Formal detection method for defense of information physical fusion system
A technology of cyber-physical fusion and detection method, which is applied in the field of formal detection of cyber-physical fusion system defense, can solve problems such as increasing the impact of false data injection attacks, and achieve the effect of improving system security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
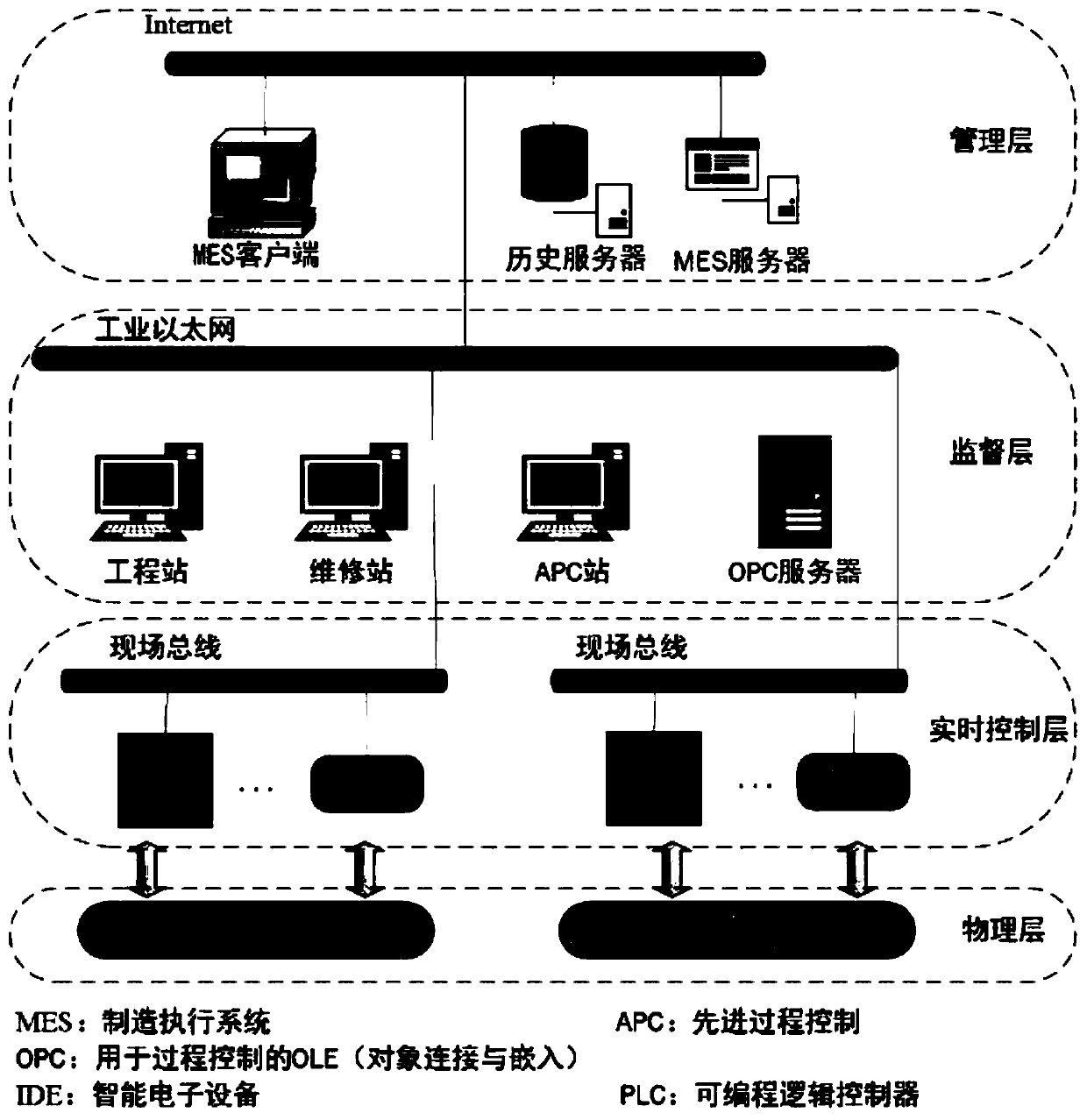
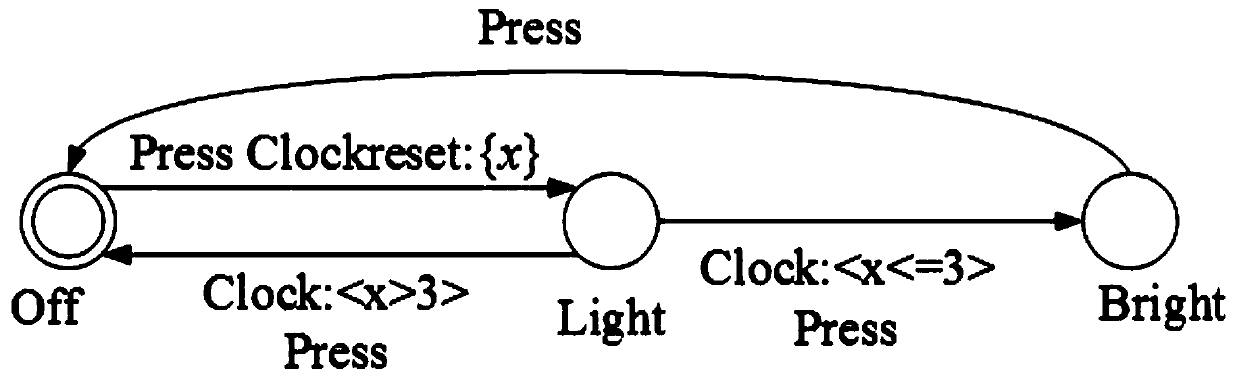
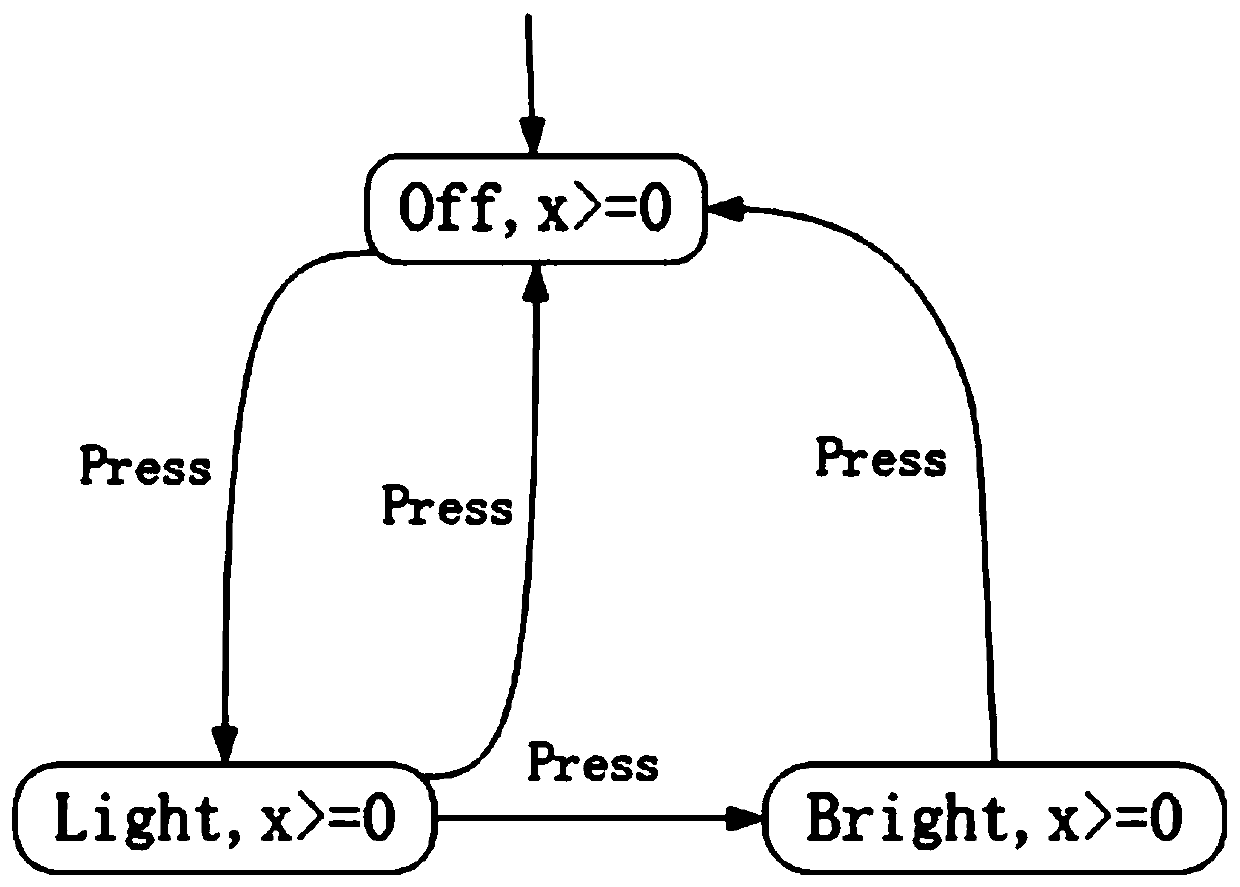
[0049] A formalized detection method for cyber-physical fusion system defense, detection and verification of CPS false data injection attacks based on timed automata, including the construction of models of each part of CPS and the verification of CPS security attributes. The construction of models of each part of CPS mainly includes system Modeling, attacker modeling, automatic recovery mechanism modeling; CPS general layered network security architecture includes management layer, supervision layer, real-time control layer and physical layer; in the management layer, information is exchanged between the hardware of the system through the Internet , functions include: historical data storage, data management and some other tasks; the function of the supervisory layer is to configure system parameters and monitor the overall stability and security of the system; the controller of the real-time control layer is connected with the physical layer equipment, and the controller dir...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com