Electric power Web application mimicry defense system
A defense system and web application technology, applied in the field of electric power information security, can solve the problems of asymmetric attack and defense, difficult to guarantee the security of key web applications in electric power enterprises, and difficult to defend, so as to achieve the effect of enhancing network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
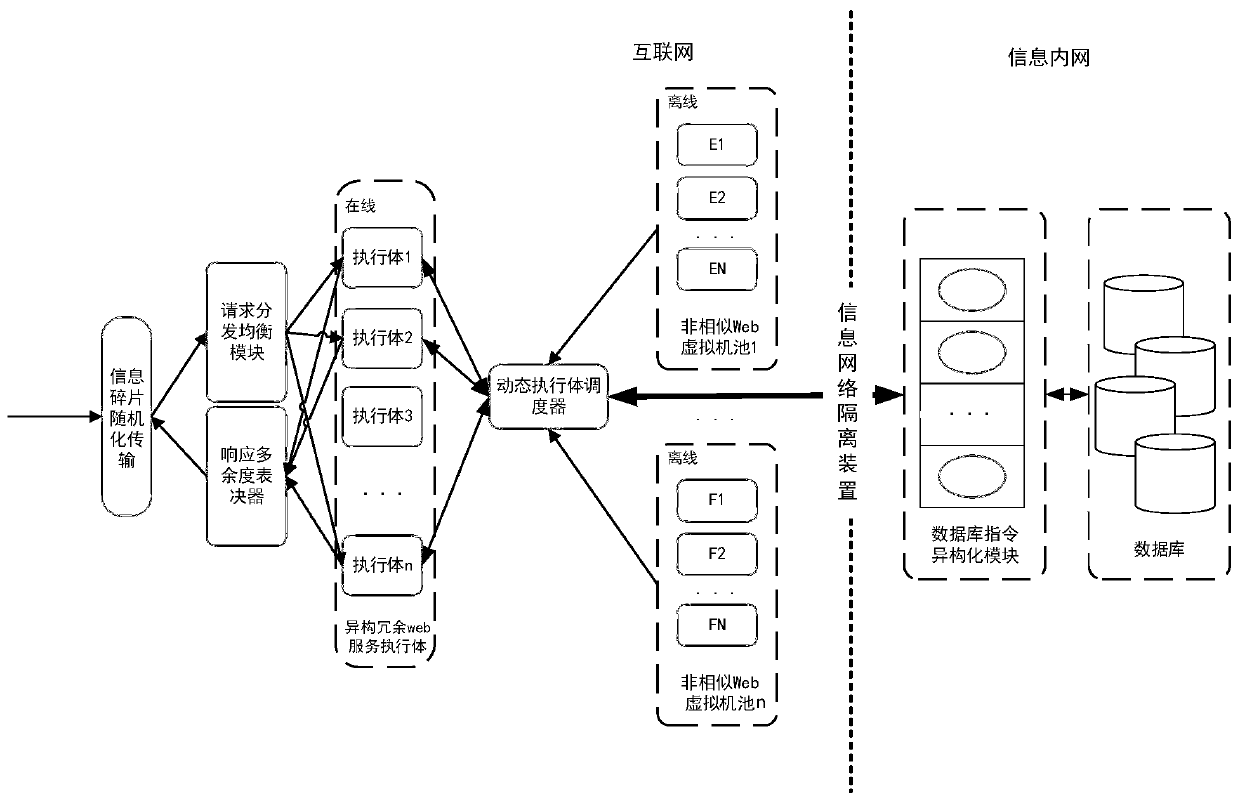
[0025] Such as figure 1 As shown, a power web application mimic defense system includes information fragment randomization transmission module, request distribution balance module, response redundancy voter, non-similar web virtual machine pool, dynamic executive scheduler and database instruction isomerization module .
[0026] The non-similar Web virtual machine pool is a real provider of Web services, and is composed of multiple non-similar Web virtual machine sub-pools, and each non-similar Web virtual machine sub-pool consists of multiple heterogeneous, diverse, redundant Web Composition of service executives; each of the non-similar web virtual machine sub-pools is physically independent and isolated from each other, and each of the web service executives and each of the heterogeneous redundant web service executives are also i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com