Database auditing method, system and equipment under big data stream load
A database and data flow technology, applied in the field of network security, can solve problems such as the difficulty of auditing equipment, and achieve the effects of simplifying message preprocessing flow, improving processing efficiency, and improving processing performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings.
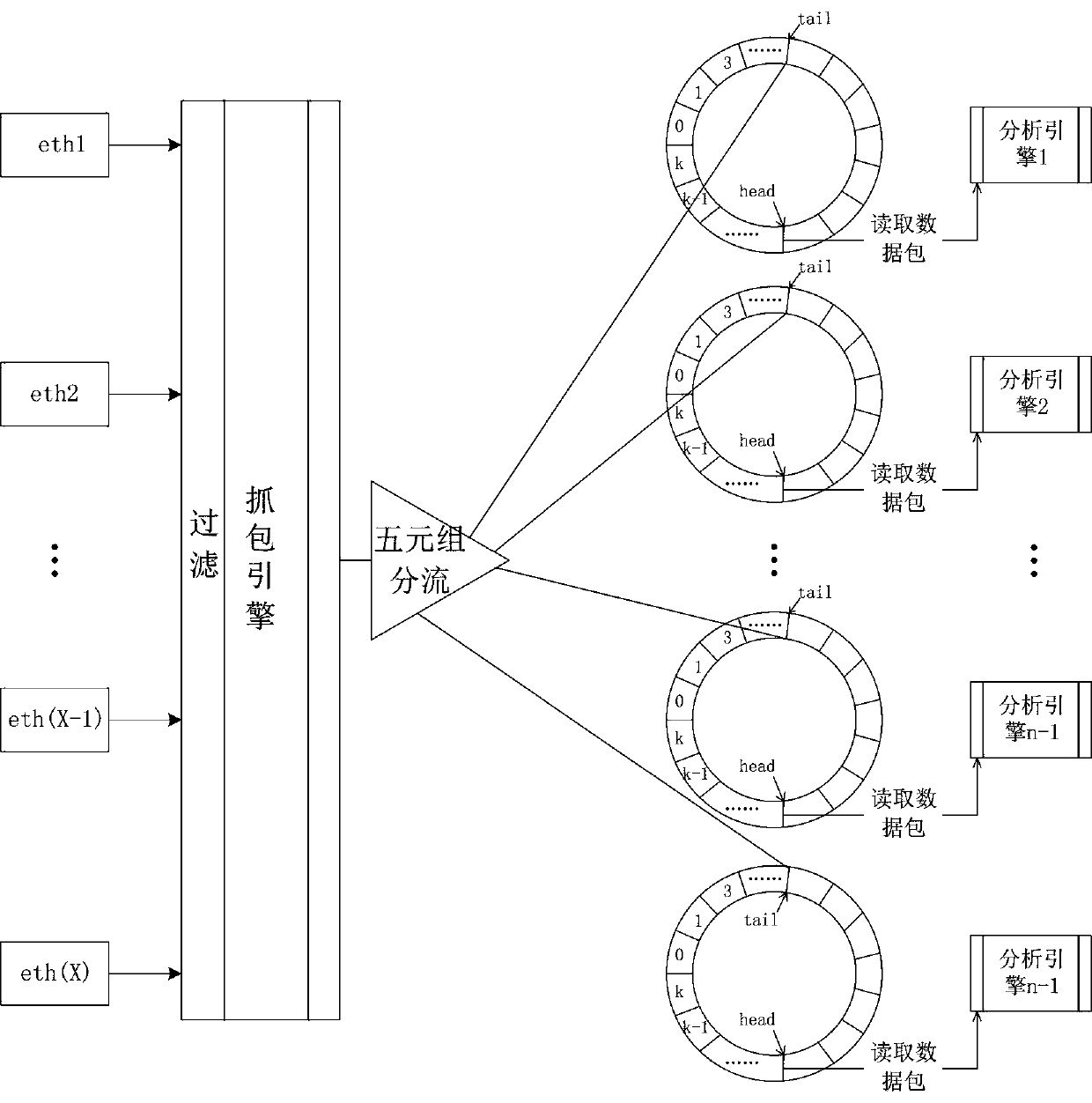
[0034] First of all, the database audit method under the load of large data flow includes environment detection, data flow collection and distribution, content analysis, and audit response; data packet content analysis includes analysis algorithms based on finite state machines, such as figure 1 Shown:
[0035] After getting the data packet from the network card, take out the database port by offset, confirm whether the protocol of the port needs to be audited, if not, discard it directly, and place the data packet on the ring queue if necessary;
[0036] Get the data packet from the ring queue, offset the five-tuple information and application layer data;
[0037] Call the public plug-in to match the host of the data packet, confirm whether the data flow of the business host needs to be audited, if not, discard it directly, and continue to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com