Author Organization Feature Engineering Method for Windows Platform Malware
A malicious software and feature engineering technology, applied in the direction of platform integrity maintenance, computer components, instruments, etc., can solve problems such as long time spent, and achieve the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
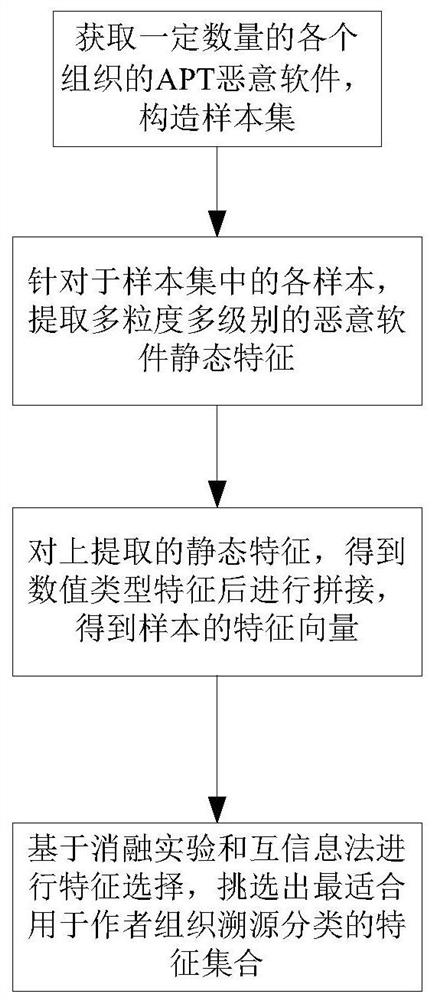
[0073] This embodiment discloses an author organization feature engineering method of Windows platform malware, such as figure 1 shown, including the following steps:
[0074] S1. Obtain a certain number of APT malware of various organizations, and construct a sample set.
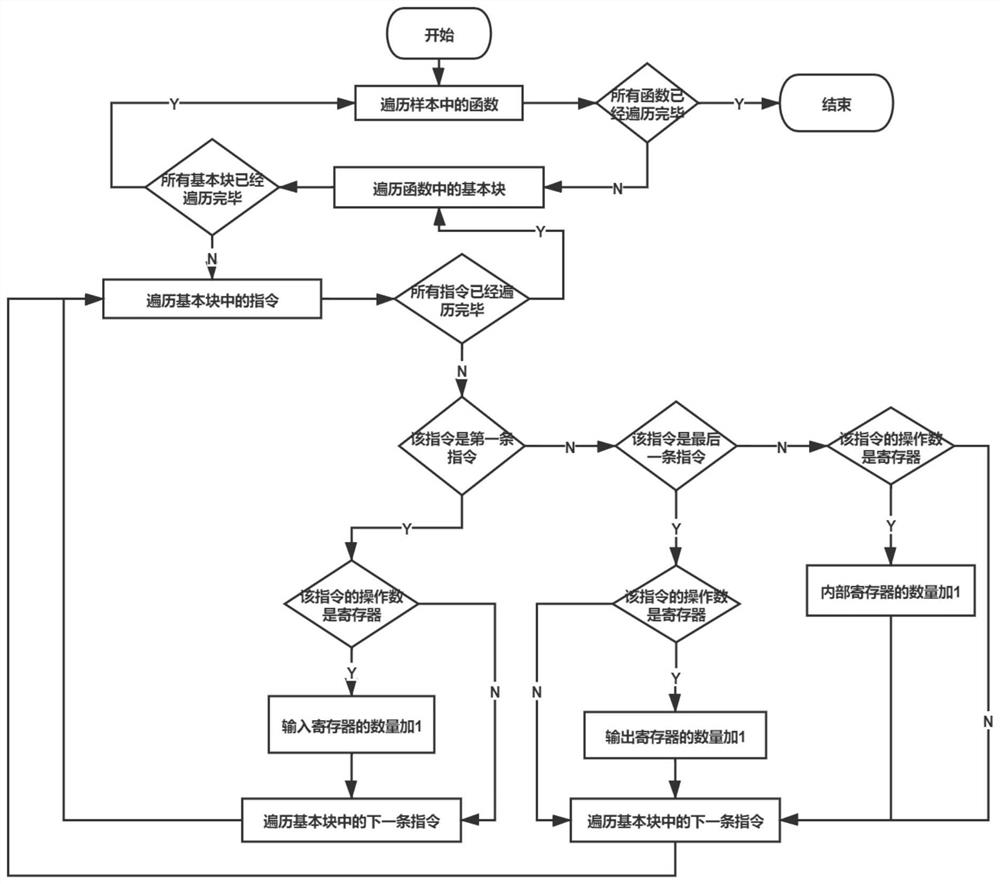
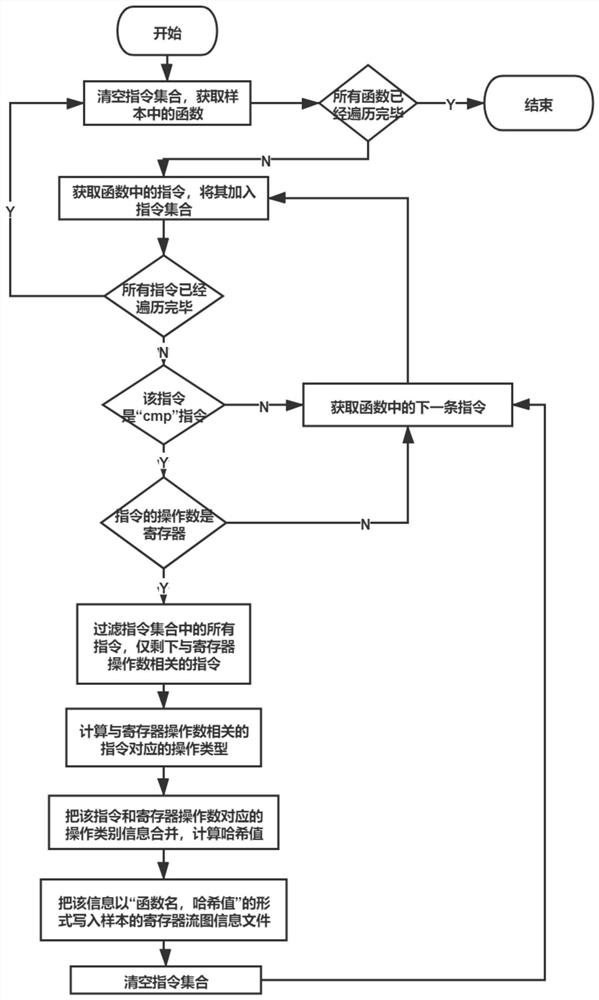
[0075] S2. For each sample in the sample set, extract multi-granularity and multi-level static features of malware, including features extracted from malicious binary files and features extracted from disassembly files of malicious binary files, specifically including PE file features , file byte characteristics, disassembly file characteristics, operand and instruction characteristics, function characteristics, program graph characteristics, and function centroid characteristics, as shown in Table 1:
[0076] Table 1
[0077]
[0078]
[0079] In this embodiment, the PE file features include PE file basic information features, header information features, import / export function information features...
Embodiment 2
[0125] This embodiment discloses an author organization feature engineering device for Windows platform malware, such as Figure 4 As shown, the device includes a sample acquisition module, a static feature extraction module, a feature processing module and a selection module, and the feature processing module includes a first conversion module, a second conversion module and a splicing module; the specific functions of each module are as follows:
[0126] The sample acquisition module is used to acquire APT malware of a certain number of known organizations and construct a sample set;
[0127] The static feature extraction module is used to extract multi-granularity and multi-level malware static features for each sample in the sample set, including features extracted from malicious binary files and features extracted from disassembly files of malicious binary files, Specifically, it includes PE file features, file byte features, disassembly file features, operand and instruc...
Embodiment 3
[0138] The present embodiment discloses a computing device, including a processor and a memory for storing executable programs of the processor, characterized in that, when the processor executes the program stored in the memory, the malicious Windows platform described in Embodiment 1 is implemented. The authors of the software organize the feature engineering approach as follows:
[0139] Obtain a certain number of APT malware of various organizations and construct a sample set;
[0140] For each sample in the sample set, extract multi-granularity and multi-level malware static features, including PE file features, file byte features, disassembly file features, operand and instruction features, function features, program graph features, and function centroid feature;
[0141] Among the static features extracted above, for the feature whose feature value type is string type, hash the string and map it to a vector of a certain dimension to obtain the feature of numerical type...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com