Trusted operation system and method with remote authentication and information independence of heterogeneous processor through open connector
A processor and encrypted processor technology, applied in the field of secure and trusted computing architecture
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
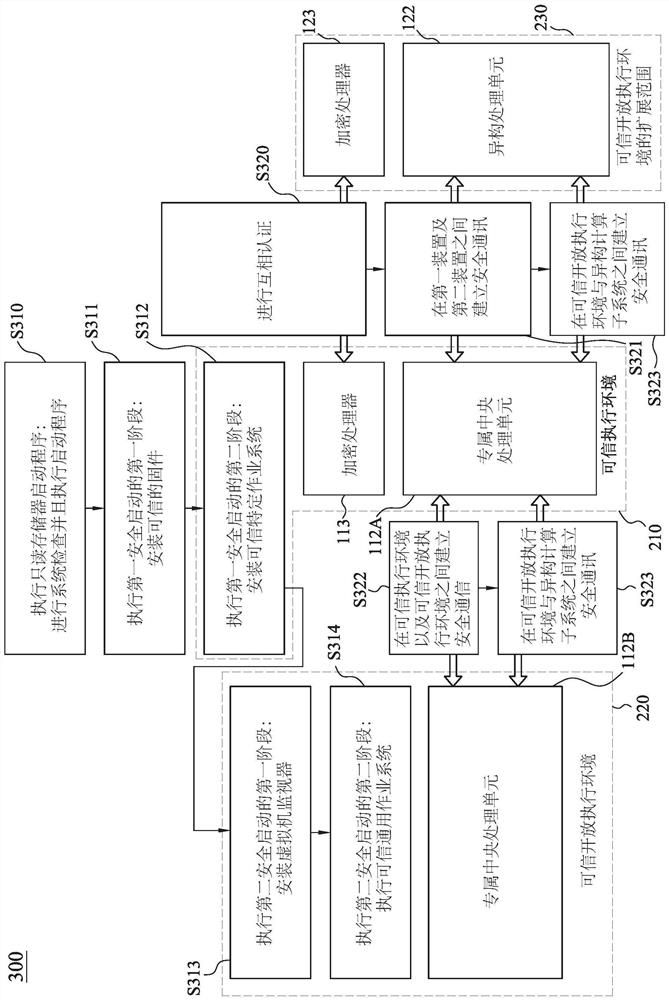
[0016] The following embodiments are described in detail with the accompanying drawings, but the provided embodiments are not intended to limit the scope of the present disclosure. In order to facilitate understanding, the same or similar elements in the following description will be described with the same reference numerals. Next, the embodiments of the present disclosure will be described in more detail, and the embodiments will be described in conjunction with the accompanying drawings. The same reference numbers are used in the drawings and description to refer to the same or like parts. With the advent of the Internet of Things (IoT), a large amount of data is collected by various sensors and analyzed by computing nodes embedded in the environment. In the emerging paradigm of edge computing, heterogeneous computing systems, such as edge computing nodes equipped with CPU, GPU, NPU, and VPU (collectively referred to as XPU), are often used to perform real-time data analys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com