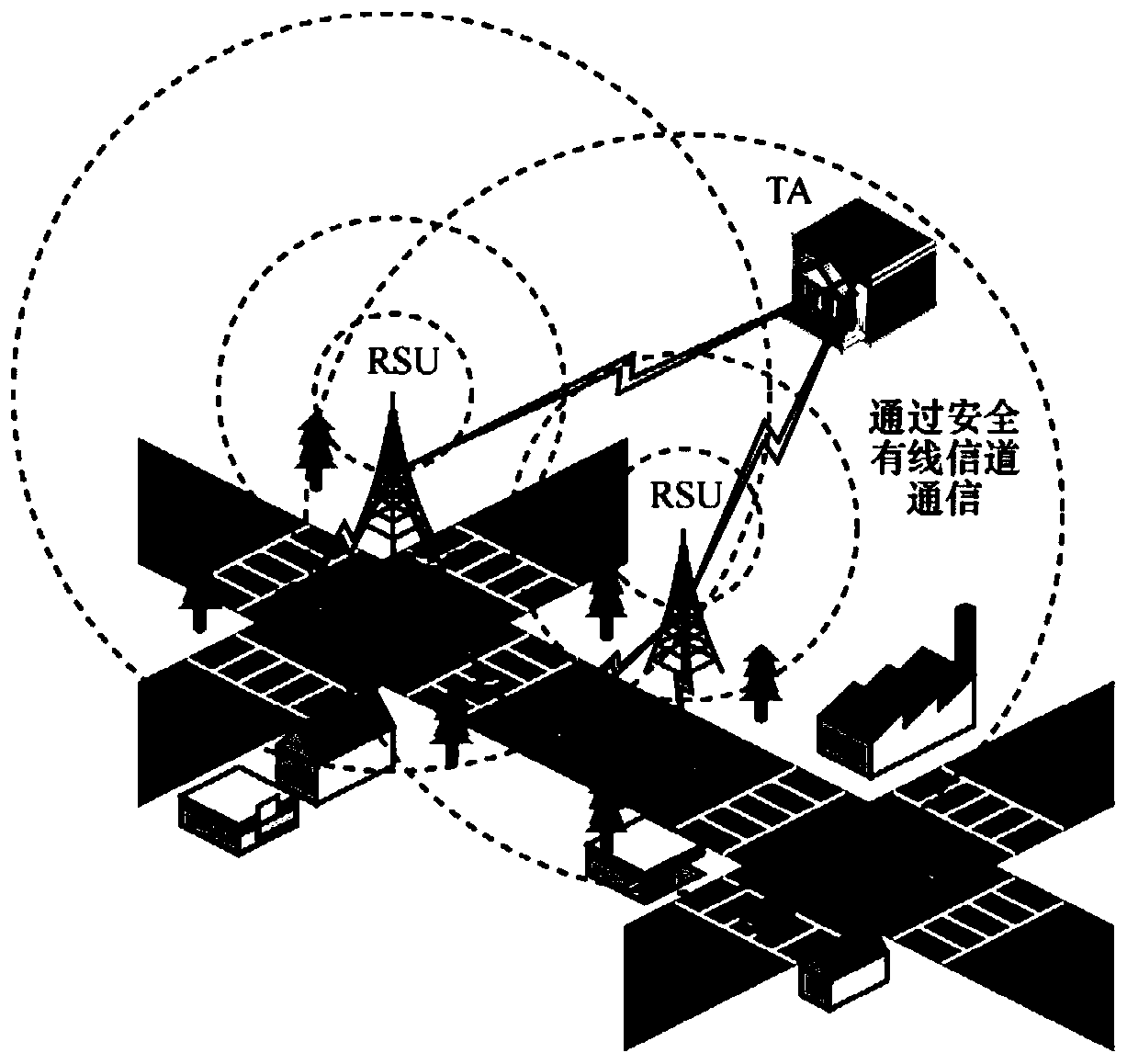
Anti-quantum computing Internet of Vehicles system based on secret sharing and mobile terminal and authentication method thereof
A mobile terminal and secret sharing technology, applied in the field of secret sharing, can solve the problems of inability to resist quantum computing, unfavorable identification, and too simple.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0075] The asymmetric algorithm used in this embodiment is identity-based cryptography. The key management server issues private keys to clients respectively. The identity of the client is ID, the public key is PK, and the private key is SK.
[0076] Based on relevant knowledge of identity cryptography: Suppose G is a group, take generator P from G, and select a random number as the private key s of the key management server, and have the public key Ppub=sP of the key management server. The key management server of this patent includes the identity used by the mobile terminal key system, issuing public and private keys, and the public and private keys of the identity are IDSM, PpubM / sM, PKSM / SKSM respectively, and the identity used by the OBU key system, issuing public and private keys, and identity The public and private keys are IDSC, PpubC / sC, and PKSC / SKSC respectively, where PKSM=H(IDSM), SKSM=sM*PKSM, PKSC=H(IDSC), SKSC=sC*PKSC. Since there is no need for communication...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com