Intelligent monitoring method and system for digital currency in block chain
A technology of digital currency and intelligent monitoring, applied in the field of blockchain, it can solve the problem of no implementation plan and achieve the effect of reducing storage capacity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
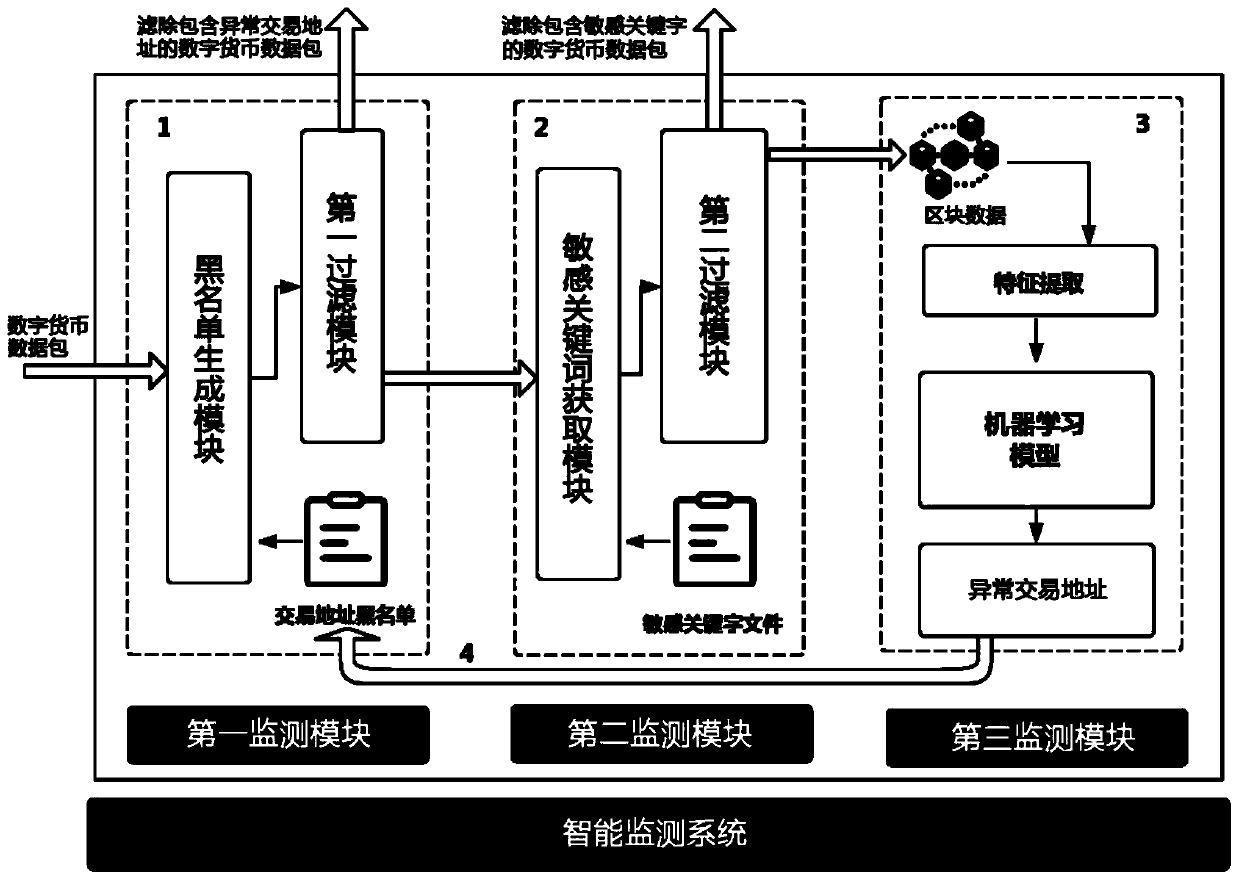
[0064] Such as figure 1 As shown in , the block chain mainly includes the following devices: router, miner node Node2, full node Node1, server, client Node3, and they can communicate through wired or wireless mode. In this embodiment, In order to solve the dark web transactions, transactions involving financial fraud, and transactions with sensitive content injected into the existing blockchain system, an intelligent monitoring method for digital currency in the blockchain is provided, where the digital currency can be Bitcoin Coin, Ethereum and other currencies, such as figure 1 As shown, the method steps are:
[0065] S1, by the block chain router (such as figure 1 R1, R2, R3) request the server S to obtain the abnormal transaction address, and use it as the transaction address blacklist; the blockchain miner node Node2 requests the server S to obtain the sensitive keyword file; load the machine in the blockchain server S learning model.
[0066] In this embodiment, the ...
Embodiment 2
[0101] This embodiment discloses an intelligent monitoring system for digital currency in a block chain, such as figure 1 and figure 2 As shown, including settings in the blockchain router (such as figure 1 The first monitoring module in R1, R2, R3), the second monitoring module set in the block chain miner node Node2 and the third monitoring module set in the block chain server S. In this embodiment, the blockchain router, the blockchain miner node, and the blockchain server communicate with each other through a wired connection or a wireless connection, and all of them transmit digital currency data streams bidirectionally.
[0102] The first monitoring module includes a blacklist generation module and a first filtering module; wherein:
[0103] The blacklist generation module is used to request the server to obtain abnormal transaction addresses, and use them as transaction address blacklists.
[0104] The first filtering module, after the blockchain router obtains the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com