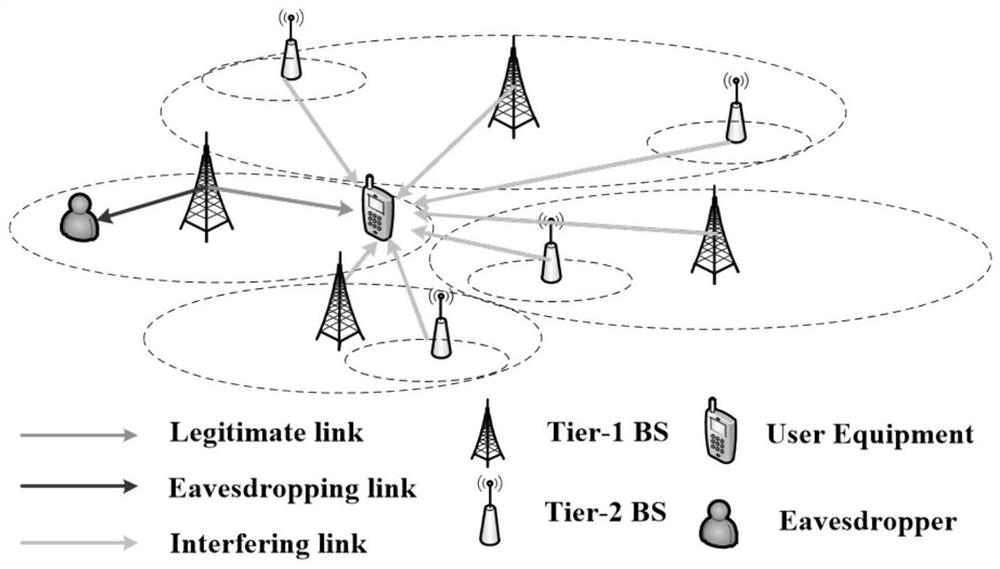
A Security Access Strategy in Heterogeneous Networks with Maximum Security Capacity
A security capacity and heterogeneous network technology, applied in the field of physical layer security and security access strategy in heterogeneous networks, can solve problems such as small-scale fading and co-band interference without consideration, and achieve the effect of improving security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
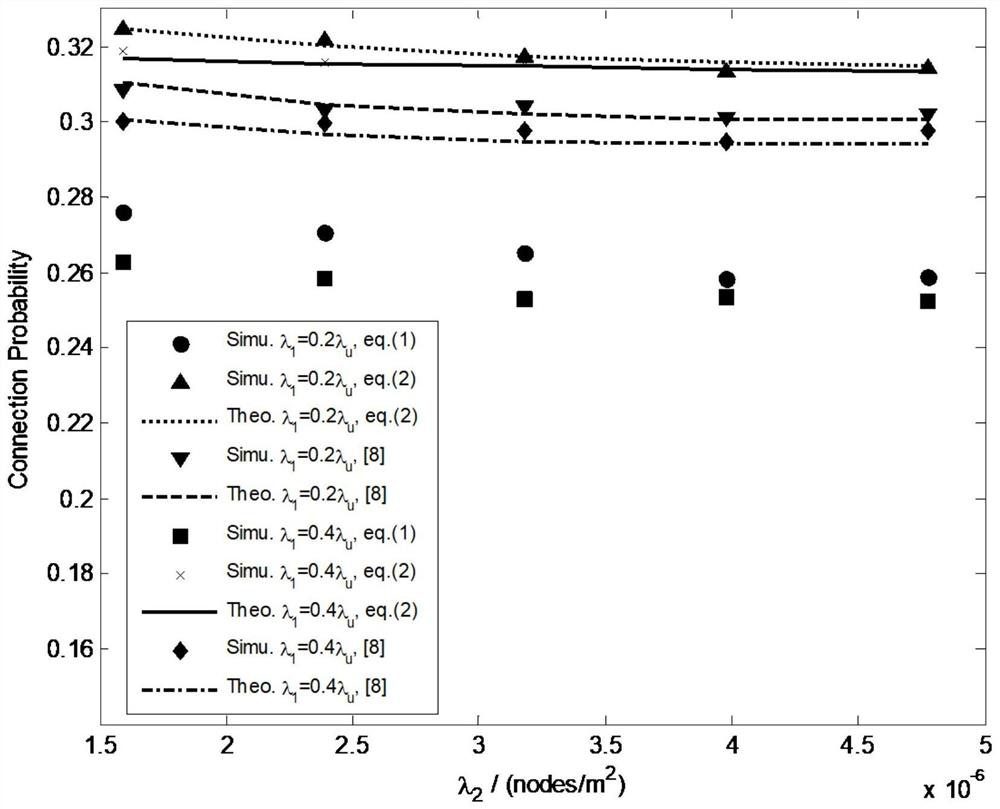
[0059] Embodiment 1 simulates the relationship between user connection probability and base station density, and compares the present invention with the maximum security capacity access strategy and the strategy in document [1].
[0060] pass figure 2 It can be found that the connection performance of the user brought by the access strategy proposed by the present invention can be well described by the theoretical formula in the present invention. The connection performance brought by the proposed strategy can approach the maximum security capacity access strategy, which is better than the strategy in literature [8]. At the same time, with the increase of base station density, the connection probability of users decreases, but the decreasing trend is slow.
Embodiment 2
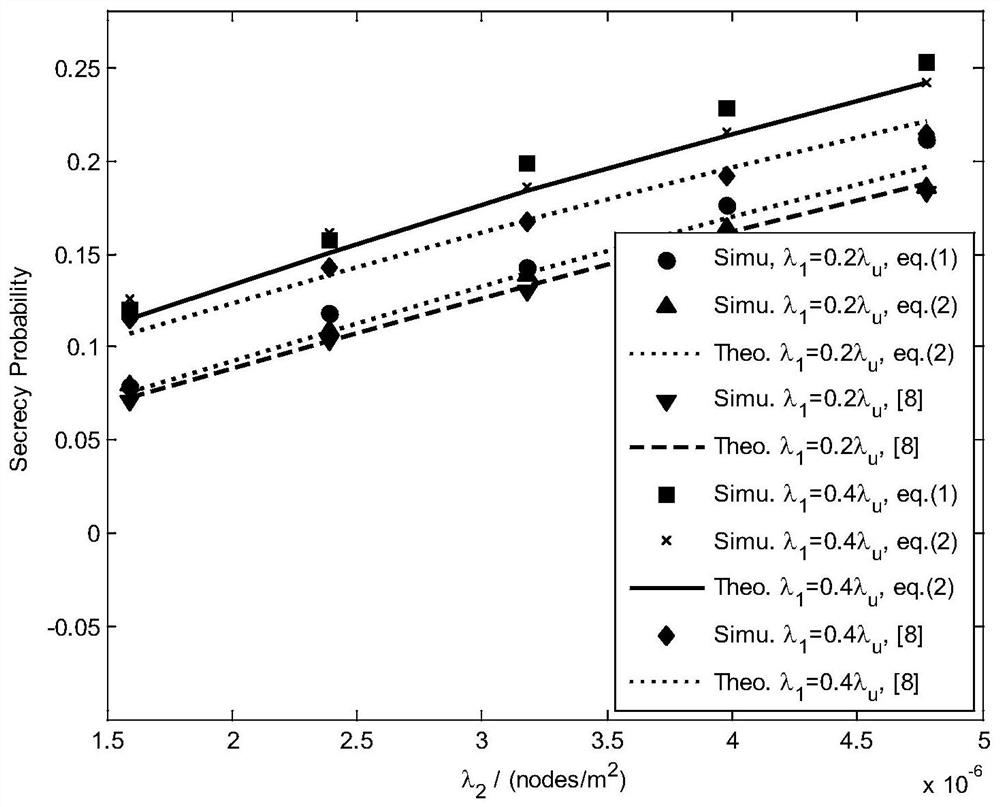
[0061] The second embodiment simulates the relationship between the user's security probability and the base station density, and compares the present invention with the maximum security capacity access strategy and the strategy in document [8].
[0062] pass image 3 It can be found that the security performance of the user brought by the access strategy proposed in the present invention can be well described by the theoretical formula in the present invention. The security performance brought by the proposed strategy can approach the maximum security capacity access strategy, which is better than the strategy in literature [8]. At the same time, with the increase of base station density, the security probability of users is significantly improved.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com