Method and system for detecting white list of data stream based on regular expression
An expression, data flow technology, applied in digital transmission systems, other database retrieval, transmission systems, etc., can solve the problems of network server intrusion, penetration attack, loss of server sensitive data, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] It should be noted that, in the case of no conflict, the embodiments in the present application and the features in the embodiments can be combined with each other.
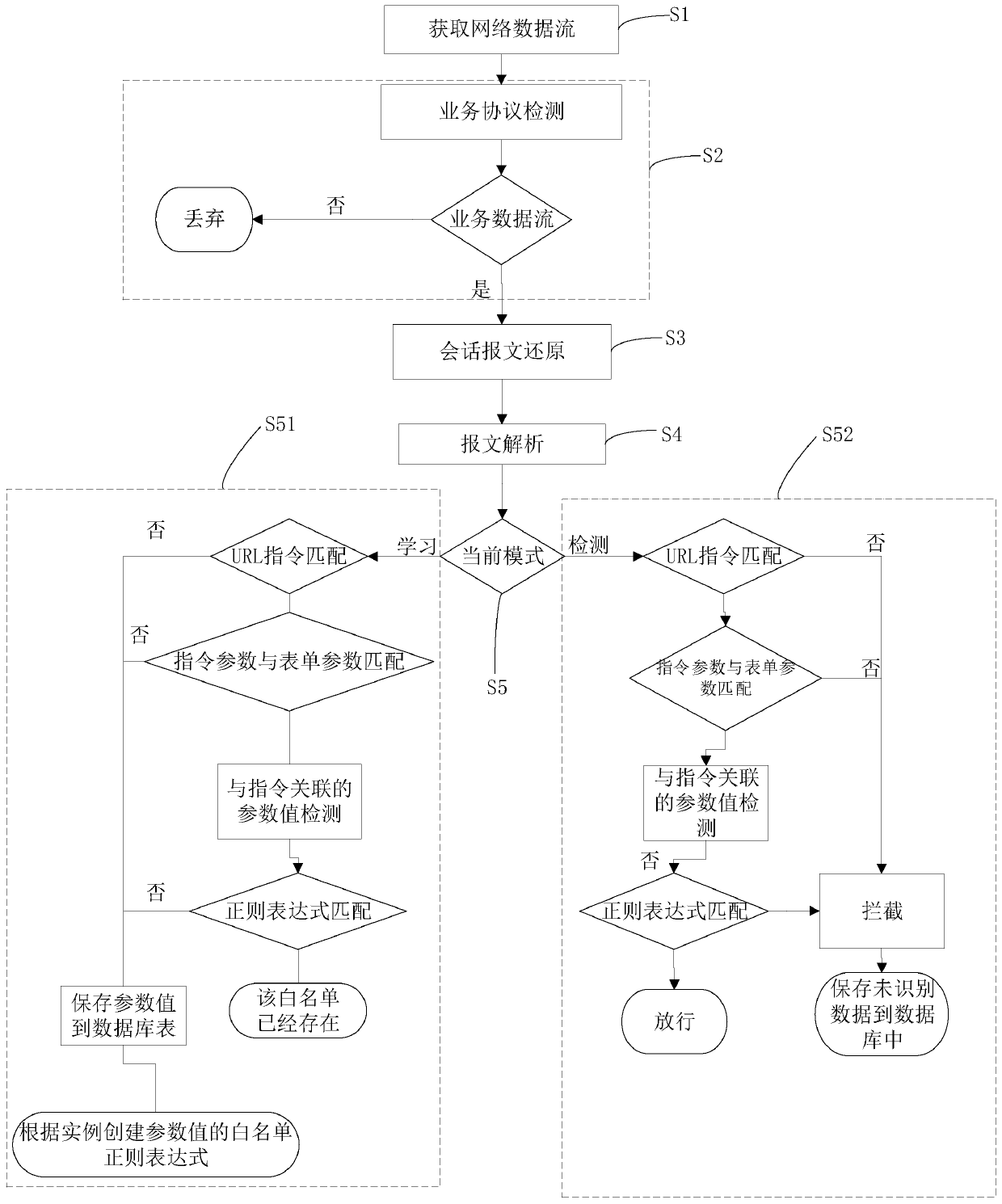
[0044] see figure 1 , a flow chart of a method for detecting a network data flow whitelist according to an embodiment of the present invention. Such as figure 1 As shown, the steps of this method are as follows:
[0045] Step S1: Obtain network data flow;
[0046] Step S2: Service protocol detection, performing service protocol detection on the network data flow, and judging whether the service data flow conforms to the service agreement,
[0047] If the judgment result of the business data flow is negative, it is discarded;
[0048] If the result of judging the business data flow is judged to be yes, then execute the next step;
[0049] Step S3: Restoring the session message to obtain a complete message;
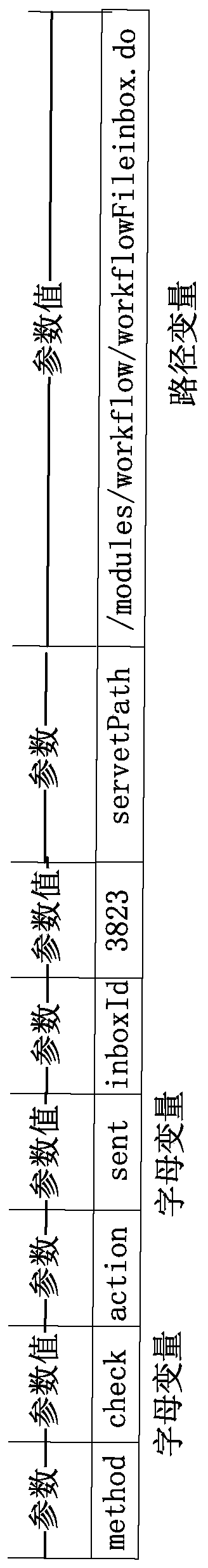
[0050] Step S4: Perform message analysis on the complete message to obtain parameter values, i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com