Identity authentication method based on iris and private key certificate chain connection storage structure
An identity verification method and storage structure technology, applied in the field of identity verification based on iris and private key certificate chain connection storage structure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
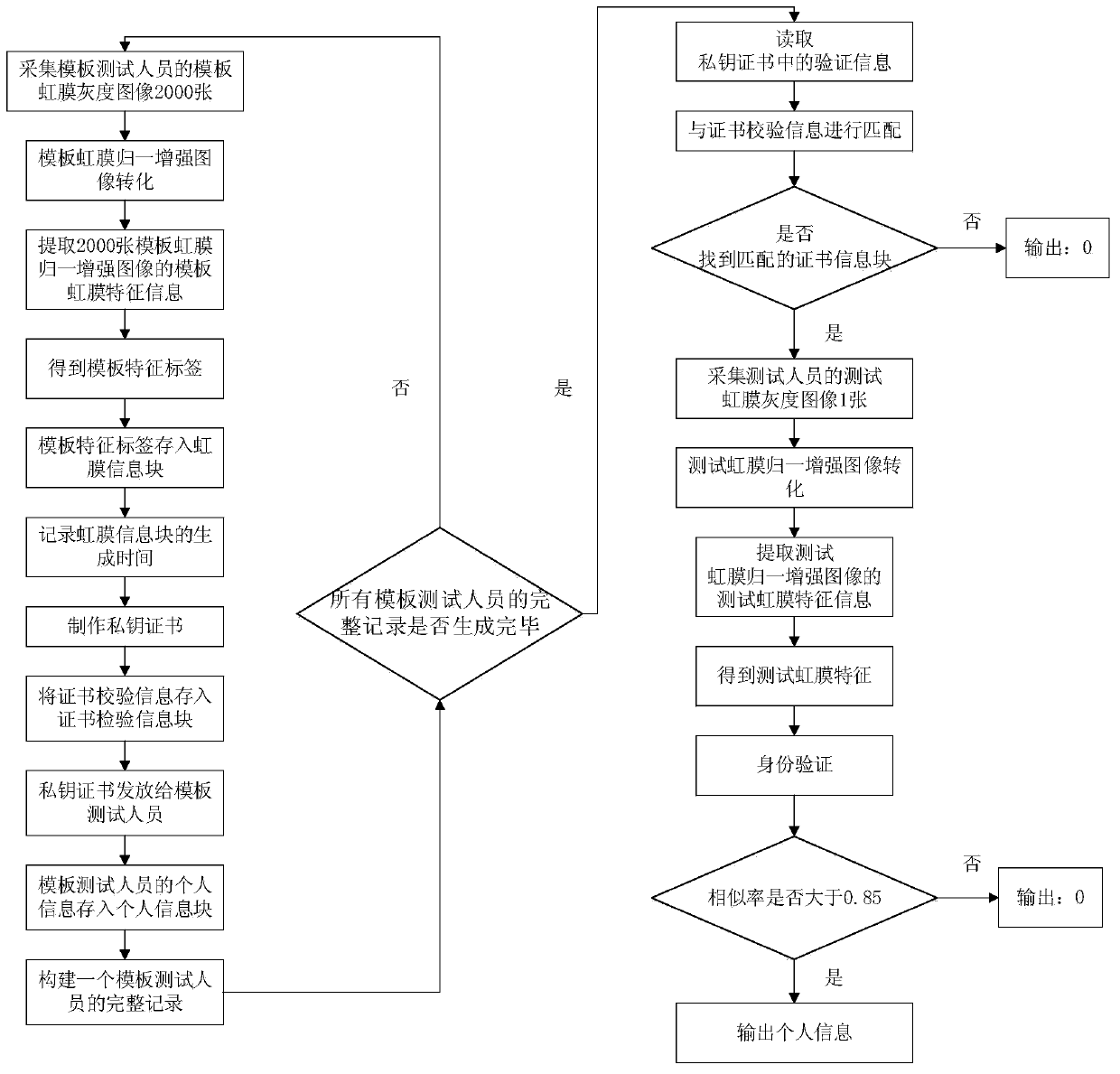
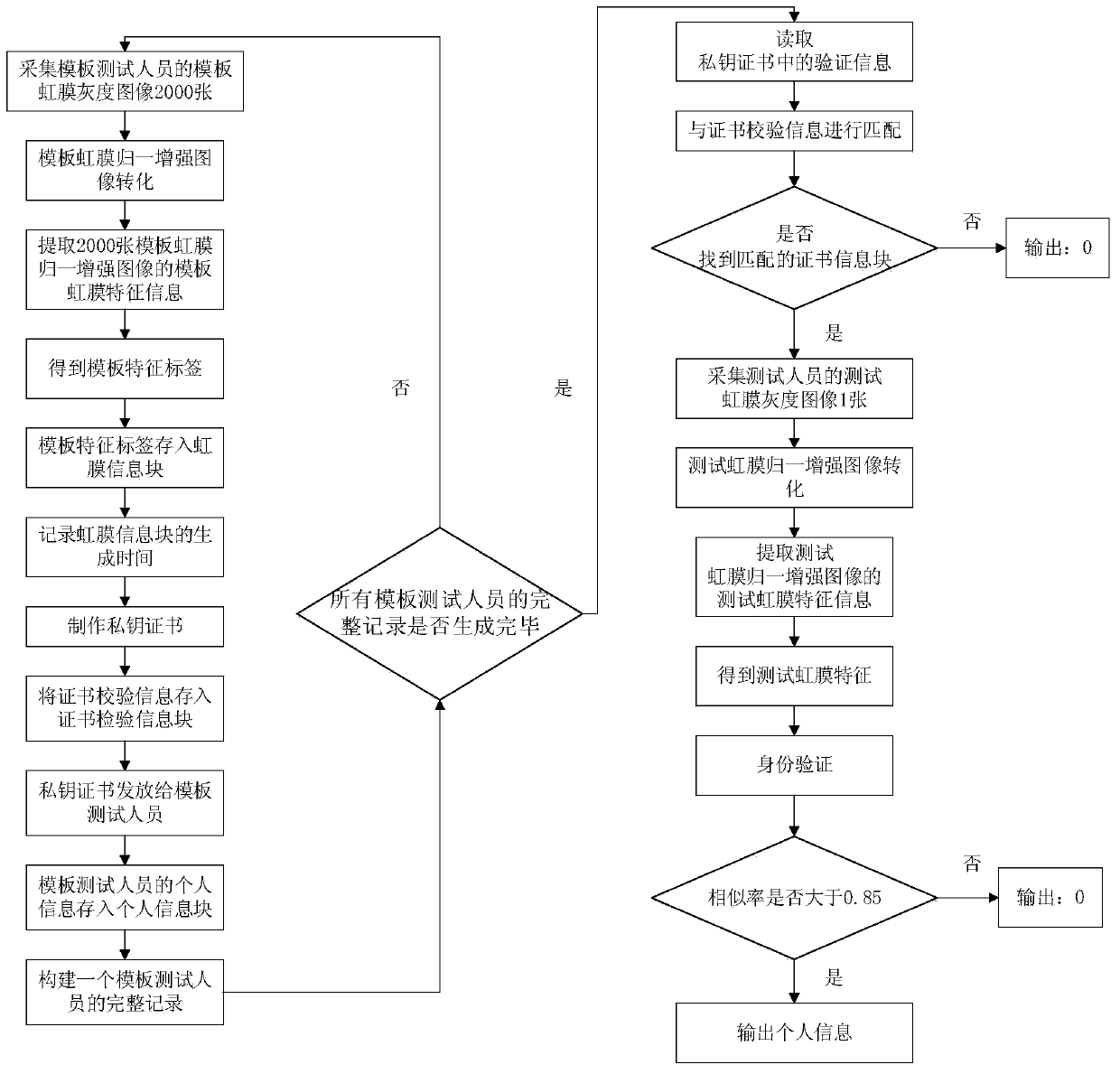
[0076] Under the framework of claim 1, for 3 people (named A (gender: male), B (gender: female), C (gender: male), no complete records of A, B, and C have been made before, test iris and template The iris collector equipment of the iris remains unchanged) the whole process of operation:
[0077] 1) Randomly use a common iris collector on the market to collect 2000 template iris grayscale images of A.
[0078] 2) The computer system converts each template iris grayscale image of A into a 256×32-dimensional template iris normalized enhanced image by means of the Daugman rubber band method and the equalized histogram.
[0079] 3) The computer system extracts the template iris feature information of 2000 template iris normalized and enhanced images of A respectively.
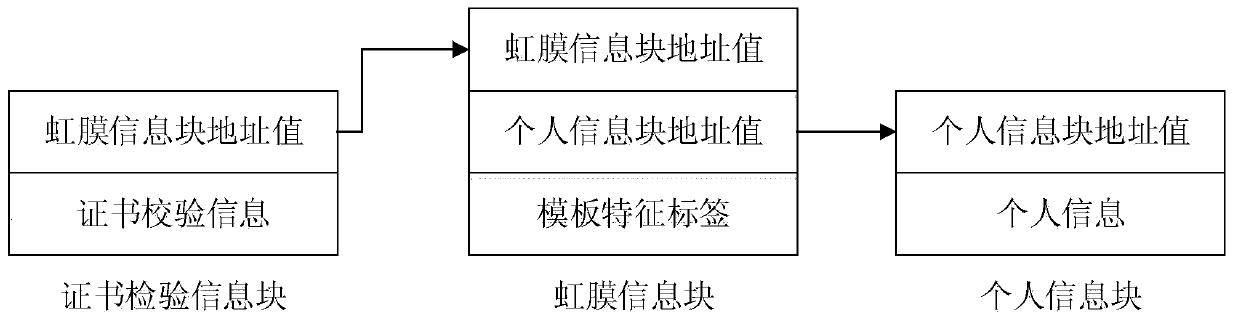
[0080] 4) The computer system counts the template iris feature information of 2000 template iris normalized and enhanced images of A, obtains the template feature label of A composed of 15 numbers, stores the templ...
Embodiment 2
[0091] Under the framework of claim 1, for 3 people (named D (gender: female), E (gender: female), F (gender: male), no complete records of D, E, F have been made before, test iris and template The iris collector equipment of the iris remains unchanged) the whole process of operation:
[0092] 1) Randomly use a common iris collector on the market to collect 2000 template iris grayscale images of D.
[0093] 2) The computer system converts each template iris grayscale image of D into a 256×32 dimensional template iris normalized enhanced image by means of the Daugman rubber band method and the equalized histogram.
[0094] 3) The computer system extracts the template iris feature information of 2000 template iris normalized and enhanced images of D respectively.
[0095] 4) The computer system counts the template iris feature information of 2000 template iris normalized enhanced images of D, obtains the template feature label of D composed of 15 numbers, stores the template fe...
Embodiment 3
[0106] Under the framework of claim 1, the whole process of operation for 4 people (named G, Q, T, M, who have made a complete record of G, Q, T before, but have not made a complete record of M):
[0107] 1) M forges a private key certificate, and uses a computer to read the verification information in the forged private key certificate, and matches the verification information with the certificate verification information in the certificate information blocks of G, Q, and T in turn. The certificate information block is found, so the output result: 0.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com