Multi-authorization attribute-based verifiable encryption method based on block chain
A technology of authorization attribute and encryption method, which is applied in the direction of digital transmission system, electrical components, transmission system, etc., can solve the problem that the correctness and integrity of cloud storage data cannot be guaranteed, and the correctness of multi-authorized organization keys cannot be verified, and the system Problems such as data security cannot be guaranteed, to achieve the effect of increasing difficulty and cost, solving heavy computing burden, and eliminating concerns about data credit
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
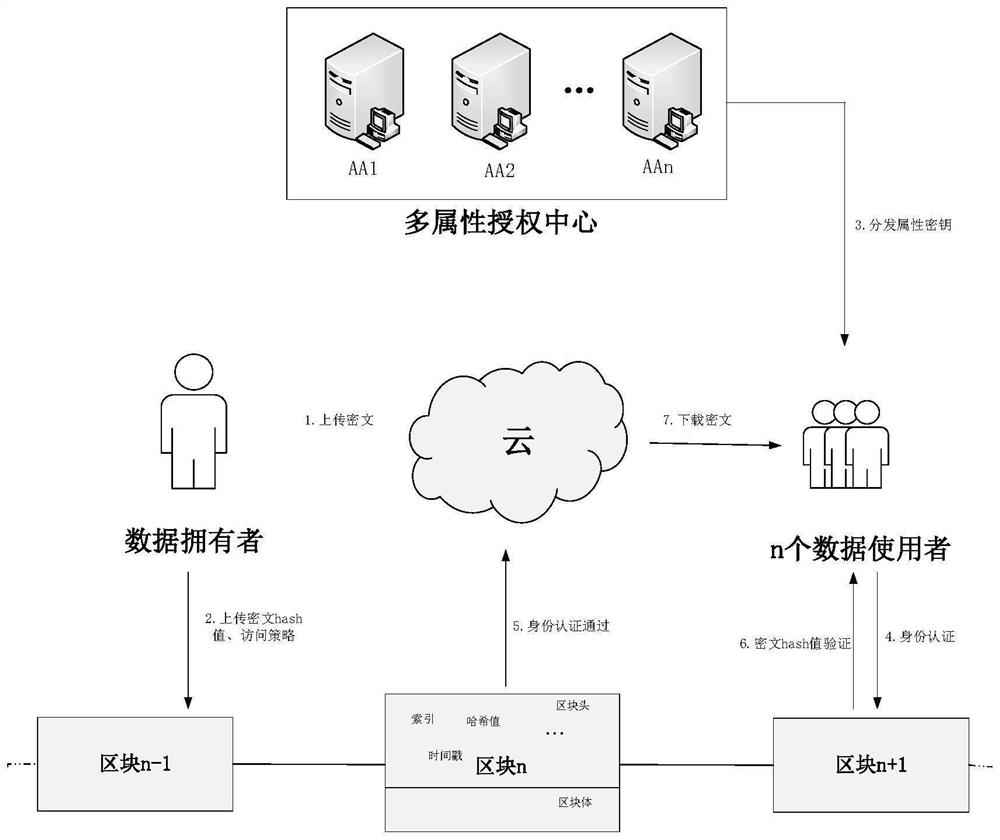
[0018] Such as figure 1 As shown, the present invention is a blockchain-based multi-authorization attribute-based verifiable encryption method, which adopts attribute-based encryption and introduces a multi-authorization attribute center to ensure one-to-many fine-grained access control and verifiable transmission of data The wrong private key; the algorithm includes initialization phase, encryption phase, key generation phase, verification phase, and decryption phase, and its steps are:
[0019] The first is that the data owner uploads the encrypted data to the cloud using the system public key, and at the same time uploads the data ciphertext hash value and access policy to the blockchain;
[0020] Secondly, the cloud storage server is responsible for receiving the data ciphertext and saving it;
[0021] Then, the data user receives the attribute key distributed by the multi-attribute authorization center and can verify the correctness of the key;
[0022] Secondly, the bl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com