Malicious network behavior identification method and device based on network gene technology
A technology of network genes and identification methods, applied in the field of Internet of Things network communication security, can solve the problems of little effect, increased killing time, unable to meet the security requirements of the Internet of Things, etc., and achieve the effect of low missed judgment rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0049] Such as figure 1 As shown, a method for identifying malicious network behavior based on network gene technology of the present invention comprises the following steps:
[0050] Step S101: Construct the network gene bank of the terminal and the cloud.
[0051] Step S102: Identify malicious network behaviors based on the network gene pool.
Embodiment 2
[0053] Such as figure 2 As shown, another network malicious behavior identification method based on network gene technology of the present invention comprises the following steps:
[0054] Step S201: constructing a terminal and cloud network gene bank, including:
[0055] Step S2011: Collect a large number of malicious code samples, analyze the malicious code samples through reverse engineering, express the malicious code in an intermediate language, use the concept of network genes to define the gene fragments of the samples, and extract all the gene fragments of the samples from the binary files to form a gene Sequence; as an implementable mode, the intermediate language is rtl;
[0056]Step S2012: Form a sample behavior sequence set, and establish a mapping relationship between the sample gene sequence and the behavior sequence;
[0057] Step S2013: Store the gene sequence, behavior sequence, and mapping relationship in the cloud gene bank at the same time;
[0058] Ste...
Embodiment 3
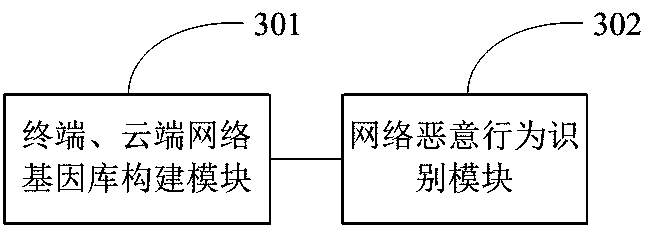
[0066] Such as image 3 As shown, a network malicious behavior identification device based on network gene technology of the present invention includes:
[0067] The terminal and cloud network gene bank construction module 301 is used to construct the terminal and cloud network gene bank.
[0068] The malicious network behavior identification module 302 is configured to identify malicious network behaviors based on the network gene database.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com