Secure storage method and system based on trusted embedded device and FTP (File Transfer Protocol)
An embedded device and secure storage technology, applied in transmission systems, digital data authentication, electrical components, etc., can solve the problems of difficult auditing of password operations, lack of security protection mechanisms for hardware drives, unacceptable performance overhead, etc., to achieve good flexibility and the effect of scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
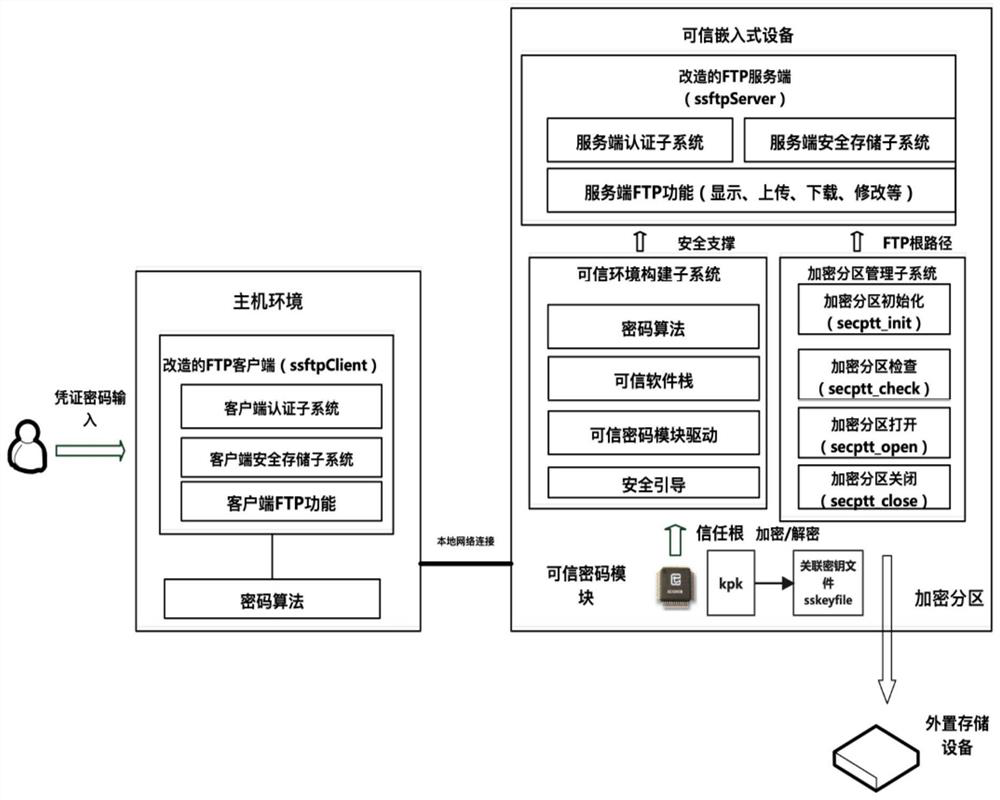
[0050] The following takes an ordinary PC device as a host environment (an entity that uses secure storage) and a Raspberry Pi equipped with a TCM security chip as a trusted embedded device (an entity that provides secure storage) as examples to illustrate the specific implementation of the present invention:
[0051] The present invention proposes a secure storage method based on a trusted embedded device and FTP. For those skilled in the art, a corresponding secure storage system can be designed and implemented with reference to the method.
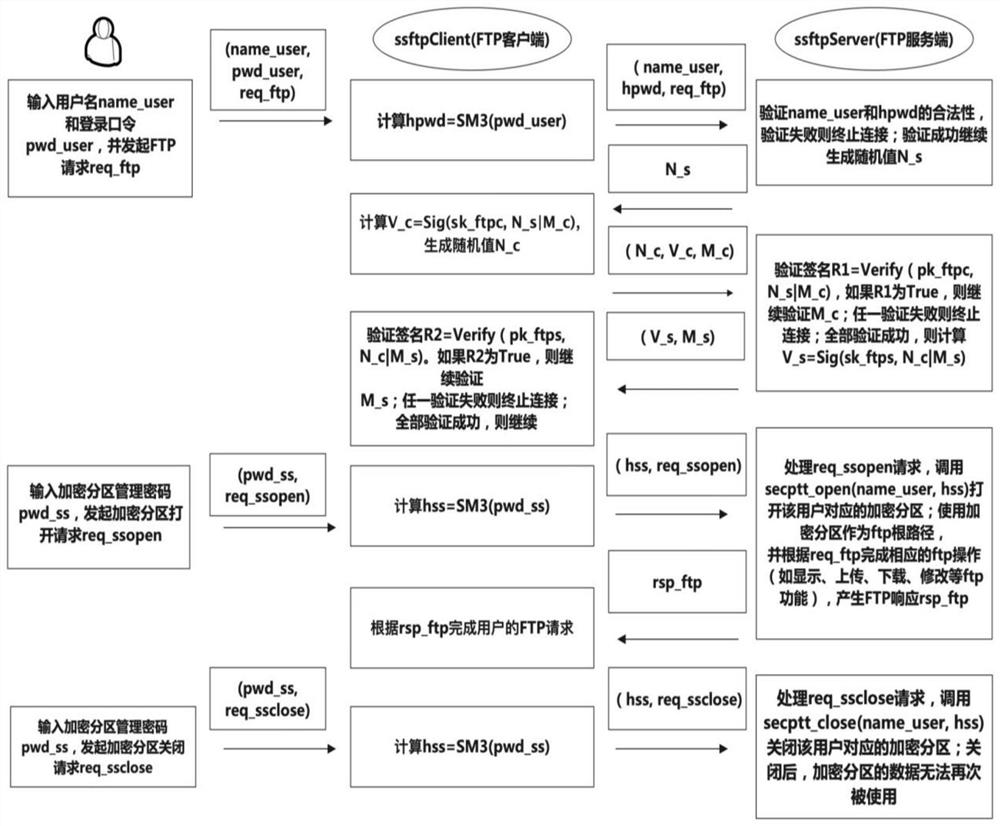
[0052] In the secure storage method based on a trusted embedded device and FTP in this embodiment, the usage flow of the secure storage is as follows figure 2 shown, including the following steps:
[0053] 1. Follow sub-step a) of step 1 of the content of the invention, the Raspberry Pi has a network port and a USB interface, the network port can be connected with the PC host environment through a network cable, and a mobile hard disk ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com