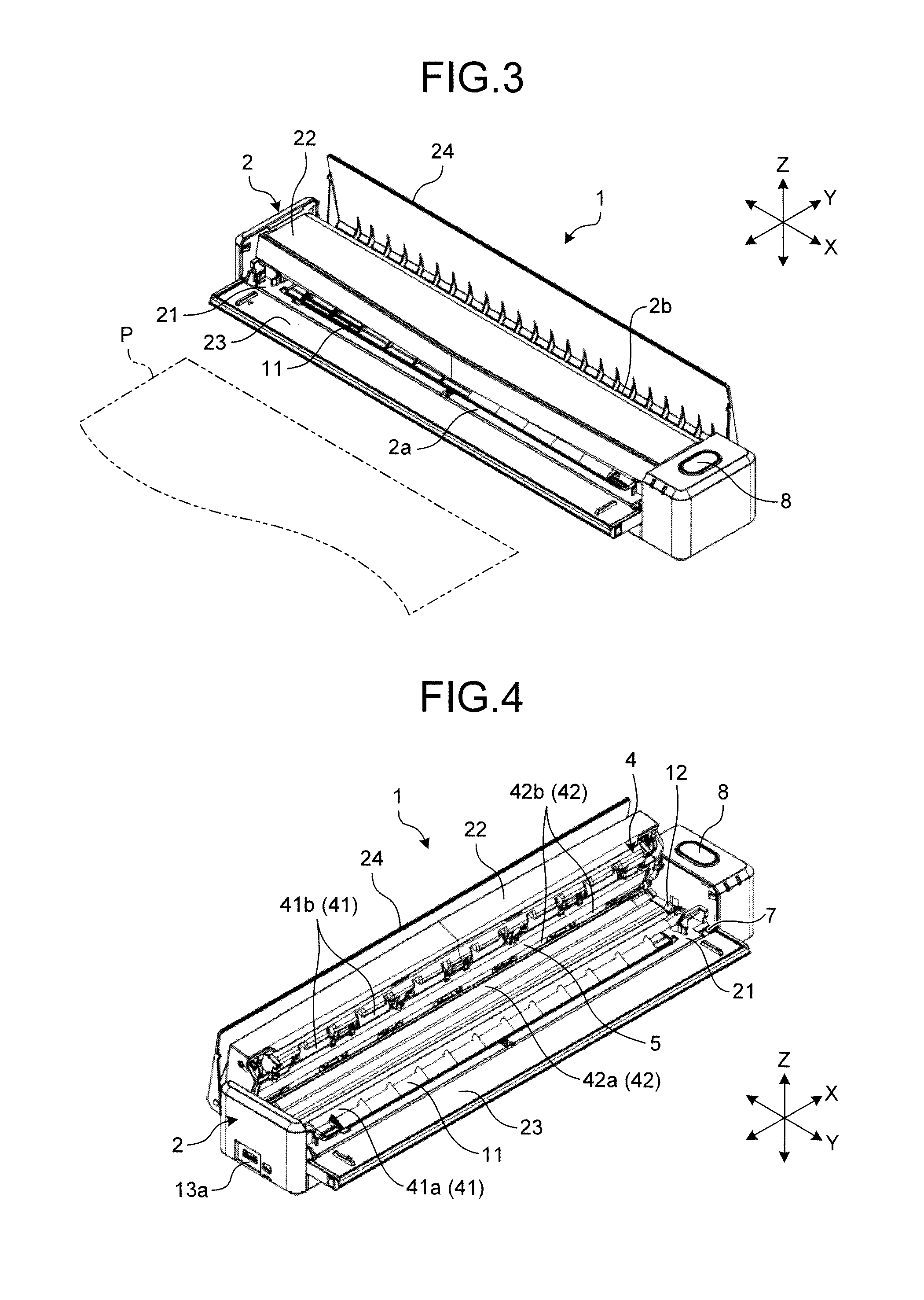
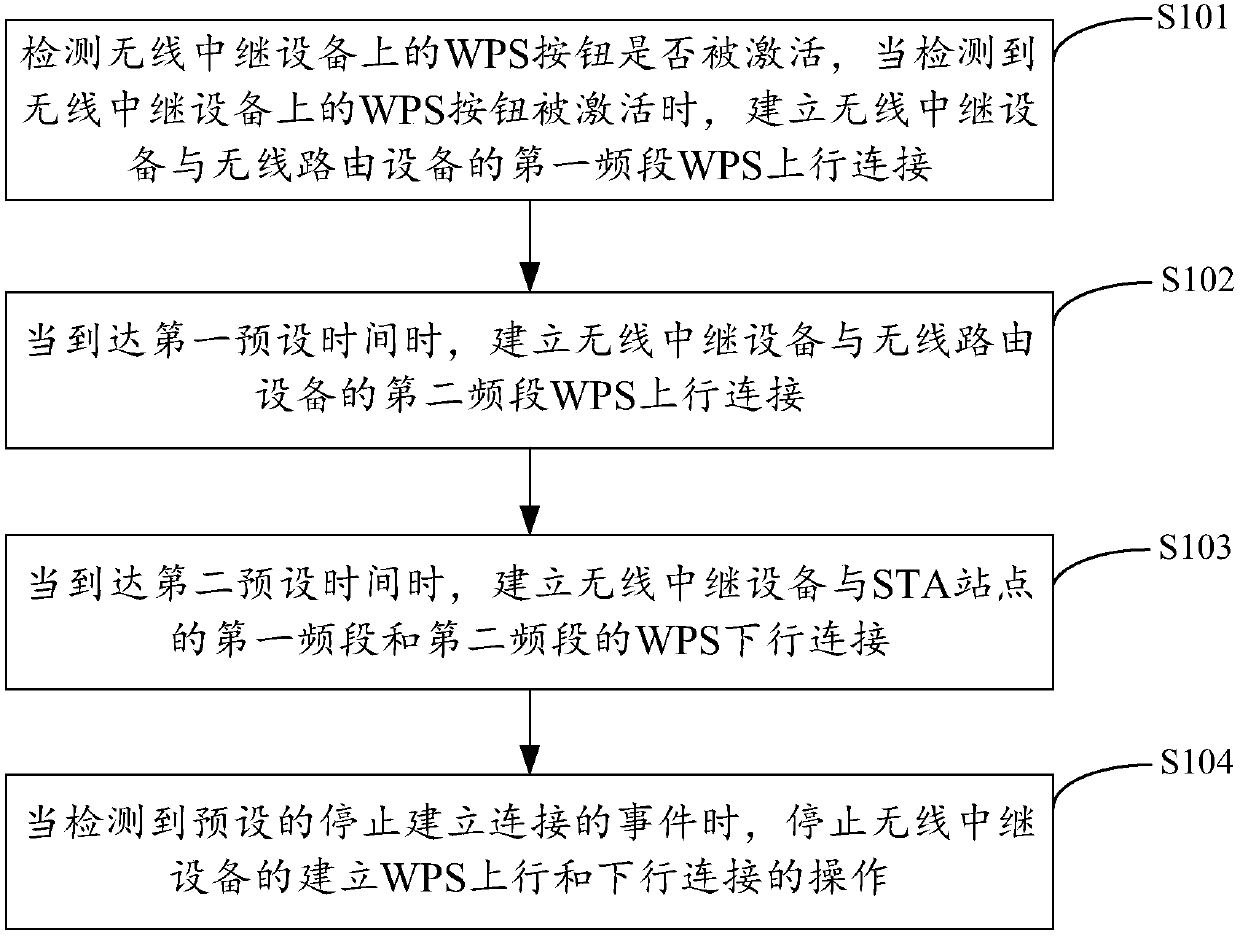
Image-reading apparatus
An image-reading apparatus includes a battery that is built-in in a housing, a conveying unit conveying a medium, an image capturing unit capturing an image of the medium, a control unit controlling at least the conveying unit and the image capturing unit, a setting-table-opened / closed sensor as a state detector detecting whether the image capturing unit is ready to read the medium, a reset unit resetting the control unit, a scanning button and a Wi-Fi protected setup (WPS) button, each of which is an operation unit disposed on an outer peripheral surface of the housing and used for giving an instruction to the control unit. The reset unit resets the control unit upon satisfaction of a first condition that the setting-table-opened / closed sensor determines that the image capturing unit is unready to read the medium and a second condition that the operation unit is operated.
Owner:PFU LTD
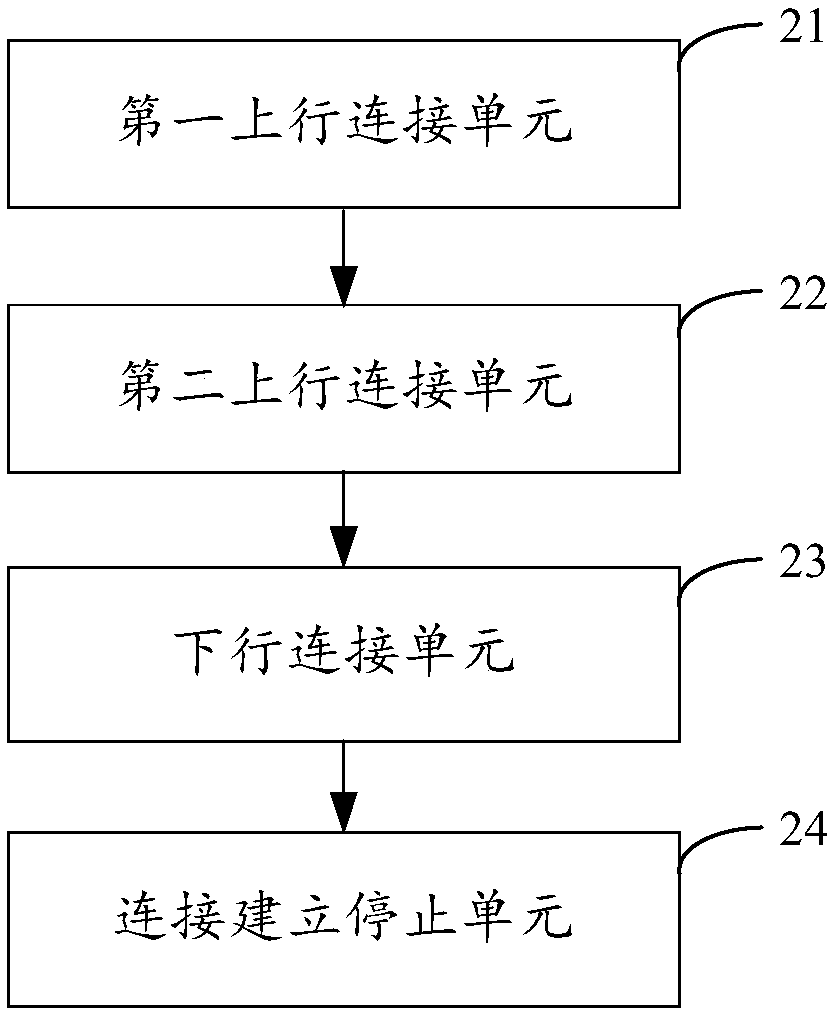
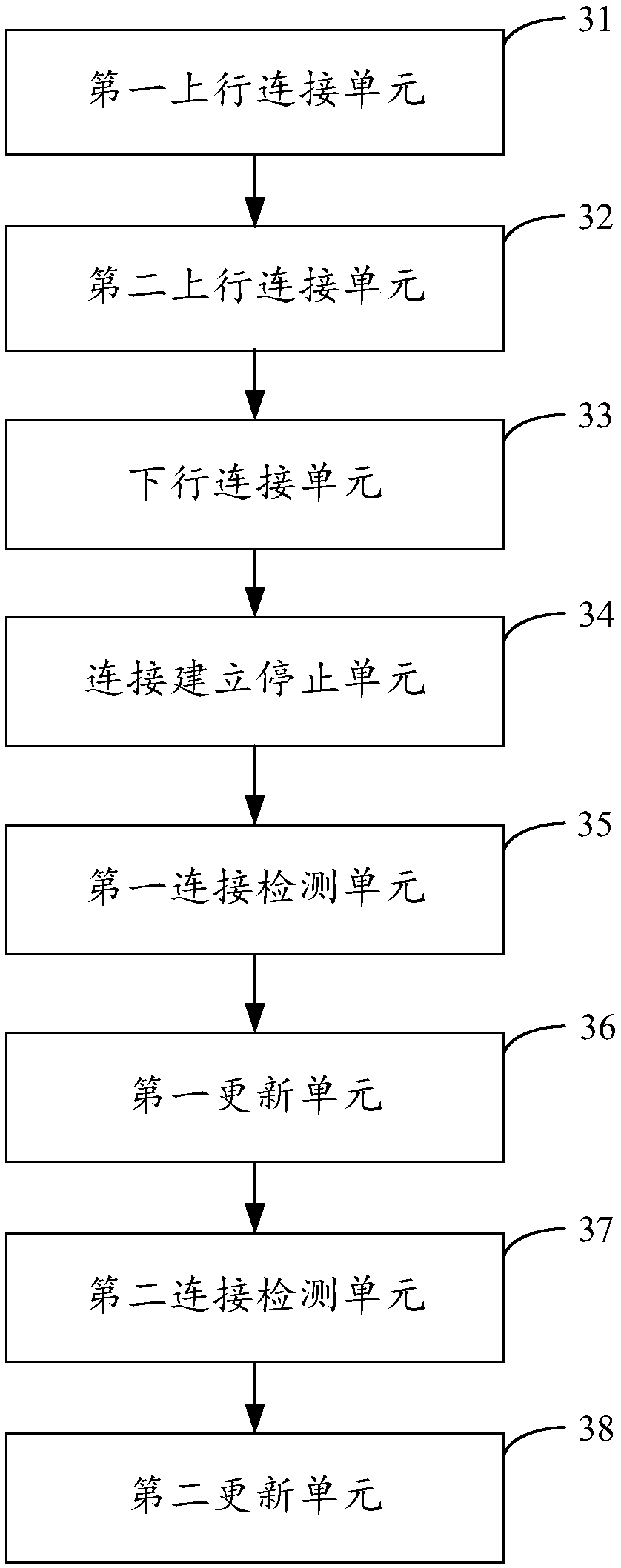
WPS (Wi-Fi Protected Setup) connection method and device for wireless relay device, apparatus and memory medium
ActiveCN107734717AImprove connection efficiencyConnection managementRadio transmissionComputer scienceWi-Fi Protected Setup
The invention applies to the technical field of a computer and provides a WPS (Wi-Fi Protected Setup) connection method and device for a wireless relay device, an apparatus and a memory medium. The method comprises the steps of detecting whether a WPS button on the wireless relay device is activated or not; establishing first band WPS uplink connection between the wireless relay device and a wireless routing device when it is detected that the WPS button on the wireless relay device is activated; establishing second band WPS uplink connection between the wireless relay device and the wirelessrouting device when first preset time arrives; establishing WPS downlink connection between the wireless relay device, and a first band and a second band of a STA station when second preset time arrives; and stopping the operation of establishing the WPS uplink and downlink connection of the wireless relay device when a preset event of stopping establishing the connection is detected. The bidirectional double-band WPS connection of the wireless relay device is realized through activation of the WPS button, so the WPS connection efficiency of the wireless relay device is improved.
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
Dual-frequency WPS (Wi-Fi protected setup) triggering method
The invention provides a dual-frequency WPS (Wi-Fi protected setup) triggering method. A hardware button trigger mode is set on a router. The method includes that all terminals are notified in broadcasting or responding mode after a hardware button is pressed down; when the WPS of a downlink terminal is activated, WPS interaction can be performed immediately; and when the WPS interaction is ended, normal data interaction can be performed. WPS triggering in dual frequencies is completed by a button triggering mode, a WPS progress is completed by guiding, and the shortcomings caused by the fact that the WPS in different frequency bands is activated in different time periods by one hardware button at present are overcome.
Owner:SHENZHEN GONGJIN ELECTRONICS CO LTD
Using a button provided in an image forming apparatus to start a Wi-Fi protected setup
Owner:HEWLETT PACKARD DEV CO LP
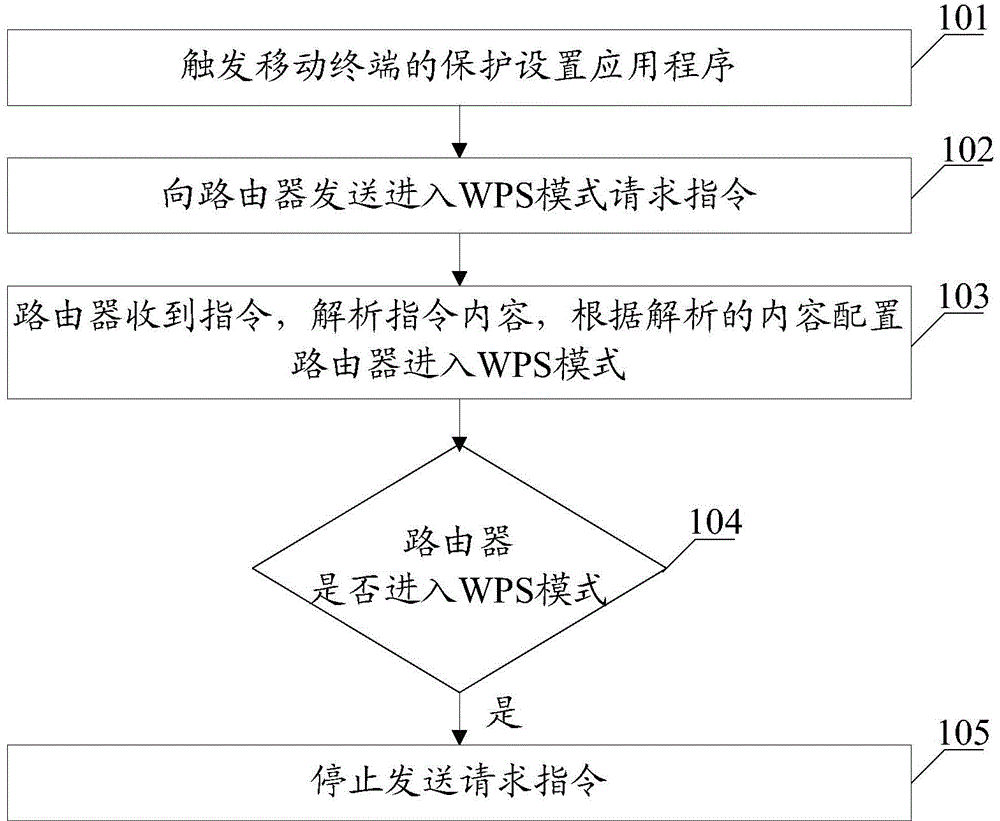
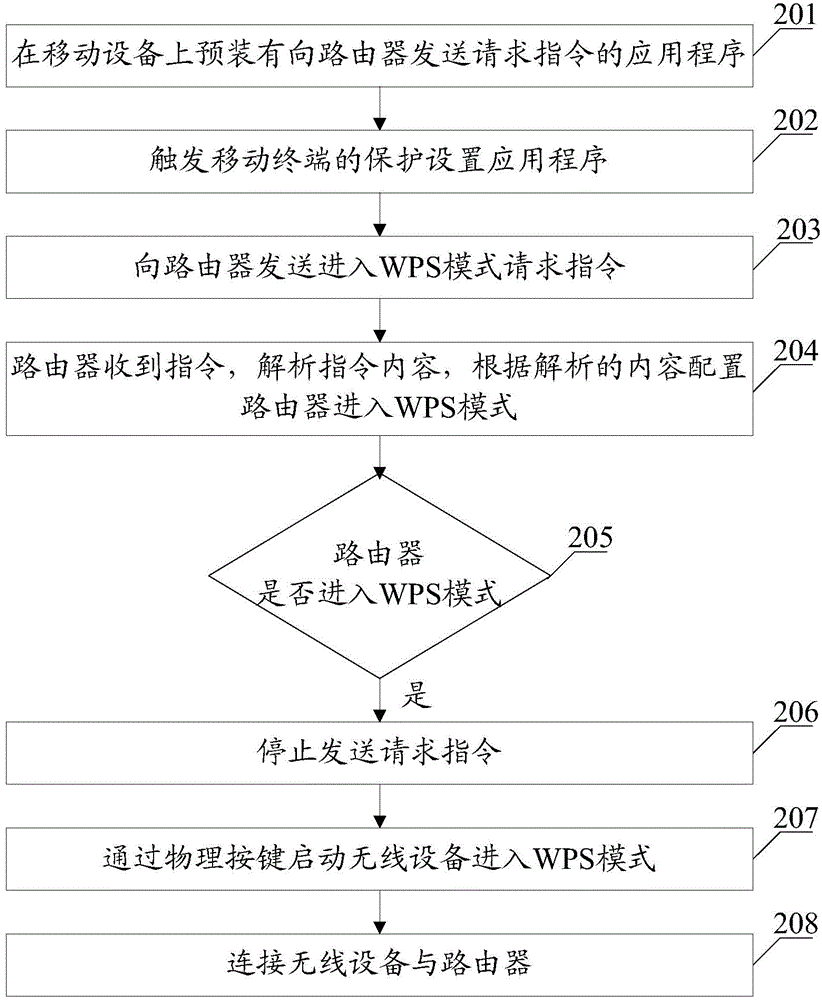
Method and device for entering WPS (Wi-Fi Protected Setup)
InactiveCN105848301AEnter into realizationImprove work efficiencyConnection managementComputer networkApplication software
The invention provides a method and a device for entering WPS (Wi-Fi Protected Setup). The method comprises the following steps: triggering a protected setup application of a mobile terminal; sending a WPS mode entering request instruction to a router, wherein the request instruction is an instruction generated by the application in response to a triggering operation; receiving the request instruction by the router, resolving content of the request instruction, and configuring the router to enter the WPS mode according to the resolved content; and judging whether the router enters the WPS mode or not through the mobile terminal, and if so, stopping sending the request instruction. According to the method for entering the WPS provided by the invention, the router enters the WPS mode through the request instruction sent by the application. Compared with a way of controlling the router to enter the WPS mode through a physical key in the prior art, the WIFI protected setup method provided by the invention has the advantages that the router can automatically enter the WPS mode conveniently, and the working efficiency of the router while entering the WPS mode is effectively increased.
Owner:SHANGHAI MXCHIP INFORMATION TECHN
Secure wireless communication initialization system and method
A wireless communication system for a vehicle is provided. The system comprises a portable wireless device comprising first and second manual interface devices and adapted to transmit a wireless network security protocol confirmation signal in response to manipulation of the first and second manual interface devices, and an onboard wireless communication device for the vehicle, adapted to accept a Wi-Fi Protected Setup (WPS) session outcome in response to receiving the wireless network security protocol confirmation signal.
Owner:GM GLOBAL TECH OPERATIONS LLC
Method, system, and device for implementing device addition in Wi-Fi device to device network
ActiveUS8595807B2Effectively avoid interruption of workEnsure work continuityDigital data processing detailsNetwork topologiesComputer hardwareWi-Fi
Owner:HUAWEI DEVICE CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com