IoT device identification method, system, device and computer readable medium
An IoT device and identification technology, applied in instruments, electrical components, safety devices, etc., can solve the problems of inconsistent matching, increased application software repetitive overhead, easy loss of identity code information, etc., to achieve good inheritance and consistency , Save repetitive resource overhead and improve management efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
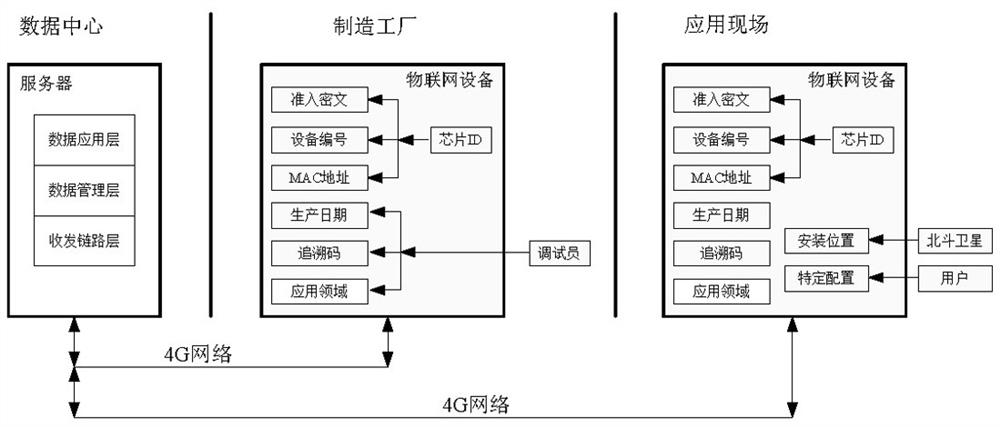
[0094] When used in the factory (such as image 3 shown), the identification and management of IoT devices in the factory are as follows:
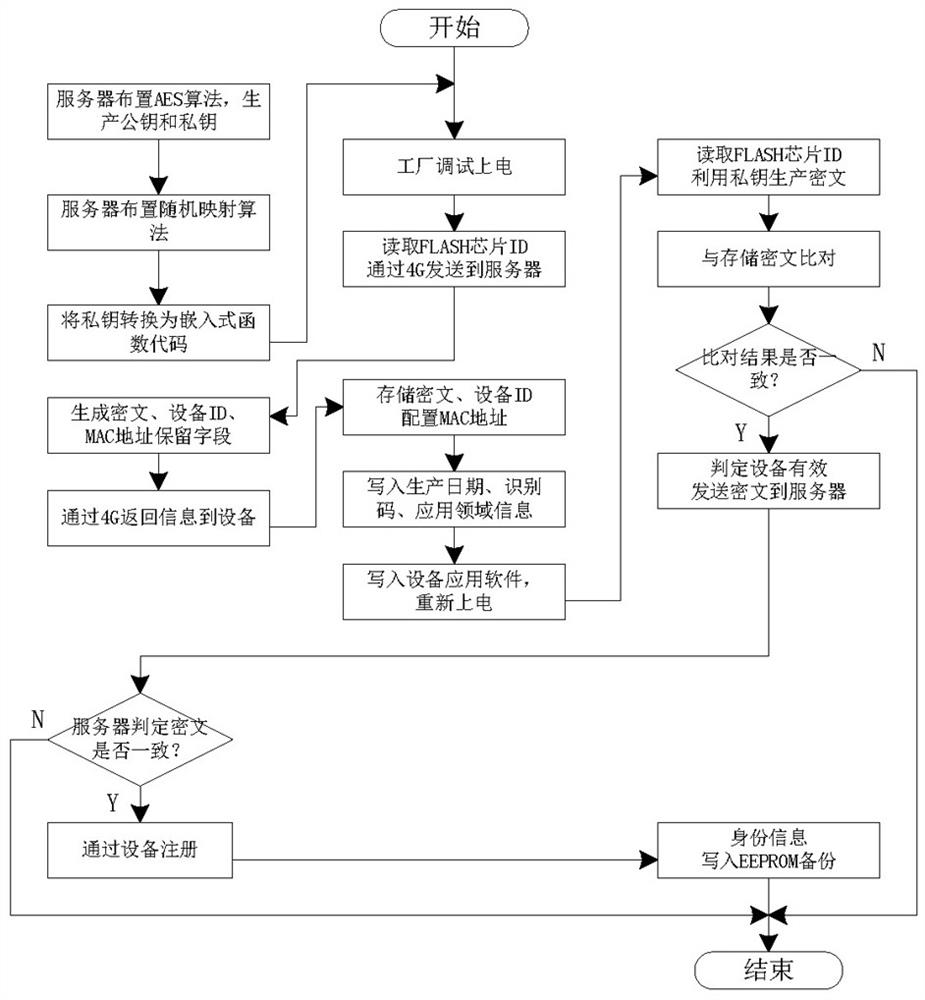
[0095] When the device is assembled in the factory and enters debugging, the debugging software reads the ID data of the FLASH chip inside the IoT device. Based on the default MAC address and fixed IP address, the device activates 4G communication through the SIM card and sends the ID data to the data center. Server, the server generates the private key and ciphertext; and generates the device ID number of 1, 2, ..., n according to the order received; generates the MAC address reserved field data according to the random algorithm. The server packs these three types of information into overall data and sends it back to the IoT device. The IoT device forms a new complete MAC address according to the reserved field data configuration, and stores the device ID and ciphertext data in the FLASH chip. After the debugger completes the above steps...
Embodiment 2
[0098] When used in the field of application (such as Figure 4 shown), the identification and management of IoT devices on the application site are as follows:
[0099] When the IoT device is put into use on site, the application software will also read the FLASH chip ID data inside the device, combine the AES algorithm and private key to generate ciphertext, and compare it with the pre-stored ciphertext. If the comparison passes, it will be determined as a device efficient. If the device is valid, send the ciphertext and device ID to the central server to apply for communication access. The server queries the corresponding ciphertext according to the received device ID, and compares it with the received ciphertext. If the comparison is successful, the communication is allowed. After admission, IoT devices can transmit application data to the data center through established channels.
[0100] After the IoT device is used on site, the device automatically connects to the Be...
Embodiment 3
[0103] When used during the maintenance phase (such as Figure 5 shown), the identification and management of IoT devices in the maintenance phase are as follows:
[0104] During the use of the IoT device, when the device fails due to random hardware failure and is returned to the factory for repair, the identity information of the device needs to be maintained simultaneously. First of all, it is necessary to check whether the FLASH chip is damaged, and if it is damaged, update the FLASH. Use the device ID information backed up in EEPROM to find the identity data of the device in the data center server, update the ciphertext and re-apply for device access according to the new FLASH chip ID, and keep other information unchanged. If the EEPROM is faulty, the identity information stored in the FLASH needs to be backed up again in the replaced EEPROM.
[0105] Compared with the prior art, the IoT device identification method of the present invention has the following advantages ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com