Method for making secure typed data language in particular in integrated system and integrated system therefor
An embedded system and security technology, which is applied to the security of classified data language, especially in the embedded system and the embedded system field that realizes it, can solve the problem of error operation spreading smart cards, etc., and achieve the effect of optimizing memory space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
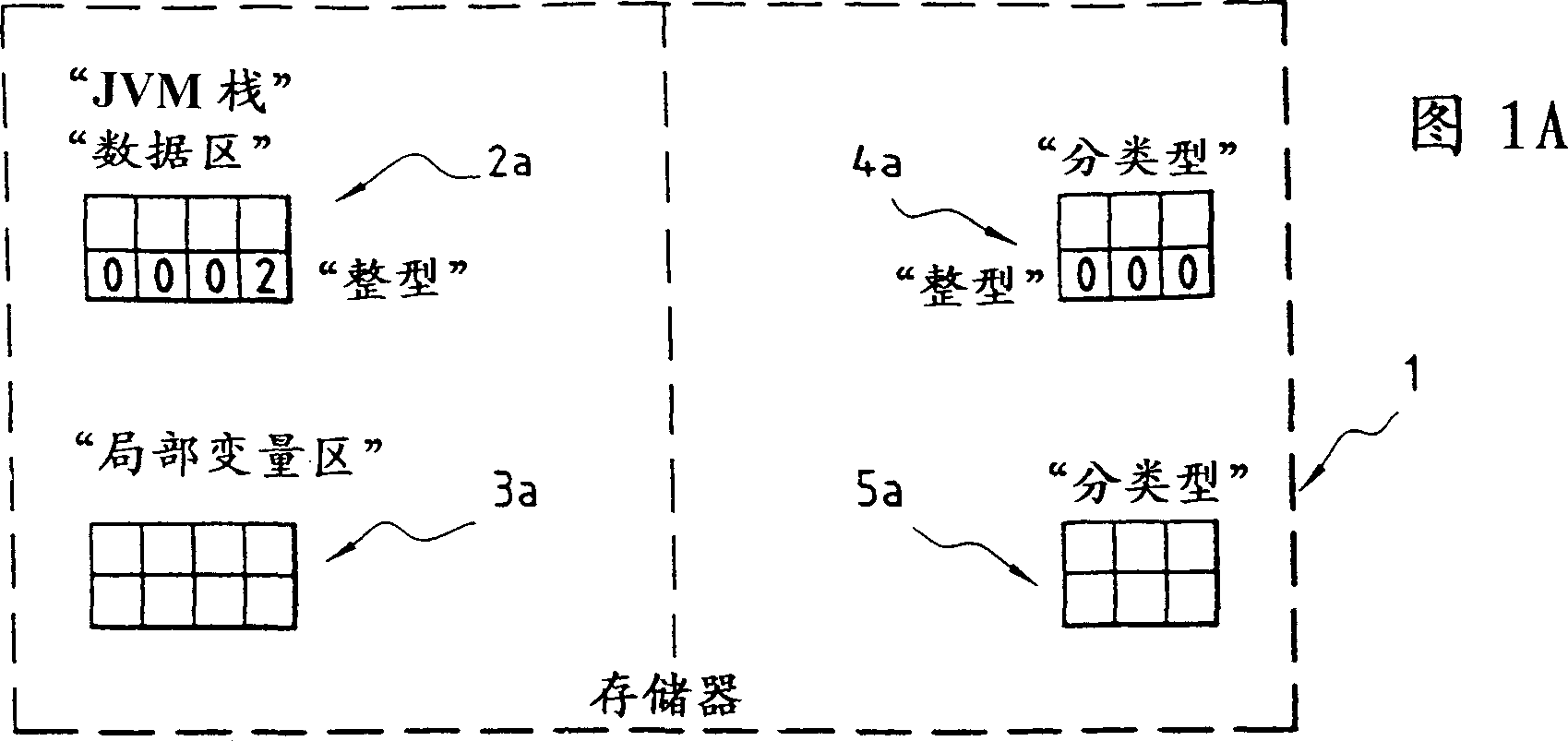
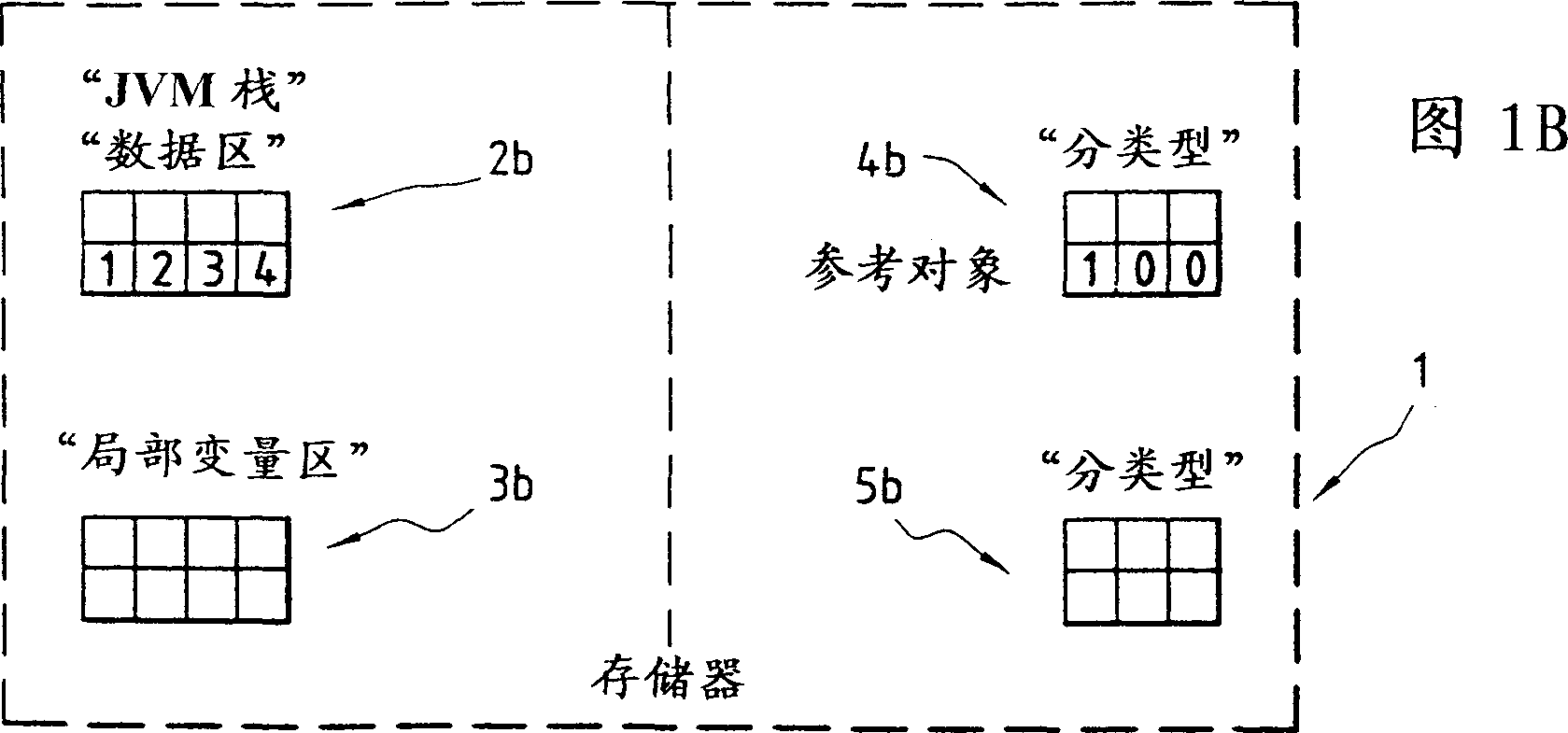
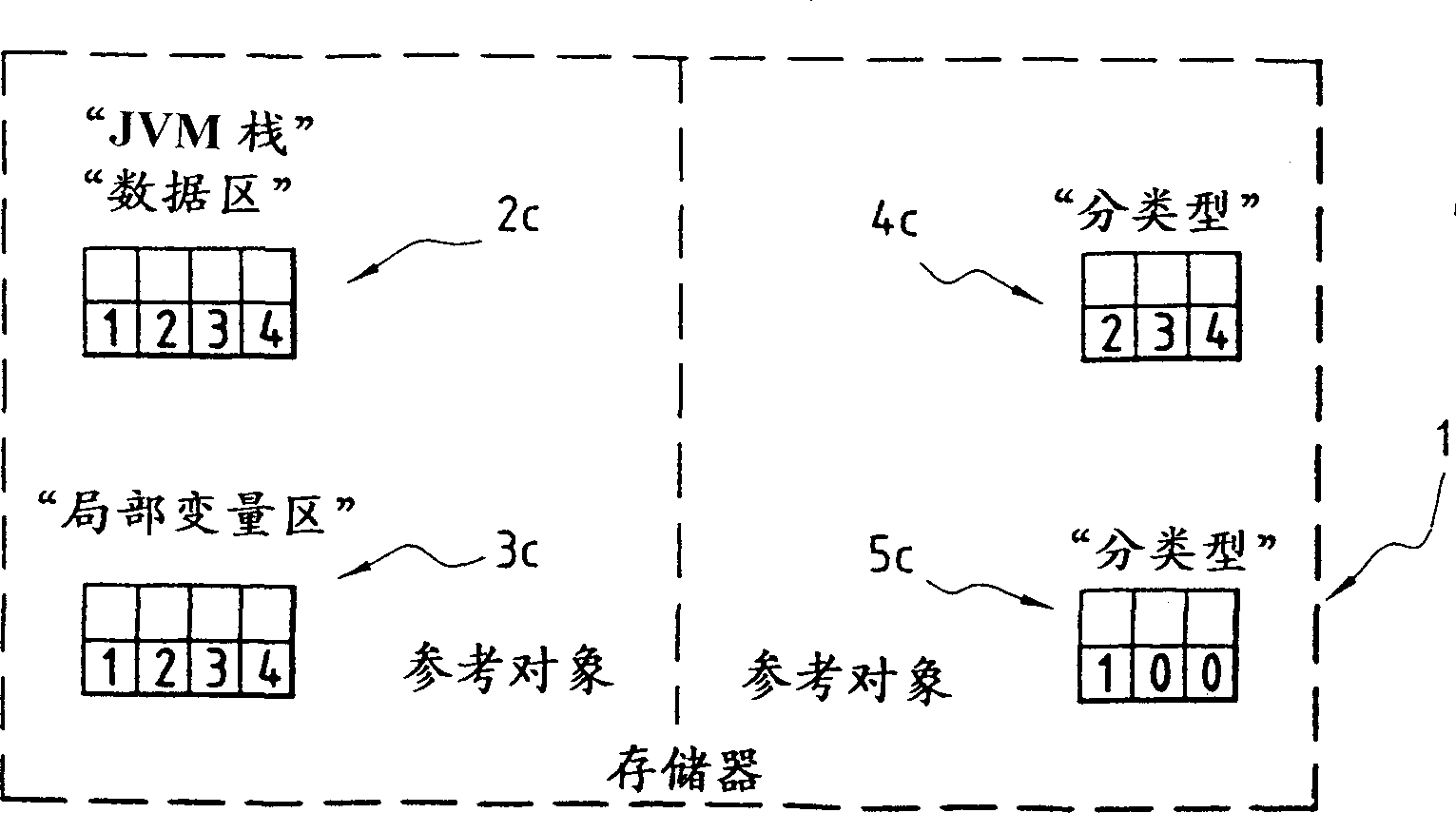
[0043] In the following, without limiting its scope, we shall hereafter be within the scope of the best application of the invention, unless the contrary is indicated, that is to say in the electronic intelligence embedded with the "JAVA" virtual machine for translating the "p-code" in the case of a system.
[0044] As we recalled in the preamble to this specification, when a given method executes, the virtual machine looks up the corresponding "p-code". This "p-code" identifies a specific operation to be performed by the virtual machine. A special stack is required for the processing of local variables and arithmetic operations or for other method calls.
[0045] For the virtual machine the stack is used as the work area. To optimize virtual machine performance, the stack size is usually fixed for a given primitive type.
[0046] As already recalled, there are two main types of objects that can be used in the stack:
[0047] - Objects of "primitive" type, which start with...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com