Network resource access control method under zero trust
A network resource and access control technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems of being unable to prevent illegal access of network resources by intranet users, and cannot guarantee the security of network resources, so as to improve scalability, portability, and application The effect of wide range and increased bandwidth
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
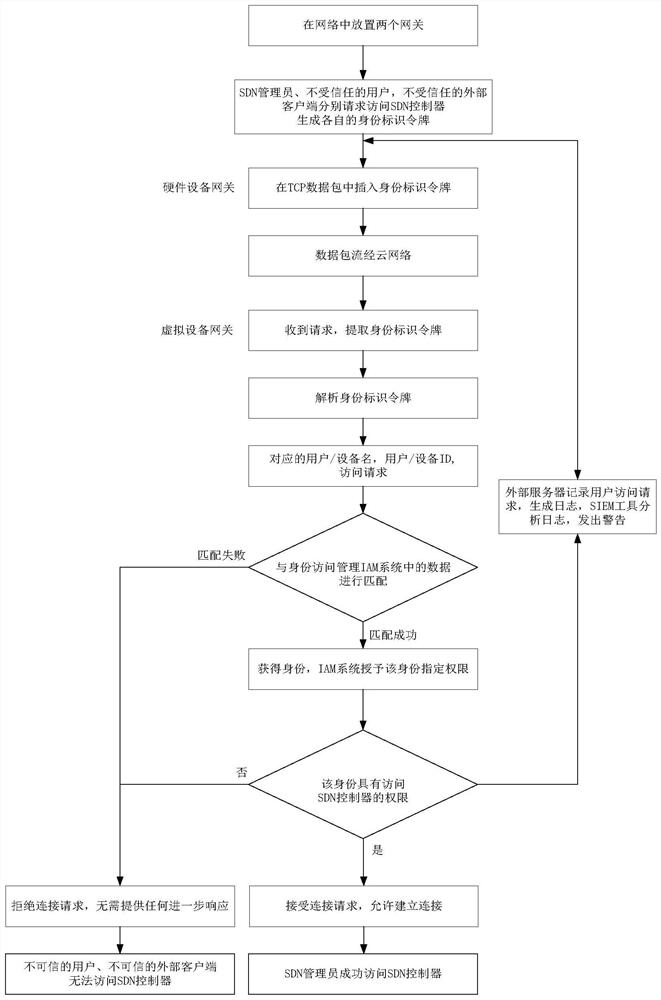
[0038] Embodiment 1 The SDN administrator requests to access the SDN controller.
[0039] refer to figure 1, the implementation steps of this example are as follows:
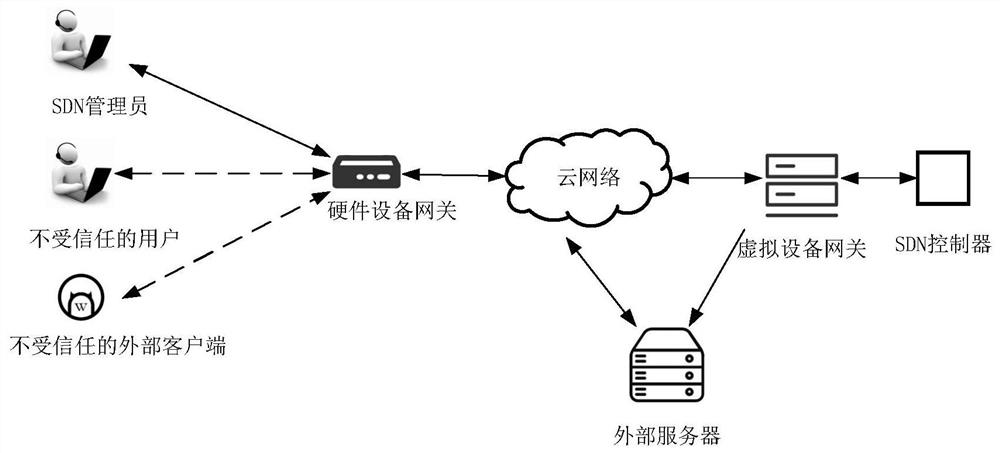
[0040] Step 1. Connect two gateways in the cloud platform.
[0041] A hardware device gateway is connected after the SDN administrator, and a virtual device gateway is connected before the SDN controller. These two gateways have three operating modes: bridge, execution, and monitoring. Among them:
[0042] In bridge mode, the gateway just acts as a bridging device for two ports, it does not insert an identity token into the data packet, and does not perform identity resolution;
[0043] In the execution mode, the gateway inserts the token into the TCP data packet and executes the extraction and analysis of the token, and implements the security policy according to the analysis result;
[0044] In monitor mode, the gateway inserts a token into TCP packets and performs extraction and parsing of that token, but ...
Embodiment 2
[0059] Embodiment 2, an untrusted user requests to access the SDN controller.
[0060] refer to figure 1 , the implementation steps of this example are as follows:
[0061] Step 1. Connect two gateways in the cloud platform.
[0062] Connect a hardware device gateway after the untrusted user, and connect a virtual device gateway before the SDN controller. The operation mode of the two gateways is the same as that described in step 1 in Example 1.
[0063] Step 2. An untrustworthy user initiates an access request to generate an identity token.
[0064] The untrustworthy user requests to access the SDN controller, and generates a corresponding identity token during the establishment of a session with the SDN controller, and the inherent information of the token is the same as the token information described in step 2 in Example 1.
[0065] Step 3, inserting the identity token into the TCP data packet.
[0066] The hardware device gateway inserts the identity token of the unt...
Embodiment 3
[0075] Embodiment 3, an untrusted external client requests to access the SDN controller.
[0076] refer to figure 1 , the implementation steps of this example are as follows:
[0077] Step A. Connect two gateways in the cloud platform.
[0078] A hardware device gateway is connected after the untrusted external client, and a virtual device gateway is connected before the SDN controller. The operation mode of the two gateways is the same as that described in step 1 in Example 1.
[0079] Step B, the client obtains the IP address of the SDN controller through an external means.
[0080] Since this client is an external client and does not know the IP address of the SDN controller in advance, assuming that the client somehow obtained the IP address of the SDN controller through an external channel, this external channel may be for the administrator's network Phishing attack.
[0081] Step C, the client initiates an access request according to the obtained IP address, and gene...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com