Multi-authorization attribute encryption and decryption method
An authorization attribute, encryption and decryption technology, applied in the field of encryption and decryption, can solve the problems of high consumption of encryption and decryption operations, high storage space occupancy rate, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
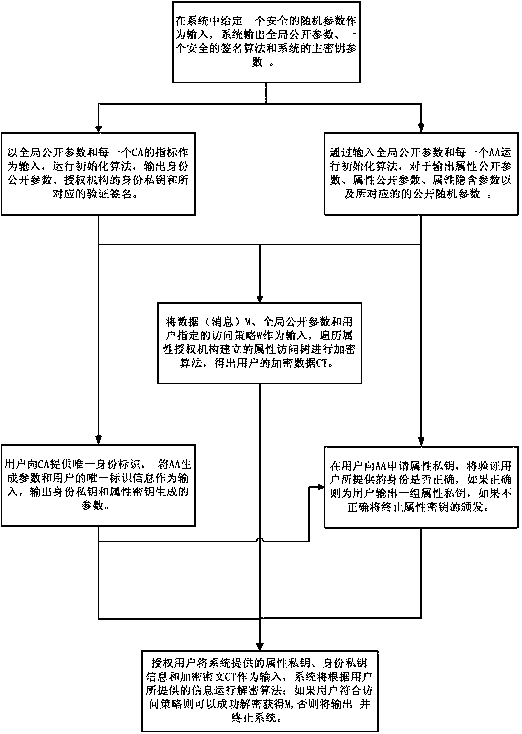
[0045] A method for encrypting and decrypting multiple authorization attributes, comprising the following steps:
[0046] Step 1. System initialization: including four aspects: the construction of the attribute access tree Γ of the hierarchical attribute organization, the generation of system parameters, the initialization of the central authorization organization, and the initialization of the attribute authorization organization;
[0047] (1) System parameter generation: input a security parameter 1 in the system λ , the system calls the group generation algorithm to generate two multiplicative cyclic groups G and G of order prime number p T , the generator of the group G is g, and there is a bilinear map e:G×G→G T , and at the same time, choose an existential unforgeable signature algorithm Σ sign =(KenGen,Sign,Verify), output global public parameters δ=(e,g,G,G T , p, Σ sign );
[0048] (2) Construction of hierarchical attribute access tree Γ: each attribute authority...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com