Method for monitoring a network and network including a monitoring functionality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
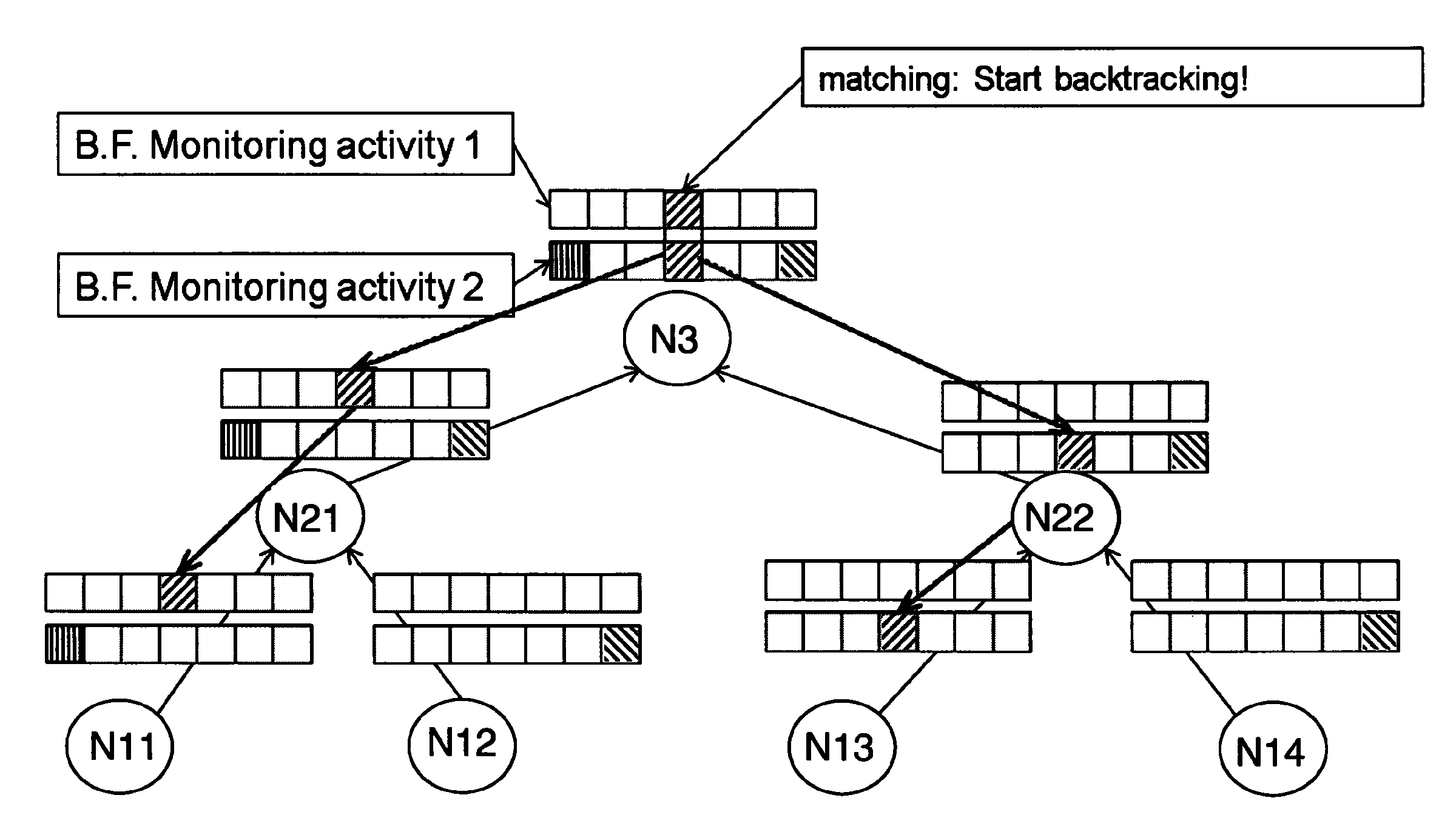
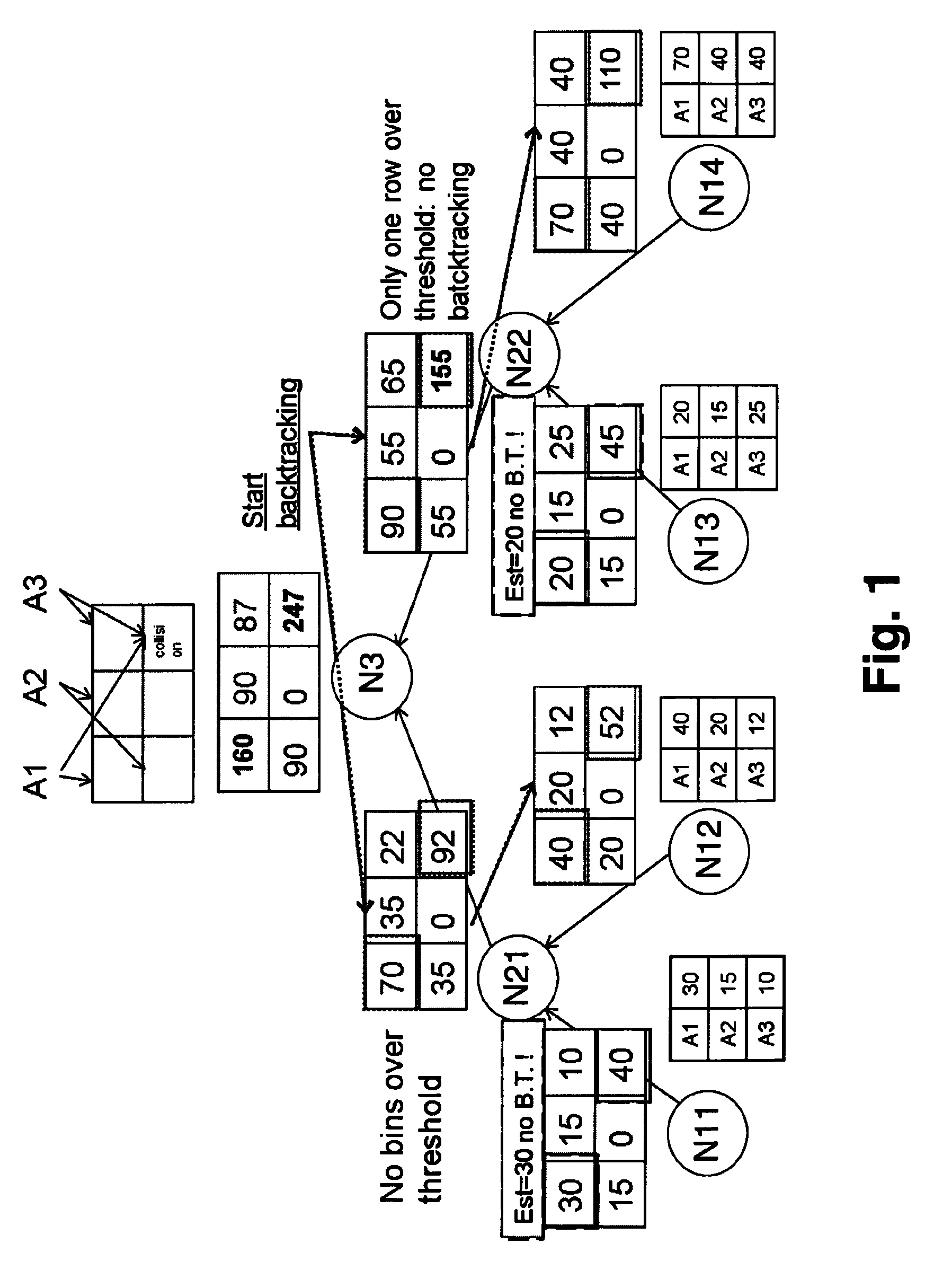
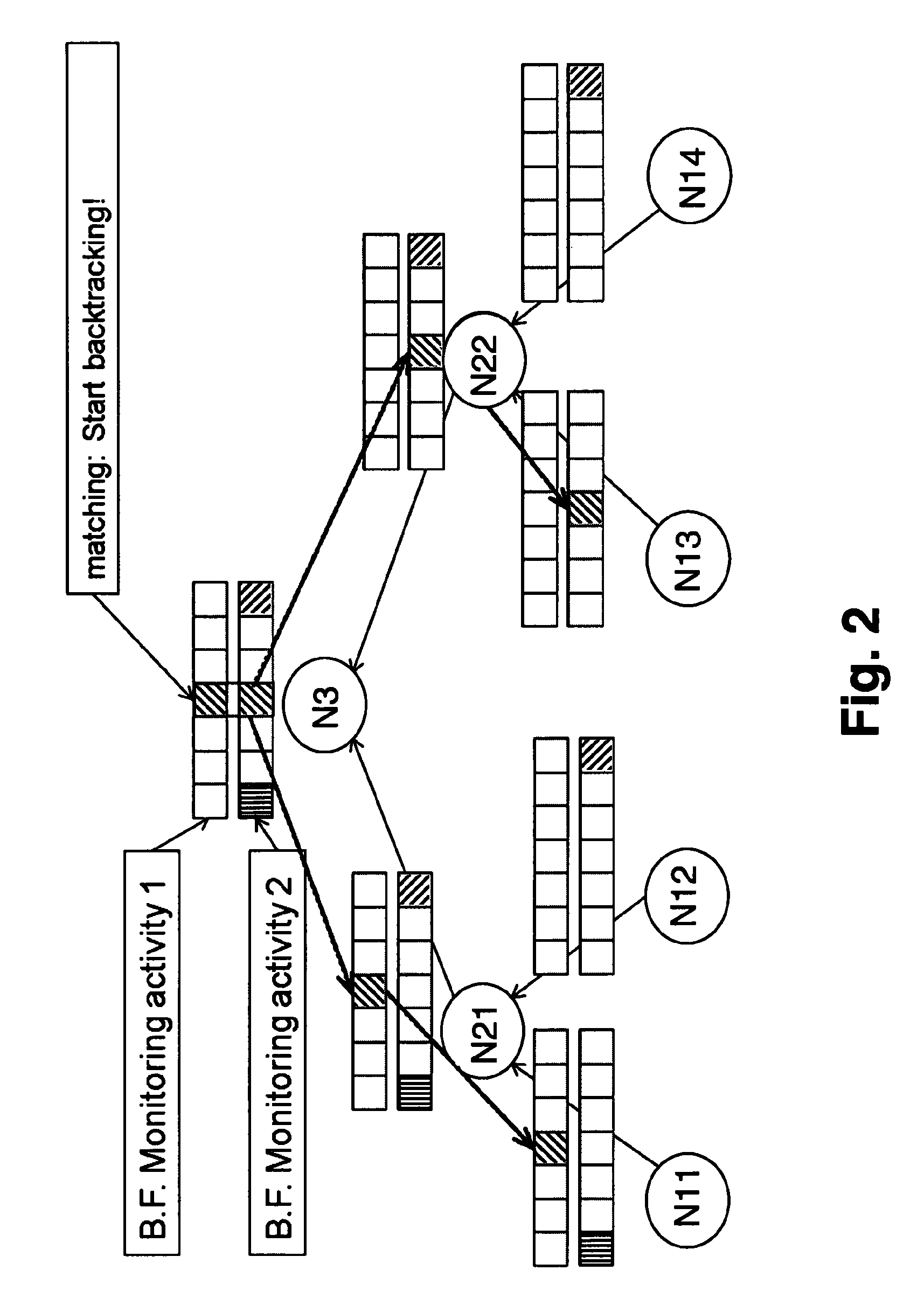
[0028]According to a preferred embodiment of the present invention, two complementary mechanisms are realized, which are privacy-preserving aggregation and backtracking. According to the invention probabilistic data structures are used, having the effect of achieving both mechanisms at the same time while preserving the privacy of the users being monitored.
[0029]One of the key applications of the present invention would be to support a distributed, cross-domain monitoring architecture that is scalable, protects the privacy of the monitored data, and allows for backtracking to the original monitoring probe for after-the-fact auditing by identification of the probes which have collected relevant information.
[0030]To simplify the description of the embodiments illustrated in the Figs. it is assumed that the monitoring nodes are arranged in a tree structure (although any connected graph would work). In this tree structure the leaves of the tree represent the network probes (or monitorin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com